Table of Contents
In broad terms, you could think of security awareness training as making sure that individuals understand and follow certain practices to help ensure the security of an organization. From this perspective, security awareness training has been around practically forever, especially considering the need for security in military applications. But for everyday businesses and their employees, security awareness training fortifies the company culture as the first line of defense against elaborate cyber-attacks and socially engineered threats.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we’ll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
What Is Security Awareness Training?
Today, security awareness training emphasizes information security, and especially cybersecurity. Rapid advances in information technology—and parallel innovations by cybercriminals—mean that employees and other end users need regular, specific training on how to safely navigate online to protect their information and that of their employers.
While certain programs take unique approaches, security awareness training is a comprehensive educational process designed to equip employees, business leaders, vendors, and other stakeholders with the knowledge and skills necessary to identify, understand, and mitigate cyber threats. This training fosters a culture of security mindfulness in an organization, ensuring that all individuals are aware of the potential risks associated with digital connectivity and technology use and are prepared to act responsibly to protect the organization’s networks, devices, data, and other assets from cyber-based threats.
The training encompasses a broad range of topics essential for maintaining cybersecurity hygiene, including but not limited to recognizing phishing attempts, understanding the importance of strong password practices, identifying malware, and adhering to company security policies and procedures. Security awareness training may also cover the legal and regulatory aspects of data protection, such as compliance with the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA), where applicable.
To remain effective, security awareness training is an ongoing learning process that continuously adapts to the evolving threat landscape. It includes various educational methods, such as interactive online learning, gamification, phishing simulations, and real-world examples to engage team members with different learning styles and technical aptitudes.
This article is an introduction and deep dive into security awareness training and its importance: why organizations use it, how it has evolved over the years, and how it helps to reduce the threat of cyberattacks and other security breaches. Finally, we’ll introduce some tools for creating an effective security awareness program.
Why Do Organizations Conduct Security Awareness Training?
Cybersecurity awareness training is critical in minimizing the serious cybersecurity threats posed to end users by phishing attacks and social engineering. Key training topics typically include password protection and management, privacy, email/phishing security, web/internet security, and physical and office security.
Organizations recognize that their most significant asset in safeguarding against these threats is also their most vulnerable point: their people. It’s not just about having the most advanced technology or the strictest protocols; it’s about ensuring that every individual within the organization is equipped with the knowledge and awareness to act as a proactive defender against cyber risks. Herein lies the pivotal role of security awareness training—a cornerstone strategy that transforms potential human vulnerabilities into robust pillars of defense.
- Empowering employees: Understanding that even state-of-the-art technical defenses can be circumvented by exploiting human factors, security awareness training aims to fortify this “human firewall.” Through comprehensive education on social engineering tactics, phishing scams, and other methods attackers use to target individuals, such initiatives bolster an employee’s ability to detect and thwart malicious attempts.
- Mitigating risks: The primary goal of instilling security consciousness among staff members is risk reduction. Security-conscious employees are less likely to fall prey to deceptive attacks leading directly or indirectly towards data breaches or compromising sensitive information—thereby maintaining organizational integrity and trust.
- Ensuring regulatory compliance: Beyond protective measures, there’s also a legal impetus behind these programs. Various regulations like GDPR for privacy protection in Europe, HIPAA for health information in the United States, or ISO 27001 international standards require demonstrable efforts towards employee security training—with non-compliance attracting severe financial penalties.
- Cultivating a security-first culture: Engaging educational content does more than inform—it inspires. Empowering employees through engaging sessions designed around active participation rather than passive reception encourages ownership over one’s role in corporate safety, fostering an environment wherein vigilance becomes a second-nature collective ethos across the enterprise.
- Financial and reputational preservation: Preemptive education is cost-effective insurance against potential future crises. Averting incidents before they occur eliminates the need for costly recovery operations while preserving a company’s hard-won reputation and market stakeholder confidence.
- Enhancing visibility and fostering improvement: Security training platforms offer valuable reporting and analytics features, which provide deep insights into user behavior and risk areas. This data-driven approach allows for identifying high-risk individuals or departments, facilitating targeted interventions that bolster overall security posture.
In the Aberdeen Group’s report, “Security Awareness Training: Small Investment, Large Reduction in Risk,” researchers conducted a workshop with enterprise security leaders to unveil why they invest in security awareness and training. They found that:
- 91% use security awareness to reduce cybersecurity risk related to user behavior
- 64% use it to change user behavior
- 61% use it to address regulatory requirements
- 55% use it to comply with internal policies
As these statistics suggest, some organizations use security awareness training simply because they must comply with external or internal requirements. But this training also makes financial sense. According to the report, “An incremental investment in security awareness training results in a median reduction in the annualized risk of phishing attacks of about 50%, and a median annual return on investment of about 5 times.”
