Table of Contents
Account Takeover Definition
Account takeover fraud, or account compromise, occurs when a cyber attacker gains control of a legitimate account. Account takeover fraud (ATO) is characterized by unauthorized individuals taking over someone else’s online account — such as a bank account, email account, or social media profile — without the account owner’s permission. This criminal activity is achieved by obtaining the account holder’s login credentials through different types of attacks, including phishing, malware attacks, social engineering, or data breaches.
Once they have control of an account, attackers can launch a variety of attacks, such as:
- Internal phishing: Emails between employees in the same organization using a compromised corporate account.
- Supply-chain phishing: Most organizations do business over email. An attacker gaining control over a legitimate account can assume your employee’s identity to defraud customers and business partners.
- BEC-style attacks: Think of account takeovers as the ultimate impersonation tactic. In ATO, attackers hijack an email account to essentially become its owner. ATO attacks bypass many email authentication controls.
- Data exfiltration: Gaining access to someone’s mailbox, attackers can access not just email but also calendar events, contacts, and sensitive data in file shares.
- Financial fraud: If attackers gain control of someone’s bank account or other financial services, they can steal funds directly via fraudulent wire transfers and purchases.
Account takeover techniques are usually automated using scripts that potentially contain thousands of credentials and user accounts. Revenue generated from a successful attack can reach millions on darknet markets for an advanced attack.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we’ll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
How Account Takeover Fraud Happens
The foundation for a successful account takeover is access to a user’s account credentials. Here’s how attackers typically compromise legitimate accounts:
- Brute-force attacks: The attacker, usually through an automated script, tries a username/password combination across many accounts until one works. These include so-called dictionary attacks, in which attackers use common passwords and dictionary terms to guess passwords.
- Breach replay attack (also known as credential stuffing): It’s a bad practice, but many people use the same password for multiple accounts. If one of those passwords is leaked in an unrelated data breach, any other account with the same username (often an email address) and password is at risk.
- Man-in-the-middle (MitM) attacks: By intercepting communication between users and websites, attackers can steal login credentials and other sensitive information that enables them to take over accounts.
- Phishing: Old-fashioned credential phishing remains an effective way to steal a victim’s password. Without controls such as multifactor authentication (MFA), lost credentials can lead to compromised accounts.
- Malware attacks: Keyloggers, stealers and other forms of malware can expose user credentials, giving attackers control of victims’ accounts.
- Data exfiltration: The unauthorized retrieval, transfer, or copying of data from a device or server provides attackers access to login credentials, such as usernames and passwords, to gain control of an account.
- Credential stuffing: Cyber-attackers employ automated tools to gather and test stolen usernames and passwords from data breaches on other websites to gain unauthorized access to accounts.
Attackers can also download cracked passwords from darknet markets to attempt ATO on the same user accounts on their target site.
After the attacker has a long list of credentials, several ATO applications are available for download. A few notable tools include SentryMBA, SNIPR, STORM, and MailRanger. The following image is one of the main windows in SentryMBA:
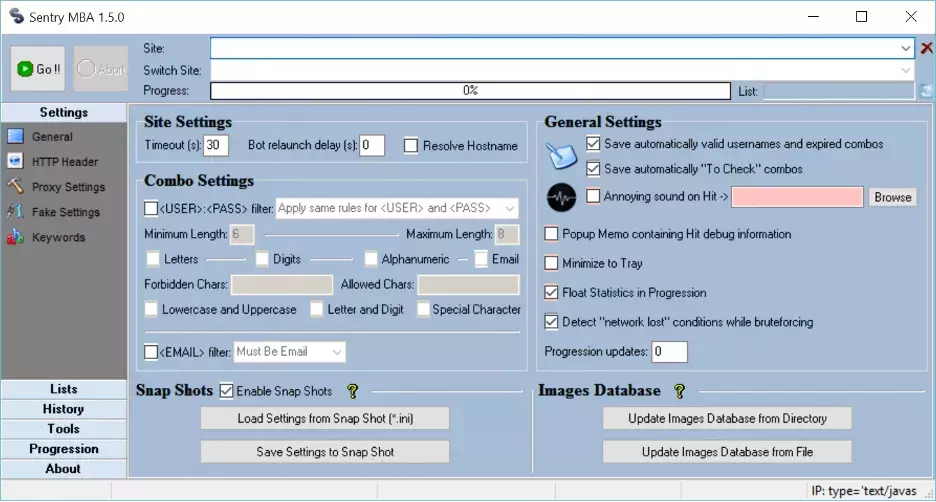
SentryMBA is an automated attack tool used by cybercriminals and one of the more popular ones due to its options and general settings. At the top, an attacker inputs the site where requests are sent for authentication into user accounts. Other settings include the list of passwords and usernames, the ability to save a list of successful authentication attempts, and timeout settings that help that attacker avoid detection. The entire ATO attack is automated, so most of the effort is spent stealing credentials. Tools such as SentryMBA can run indefinitely on the attacker’s computer until it creates a list of stolen accounts.
