November 17 presented an interesting variation in Dridex and Shifu distribution techniques, as Proofpoint researchers observed both spreading via compromised websites that led to exploit kits. In these cases, the same compromised web site could infect a user with one Trojan or the other depending on the user’s geographical location.
- Day with Dridex and Shifu spreading via RIG and Angler exploit kits, respectively, rather than via spam
- Dridex rarely spreads via exploit kits
- Shifu routinely spread via exploit kits [1]
No Dridex/Shifu Email Spam on November 17
Proofpoint normally observes one or two Dridex document email spam campaigns per day on weekdays. For example, the following Dridex campaigns were detected over a single five-day span in the month of November.
- November 13 (Fri): Dridex 220, 122
- November 12 (Thu): Dridex 220, 301
- November 11 (Wed): Dridex 220
- November 10 (Tue): Dridex 220, 120
- November 09 (Mon): Dridex 220, 120
Email campaigns distributing Dridex have been a staple of 2015 (with the exception of September [2]), and November in particular has been characterized by a significant increase in the daily email volume of these campaigns. Thus the complete absence of Dridex document spam campaigns on November 17, while not necessarily a sign of things to come, is nonetheless unusual enough to merit noting. The Shifu Trojan, on the other hand, is routinely observed spreading via exploit kits in addition to document spam.
Dridex and Shifu Spreading via Exploit Kits
Proofpoint detected infected websites (most likely malvertising in adult websites) that use a traffic direction system (TDS) to redirect users to exploit kits that serve different payloads, depending on the geographical location of the user. The TDS redirect from the infected adult site appears with the URI path “/492k” in Figures 1 and 3 below.
Users coming to the infected site from most IP addresses, such as in the US or UK, are redirected by the infected adult site to RIG exploit kit and end up infected with Dridex 121 (Fig. 1). A recent analysis of RIG EK shows that it includes exploits for Adobe Flash and Microsoft Internet Explorer [3]. The installed Dridex Trojan (md5: 60c1ca4fbcb10094ab7baa0eb725ac6d or 958720c259356f8ba5b1220001f7eddd) with a botnet ID of 121, traditionally shares command and control (C2) infrastructure with botnet IDs 120 and 122, which we see being distributed via malicious document email campaigns. Interestingly, the loader C2 IP addresses (Fig. 2) are all currently unavailable and are the same IPs as used by the randomized Dridex 121 document spam campaign on November 3, 2015 (Example document MD5: a8632ae3cad384d3979302d4aab0b3cc).
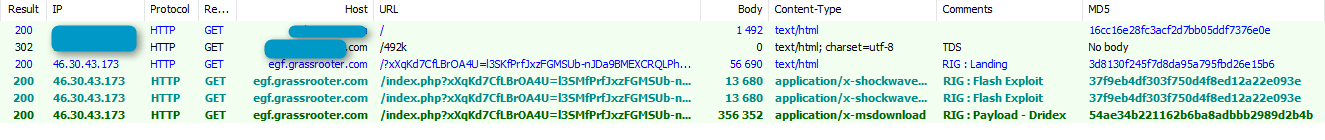 Figure1: Initial TDS redirect and RIG EK landing from a US IP address
Figure1: Initial TDS redirect and RIG EK landing from a US IP address
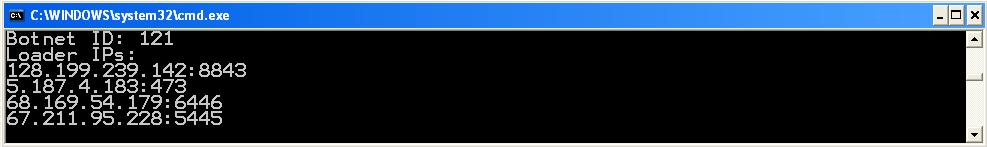
Figure 2: Dridex Loader configuration
Alternately, users from Japanese IP addresses are instead redirected by the infected adult site to Angler EK, which includes exploits for Flash and Internet Explorer [4]. If the user system is exploitable, Angler loads the Bedep Trojan in memory, which in turn downloads Shifu, Tinyloader C and two other payloads. The Shifu banking Trojan (md5: 5af66a00733254e93bc6c499eff9cbc1) targets customers of Japanese banks and uses the following C2 URLs:
