Key Takeaways
- Over the last six months, Proofpoint researchers have observed a dramatic surge of over 100% in successful cloud account takeover incidents impacting high-level executives at leading companies.
- Over 100 organizations were targeted globally, collectively representing 1.5 million employees.
- Threat actors utilized EvilProxy - a phishing tool based on a reverse proxy architecture, which allows attackers to steal MFA-protected credentials and session cookies.
- This rising threat combines sophisticated Adversary-in-the-Middle phishing with advanced account takeover methods, in response to the growing adoption of multifactor authentication by organizations.
Multifactor authentication (MFA) use has increased over the past few years in organizations. Contrary to what one might anticipate, there has been an increase in cloud account takeovers among tenants that have MFA protection. Based on our data, at least 35% of all compromised users during the past year had MFA enabled.
Threat actors are advancing their methods for compromising accounts; one method we watched was particularly effective. Attackers use new advanced automation to accurately determine in real-time whether a phished user is a high-level profile, and immediately obtain access to the account, while ignoring less lucrative phished profiles.
Contents:
Reverse Proxy Turned Evil
In a previous blog post, we explored how the growing adoption of MFA led to the proliferation of phishing kits and tools designed to bypass this popular layer of security. We reported how threat actors are increasingly employing Adversary-in-the-Middle (AitM) phishing kits (such as EvilProxy), to steal credentials and session cookies in real-time (Figure 1). As we predicted at the time of our blog, the presence and impact of these MFA kits on the threat landscape have since grown significantly.
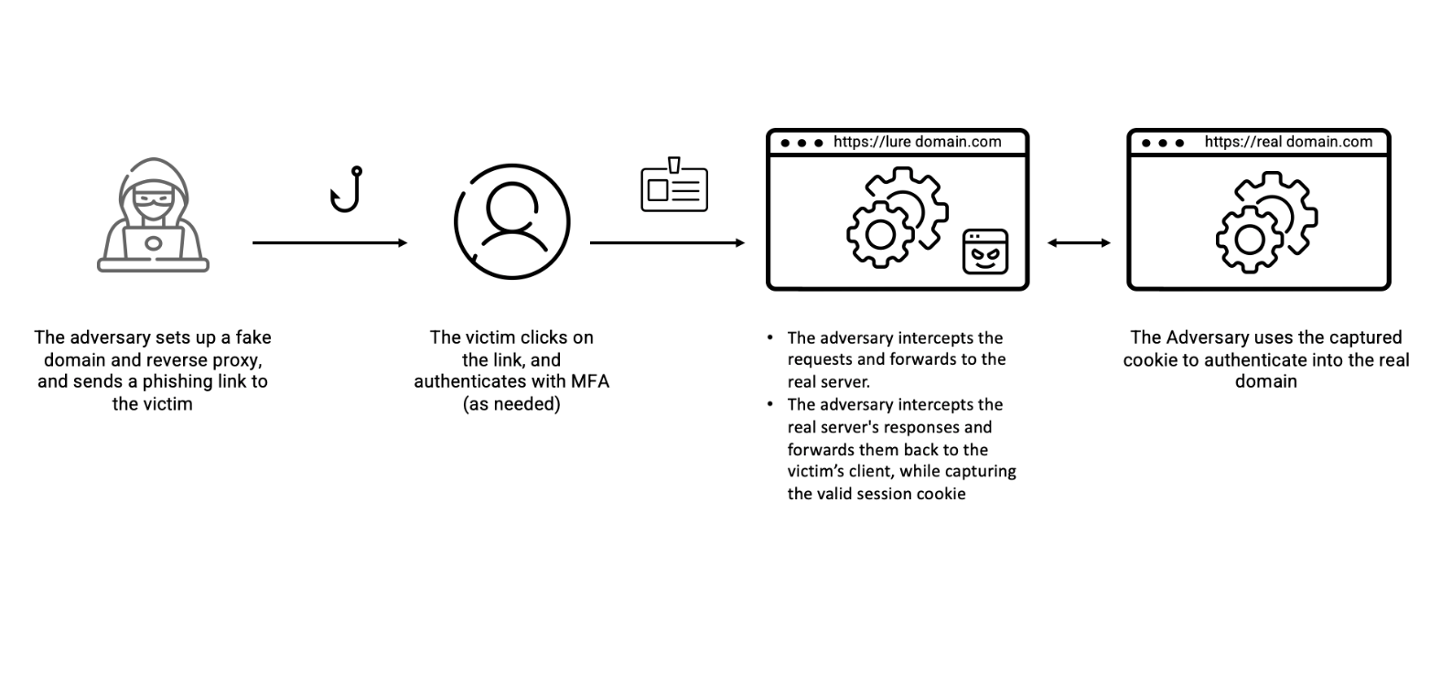
Figure 1. AitM Transparent Reverse Proxy.