In some account takeover fraud scenarios, an attacker will not use the initial ATO attack on the primary target site. As users commonly use the same credentials across several sites, an attacker might use a site with weaker cybersecurity defenses and fraud detection to validate credentials.
If a user employs the same credentials across multiple sites, the attacker’s successful authentication into one site might work on the primary site. For instance, an attacker might use SentryMBA to authenticate into a popular hotel site, knowing most users have accounts with prominent hotel brands for traveling. If authentication is successful on the hotel site, it could also be successful on a banking site. By validating credentials on a secondary site first, the attacker reduces the number of authentication attempts, minimizing the likelihood of detection.
With a list of successfully authenticated accounts, an attacker has two choices: transfer money or sell the validated credentials online. Attackers can transfer funds from a targeted user’s bank account to their accounts. On credit card sites, an attacker could order new credit cards in a targeted user’s name but send new cards to their address. If a site doesn’t have proper ATO fraud detection, targeted users have no idea when money is transferred, or a credit card is sent to a new address.
Selling the list of authenticated accounts could mean a high payout for attackers. The value of just one hacked account depends on the amount of data stolen and the type of account. For instance, a PayPal account could be worth $1,200, while a targeted user’s personal data could be sold from $40 to $200. Bank cards are worth $800 to $1,000. With hundreds and potentially thousands of accounts, an attacker could have a hefty payday selling on darknet markets and limit detection compared to directly stealing from victims.
ATO fraud is not limited to banking and credit card accounts. Attackers can also use rewards cards and services, including stored points on hotel accounts and airline miles. This fraud is gaining interest because targeted users rarely monitor reward accounts for fraud compared to credit cards and bank accounts.
Social Media Protection
Real-time security for your branded social media accounts
Factors That Increase Account Takeover Fraud Popularity
Darknet markets make account takeover fraud much more attractive to attackers by reducing liability as they no longer need to steal directly from targeted users. Attackers wanting to steal directly from targeted users can simply purchase valid accounts on darknet markets instead of performing the arduous task of cracking passwords.
While darknet markets make it easier to steal from users, increased online financial accounts and offerings also fuel the market. Targeted users often have many financial accounts spread across several websites. The proliferation of financial accounts and online presence means an increase in the attack surface for ATO fraud.
Account Takeover Fraud Detection
Detecting ATO fraud can be challenging, but often these attacks can be detected by monitoring for suspicious activity and behavior. Here are some of the most effective ways to identify potential ATO threats:
- Monitor emails and other communications: It’s critical to implement measures that effectively monitor emails, text messages, and other communications for suspicious activity, like phishing attempts or requests for sensitive information.
- Recognize suspicious IP addresses: Look for unusual activity regarding suspicious IP addresses (e.g., from countries outside typical access locations) and analyze timestamp data transfers. This helps identify fraudsters attempting to take over an account.
- Leverage machine learning models: Use machine learning models to help pinpoint fraudulent online activity by detecting account compromise through malicious takeovers, phishing, or from credentials being stolen.
- Identify and block requests from known attackers: Identify and block requests from known attackers and detect bad bots used by attackers as part of ATO attacks. You can also find credential stuffing on login attempts and block them.
- Pinpoint unknown devices: Attackers will often use device spoofing techniques to conceal what device they’re using. If your system detects devices as “unknown,” especially at an abnormally high ratio, then an ATO threat is likely.
- Multiple accounts being accessed by one device: If an attacker steals and accesses more than one account, their activity will likely be linked to one device. This can be a sign of an ATO attack.
- Use AI-based detection technology: ATO attacks often use fourth-generation bots that mimic user behaviors, making them difficult to isolate. AI-based detection technology can be effective in identifying these ATO attacks.
By implementing these strategies, you can better detect and prevent ATO fraud and protect your accounts from unauthorized access.
Impact of ATO Attacks
Successful ATO attacks can have a serious negative impact on both individuals and businesses. Some of the ramifications of ATO fraud at both levels:
- Identity theft: ATO fraudsters can steal personal information, such as social security numbers, credit card numbers, and login credentials used for identity theft. The outcome can result in severe financial losses and lower credit scores.
- Financial losses: ATO fraudsters can use stolen login credentials to make unauthorized purchases, transfer funds, or access other accounts linked to the victim’s account. This can result in significant financial losses for individuals and businesses. A study by Security.org found the average ATO to incur financial losses of around $12,000.
- Reputational damage: For businesses, ATO fraud can result in reputational damage, leading to a loss of customers and revenue.
- Chargebacks: Fraudulent transactions resulting from ATO attacks may come back as chargebacks, which can cause businesses to bear costs associated with disputing and processing them.
- Negative impact on user experience: ATO attacks can severely damage both user experience and brand reputation. For instance, eCommerce companies are obligated to keep user accounts safe, and failure to do so can harm their business through fraudulent transactions, payment fraud, user distrust, and negative brand reputation. eCommerce accounts are the most heavily targeted, making up 61% of ATO attacks, according to Intellicheck.com.
To prevent the ramifications of ATO fraud, proactive measures are imperative to protect sensitive information and monitor accounts for suspicious activity.