[hxxps://asianonlinestatistics[.]com/news/userlogin.php]
[hxxps://91.233.117[.]113/news/userlogin.php]
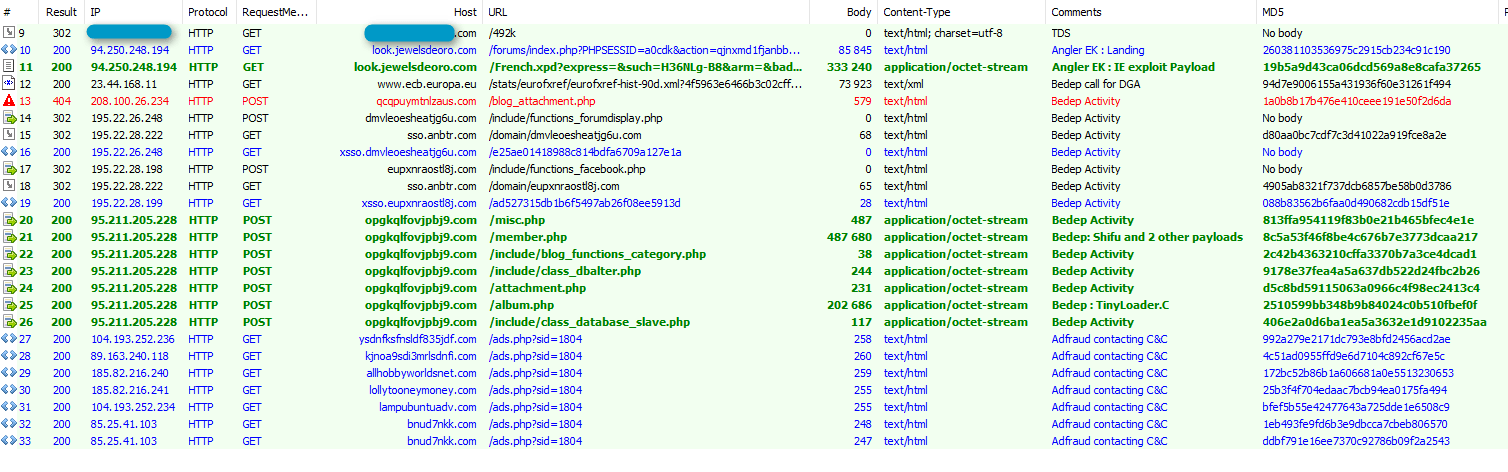
Figure 3: Initial TDS redirect and Angler EK landing from a Japanese IP address
Previous Known Instances of Dridex using Exploit Kits to Spread
As noted above, Dridex rarely spreads via exploit kits. Some rare examples of this behavior include spreading via Angler EK in 2014 and via malvertising in Poland on May 2, 2015. The diagram below (Fig. 4) shows the Angler exploit kit calls at the domain name.allbestreets[.]xyz, and following that the Dridex call to IP 46.36.217[.]227:3443. This IP address was used throughout the first part of May as Loader C2 IP address by Dridex botnet id 120.
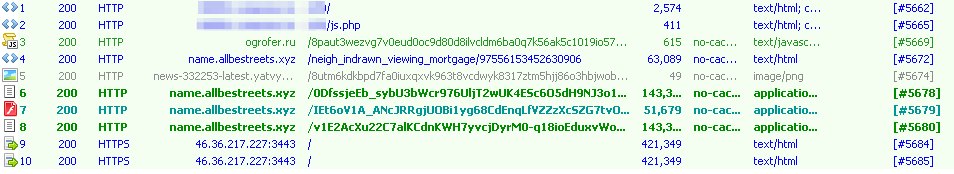
Figure 4: Angler EK spreading Dridex on May 2, 2015
Conclusion
Since their return to operation at the beginning of October, the threat actors behind these malicious document attachment campaigns have increased the volume and the variety of their campaigns. Even if it only lasted for a single day, the apparent substitution of Dridex spam with distribution via malvertising and EK shows that the Dridex threat actors increasing their efforts to vary their delivery and payloads, including leveraging a TDS to tailor the payload to the region of the victim. While it is too soon to claim that this is the start of a new trend for these actors, it does show these actors can adapt quickly and that organizations must be able to detect and stop these threats through a variety of vectors.
References
[1] http://malware.dontneedcoffee.com/2015/09/shifu-great-britain.html
[2] https://www.proofpoint.com/us/threat-insight/post/Not-Yet-Dead
[3] Relevant RIG EK exploits:
- CVE-2015-2419 - http://malware.dontneedcoffee.com/2015/08/cve-2014-2419-internet-explorer
- CVE-2015-5122 - http://malware.dontneedcoffee.com/2015/07/cve-2015-5122-hackingteam-0d-two-flash.html
- CVE-2014-6332 - http://malware.dontneedcoffee.com/2014/11/cve-2014-6332.html
[4] Relevant Angler EK exploits:
- CVE-2015-2419 - https://www.fireeye.com/blog/threat-research/2015/08/cve-2015-2419_inte.html
- CVE-2014-6332 - http://malware.dontneedcoffee.com/2014/11/cve-2014-6332.html
- CVE-2015-7645 - http://malware.dontneedcoffee.com/2015/10/cve-2015-7645.html
- CVE-2015-5560 - http://malware.dontneedcoffee.com/2015/08/cve-2015-flash-player-up-to-1800209-and.html
- CVE-2015-5122 - http://malware.dontneedcoffee.com/2015/07/cve-2015-5122-hackingteam-0d-two-flash.html
IOCs
|
Value |
Type |
|
60c1ca4fbcb10094ab7baa0eb725ac6d |
Dridex 121 Loader MD5 hash |
|
958720c259356f8ba5b1220001f7eddd |
Dridex 121 Loader MD5 hash |
|
128.199.239[.]142:8843 |
Dridex 121 Loader C2 |
|
5.187.4[.]183:473 |
Dridex 121 Loader C2 |
|
68.169.54[.]179:6446 |
Dridex 121 Loader C2 |
|
67.211.95[.]228:5445 |
Dridex 121 Loader C2 |
|
[hxxp://egf.grassrooter[.]com] |
RIG EK domain |
|
5af66a00733254e93bc6c499eff9cbc1 |
Shifu MD5 hash |
|
[hxxps://asianonlinestatistics[.]com/news/userlogin.php] |
Shifu C2 |
|
[hxxps://91.233.117[.]113/news/userlogin.php] |
Shifu C2 |
|
[hxxp://look.jewelsdeoro[.]com] |
Angler EK domain |

