Tycoon 2FA is a phishing-as-a-service (PhaaS) platform that was first seen in August 2023. Like many phish kits, it bypasses multifactor authentication (MFA) protections and poses a significant threat to users. Lately, Tycoon 2FA has been grabbing headlines because of its role in ongoing campaigns designed to target Microsoft 365 and Gmail accounts.
This blog post is a rundown of how these attacks work, how they’re evolving, what they look like in the real world—and how Proofpoint can help.
How it works
Tycoon 2FA operates as an adversary-in-the-middle (AitM) phishing kit. Its primary function is to harvest Microsoft 365 and Gmail session cookies. Attackers use these cookies to circumvent MFA access controls during subsequent authentication. That allows them to gain unauthorized access to a user’s accounts, systems and cloud services—even those that have additional security measures in place.
What’s new
In March 2024, the group behind Tycoon 2FA released an updated version of the kit. This new version boasts enhanced detection evasion capabilities that make it even harder for security systems to identify and block the kit.
Significant alterations to the kit’s JavaScript and HTML code have been implemented to increase its stealthiness and effectiveness. These changes include:
- Obfuscation techniques that scramble the code, making it difficult to understand
- Dynamic code generation that alters the code each time it runs, thereby enabling it to evade signature-based detection systems
Where to find it
The group behind Tycoon 2FA sells ready-to-use phishing pages for Microsoft 365 and Gmail via Telegram, a malicious cloud-based encrypted messaging service. Prices start at $120 for 10 days of access to the service, with variations based on top-level domains (TLDs). This business model broadens the potential pool of attackers because it allows less technically skilled bad actors to launch sophisticated phishing attacks.
What an attack looks like
Tycoon 2FA relies on attacker-controlled infrastructure to host the phishing webpage. Through the use of a “reverse proxy,” the platform allows the interception of victims’ entered credentials. The credentials are then relayed to the legitimate service for a transparent, successful login, prompting MFA requests. The resulting session cookies are relayed back to the threat actors.
The stolen session credentials allow the attackers to bypass a company’s MFA protection if they remain active. This gives them unauthorized access to the user’s account.
Real-world examples
Since December 2023, Proofpoint has observed phishing landing pages that use Tycoon 2FA to facilitate MFA token theft and bypass.
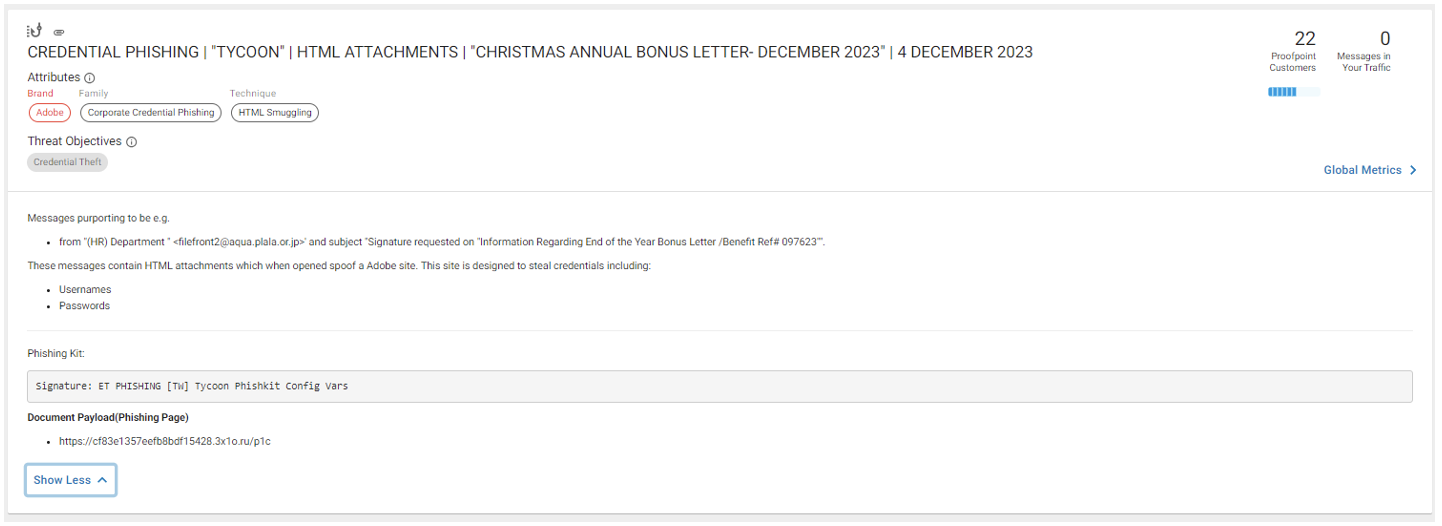
Proofpoint TAP Dashboard campaign snapshot from December campaigns.