Security Awareness and Education Platform
Key features and benefits
The Evolution of Security Awareness Training
While the core concepts of cybersecurity awareness training aren’t new, they have reached mainstream consciousness relatively recently. One indication of its emergence was the 2004 launch of National Cybersecurity Awareness Month. The initiative, by the National Cybersecurity Alliance and the US Department of Homeland Security, was intended to help people stay safer and more secure online, encouraging such practices as regularly updating antivirus software.
Since then, the annual awareness month has inspired similar events in other countries, expanded its themes and content, and drawn increased participation across industries and government, as well as universities, nonprofits, and the general public.

The focus, methods, and effectiveness of security awareness training have undergone significant changes over the years. Back in 2004, most programs were driven by the need for compliance—simply meeting regulatory requirements. Today, that focus has shifted to seeing cybersecurity awareness training as a means to manage and mitigate organizational risk.
Along the way, training methods themselves have matured. In 2004, the dominant paradigm was for annual presentations, either as in-person training sessions or long-form computer-based training. Unfortunately, these lengthy, infrequent sessions do not result in good knowledge retention. A gradual shift toward short, focused training on individual topics represented an improvement, but these trainings were still presented infrequently, which allowed knowledge to dissipate over time.
Around 2014, security awareness training began shifting toward continuous education and improvement, in which a program includes ongoing cycles of assessments and training. The latest developments have been “just-in-time” and in-context training, which adds the ability to launch training in response to an end-user exhibiting poor cybersecurity behavior, such as unsafe web browsing.
Security Awareness Modules, Videos, and Materials
Change behavior to reduce risk
Tools for Training End Users
Today, infosec professionals use a variety of tools to train end users, as can be seen in Proofpoint’s State of the Phish™ Report. The dominant tool—and one that continues to grow in popularity—is computer-based awareness training.
- 79% use computer-based awareness training
- 68% use phishing simulation exercises
- 46% use awareness campaigns (videos and posters)
- 45% use in-person security awareness training
- 38% use monthly notifications or newsletters
Well-designed training programs often use several of these tools. Equally important is deploying these tools systematically, allowing you to track and measure progress over time.

At Proofpoint, we’ve created highly effective training solutions utilizing our Continuous Training Methodology based on Learning Science Principles that engage the learner and change behavior.
Carnegie Mellon University’s research determined how we employ Learning Science Principles was proven effective.
5 Principles of a Positive Anti-Phishing Behavior Management Program
Fostering a culture that embraces proactive defenses against phishing attacks is essential in reinforcing an organization’s security posture. Building an anti-phishing behavior management program not only secures organizational assets but also cultivates an environment where employees feel empowered and engaged. Here are five principles to guide the development of such a program, ensuring it resonates with leadership and becomes embraced by staff.
- Champion education over punishment: Shift the narrative from penalizing mistakes to celebrating learning opportunities. By framing security awareness training as a tool for personal and professional growth, organizations can dismantle barriers to engagement. Highlight stories of how knowledge gained through these programs has helped individuals both within and outside work contexts—transforming potential apprehension into enthusiasm for participating.
- Encourage leadership advocacy: Secure buy-in from top executives by demonstrating how positive reinforcement strategies align with broader business goals like reducing risk and enhancing corporate reputation. When leaders actively promote and participate in anti-phishing initiatives, their endorsement serves as a powerful motivator for wider acceptance across all levels of the organization.
- Personalize the learning experience: Recognize that one size does not fit all in education. Tailor training content to meet diverse learning styles and job roles within your company as relevance breeds interest, which fosters better retention rates. Incorporating interactive elements such as gamification or real-life simulations can transform routine exercises into engaging challenges that stimulate genuine interest while reinforcing key concepts about cyber vigilance.
- Promote open dialogue: Establish a culture where feedback on the training program is not just encouraged but valued. Allowing participants to express their thoughts and concerns enables a cycle of continuous improvement that ensures materials remain engaging and relevant. Furthermore, creating forums for employees to share experiences with phishing attempts fosters a sense of community and collective responsibility toward safeguarding against digital threats.
