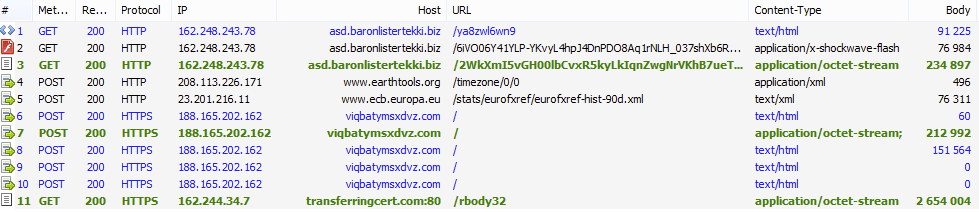
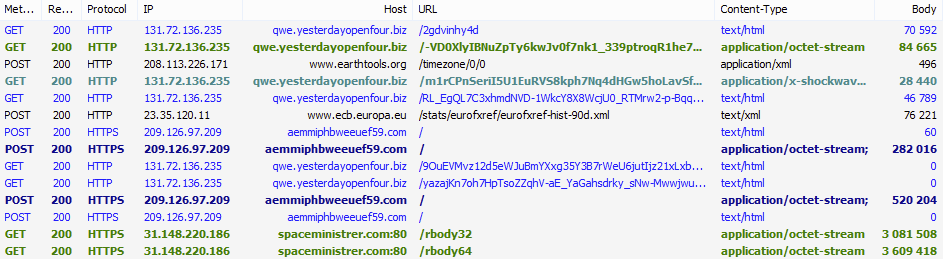
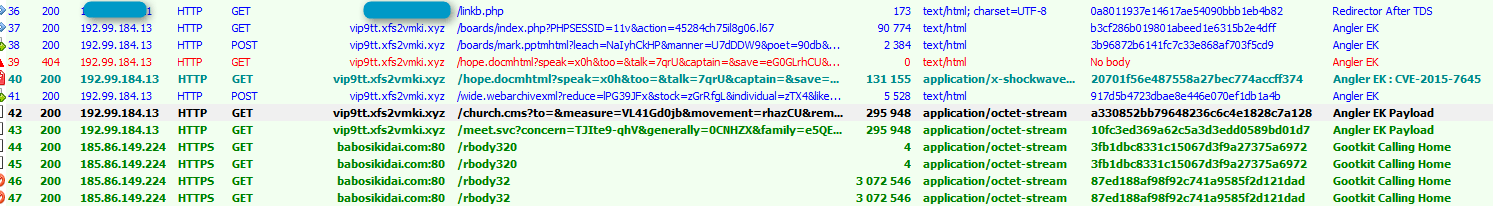
First documented in mid-2014 [1], the Gootkit banking Trojan appeared to focus solely on customers from several French banks. This JavaScript-based malware combines web-injects (a la Zeus) and a clever persistence technique to create a robust tool for stealing online banking logins and other credentials from users of infected systems. In 2015, Gootkit integrated certain fileless features previously noted in Poweliks [2], and it has also been observed being dropped directly by Angler EK (Fig. 1) or indirectly via Bedep (Fig. 2).
Figure 1: Angler EK dropping Gootkit (2014-09-23)
Figure 2: Bedep dropping Gootkit (2014-12-10)
Gootkit has been observed targeting credentials for customers of a range of French financial institutions, including Crédit Mutuel, BNP Paribas, Le Crédit Lyonnais, Crédit Agricole, Société Générale, BTP Banque, and Crédit Coopératif. In March 2015, this distribution expanded to include customers of French and Italian banks through spam campaigns [3] that are still ongoing.