A forensics snapshot that showcases our Emerging Threats rules, which detect the Tycoon 2FA landing pages.
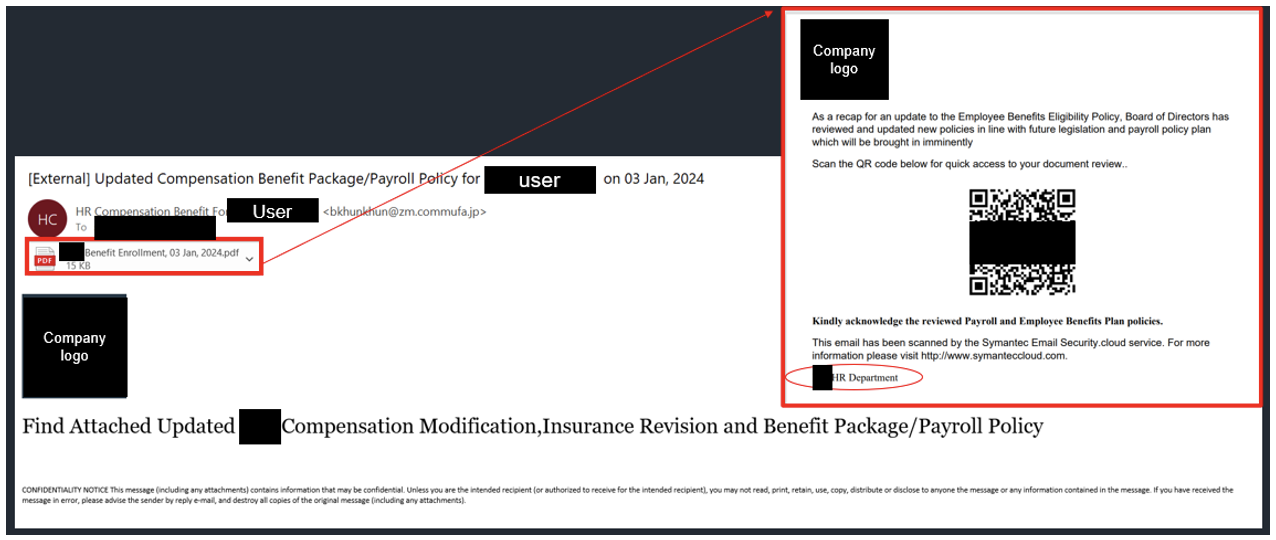
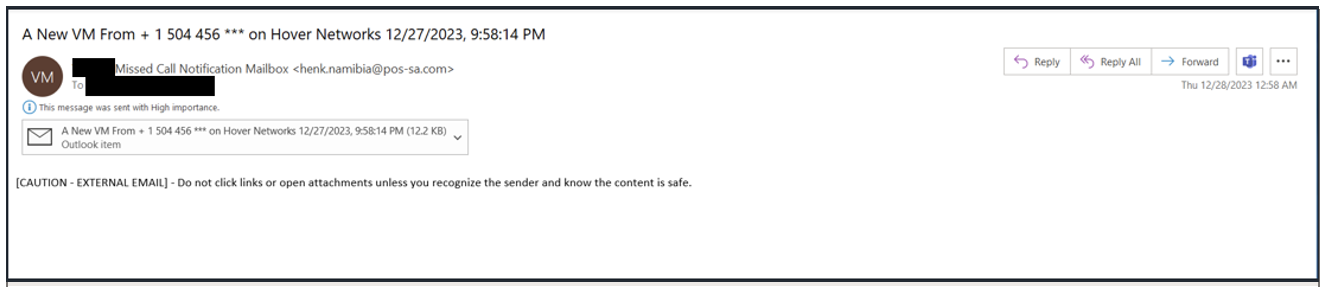
QR code and voicemail lure examples for the Tycoon 2FA threats that were seen in late 2023.