- Focus on long-term behavioral change: Instead of seeking quick fixes, aim to develop enduring security habits that require ongoing effort and reinforcement. Acknowledge and celebrate small victories as part of the journey towards a more secure mindset. This approach ensures that security awareness evolves from being seen as an external imposition to becoming an integral part of employees’ daily routines, leading to a profound cultural shift within the organization.
By embracing these five principles, organizations can craft an anti-phishing behavior management program that not only addresses immediate cybersecurity threats but also fosters a lasting environment of vigilance and empowerment.
Effectiveness of Security Awareness Training
Our own case studies and Results Snapshots have shown persuasive results:
95%
Over a two-year period, a financial institution recorded a 95% reduction in malware and viruses and a greater awareness of cybersecurity threats.
90%
A college in the Northeastern US reported a significant reduction in malware and viruses, a 90% reduction in successful phishing attacks, significantly fewer support requests, an increase in the number of users reporting incidents and attacks, and a greater awareness of security issues.
89%
An employee benefits organization realized more than an 89% reduction in phishing susceptibility by utilizing our assessment and education modules as core components of their security awareness and training program.
80%
Security awareness training helped city government employees reduce average click rates by 80% in one year and avoid a sophisticated wire transfer fraud attack.
Evaluate
Measure program success
Creating a Security Awareness Training Program
Training employees to increase an organization’s security posture versus engaging cybersecurity experts requires a unique strategy. Users don’t have the expertise, so they need information presented to them in an engaging way that helps them visualize and understand phishing.
Your security awareness program should include several features:
- Threat-driven content: To optimize its effectiveness, security awareness training must be tailored to the current threat landscape, ensuring that users are prepared for real-world threats.
- Real-time reporting: The training platform should provide real-time reporting on simulated phishing tests and real-world threats, allowing organizations to monitor their security posture and identify areas for improvement.
- Customizable content: Advanced programs offer a wide variety of training modules in multiple languages, enabling organizations to tailor the content to their specific needs and user demographics.
- Adaptive learning framework: Security training programs should utilize an adaptive learning framework that delivers security education on a progressive scale, from the basics to advanced concepts. It can further be tailored to individual factors like role, learning style, competency, vulnerability level, and language.
- Microlearning: Training delivered in digestible modules with concise and specific learning objectives, making it easy for users to digest and retain the information.
- Continuous improvement: A comprehensive approach to security awareness includes periodic reassessments to track progress and identify areas of concern, allowing organizations to refine their cybersecurity awareness and education plan.
- Guided Targeted Attack Protection (TAP) Training: This advanced feature allows organizations to run targeted training programs based on actual risks in their environment, focusing on specific threat types like email impersonation, credential phishing, and ransomware.
While some organizations assemble their own strategic approach, these fundamental features are inherent in Proofpoint’s Security Awareness Training programs. Ultimately, how you organize and develop security training will determine its effectiveness. You need a strategy for how the content is written and organized.
An example approach is a Contextual Learning Model, which emphasizes relevance, engagement, and practical application. This model moves away from strict divisions between formal, informal, and experiential learning to focus more holistically on how content can be integrated into an employee’s daily workflow and decision-making processes. Here’s how it breaks down:
- Integrated Learning (40%): This component is incorporated into employees’ day-to-day activities. By embedding microlearning sessions directly into their workflow—such as brief quizzes after accessing certain company systems or short video tips before using specific software tools—training becomes less intrusive and more relevant.
- Scenario-Based Engagement (30%): Instead of traditional lectures or presentations, this training relies heavily on immersive simulations and interactive scenarios that reflect real-life situations employees might face. These scenarios are designed for individual participation and to encourage team-based problem-solving exercises that foster collaboration while enhancing understanding.
- Interactive Platforms (20%): Leveraging modern educational technology platforms can transform passive learning into active exploration. Features like gamified elements for achieving cybersecurity milestones or forums for discussing recent phishing attempts among peers create a vibrant community around cybersecurity education.
- Reflective Practice & Feedback Loops (10%): Encouraging employees to reflect upon what they’ve learned through regular feedback mechanisms—such as surveys or discussion groups—and applying these insights in practice helps cement knowledge while identifying areas needing further clarification or reinforcement.
Proofpoint offers a full suite of products for your security awareness and training program, from knowledge assessments and phishing simulations to interactive training, powerful reports, and easy-to-use dashboards.
