It is well-established that email is the number one threat vector for cyberattacks. It’s a go-to for many bad actors because they don’t need to be highly skilled to initiate an email-based attack. Nor do they need to do elaborate work upfront. Their success hinges on their ability to be convincing.
Targets must believe that they are interacting with a trusted source if they’re going to voluntarily hand over sensitive data, provide their authentication credentials, make a wire transfer or install malware. That’s why a critical part of any company’s security posture is using protocols and policies that reduce impersonation risk. And a major step in this direction is to enable and enforce email authentication methods across all your domains. These include:
- Sender Policy Framework (SPF). This is a published authoritative list of approved sending IP addresses. It can help recipient email systems confirm that an email is coming from a legitimate source and is not impersonating a person or entity through spoofing.
- DomainKeys Identified Mail (DKIM). This email authentication method stamps a digital signature to outgoing emails. It helps recipient email systems verify, with proper alignment, that the email was sent by the domain it claims to be from and that it hasn’t been altered in transit.
- Domain-based Message Authentication, Reporting, and Conformance (DMARC). This email authentication protocol builds on SPF and DKIM by allowing senders to set policies for handling emails that fail these authentication checks.
If you don’t maintain your systems, bad actors can exploit out-of-date information and nullify your email authentication efforts. In this blog, we will highlight a key bad actor impersonation tactic to inspire you to regularly spring clean your records moving forward.
The tactic in focus: “dangling DNS”
Dangling DNS refers to a misconfiguration in your email-related domain name system (DNS) records. A reference domain or subdomain is left pointing to a domain that no longer exists or is not under the control of the original domain owner. The term “dangling" implies that the DNS entry is pointing to something that is hanging without proper support. In this case, it is a domain that has expired.
Bad actors have gotten wise to the fact that these expired domains create a crack in your defense that they can exploit.
The risk of subdomain takeover
If a subdomain is left pointing to an external service that the domain owner no longer controls, an attacker can register that domain to gain control of any DNS records that are pointed toward it. So, when they initiate their impersonation-based attack, they have the added benefit of passing email authentication!
Using SPF records with all your sending infrastructure listed, rather than hidden behind an SPF macro, also discloses sensitive data about your company’s infrastructure. Attackers can use this data to plan and execute targeted attacks.
Actions you can take to reduce risk
To mitigate the risks associated with dangling DNS records, domain owners must review their email-related DNS configurations regularly. It is especially important when you decommission or change services. Here are some actions that can help you to reduce your risk exposure.
Regularly review and remove unused DNS records
You should promptly remove DNS records that point to deprecated or unused services:
- SPF records. Review and minimize the entries that are posted within your SPF record. Review every “Include” and “Reference”, especially for third parties and expired domains, or if domains change owners. Access to SPF telemetry data can help simplify your investigations.
- DKIM selector records. Review CNAMEd DKIM selector records that point to third parties for expired domains, or if domains change owners.
- DMARC policy records. Review CNAMEd DMARC records that point to third parties for expired domains, or if domains change owners.
- MX records. Review MX records for your domains to see if any old entries are still included that point to third parties for expired domains, or if domains change owners.
Take steps to prevent subdomain takeovers
- Follow guidelines. When you use third-party services or cloud providers, follow their guidelines on how to avoid subdomain takeover risks.
- Publish a strong DMARC reject policy. This will help prevent malicious actors from exploiting your current and future subdomains.
- Use SPF telemetry technology. This will give you visibility into inactive domains. Inactivity could be a sign that domains are expired and should be removed from your SPF record.
Enhance the integrity and authenticity of your DNS data
-
Use DNS security features. This includes DNSSEC (Domain Name System Security Extensions).
A proactive approach to managing DNS configurations and addressing dangling DNS issues is essential. It will help you to reduce the risk of certain impersonation-based security incidents and better protect your company’s online presence. Regular auditing and monitoring of DNS records are important steps to maintain a secure and reliable DNS infrastructure.
How Proofpoint can help
Proofpoint takes a holistic approach to addressing impersonation risk with a unified email authentication solution that offers hosted SPF, DKIM and DMARC capabilities. SPF telemetry is now a standard feature in our hosted SPF service Proofpoint Email Fraud Defense. That means you get visibility into IPs that are no longer active, which attackers could exploit.
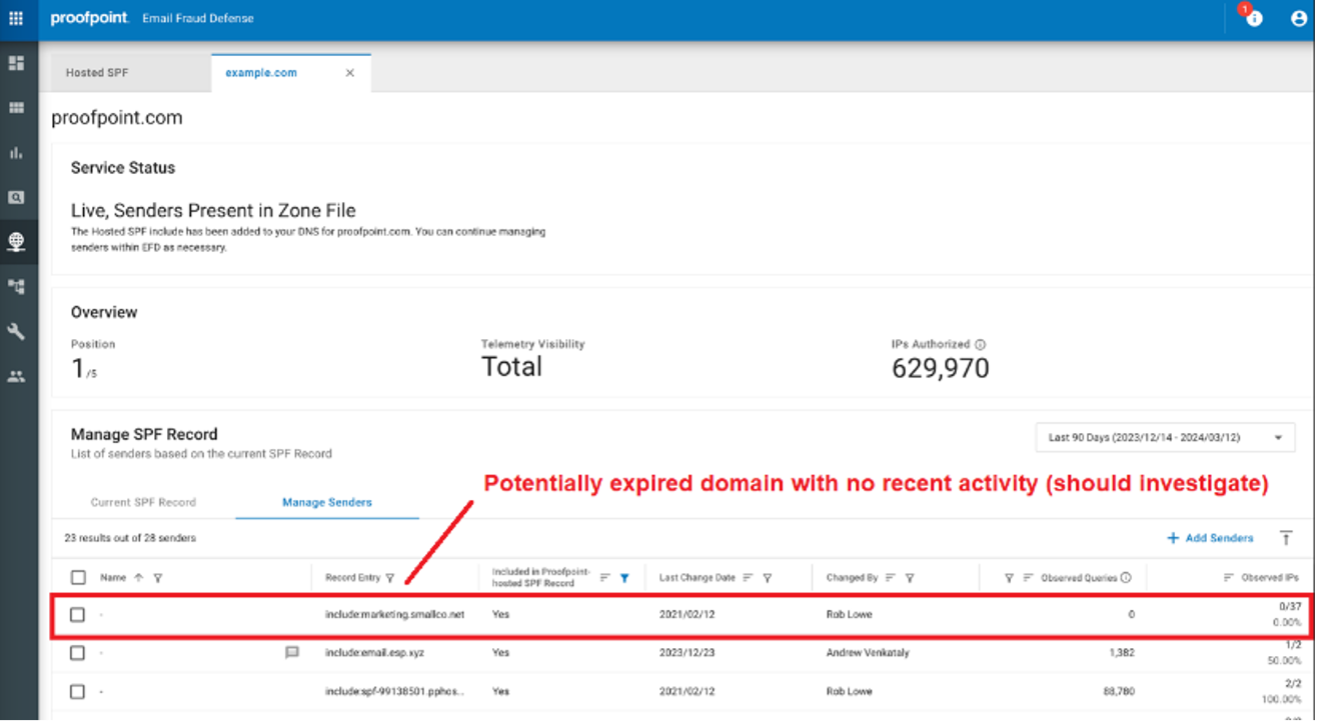
SPF Telemetry Reporting in Proofpoint Email Fraud Defense.
Learn more
For more information about Proofpoint impersonation protection, see this solution brief. You can also contact your Proofpoint account team to discuss how we can help improve your security posture and reduce your overall risk.
Subscribe to the Proofpoint Blog