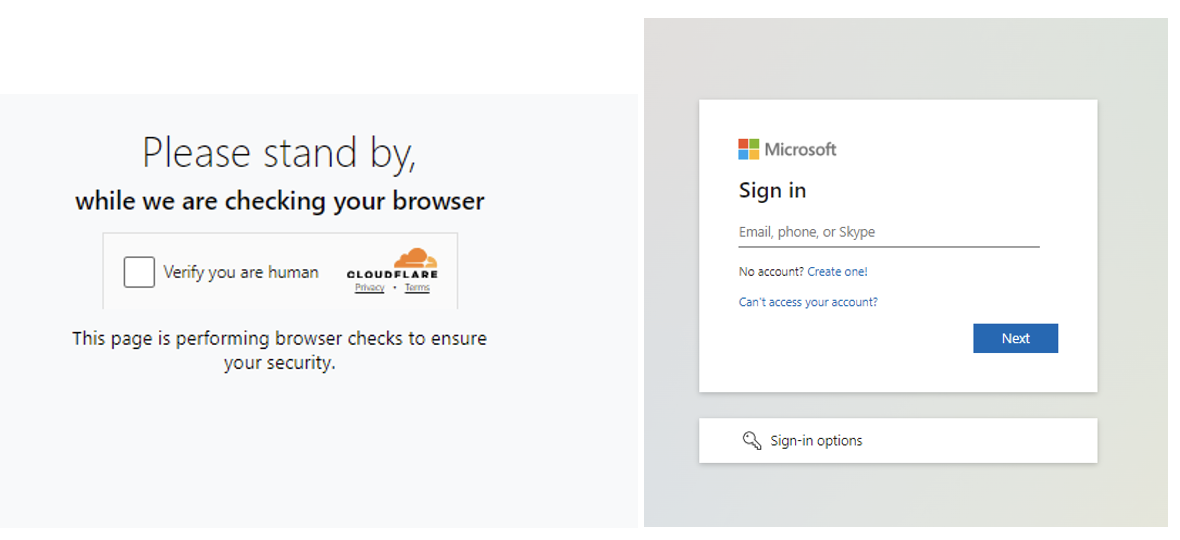
In the next steps of the attack chain, the user is directed to a CAPTCHA landing page and then to a final landing page that the attackers use to harvest credentials.
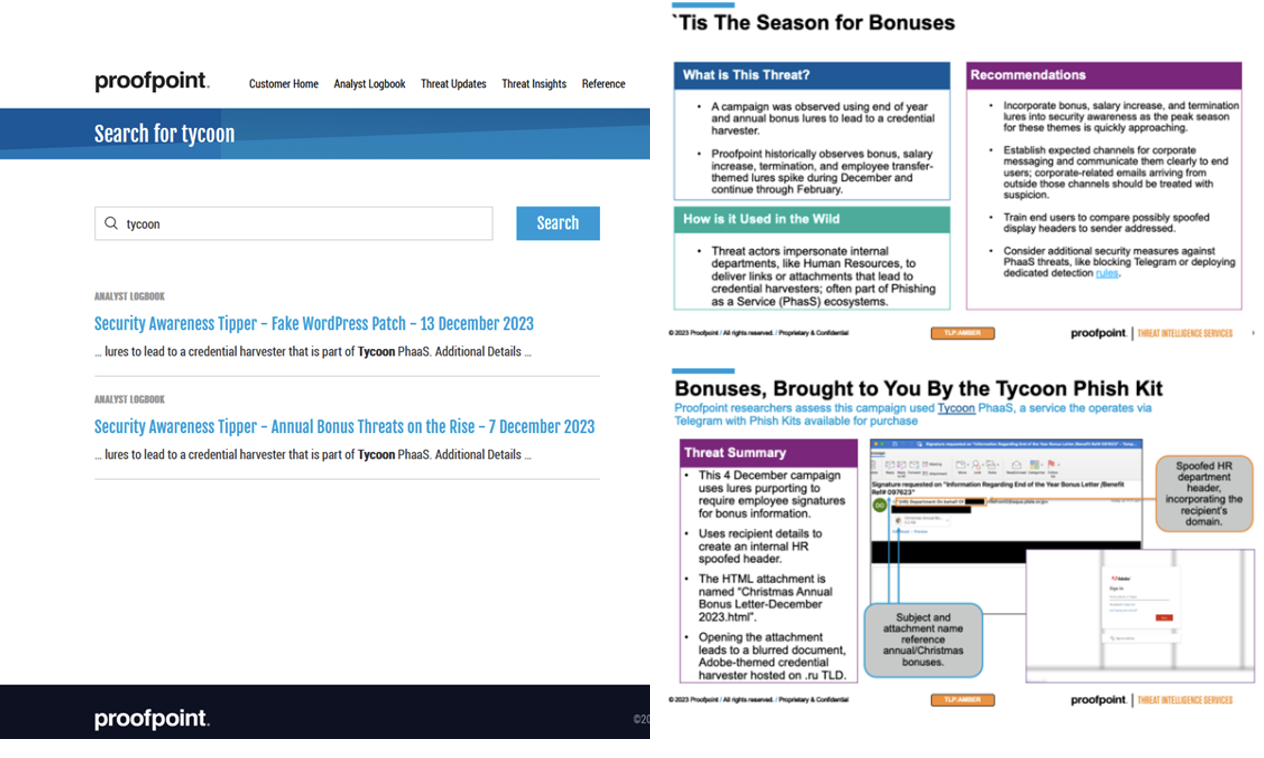
Proofpoint PTIS portal Threat Tippers around Tycoon 2FA phish threats that were curated for security awareness and training teams and end users.