Anti-Phishing Training Suite
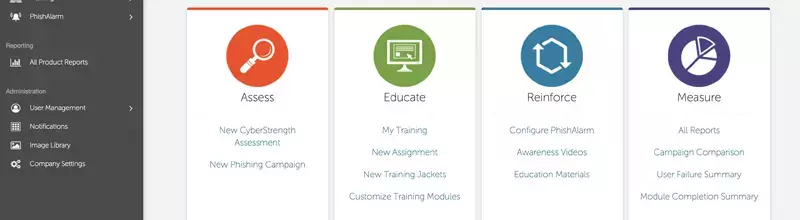
Our customers have used our Anti-Phishing Training Suite and our Continuous Training Methodology to reduce successful phishing attacks and malware infections by up to 90%. Make our unique, four-step Assess, Educate, Reinforce, Measure approach the foundation of your phishing awareness training program.
Simulated Phishing Attacks
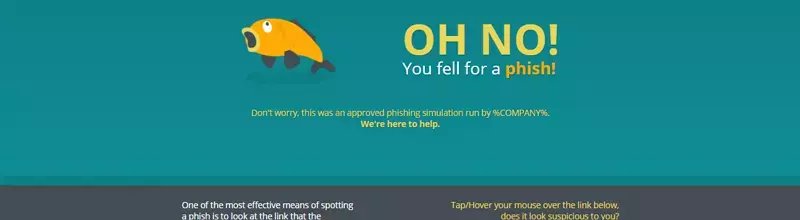
Quickly and effectively assess how susceptible your employees are to phishing and spear phishing attacks with our ThreatSim® Phishing Simulations. End users who fall for simulated phishing attacks are automatically presented with a Teachable Moment. This “just-in-time” guidance lets users know what they did wrong and offers tips to help them avoid future threats.
Security Awareness Training
We recommend that your security awareness training program include organization-wide phishing education as well as targeted anti-phishing training. Our unique approach and interactive training modules help you deliver effective cybersecurity education in a flexible, on-demand format that minimizes disruption to daily work routines.
PhishAlarm® Email Reporting Tool
Reinforcing best practices is critical to improving retention. Our PhishAlarm® email reporting tool enables end users to report a suspected phishing email with a single mouse click, reinforcing positive behaviors. Our optional PhishAlarm Analyzer email prioritization tool maximizes PhishAlarm’s capabilities and streamlines response and remediation efforts on reported emails.
4 Layers of Security
Implementing a multi-layered approach is crucial for an effective defense against cyber threats. This holistic strategy encompasses four essential layers that work together to enhance organizational security:
1. Human Layer
Often considered the first and most critical line of defense, this layer focuses on educating employees about cybersecurity best practices, phishing scams, password policies, and other potential cyber risks. The human layer emphasizes creating a culture of security where every team member is empowered with the knowledge to act as a vigilant protector of their organization’s digital assets.
2. Policy Layer
This layer involves developing comprehensive security policies defining acceptable resource use, data protection guidelines, incident response plans, and more. These policies provide a framework for behavior within the organization and ensure clear procedures are in place for maintaining compliance with regulatory requirements and responding effectively to any breaches or incidents.
3. Technology Layer
The technology layer zeroes in on securing devices and tools integral to an organization’s daily operations. It encompasses deploying robust antivirus software across all endpoints, ensuring that every device—a laptop, desktop, smartphone, or tablet—is fortified against malware and cyber threats. Additionally, this layer includes using secure communication tools for encrypting emails and protecting sensitive information shared online.
4. Infrastructure Layer
At this foundational level lies the backbone of an organization’s digital environment—the networks, servers, VPNs, firewalls, and proxies that facilitate operational functionality while also posing as potential vectors for attack if left unprotected. Strengthening this layer involves meticulous configuration of network defenses such as next-generation firewalls capable of deep packet inspection, deployment of VPN services for secure remote access, and rigorous monitoring and management of server security to prevent unauthorized access or data breaches.
What Differentiates Proofpoint Security Awareness
Because security awareness training works with the human element in cybersecurity, organizations must find’ a company that can connect with users. Proofpoint’s training is developed to empower employees, vendors, and contractors with the information needed to detect and stop phishing attacks. We differentiate ourselves using a number of factors.
- Proven results. Security training has been shown to reduce click rates by up to 50%.
- Real-world examples. Train employees with real-world examples so that they recognize a phishing email more effectively.
- Better compliance. Proofpoint training improves compliance by educating users on proper auditing and record-keeping when working with customer data.
- Engaging for users. All lessons and training courses are created to engage users so that they get the most out of their sessions.