Due to the do-it-yourself nature of open-source kits, threat actors have seized on a market opportunity and developed MFA Phishing as a Service (PhaaS). This has allowed would-be credential phishers of even low technical aptitude to simply pay for pre-configured kits for a variety of online services (such as Gmail, Microsoft, Dropbox, Facebook, Twitter, etc.).
Nowadays, all an attacker needs is to set up a campaign using a point-and-click interface with customizable options, such as bot detection, proxy detection, and geofencing. This relatively simple and low-cost interface has opened a floodgate of successful MFA phishing activity. One such interface is the EvilProxy phishing toolkit, an all-inclusive kit that is easy to acquire, configure, and set up.
Although the effectiveness of EvilProxy as a phishing tool is largely recognized, Proofpoint threat analysts have identified a concerning gap in public awareness regarding its risks and potential consequences. While multiple other proxy and phishing kits exist, in this blog we will examine the practices and consequences of EvilProxy attacks, resulting in Business Email Compromise (BEC) and Account Takeover (ATO) incidents.
What Are We Seeing?
Since early March, Proofpoint researchers have been monitoring an ongoing hybrid campaign using EvilProxy to target thousands of Microsoft 365 user accounts. This campaign’s overall spread is impressive, with approximately 120,000 phishing emails sent to hundreds of targeted organizations across the globe between March and June 2023.
During the phishing stage of the reverse proxy attack, attackers employed several noteworthy techniques:
- Brand impersonation. Sender addresses impersonated trusted services and apps, such as Concur Solutions, DocuSign and Adobe.
- Scan blocking. Attackers utilized protection against cyber security scanning bots, making it harder for security solutions to analyze their malicious web pages.
- Multi-step infection chain. Attackers redirected traffic via open legitimate redirectors, including YouTube, followed by additional steps, such as malicious cookies and 404 redirects.
Phase 1 - EvilProxy in Action
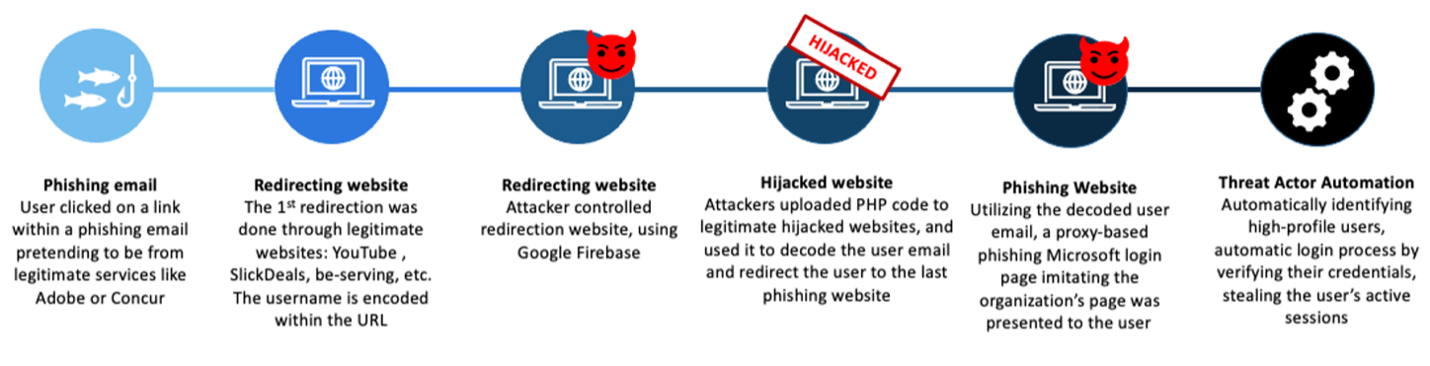
Figure 2. The attack's redirection chain.
Initially, attackers impersonated known trusted services, such as the business expense management system Concur, DocuSign and Adobe (Figures 5 and 6). They used spoofed email addresses to send phishing emails that contained links to malicious Microsoft 365 phishing websites.