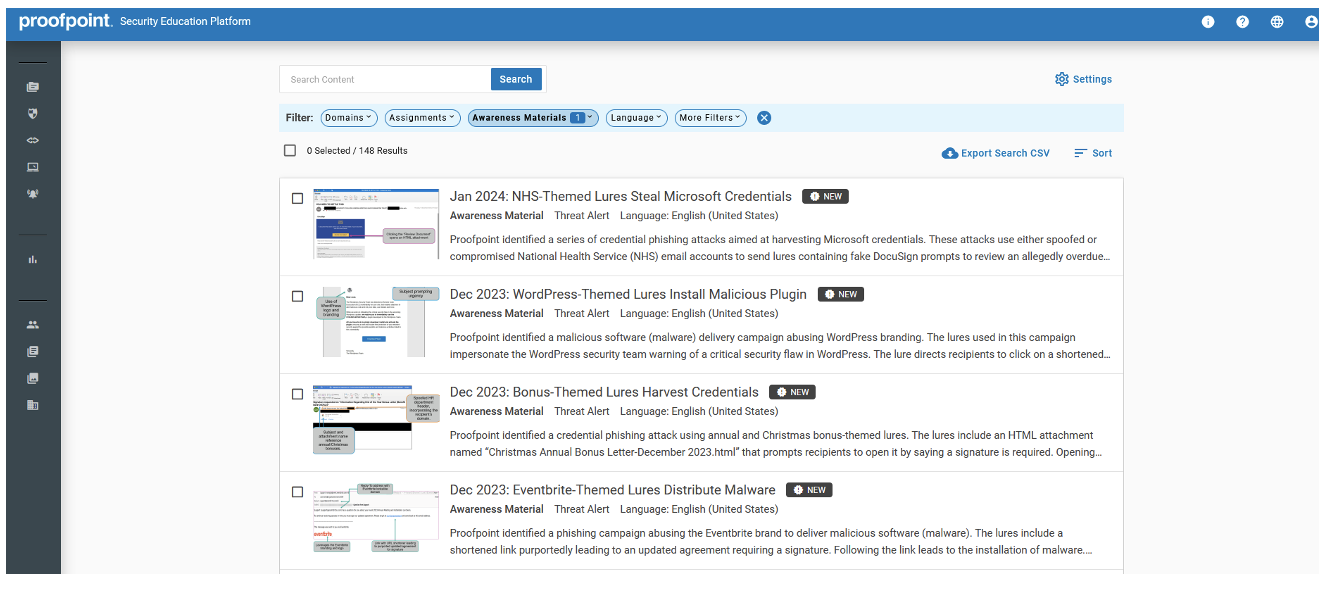
A PSAT portal snapshot that showcases Threat Alerts around Tycoon 2FA phish threats (bonus-themed and WordPress lures).
The lures the attackers use include the following.
- Malicious links in emails to fake authentication landing pages
- Voicemail-themed threats
- Attached PDFs with QR codes that lead to phishing landing pages
These lures are designed to trick users into providing their login credentials and sensitive information.
In the threats Proofpoint has seen, lure themes have frequently been related to company bonuses, payroll increases and bogus WordPress updates. However, it is important to note that since this is PhaaS, multiple actors likely use the platform. And that means the lures and landing pages likely extend far beyond what we have observed so far.
How Proofpoint detects threats like Tycoon 2FA
Tycoon 2FA has received considerable attention recently. But Proofpoint has been detecting and blocking activity associated with a range of reverse proxy services for some time. That includes Evilginx and EvilProxy.
Many bad actors continue to use simpler phish kits that are not designed to bypass MFA. But the use of kits that can steal session tokens is on the rise among phishing actors and initial access brokers (IAB). That trend is creating an urgent need for defenders to amplify detection, remediation and human risk management in this space.
Proofpoint has a unique combination of behavioral artificial intelligence (AI), analytics and deep threat intelligence, and a security awareness solution that enables a defense-in-depth approach against malicious tools like Tycoon 2FA.
- Pre-delivery AI-powered detection. AI- and machine learning-driven behavioral analytics and URL sandbox identify and block Tycoon 2FA landing pages and phishing activity.
- Global threat intelligence visibility. Proofpoint Threat Intelligence provides businesses with insights into threat intelligence infrastructure to identify known and emerging threats that are blocked at the edge.
Empower user behavior change
Our security awareness uses real-world examples, like MFA bypass technologies, drawn from Proofpoint Threat Intelligence. This approach equips end users with the knowledge they need to recognize and respond appropriately to potential threats.
If you are concerned about the threat Tycoon 2FA and similar phishing kits pose to your business and users, you can reach out to Proofpoint to get further details and threat-hunting tips from our threat researchers. To learn more about how we can help you defend against these and other phishing threats, check out our security awareness training solutions or contact us.