The effectiveness and scope of Proofpoint’s security solutions provide notable capabilities in both pre- and post-threat detection and remediation, along with advanced training that leads to measurable behavioral changes in organizational security practices.
Metric
Statistics
Description
Detection Efficacy Rate
99.99%
Proofpoint detects nearly all threats before they reach user inboxes, ensuring high security.
Advanced Threat Detection
32% more effective than MSFT
Superior in identifying complex threats compared to Microsoft solutions.
Pre-Delivery Protection
Stops threats at the front door
Prevents threats before they are delivered, significantly reducing the risk.
Human Risk Insights
Identifies vulnerable, highly attacked roles
Pinpoints which individuals are targeted most frequently to focus security measures.
Threat Actor Activity Tracking
Provides detailed insights
Monitors and reports on specific threat actors and tactics targeting the organization.
Post-Delivery Threat Remediation
10 seconds or less
Quickly neutralizes threats even after delivery, enhancing incident response.
Behavioral Change Impact
40% reduction in clicks on threats
Significant decrease in risky behavior due to effective training and simulations.
Global Reach
230,000+ organizations
Proofpoint analyzes 3 trillion messages annually across a vast number of organizations.
Metric
Detection Efficacy Rate
Statistics
99.99%
Description
Proofpoint detects nearly all threats before they reach user inboxes, ensuring high security.
Metric
Advanced Threat Detection
Statistics
32% more effective than MSFT
Description
Superior in identifying complex threats compared to Microsoft solutions.
Metric
Pre-Delivery Protection
Statistics
Stops threats at the front door
Description
Prevents threats before they are delivered, significantly reducing the risk.
Metric
Human Risk Insights
Statistics
Identifies vulnerable, highly attacked roles
Description
Pinpoints which individuals are targeted most frequently to focus security measures.
Metric
Threat Actor Activity Tracking
Statistics
Provides detailed insights
Description
Monitors and reports on specific threat actors and tactics targeting the organization.
Metric
Post-Delivery Threat Remediation
Statistics
10 seconds or less
Description
Quickly neutralizes threats even after delivery, enhancing incident response.
Metric
Behavioral Change Impact
Statistics
40% reduction in clicks on threats
Description
Significant decrease in risky behavior due to effective training and simulations.
Metric
Global Reach
Statistics
230,000+ organizations
Description
Proofpoint analyzes 3 trillion messages annually across a vast number of organizations.
FAQs: Security Awareness Training
What Is Security Awareness Training?
Security awareness training is a corporate-wide initiative to help employees identify and avoid cyber-threats in the workplace. It’s a component in effective cybersecurity to stop human errors and insider threats from causing data breaches.
What Are Some Security Awareness Training Best Practices?
Teaching hundreds or thousands of employees with different cybersecurity awareness levels requires a strategic approach. Every organization has their own methods, but it’s important that security awareness training is an ongoing process and curriculum is reviewed and updated frequently to account for changes in the cybersecurity landscape.
What Is the Main Purpose of Security Awareness Training?
Data breaches are expensive, and employees are primary risks for targeted threats. Training employees to detect threats minimizes risk of phishing and ransomware, thus prevents loss of personally identifiable information (PII), intellectual property (IP), revenue, brand reputation, and customer loyalty.
What Are the Benefits of Security Awareness Training?
Empowering employees with security knowledge reduces risk of data breaches, and provides additional benefits. Training employees to identify threats prevents downtime from data breaches, ensures that your organization stays compliant, and improves customer confidence in your brand.
What Should Security Awareness Training Include?
Security awareness training materials include reading modules, videos, on-hand exercises, and testing to ensure effectiveness. The way an organization formats a security awareness training program is unique to their user base, but should be freely accessible to anyone.
How Effective Is Security Awareness Training?
Security awareness training is so effective that it’s now a compliance requirement for the EU’s GDPR. Through the years, organizations have seen a sharp decline in data breaches due to better cybersecurity education.
What Are the Most Important Security Awareness Training Topics?
Any security awareness training should cover common topics such as phishing, password protection, safe social media usage, social engineering, physical security, public Wi-Fi safety, and guidance on working remotely. Your organization should tailor training to cover the biggest threats to your organization's cybersecurity.
How Much Does Security Awareness Training Cost?
Every organization has their own cybersecurity strategy and number of employees. Some employees need more training than others. Proofpoint customizes training material specifically towards your cybersecurity needs. Contact us for pricing of your own security awareness training. If you’re interested in trying us out, request your free security awareness training trial today!