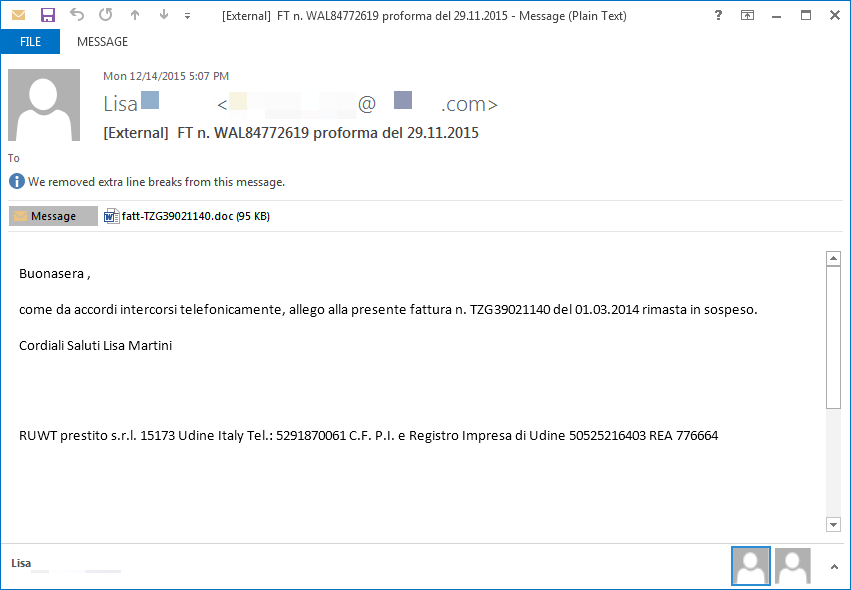
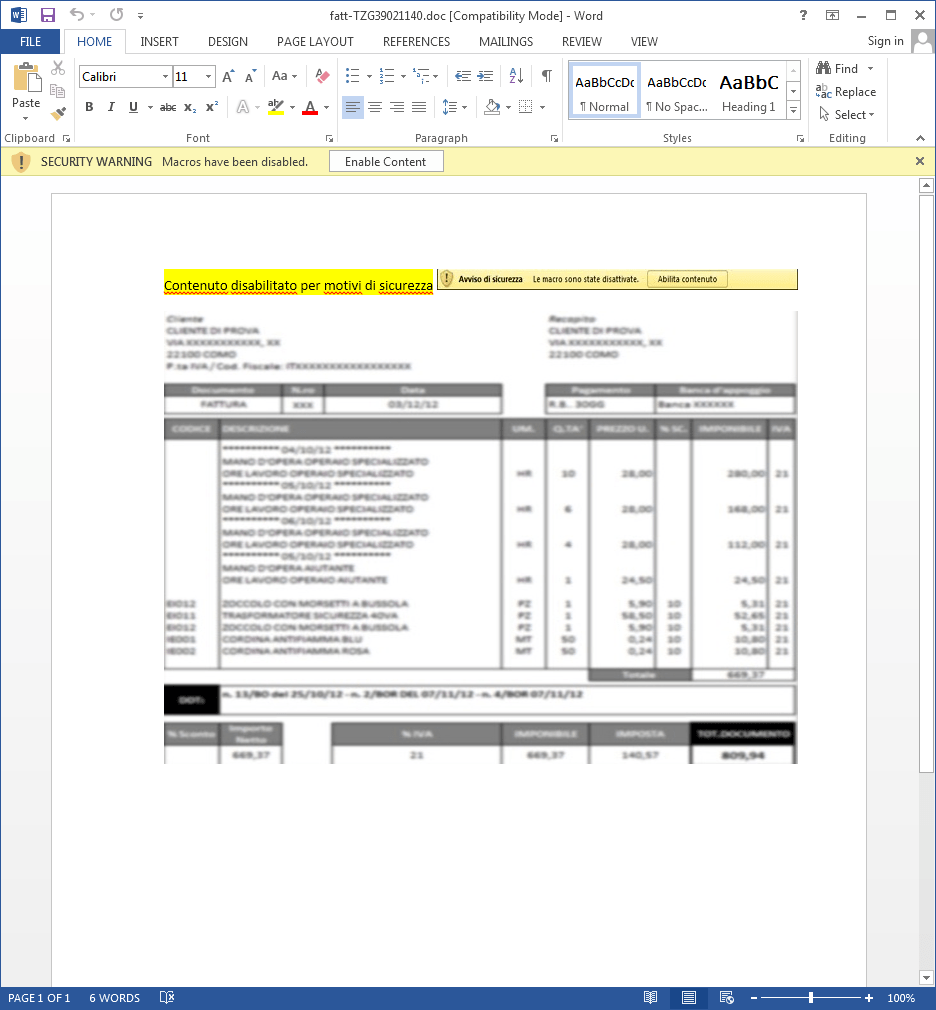
Here is an example of an email and accompanying Word doc used to deliver Gootkit to Italian targets in December of 2015.
