In a quarter that saw large-scale ransomware outbreaks grabbing headlines, email-based ransomware campaigns quietly continued to target millions of users at organizations around the world. The threat actor behind the largest campaigns of the last two years (TA505) led the way with their mainstays of Dridex and Locky as well as the new Jaff ransomware and other malware previously used in smaller campaigns.
At the same time, other actors engaged in both targeted and large-scale attacks covering a wide range of geographies, verticals, and types of malware. Email fraud continued to evolve and social media remained a breeding ground for varied and effective attacks, while network-based attacks gained significant media attention, reminding businesses of the diverse and destructive tools available to threat actors.
Our latest threat report reviews these and other developments, top security trends, techniques, and recommendations for the second quarter of 2017. Here are our top findings:
Email Trends
In a shift from the first quarter, malicious email campaigns were dramatically larger, often approaching the record-setting campaign sizes we saw in the last half of 2016. The campaigns also used email attachments more often than URLs (Figure 1), another change from Q1.
Despite a 250% increase in malicious message volumes over last quarter, overall volume was still less than half of year-ago levels. However, what the quarter lacked in volume compared to last year it made up for in variety, with new ransomware strains, new attachment types, and a surge of new malware across our customer base.
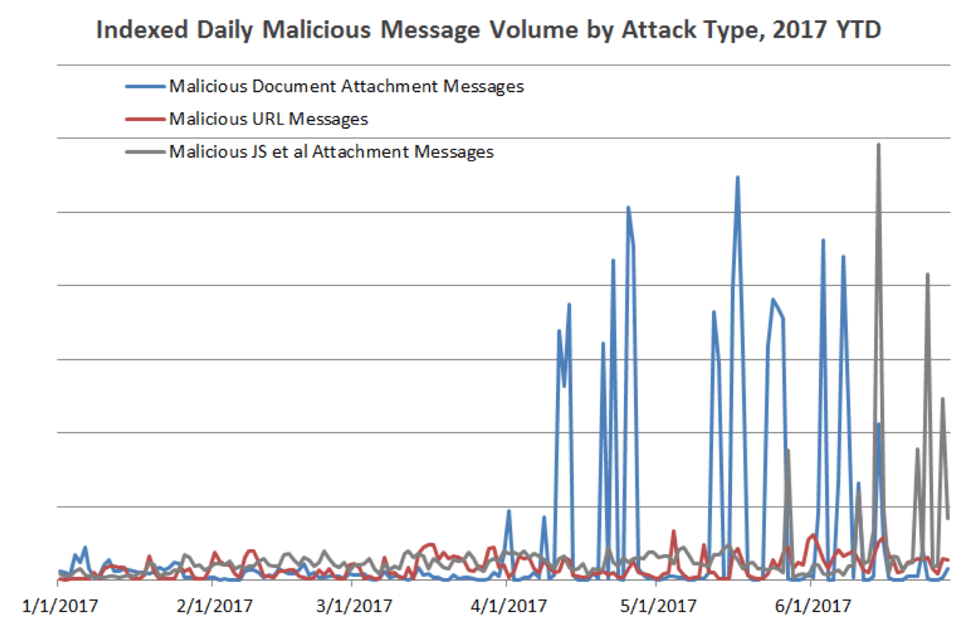
Figure 1: Indexed attack type trend, 180 days ending June 2
Exploit Kits and Web-based Attacks
Exploit kit (EK) activity held steady at dramatically reduced levels compared to what we observed in the first half of 2016. Yet even at these reduced levels of activity, EK threats continued to grow more sophisticated, incorporating smarter targeting and filtering to avoid detection and improve infection rates.
Other network-based attacks made headlines with both WannaCry and a new Petya variant spreading via leaked NSA exploits and backdoors, creating a new class of malware that we dubbed “ransomworms.” Though employing traditional ransomware, the propagation mechanisms suggested that threat actors were more focused on disruption than profit.
Ransomware
Ransomware remains the malware du jour, with 68% of all malicious messages bearing some variant of ransomware (Figure 2). Again, the threat actor we designate as TA505 vastly surpassed all other actors in terms of volume with Locky and Jaff ransomware. The group switched from Locky to Jaff in Q2 and then back to Locky as soon as a decryptor was released, underscoring how easily attackers can adjust to changing conditions and defenses.

