Email fraud often starts with an email in which the attacker poses as someone the victim trusts or “actually becomes” that person by compromising his/her account. The message makes a seemingly legitimate business request that often leads to wire transfer or financial payment.
In the recently published Internet Crime Report, the FBI warned the public that email fraud schemes have evolved. Attackers went from spoofing or hacking the email accounts of C-levels, requesting wire payments to be sent to fraudulent locations, to compromising and impersonating vendor emails.
Among various types of email fraud, supplier invoicing fraud often accounts for the biggest financial losses due to the nature of B2B payment. Attackers now target an organization’s suppliers and vendors to launch fraud, phishing and other attacks. These indirect attacks abuse the implicit trust relationship your organization has with its suppliers. Unfortunately, most security teams don’t have visibility into who their suppliers are, let alone the risk posed by their trusted vendors.
Introducing Nexus Supplier Risk Explorer
To provide visibility into supplier vendor risk, Proofpoint recently introduced Nexus Supplier Risk Explorer, a unique feature in our Proofpoint Email Fraud Defense offering.
To help you overcome the challenge with complex supply chain attacks, Supplier Risk Explorer automatically identifies your suppliers and the domains they use to send email to your users. Integrated with Proofpoint’s industry-leading Threat Protection Platform, Supplier Risk Explorer analyzes your email communications and provides a supplier-centric view of threats. It reveals the message volume, the threats detected from supplier domains, as well as the messages blocked from malicious lookalikes of your suppliers’ domains.
Supplier Risk Explorer then assesses the risk level of these supplier domains by evaluating several dimensions, including:
- Threats sent to your organization
- Threats sent to other Proofpoint customers
- The lookalikes of supplier domains
- Whether it is recently registered
- Whether it has a DMARC reject policy
By ranking and prioritizing the risk level of your supplier domains, your security team can see and prioritize which suppliers that they should pay the most attention to. If a supplier’s domain is actively sending your users malicious email, it will pop to the top of the list. That way, your security team can focus their efforts on suppliers that pose the highest risk to your organization.
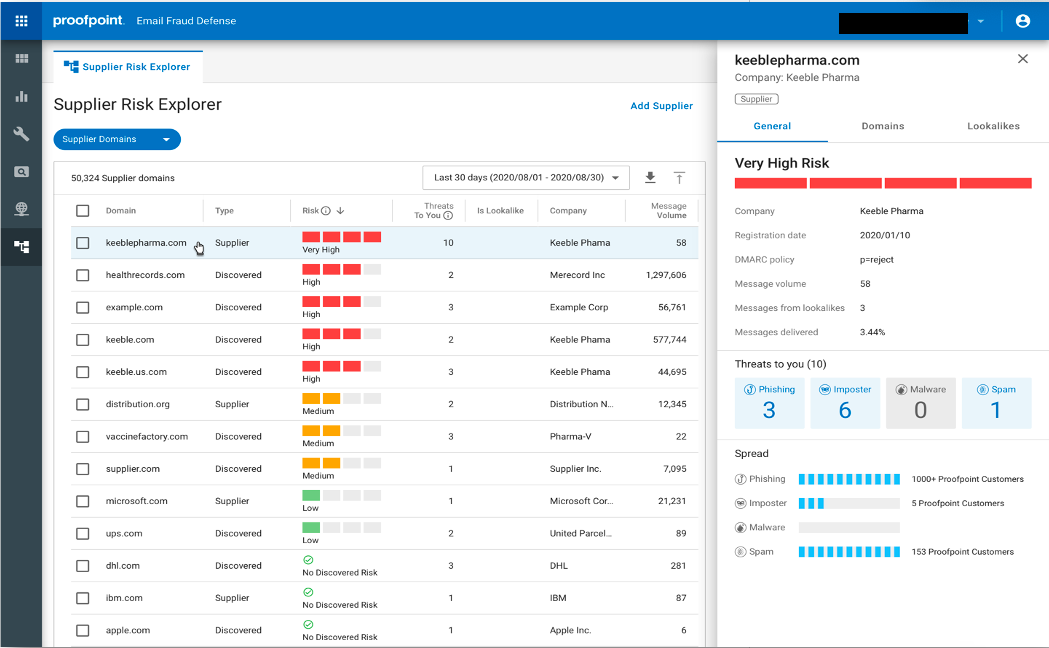
Figure 1: Supplier Risk Explorer identifies supplier domains and provides visibility into which suppliers pose risk to your organization.
Drilling Down into Supplier Domains
Supplier Risk Explorer unveils threats from impersonated and compromised suppliers. It identifies the malicious lookalikes of your suppliers’ domains, which is a common business email compromise (BEC) tactic. It shows the registration date of a supplier domain, which is an indicator of newly registered malicious lookalikes of supplier domain. It also validates the DMARC record of each domain. If a supplier domain is at P= reject, it won’t be vulnerable to domain spoofing.
Supplier Risk Explorer consumes and analyzes threat feeds from Proofpoint’s advanced email protection where our detection engines accurately identify and classify threats. With this shared threat intelligence, Supplier Risk Explorer shows you the count of unique threats sent from supplier domains, including phishing, impostor threats, malware, and spam. It also provides visibility into the threat spread— how many Proofpoint customers have also seen this threat. This insight indicates the severity and the prevalence of the threat, so you can better understand and communicate the risk. Your security analysts can automatically drill down into threat details in the Proofpoint Targeted Attack Protection dashboard, where they can investigate the threat actor, attack techniques, intended users and more.
Fraudsters are turning your suppliers against you by impersonating them or compromising their email accounts. Supplier Risk Explorer provides you with a supplier-centric view of threats targeting your users, so you know which suppliers are posing risk to your organization.
To learn more about how Proofpoint protects against supplier invoicing fraud scams, check out our blogpost: Understanding BEC Scams: Supplier Invoicing Fraud. To find out how prepared your organization is to combat email fraud, take our BEC readiness assessment here.
Subscribe to the Proofpoint Blog