Emails purporting to be from DocuSign, Adobe Sign and Concur contained malicious URLs that initiated a multi-step infection chain:
- First, user traffic is redirected via an open, legitimate redirector (such as youtube[.]com, bs.serving-sys[.]com, etc).
- Next, user traffic may undergo several more redirection steps, which involve malicious cookies and 404 redirects. This is done to scatter the traffic in an unpredictable way, lowering the likelihood of discovery (as seen in Figure 2).
- Eventually, user traffic is directed to an EvilProxy phishing framework. The landing page functions as a reverse proxy, mimicking recipient branding and attempting to handle third-party identity providers. If needed, these pages may request MFA credentials to facilitate a real, successful authentication on behalf of the victim – thus also validating the gathered credentials as legitimate.
One of the abused domains seen in this attack flow, bs.serving-sys[.]com, is a domain known for redirecting users to a range of undesired webpages. During the first wave of the reverse proxy attack, attackers utilize this domain to direct traffic to malicious websites.
In the next waves, in order to prevent detection by security solutions and to entice the user to click the links, attackers employ redirect links on reputable websites (such as YouTube, SlickDeals, etc.).
Here is an example of a malicious URL pattern using YouTube as its redirection domain:
https://www.youtube[.]com/attribution_link?c=10570810&u=http://dseapps.web[.]app/pi2Pss****3RWO3BM2?id=com.google.android.apps.youtube.music
When analyzing some redirection pages, our researchers identified a small, albeit important, detail that appeared on the first days of the attack and set this campaign apart from other attacks.
It was a minor typo in the redirect string: instead of transferring the user to a “https” page, attackers mistakenly pointed to a “hhttps” address (Figure 3). That led to a failed redirection flow.
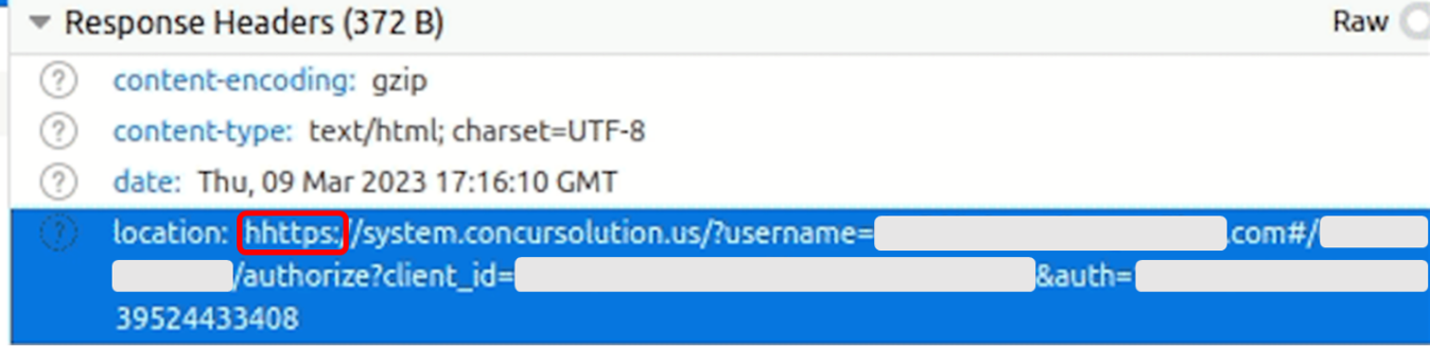
Figure 3. Attackers’ Typing Error (“hhttps” instead of “https”) Caused a Failed Redirection Flow.
In order to hide the user email from automatic scanning tools, the attackers employed special encoding of the user email, and used legitimate websites that have been hacked, to upload their PHP code to decode the email address of a particular user.
After decoding the email address, the user was forwarded to the final website - the actual phishing page, tailor-made just for that target’s organization.
This encoding has a few different variations that changed with each wave of the attack, but the basic concept of decoding was the same for all of them.
- The email address is written in lowercase only.
- A number, or uppercase letter, is paired with another number or letter to decode.
