For years, the Proofpoint Cloud Research team has been particularly focused on the constantly changing landscape of cloud malware threats. While precise future predictions remain elusive, a retrospective examination of 2023 enabled us to discern significant shifts and trends in threat actors’ behaviors, thereby informing our projections for the developments expected in 2024.
There is no doubt that one of the major, and most concerning, trends observed in 2023 was the increased adoption of malicious and abused OAuth applications by cybercriminals and state-sponsored actors. In January, Microsoft announced they, among other organizations, were targeted by a sophisticated nation-state attack. It seems that the significant impact of this attack, which was attributed to TA421 (AKA Midnight Blizzard and APT29), largely stemmed from the strategic exploitation of pre-existing OAuth applications, coupled with the creation of new malicious applications within compromised environments. Adding to a long list of data breaches, this incident emphasizes the inherent potential risk that users and organizations face when using inadequately protected cloud environments.
Expanding on early insights shared in our 2021 blog, where we first explored the emerging phenomenon of application creation attacks and armed with extensive recent discoveries, we delve into the latest developments concerning this threat in our 2024 update.
In this blog, we will:
- Define key fundamental terms pertinent to the realm of cloud malware and OAuth threats.
- Examine some of the current tactics, techniques, and procedures (TTPs) employed by threat actors as part of their account-takeover (ATO) kill chain.
- Provide specific IOCs related to recently detected threats and campaigns.
- Highlight effective strategies and solutions to help protect organizations and users against cloud malware threats.
Basic terminology
- OAuth (Open Authorization) 2.0. OAuth is an open standard protocol that enables third-party applications to access a user’s data without exposing credentials. It is widely used to facilitate secure authentication and authorization processes.
- Line-of-business (LOB) applications. LOB apps (also known as second-party apps) typically refer to applications created by a user within their cloud environment in order to support a specific purpose for the organization.
- Cloud malware. A term usually referring to malicious applications created, utilized, and proliferated by threat actors. Malicious apps can be leveraged for various purposes, such as: mailbox access, file access, data exfiltration, internal reconnaissance, and maintaining persistent access to specific resources.
- MACT (Malicious Applications Created in Compromised Credible Tenants). A common technique wherein threat actors create new applications within hijacked environments, exploiting unauthorized access to compromised accounts to initiate additional attacks and establish a persistent foothold within impacted cloud tenants.
- Apphish. A term denoting the fusion of cloud apps-based malware with phishing tactics, mainly by utilizing OAuth 2.0 infrastructure to implement open redirection attacks. Targeted users could be taken to a designated phishing webpage upon clicking an app’s consent link. Alternatively, redirection to a malicious webpage could follow authorizing or declining an application’s consent request.
- Abused OAuth applications. Benign apps that are authorized or used by attackers, usually following a successful account takeover, to perform illegitimate activities.
What we are seeing
Already in 2020, we witnessed a rise in malicious OAuth applications targeting cloud users, with bad actors utilizing increasingly sophisticated methods such as application impersonation and diverse lures.
In October 2022, Proofpoint researchers demonstrated how different threat actors capitalized on the global relevance of the COVID-19 pandemic to spread malware and phishing threats. Proofpoint has also seen this trend include the propagation of malicious OAuth applications seamlessly integrated into phishing campaigns or disseminated via alternative vectors. Another widely-observed tactic, known as “Apphish,” leverages OAuth implementation flaws to redirect users to malicious phishing webpages.
Fast forward to the present, and the landscape has undergone further transformations. In 2023, our researchers have seen attackers prioritizing using OAuth apps created within compromised (and often verified) cloud tenants. However, attackers are not leveraging OAuth apps merely to gain a foothold within impacted cloud environments; They are continuously harnessing the trust associated with verified identities to distribute multitenant cloud malware across organizations.
In conjunction with the relevance of cloud malware threats, Proofpoint analysts have also identified a recent increase in the number of account takeover incidents involving application abuse. Threat actors were observed authorizing popular benign apps in order to maintain persistent access to valuable resources post-compromise.
Based on our research, around 16% of the organizations we monitored in 2023 experienced at least one incident involving cloud malware threats. This includes instances of authorized malicious applications and the exploitation of benign applications. Additionally, there has been a steady rise in the proportion of benign application abuse, accounting for 20% of all categorized threats related to OAuth apps.
These insights drove our threat research team to implement advanced detection mechanisms aimed at identifying unauthorized usage of OAuth applications.
