Many organizations are turning to a new mechanism to deliver customer care: social media. A preferred communication channel for many consumers, social media provides a low-cost model for the business to respond to inquiries. However, any time a communication link between a business and consumers appears, bad actors and criminals look for ways to take advantage of it. Social is no exception, and Proofpoint Nexgate researchers increasingly see hackers, scammers and pranksters use fraudulent customer care accounts to phish credentials, steal personally identifiable information (PII) and compromise brand reputations.
Bank Account Credential Phishing
One of the most significant attacks we see employs fake retail banking customer service accounts to phish bank account credentials. Here’s how it works…
-
A customer tweets a question (for example. “I lost my lost password”) to a bank’s Twitter customer service account – for example @MajorBankHelp.
-
An attacker monitoring @MajorBankHelp sees the question and tweets a "response" directly to the customer from a fake twitter account with a slightly different name. For example, the fake name might be @MajorBank_Help. The account appears otherwise identical (logo, images, etc.) to the real account. Often attackers target after-hours support inquiries in order to engage before actual representatives see the request.
-
The attacker’s tweet includes a link to a bogus website asking the customer to login to resolve their issue (e.g. reset their password, etc.). When the customer logs in to the bogus site, the attacker captures credentials to the customer’s actual bank account.
This scheme enables attackers to access customer account data without the trouble of penetrating bank infrastructure, nor even of delivering a phishing email to the bank’s customer. Why bother hacking through layers of security controls or sending thousands of emails when you can steal the same data by asking a known customer to hand it over?
Hijacking the Conversation
In the example above, the attacker tweets directly to the customer from the fake account to effectively hijack the conversation. Once this has occurred, the bank has zero visibility into the scam until they hear about it later from the victim.