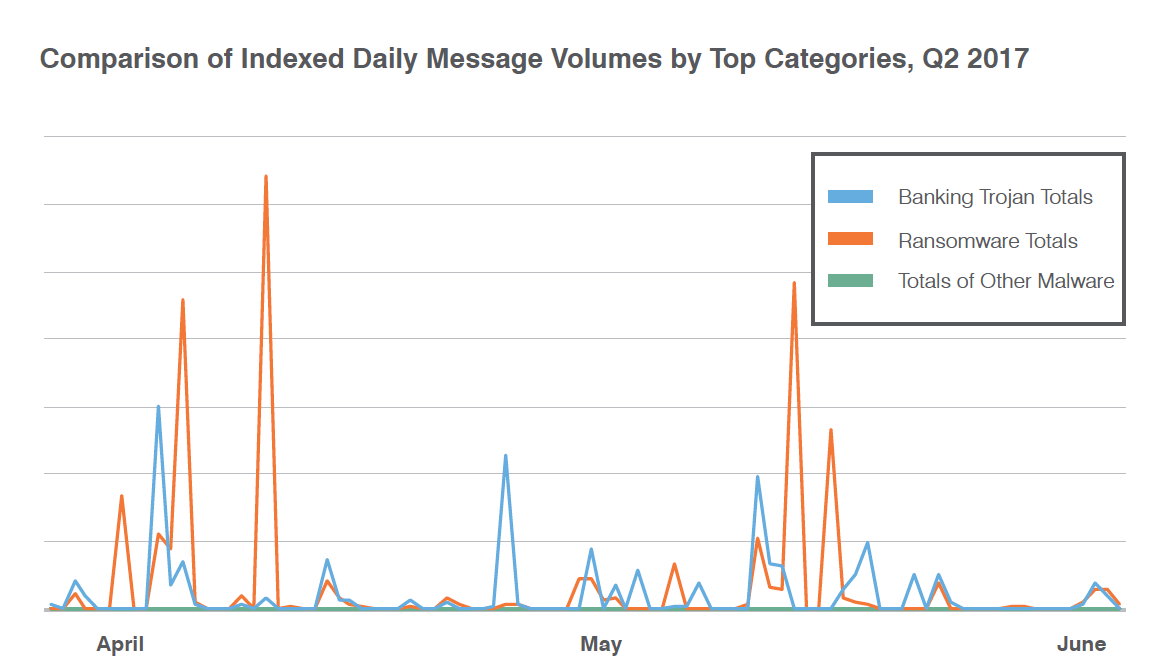
Figure 2: Indexed daily message volumes by top malware categories, April-June 2017
Email Fraud
In a break from past quarters, we are beginning to see a moderate correlation between company size and the likelihood of an email fraud attempt. Our data also suggest that email fraudsters are refining their techniques and targeting businesses more deliberately. While we continue to observe BEC activity across all industries, some appear to be disproportionately targeted, with increased rates of email fraud attempts in Q2 compared to one year ago in technology, telecommunications, automotive, and education sectors.
Social Media
Social media continues to grow as a threat vector. The number of phishing links in social channels grew 70% from the previous quarter, and fake customer-support accounts used for angler phishing jumped 300%. Attackers used compromised apps on social platforms and took advantage of “the human factor” that is so readily exploited in social media.
Proofpoint Recommendations
This report provides insight into the shifting threat landscape that can inform your cybersecurity strategy. Here are our top recommendations for how you can protect your company and brand in the coming months.
Revisit your patching practices
The WannaCry exploit is another example of an advanced threat that takes advantage of legacy systems that are unpatched or poorly configured. As these attacks become more frequent, your best bet is to install the latest patches, validate your security setup and test your backup infrastructure to ensure that you can restore individual machines and company-wide data.
Deploy advanced email gateway analysis
Attackers are constantly finding ways to get around the latest defenses. To detect and stop new attack tools, tactics, and techniques, deploy advanced analysis at the email gateway. Your gateway should draw on advanced threat intelligence to inspect the entire attack chain using static and dynamic techniques. And it should constantly adapt to new threats as they emerge with fast, continual updates.
Use DMARC authentication
DMARC (Domain-based Message Authentication, Reporting and Conformance) authentication can instantly stop email fraud that uses domain spoofing. With DMARC, you can be sure that email uses your domain is really from your organization.
Get visibility into geo-targeted threats
Full visibility within the flow of email can make all the difference in a targeted attack. Visibility means being able to distinguish broad attack campaigns from targeted threats. You should be able to see attacks directed at your executive leadership and other high-value employees so you can prioritize alerts and act on them.
Secure all of your channels from digital fraud
If your organization uses social media to support or collaborate with customers and partners, it’s time to bring your secure your social media channels into the fold of your security program. To protect your brand and the people who trust it, consider solutions that can deliver find and mitigate risks across all the digital channels that matter.
For more details about Q2 threats and trends, download the full report.
Subscribe to the Proofpoint Blog