Digital Risk Protection
Secure your brand and customers against digital security risks
Account Takeover Fraud Prevention
As ATO fraud continues to escalate as a growing threat to individuals and businesses, there’s a heightened need to implement strategies to prevent such costly attacks:
- Set rate limits on login attempts: Organizations should set rate limits on login attempts based on username, device, and IP address. These limits can be determined based on the standard behavior of users as a benchmark to help prevent account takeover. You can also incorporate limits on the use of proxies, VPNs, and other factors.
- Employ password security policies: Ensure employees always use unique, strong passwords across their accounts. To manage a collection of passwords, use secure services like LastPass, 1Password, or Bitwarden to minimize the burden of exhaustive password management.
- Early detection: ATO prevention is possible with early detection. Stopping ATO requires understanding the attack timeline and solving for different attack patterns occurring in the first 18-24 months following a breach.
- Freeze compromised accounts: If an account is compromised, the first thing to do is to freeze it. This helps prevent attackers from performing actions like changing passwords.
- Implement multifactor authentication: Multifactor authentication adds extra layers of security to accounts by requiring an additional form of authentication, such as a code sent to a mobile device, in addition to a password.
- Leverage CAPTCHA: Instead of locking out an IP, fraud detection systems can display a CAPTCHA after a specific number of authentication attempts. The CAPTCHA could be required for a specified duration after too many authentication requests from the same IP address.
- Monitor accounts for suspicious activity: It is important to monitor accounts for suspicious activity, such as failed login attempts, changes to account information, and unusual transactions.
By implementing these prevention strategies, individuals and businesses can take the initiative to effectively prevent ATO attacks and better protect sensitive information and accounts from unauthorized access.
Account Takeover Fraud Protection
In addition to employing prevention strategies against account takeovers, several tools and solutions can help minimize the potential of ATO attacks.
Threat Intelligence and Monitoring
These tools monitor and analyze data from various sources, including known blocklists, data breaches, and suspicious online activities, to detect potential threats and account compromises. They can provide real-time alerts and help prevent fraudulent access attempts.
Account Activity Monitoring and User Profiling
Solutions that monitor user account activities, such as login history, transactions, and changes to account settings, can identify unusual or suspicious behavior. User profiling involves analyzing historical data and user behavior to establish patterns and detect anomalies.
User Education and Security Awareness Training
Cybersecurity training to educate users about common attack methods, phishing techniques, and best security practices can help prevent account takeover fraud. This includes promoting strong password hygiene, caution against sharing sensitive information, and providing guidance on recognizing and reporting suspicious activities.
IP Geolocation and Anomaly Detection
These tools analyze the geographic location and behavioral patterns associated with login attempts. They can identify suspicious activities, such as login attempts from unfamiliar locations or unusual login patterns, and trigger additional security measures or alerts.
Device Fingerprinting
This technique involves collecting and analyzing device-specific data, such as IP address, operating system, browser type, and cookies, to create a unique identifier or “fingerprint” for each device. Fingerprinting helps detect anomalies like login attempts from unrecognized devices and flags potential account takeover attempts.
Behavioral Biometrics
Behavioral biometrics solutions analyze user behavior patterns, including keystrokes, mouse movements, typing speed, and navigation patterns, to establish a baseline of normal behavior. Any deviations from the baseline can trigger alerts and indicate possible fraudulent activity.
It’s important to note that these tools and solutions should be implemented as part of a comprehensive cybersecurity and data protection strategy, as tailored to the specific needs of the organization or individual, and regularly updated to address emerging threats and vulnerabilities.
How Proofpoint Can Help
Proofpoint’s Targeted Attack Protection (TAP) is an advanced threat protection solution that helps organizations detect, analyze, and block advanced threats before they reach their inbox. TAP identifies and blocks advanced email threats, including ransomware and other advanced email threats delivered through malicious attachments and URLs.
TAP Account Takeover from Proofpoint is an add-on to TAP that extends its capabilities by detecting compromised accounts and protecting emails and cloud environments. It further defends threats that can lead to ATO attacks by focusing on:
- Visibility across the entire email account takeover attack chain: Proofpoint TAP ATO provides visibility across the entire email account takeover attack chain. It accelerates detection and response to ATO attacks, helping organizations to prevent and mitigate the impact of these attacks.
- Detecting compromised accounts: Proofpoint TAP detects compromised accounts and alerts security teams to take action. This helps prevent ATO attacks before they can cause damage.
- Preventing phishing attacks: Proofpoint helps prevent phishing attacks, a common method attackers use to access accounts. Proofpoint’s solutions use machine learning and other advanced techniques to detect and block phishing attacks.
- Protecting against data exfiltration: Proofpoint’s solutions protect against data exfiltration, which is a common goal of ATO attacks. Proofpoint’s solutions use advanced threat intelligence and analytics to detect and prevent data exfiltration.
By using Proofpoint’s solutions, organizations can prevent and detect ATO attacks, protecting their sensitive information and accounts from unauthorized access.