Given that the bank has no visibility, how can the bank’s customers detect the scam on their own? It’s not easy. Consider the legitimate social media support tweets below. All are direct tweets from the brand to a consumer in response to an inquiry – exactly as observed in the banking credential phishing scheme.
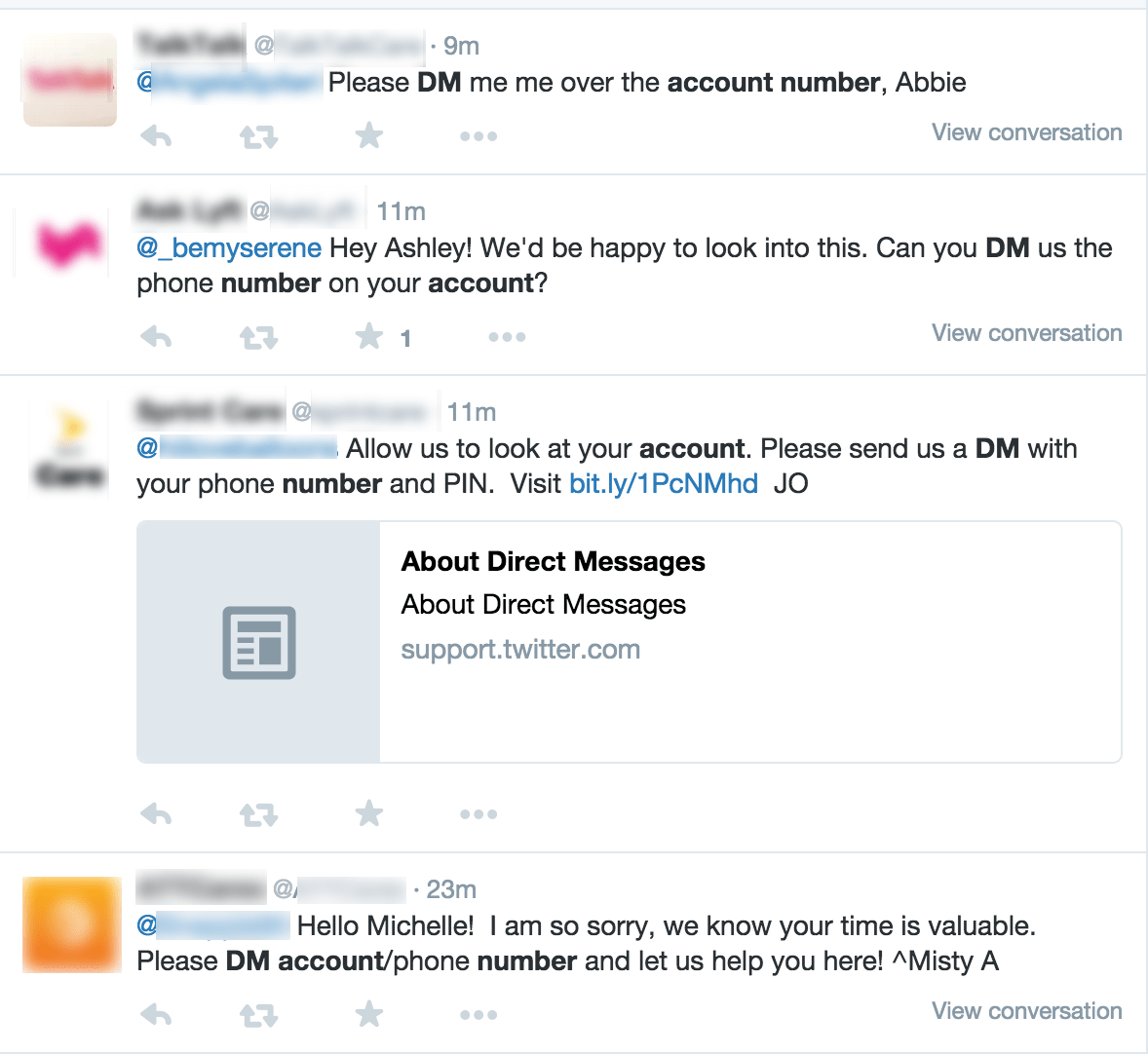
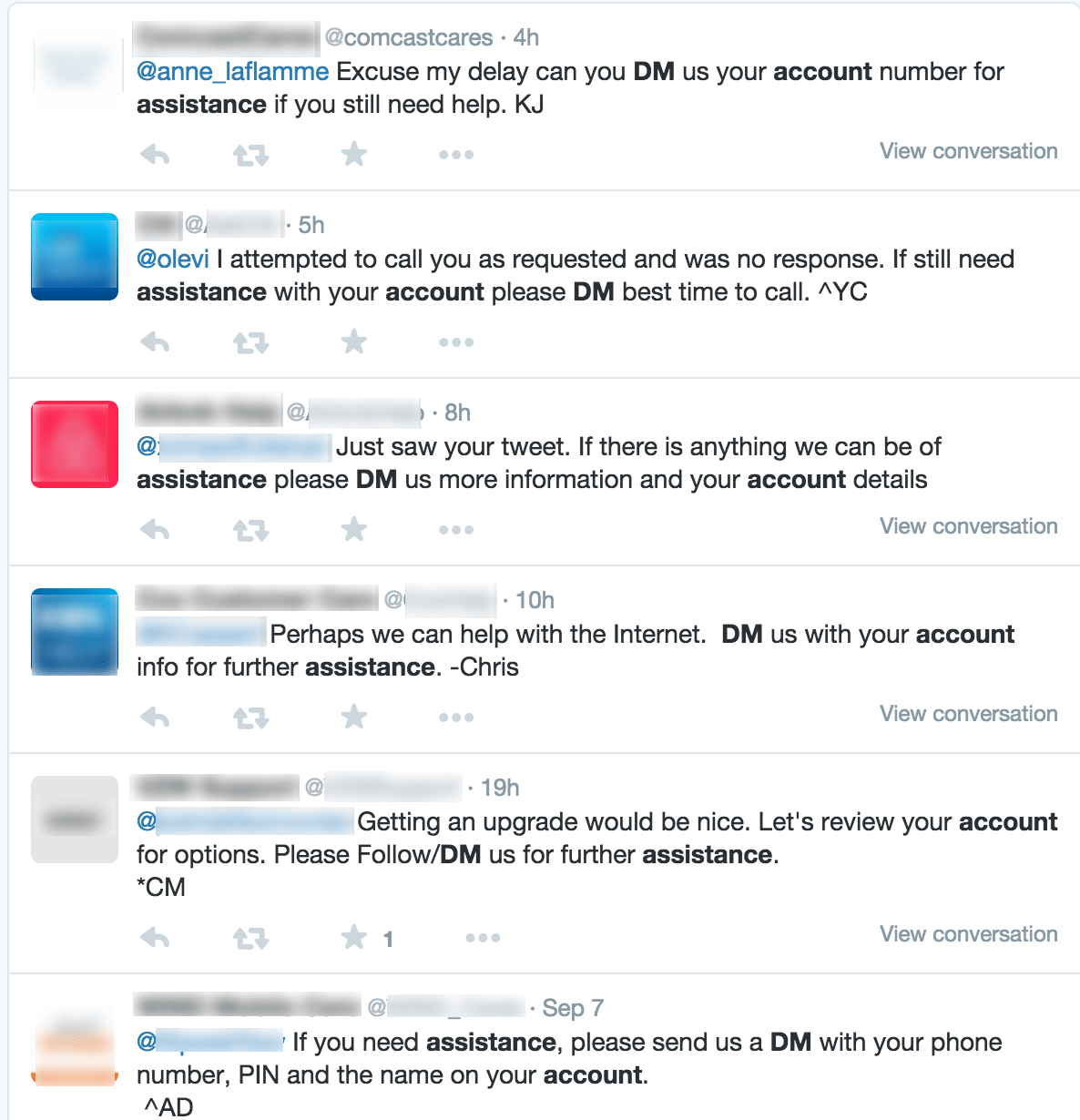
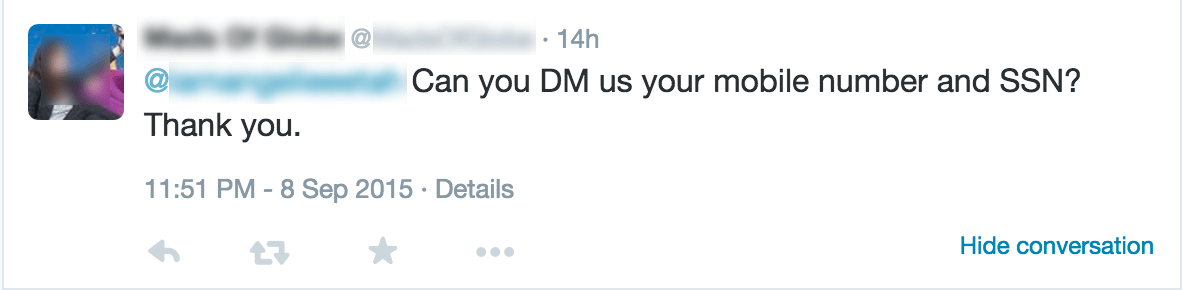
In each case, a legitimate brand is requesting that the customer use direct messaging (DM) to provide the support agent with account information - even social security numbers are requested! How would a customer know if these tweets were fake? In order to impersonate any of these brands and send the same message or send a link to phishing site, an attacker need simply:
-
Create an account with a slight name change (e.g. change BankHelp to Bank_Help)
-
Copy the logo from a web page into the account profile.
That can be done in five minutes at zero cost. If you made a support request, would you notice an additional underscore in a follow-up tweet? Most would not.
The Power of Social Context
Fraudulent customer care accounts highlight the use of social media context to craft attack schemes that are far more convincing than similar email-borne threats. In this case, the attacker gathered detailed context in the form of a specific inquiry, from a specific customer, to a specific bank. That context is then applied to craft a highly convincing phishing lure that the target expects to receive, appears legitimate, and has incentive to act upon (i.e., the customer wants their password reset). Conversely, a generic email scheme sends customized but still generic phishing emails to random consumers, with an offer they do not expect, from a bank where they may or may not have an account! What’s more, most consumers have been warned many times by their bank to ignore unexpected email correspondence. Social media context clearly gives attackers an edge.
What about “Verified” Accounts?