- The attackers utilized the following decoding patterns on all observed links:
|
Email encoded patterns |
Decoded |
|
x0q / a51 |
@ |
|
dy9 / d07 / d0T |
. |
|
2P |
blank |
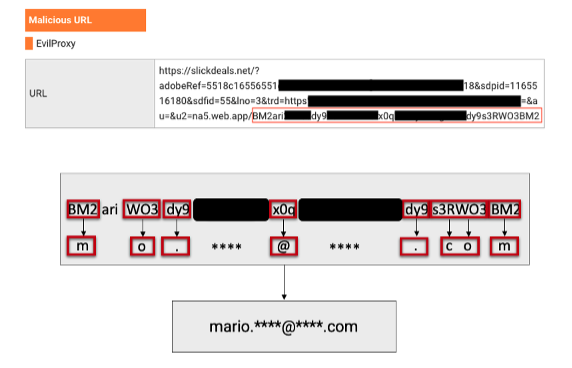
Figure 4. Example decoding of a targeted user email from a redirect URL.
Another curious element we observed is the apparent alteration in the attack flow when accessing malicious phishing web pages from certain geographies. Concretely, user traffic originating from Turkish IP addresses was directed to the legitimate web page, out of the attacker’s control. Although this change might be explained by the proxy service using a form of “safe-listing”, this behavior was seen exclusively for traffic originating from Turkey. If this flow is indeed intentional, it could suggest that the threat actors behind this campaign appear to be based in Turkey, or otherwise were intentionally avoiding targeting Turkish users. It is worth mentioning that numerous VPNs throughout the world are also blocked from accessing the malicious phishing websites.

Figure 5. A GIF demonstrates how attackers redirect traffic from Turkish IP addresses to the genuine DocuSign website.

Figure 6. Example of a phishing threat sent to targeted users by attackers, utilizing brand impersonation (posing as “SAP Concur”), as part of a widespread malicious campaign.
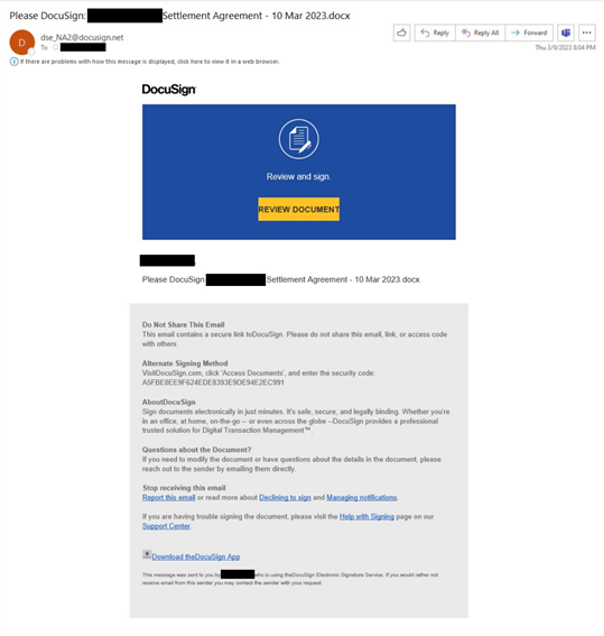
Figure 7. An example of a phishing threat sent to targeted users by attackers, utilizing brand impersonation (posing as “DocuSign”), as part of a widespread malicious campaign.
Phase 2 – Account Compromise
According to our research, the list of targeted users included many high-value targets, such as C-level executives & VPs at leading companies. These titleholders are especially valued by threat actors due to their potential access to sensitive data and financial assets. Once a targeted user has provided their credentials, attackers were able to log into their Microsoft 365 account within seconds, indicating a streamlined and automated process.
However, not all users who fell for the initial phishing lure and submitted their credentials were accessed by bad actors. In contrast to other malicious campaigns we’ve observed, in this case, attackers clearly prioritized only “VIP” targets, while ignoring those of lesser value to them. This pattern can be an indication of a process which makes use of the victim's organizational information that was acquired from other sources, most likely information that was made available to the public.
Amongst the hundreds of compromised users, approximately 39% were C-level executives of which 17% were Chief Financial Officers, and 9% were Presidents and CEOs. Attackers have also shown interest in lower-level management, focusing their efforts on personnel with access to financial assets or sensitive information.
