
Researchers are warning of threat actors increasingly abusing the Cloudflare Tunnel service in malware campaigns that usually deliver remote access trojans (RATs).
This cybercriminal activity was first detected in February and it is leveraging the TryCloudflare free service to distribute multiple RATs, including AsyncRAT, GuLoader, VenomRAT, Remcos RAT, and Xworm.
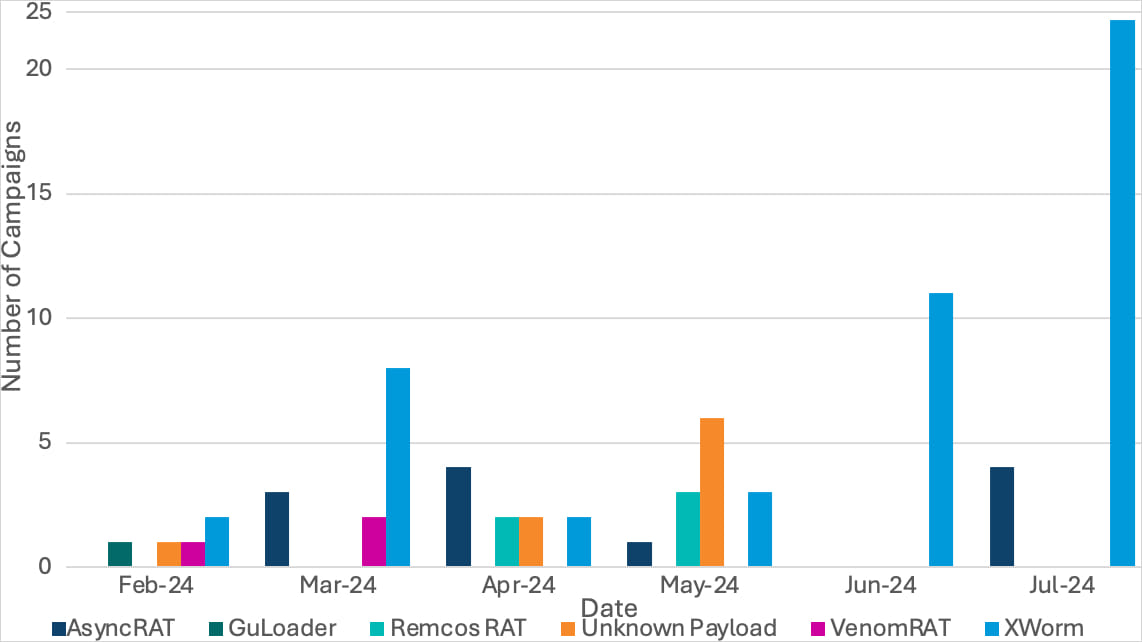
Source: Proofpoint
The Cloudflare Tunnel service allows proxying traffic through an encrypted tunnel to access local services and servers over the internet without exposing IP addresses. This should come with added security and convenience because there is no need to open any public inbound ports or to set up VPN connections.
With TryCloudflare, users can create temporary tunnels to local servers and test the service without the need of a Cloudflare account.
Each tunnel generates a temporary random subdomain on the trycloudflare.com domain, which is used to route traffic through Cloudflare’s network to the local server.
Threat actors have abused the feature in the past to gain remote access to compromised systems while evading detection.
Latest campaign
In a report today, cybersecurity company Proofpoint says that it observed malware activity targeting law, finance, manufacturing, and technology organizations with malicious .LNK files hosted on the legitimate TryCloudflare domain.
The threat actors are luring targets with tax-themed emails with URLs or attachments leading to the LNK payload. When launched, the payload runs BAT or CMD scripts that deploy PowerShell.