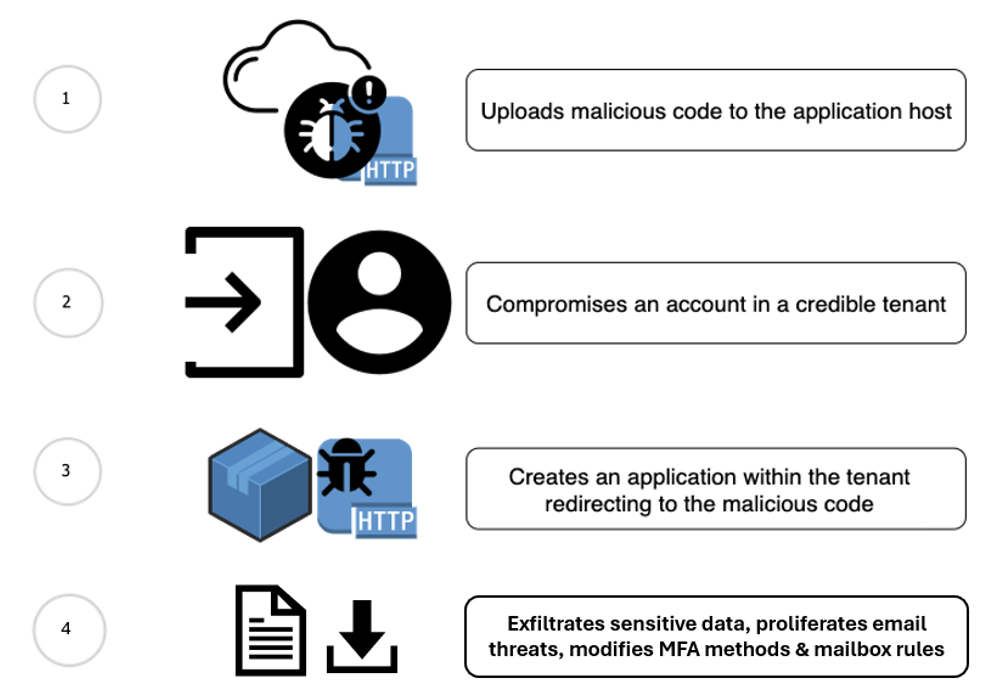
Steps taken by an attacker as part of the MACT kill chain.
Understanding MACT
Attackers leverage compromised cloud environments to create seemingly legitimate OAuth applications, mimicking the functionality of trustworthy services. Once permission to these apps is granted, attackers gain access to data and resources associated with the compromised account based on the app’s requested scopes.
Our analysis shows that the majority of observed MACT incidents occur in hijacked Microsoft 365 environments. In the past, malicious apps created by attackers were commonly marked as “multi-tenant application.” This allowed threat actors to freely proliferate OAuth threats to external tenants, infecting additional cloud environments.
However, not all malicious second-party OAuth apps are used to target external environments. It seems attackers began pivoting to flagging their second-party apps as ‘internal’ and using them to maintain persistent access to resources within already-compromised tenants.
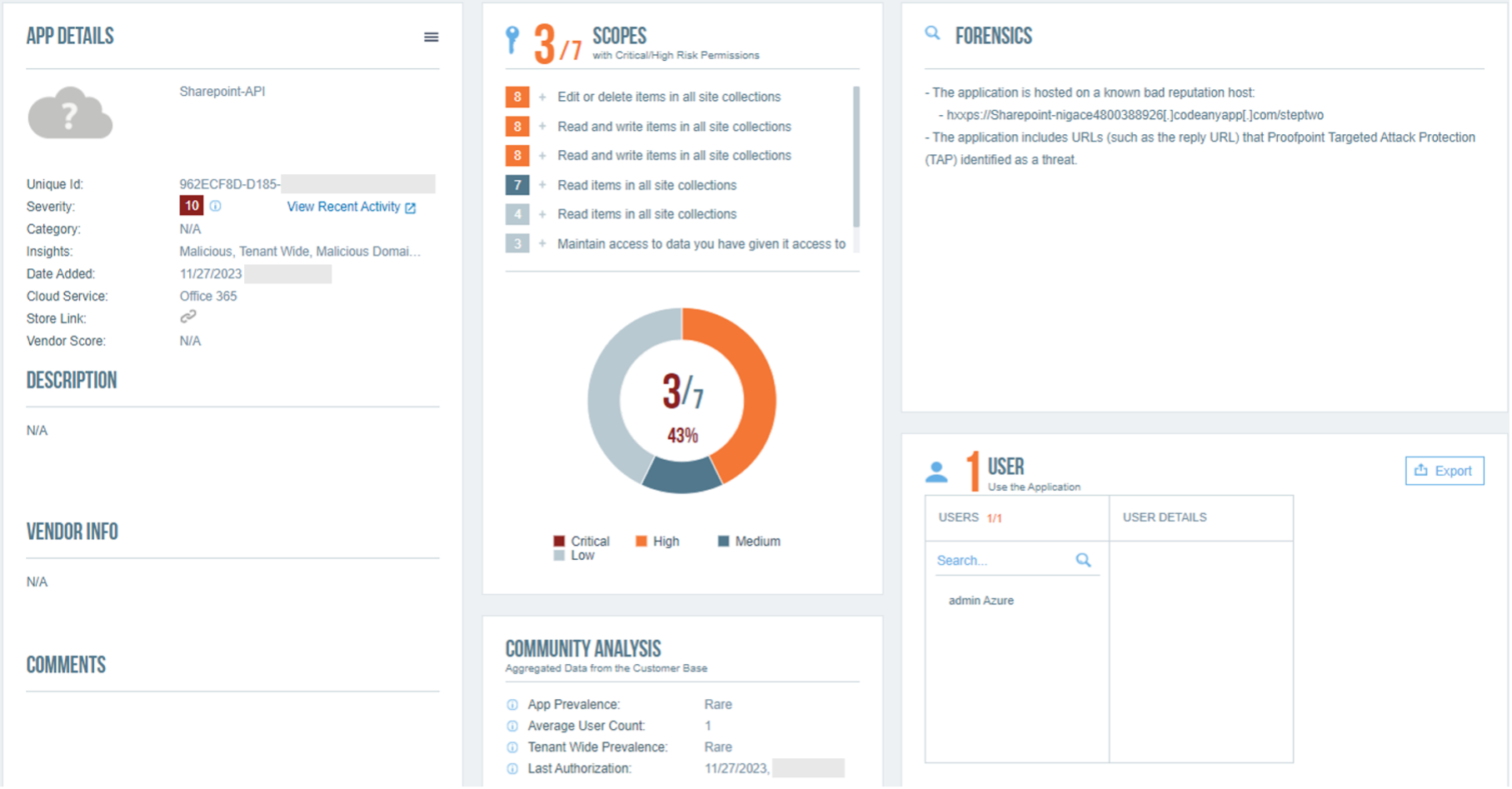
A malicious application created within a compromised Office 365 environment by an admin service account, as detected by Proofpoint’s CASB.
Recent cloud malware attacks
As part of this trend, Proofpoint researchers have recently been able to condemn over 50 malicious OAuth applications, linking most of them to 2 distinct cloud malware campaigns, known as MACT campaigns 1204 and 1445.
- MACT campaign 1204. A campaign using at least 5 internally created multitenant applications. These applications, referenced by Microsoft Threat Intelligence in a blog released in December 2023, share a common naming pattern (“App”), reply URL, and similar scopes. Although these apps are now disabled, their permission suite allowed attackers to exploit them for extensive data exfiltration and to target additional user accounts with high volumes of phishing threats. Currently, no active apps attributed to this campaign have been identified.