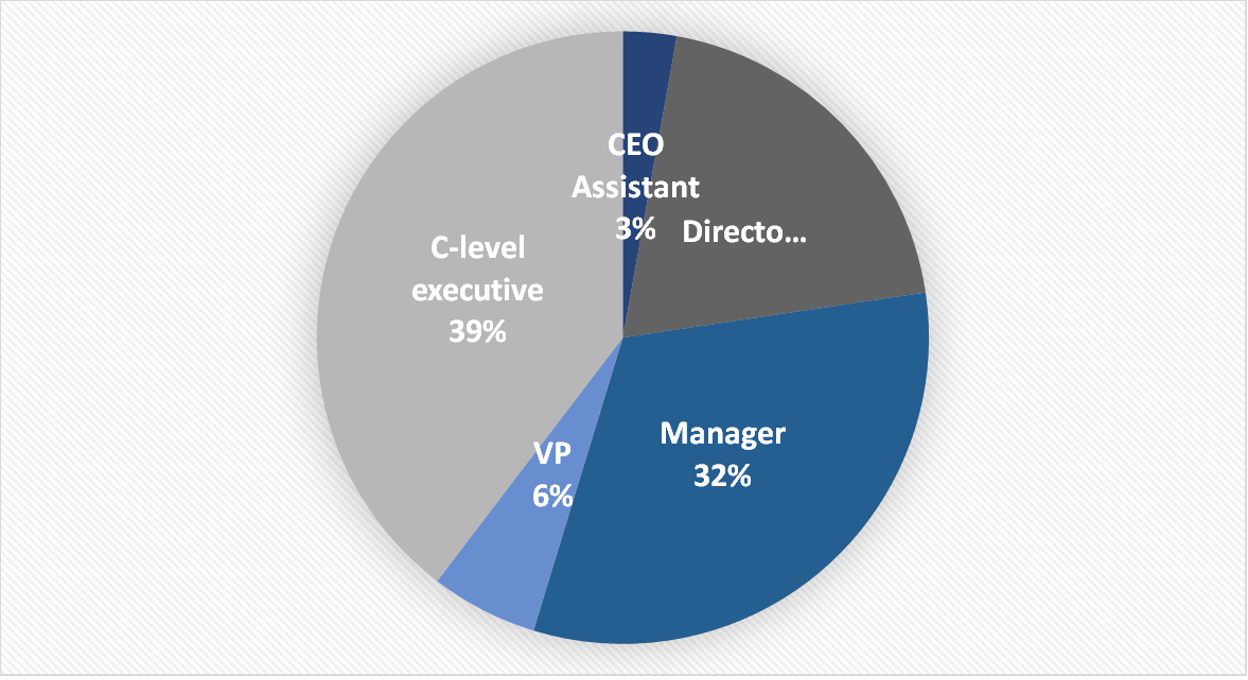
Figure 8. The chart illustrates the roles that have been compromised.
Phase 3 – Post-Compromise Exploitation
Once attackers accessed a victim’s account, they proceeded to cement their foothold within the impacted organization’s cloud environment. On multiple occasions, threat actors leveraged a native Microsoft 365 application to execute MFA manipulation. Utilizing ‘My Sign-Ins’ (Figure 9), attackers were able to add their own multi-factor authentication method, establishing persistent access to compromised user accounts. The preferred method of authentication for attackers was “Authenticator App with Notification and Code” (Figure 10).
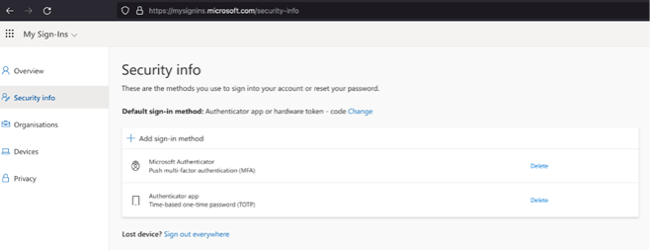
Figure 9. Microsoft's My Sign-Ins Application, Leveraged by Attackers to Execute MFA Manipulation.
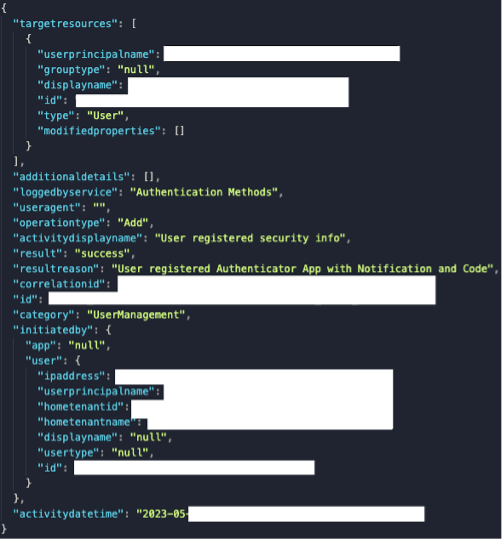
Figure 10. Attacker-controlled MFA method added post-compromise (Authenticator App with notification and code).