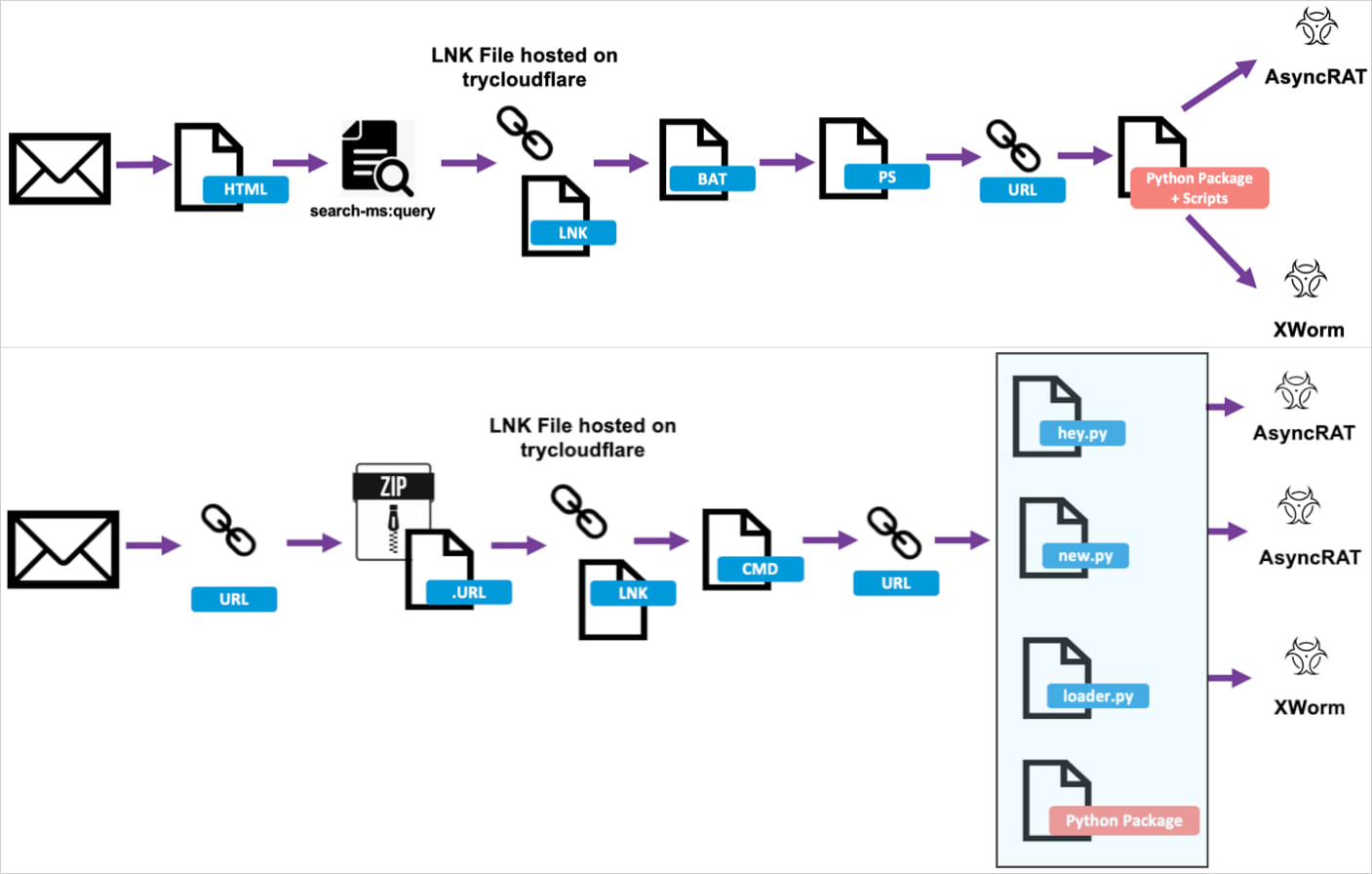
Source: Proofpoint
In the final stage of the attack, Python installers are downloaded for the final payload.
Proofpoint reports that the email distribution wave that started on July 11 has distributed over 1,500 malicious messages, while an earlier wave from May 28 contained less than 50 messages.
Source: Proofpoint
Hosting LNK files on Cloudflare offers several benefits, including making the traffic appear legitimate due to the service's reputation.
Moreover, the TryCloudflare Tunnel feature offers anonymity, and the LNK-serving subdomains are temporary, so blocking them does not help defenders too much.
Ultimately, the service is free and reliable, so the cybercriminals do not need to cover the cost of setting up their own infrastructure. If automation is employed to evade blocks from Cloudflare, the cybercriminals can abuse those tunnels even for large-scale operations.
BleepingComputer has reached Cloudflare for a comment on the activity reported by Proofpoint, and a company representative replied with the following statement:
Cloudflare immediately disables and takes down malicious tunnels as they are discovered by our team or reported on by third parties.
In the past few years, Cloudflare has introduced machine learning detections on our tunnel product in order to better contain malicious activity that may occur.
We encourage Proofpoint and other security vendors to submit any suspicious URLs and we will take action against any customers that use our services for malware.
Top 10 MITRE ATT&CK© Techniques Behind 93% of Attacks
Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.











Comments
NoneRain - 9 months ago
And that is why we can't have nice things.
johnlsenchak - 9 months ago
Cloudflare once again comes under pressure for enabling abusive sites
Cloudflare masks the origin of roughly 10% of abusive domains, watchdog says.
https://arstechnica.com/security/2024/07/cloudflare-once-again-comes-under-pressure-for-enabling-abusive-sites/
NoneRain - 9 months ago
I don't think I agree for the most part with Ars' article. It doesn't say Cloudflare offer services for 16% of the internet, which is HUGE. It's expected that a small percentage of that will be malicious domains, thus 10% of Spamhaus. It also implies Cloudflare do not act against malicious activity, which is just false. One can argue that they do not do a good job, but not that their permissive policies are the root cause of it.
Cloudflare offer services like the one in this article, and malicious actors abuse 'em. There's no simple way to combat it considering the nature of the service, other than cutting or restricting it, which is a double-edged sword.
I do agree Cloudflare should improve their sec and push innovation in this segment, IMO it's part of the top dog responsibility.