Twitter provides verification of accounts to establish the authenticity of identities of individuals and brands on Twitter. Verified accounts are marked on their main Twitter page with a blue check mark logo next to their account name. Although Twitter verification has potential to combat fraudulent accounts, it is by no means foolproof for several reasons:
-
The “verified” logo does not appear in the tweets themselves. A consumer receiving a tweet in response to an inquiry will not see a verified logo, nor notice the lack of a logo.
-
Many consumers have no idea what the verified logo means.
-
Fraudulent accounts often fake verification by including the logo in their profile or background images. Even consumers who recognize the logo do not recognize that the logo is not in the proper location.
Phishing, Malware, Knock-Offs, Pranks, and More
Bank account credential phishing is just the tip of the iceberg when it comes to fraudulent accounts. We find thousands of fraudulent social media accounts that support malware distribution, knock-off product sales, pirated software, and even brand pranks. Check out this and this to read about how pranksters are using fake customer care accounts to poke fun at brands and customers. We also recommend reading our Fortune 100 threat report for more information on fraudulent social media accounts.
What to Do?
Here are some recommended strategies for organizations seeking to mitigate risk associated with fraudulent social media accounts in general and with fraudulent customer service accounts specifically.
-
Define the group within your organization responsible for identifying and addressing fraudulent accounts. This may be a social media team, but it could also be a security team.
-
Monitor social networks for fraudulent accounts. Automated tools can continuously scan for suspicious accounts and send alerts when they appear.
-
Establish a process for reporting fake accounts to social network platforms (Twitter, Facebook, etc.) to request their removal.
-
Consider asking customers to submit inquiries only during posted social media support hours. This can reduce the window of time available for bad actors to carry out their scams.