Conclusion
Threat actors constantly seek new ways to steal users’ credentials and acquire access to valuable user accounts. Their methods and techniques constantly adapt to new security products and methodologies, such as multi-factor authentication. As this blog illustrates, even MFA is not a silver bullet against sophisticated threats and could be bypassed by various forms of combined email-to-cloud attacks.
Reverse proxy threats (and EvilProxy in particular) are a potent threat in today’s dynamic landscape and are out-competing the less capable phish kits of the past. They have risen significantly in popularity and exposed crucial gaps in organizations’ defense strategies. For that reason, attackers are quickly pivoting to easy-to-use advanced phishing kits, which leads to an increase in hybrid attacks’ efficacy and velocity.
Although these attacks’ initial threat vector is email-based, their final goal is to compromise and exploit valuable cloud user accounts, assets, and data. Given access to a “VIP” user account, attackers will first seek to consolidate their gains by establishing persistence. Then, they will attempt to exploit their unauthorized access (Figure 9).
During those last phases, cyber criminals employ various techniques, including lateral movement and malware proliferation. The attackers have been known to study their target organizations’ culture, hierarchy, and processes, to prepare their attacks and improve success rates. In order to monetize their access, attackers were seen executing financial fraud, performing data exfiltration or partaking in Hacking-as-a-Service (HaaS) transactions, selling access to compromised user accounts.
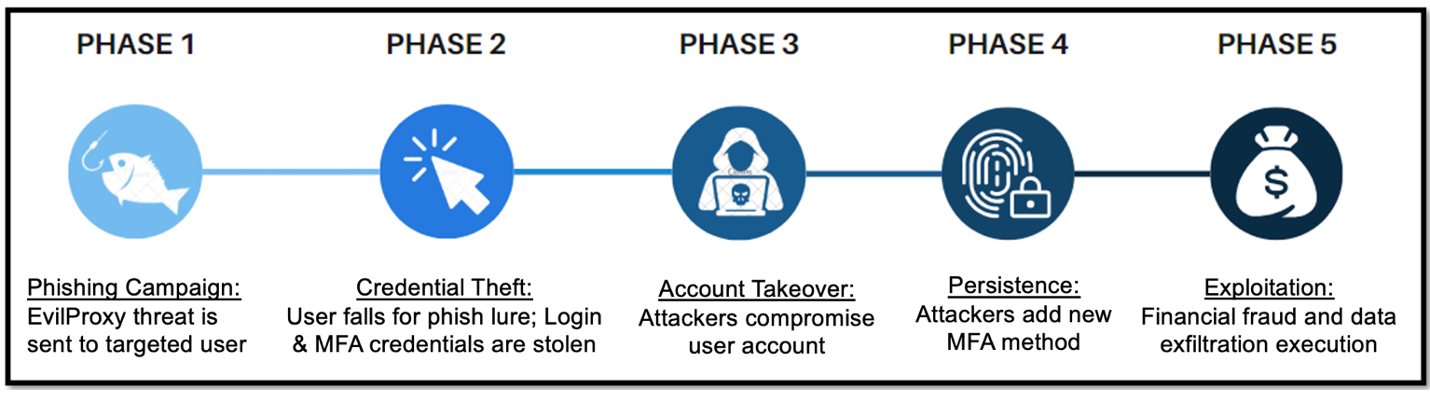
Figure 11. EvilProxy Attack Chain Phases.
Recommendations
Below are ways to help your organization defend against advanced hybrid (email-cloud) threats:
- Email Security: Block and monitor malicious email threats targeting your users. Effective BEC-prevention solutions can greatly minimize practical attack surfaces.
- Cloud Security: Identify account takeover (ATO) and unauthorized access to sensitive resources within your cloud environment.
- These solutions should provide accurate and timely detection of both the initial account compromise and post-compromise activities, including visibility into abused services and applications.
- Employ auto-remediation capabilities to reduce attackers’ dwell time and potential damages.
- Web Security: Isolate potentially malicious sessions initiated by links embedded in email messages.