Figure 3: Email used to deliver Gootkit (2015-12-14)
Figure 4: Word document used to deliver Gootkit (2015-12-14)
This expansion continued in late October, as Proofpoint researchers observed Gootkit being dropped by Angler EK through multiple infection paths in Canada. Since 2015-11-26, Gootkit has also been seen dropped in Great Britain via Angler EK at the end of a malvertising infection chain.
Figure 5: Gootkit dropped by Angler EK in Great Britain at the end of a Malvertising chain (2015-12-13)
Figure 6: Snippet of UK-focused injects tied to sample 58aeefd4700af5cb1db1f5603025a5ec
Configs from the UK-focused injects (Fig. 6) show that these latest payloads are attempting to capture information from customers of a range of financial institutions that are based or operate in the UK, including Paypal, Santander, Natwest, Ulster Bank, Royal Bank of Scotland, and Barclays.
This expanded targeting follows a trend we have observed in recent months, as threat actors seek to reach new victims by shifting their distribution to new regions and verticals. With Gootkit finally crossing the Channel it would not be surprising to see it in other regions in the near future, as well as to see other malware with limited geographic presence (such as Shifu) jump on this trend.
References
[1] Analyzing Gootkit's persistence mechanism (new ASEP inside!) - 2015-04-13 - CERTSG - https://www.sentinelone.com/labs/gootkit-banking-trojan-part-2-persistence-other-capabilities/
[2] Win32/Xswkit (alias Gootkit) - http://www.kernelmode.info/forum/viewtopic.php?f=16&t=3669
[3] Fake Judicial Spam Leads to Backdoor with Fake Certificate Authority - 2015-03-30 - http://blog.trendmicro.com/trendlabs-security-intelligence/fake-judicial-spam-leads-to-backdoor-with-fake-certificate-authority/
[4] “Hey Brian, Heya Homer, fancy meeting you here!” – Zeus Gootkit, 2014 AD - 2014-08-07 - CertLexsi https://www.lexsi.com/securityhub/hey-brian-heya-homer-fancy-meeting-you-here-zeus-gootkit-2014-ad/?lang=en
Indicators of Compromise (IOC’s)
File hashes:
6195950991475ec363f53b2c570469512b8e4a1995db73056cff39251c211dff - 2015-08-26 - CAN
a24c9996913ecbe2af183e5ac3d176f869ed62e15a31deb2dc2ea947900432c3 - 2015-11-26 - GBR
cb55bd4ee66ee8fcbda9f0f15192406bb1d089bc72a0f121395fafc8e04cb0e8 - 2015-12-02 - CAN
532bd85487ce3c16654d21c6425f6f728430d50e47e802b332ea82ae0511adca - 2015-12-13 - GBR
3922F2317BE8D0420F1DC938A633B3243D938FC0098A528D70B89C2D2F080C5C - 2015-12-21 - ITA
C2 server addresses:
swysocki77.com - 138.204.171.103
gorski83.com
ostrowski87.com
jasinski2015.com
olszewski78.com
pozheeshebudem.com
freforevermailtes.com
nidermidertom.com
ecuremailbestfree.com
securewebgooglesite.com
robertpouslen12494.pw - 151.80.201.187
robertpouslen1234524.com
update-service7825t28.com
domolor.com - 108.61.178.212
babosikimne.com - 81.2.241.227
babosikidai.com - 185.86.149.224
vaillantsawer.com - 198.96.89.181 185.82.202.38
proballansmen.com
reputamadrell.com
lastrizariano.com
rokobarokkino.com
artipreambulo.com
trequablaster.com
pretriquestro.com
rebellintosto.com
mellicianactr.com
abc.doitgraphic.org - 198.71.232.3
updatebase.bid
shop.lifexcellence.org
ET Open and Pro rules:
2022257 || ET TROJAN Possible Gootkit CnC SSL Cert M5
2022256 || ET TROJAN Possible Gootkit CnC SSL Cert M4
2022255 || ET TROJAN Possible Gootkit CnC SSL Cert M3
2022253 || ET TROJAN Possible Gootkit CnC SSL Cert M1
2019907 || ET CURRENT_EVENTS Gootkit SSL Cert Dec 10 2014
2022259 || ET TROJAN Possible Gootkit CnC SSL Cert M7