- Security Awareness: Educate users to be aware of these risks when using Microsoft 365.
- FIDO: Consider adopting FIDO-based physical security keys (https://fidoalliance.org/how-fido-works).
Contact Proofpoint to learn more about how we can help your organization protect cloud apps and secure Microsoft 365 cloud environments.
IOCs
|
Indicator |
Type |
Description |
|
01-net[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
837[.]best |
Domain |
Malicious “Step 2” redirection domain |
|
abbotsfordbc[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
ae-lrmed[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
andrealynnsanders[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
bdowh[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
cad-3[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
cdjcfc[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
chiromaflo[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
cmzo-eu[.]cz |
Domain |
Malicious “Step 2” redirection domain |
|
concur[.]bond |
Domain |
Malicious “Step 2” redirection domain |
|
concurcloud[.]us |
Domain |
Malicious “Step 2” redirection domain |
|
concursolution[.]us |
Domain |
Malicious “Step 2” redirection domain |
|
concursolutions[.]info |
Domain |
Malicious “Step 2” redirection domain |
|
cualn[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
d8z[.]net |
Domain |
Malicious “Step 2” redirection domain |
|
dealemd[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
dl2b[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
dsa-erie[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
dse[.]best |
Domain |
Malicious “Step 2” redirection domain |
|
dse[.]buzz |
Domain |
Malicious “Step 2” redirection domain |
|
dsena[.]net |
Domain |
Malicious “Step 2” redirection domain |
|
e-csg[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
etrax[.]eu |
Domain |
Malicious “Step 2” redirection domain |
|
farmacgroup[.]ca |
Domain |
Malicious “Step 2” redirection domain |
|
faxphoto[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
fdh[.]aero |
Domain |
Malicious “Step 2” redirection domain |
|
finsw[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
fortnelsonbc[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
g3u[.]eu |
Domain |
Malicious “Step 2” redirection domain |
|
greatbayservices[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
gwcea[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
indevsys[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
inteproinc[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
jxh[.]us |
Domain |
Malicious “Step 2” redirection domain |
|
k4a[.]eu |
Domain |
Malicious “Step 2” redirection domain |
|
kayakingbc[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
kirklandellis[.]net |
Domain |
Malicious “Step 2” redirection domain |
|
kofisch[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
ld3[.]eu |
Domain |
Malicious “Step 2” redirection domain |
|
mde45[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
mjdac[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
n4q[.]net |
Domain |
Malicious “Step 2” redirection domain |
|
na-7[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
na3[.]wiki |
Domain |
Malicious “Step 2” redirection domain |
|
nilyn[.]us |
Domain |
Malicious “Step 2” redirection domain |
|
p1q[.]eu |
Domain |
Malicious “Step 2” redirection domain |
|
pagetome[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
parsfn[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
pbcinvestment[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
phillipsoc[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
pwsarch[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
re5[.]eu |
Domain |
Malicious “Step 2” redirection domain |
|
sloanecarpet[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
ssidaignostica[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
tallwind[.]com[.]tr |
Domain |
Malicious “Step 2” redirection domain |
|
ukbarrister[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
utnets[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
uv-pm[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
vleonard[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
wattsmed[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
whoyiz[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
wj-asys[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
wmbr[.]us |
Domain |
Malicious “Step 2” redirection domain |
|
wwgstaff[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
xp1[.]us |
Domain |
Malicious “Step 2” redirection domain |
|
xstpl[.]com |
Domain |
Malicious “Step 2” redirection domain |
|
154.29.75.192 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
185.241.52.78 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
185.250.243.176 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
185.250.243.38 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
198.44.132.249 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
212.224.107.12 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
45.8.191.151 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
45.8.191.17 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
74.208.49.213 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
77.91.84.52 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
78.153.130.178 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
87.120.37.47 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
104.183.206.97 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
172.102.23.21 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
191.96.227.102 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
90.92.138.71 |
IP Address |
Source IP address involved in EvilProxy Attack |
|
autonotification@concursolutions[.]com |
Spoofed email address |
Spoofed sender address involved in EvilProxy campaigns |
|
dse@eumail.docusign[.]net |
Spoofed email address |
Spoofed sender address involved in EvilProxy campaigns |
|
adobesign@adobesign[.]com |
Spoofed email address |
Spoofed sender address involved in EvilProxy campaigns |