- MACT campaign 1445. Encompassing at least 40 multitenant apps, this ongoing campaign uses unique naming patterns and similar scope sets. Notably, 28% of apps were named after the compromised user account with which they were created, while 20% were labeled as “Test” or “Test App” by attackers. For almost half (44%) of all applications, attackers opted for arbitrary strings as the designated names. Interestingly, MACT Campaign 1445 applications also employ an anomalous URL as their reply URL – a local loopback with port 7823 [“http://localhost:7823/access/”]. Port 7823, utilized for TCP traffic, is associated with Amitis, a Windows remote access trojan. Out of over 40 identified malicious apps attributed to MACT Campaign 1445, several are still active.
- Unattributed attacks.
- In another exemplary incident, currently unattributed to any known campaign, Proofpoint’s threat detection engine has surfaced a malicious application created by a hijacked admin user account. Named “Sharepoint-API,” this application was set up as multitenant and granted a distinct set of permissions, including full access to SharePoint and offline capabilities. A Reply URL linked to this application exhibits indications of potential domain impersonation and is associated with known phishing web pages.
- In other cases, Proofpoint researchers came across “Apphish” threats created within compromised credible tenants and utilized by phishing campaigns, thus constituting a MACT-Apphish hybrid.
Given the current limited extent of affected organizations and users, these highlighted campaigns’ velocity is considered low.
However, as long as authorized malicious apps remain enabled, they have the capacity to spread to both internal and external user accounts, amplifying the potential reach and impact of these attacks.
Malicious apps created within a credible tenant by a compromised user account and attributed to MACT Campaign 1445.
|
Campaign |
Threat Type |
# Detected Malicious OAuth Apps |
Name Samples |
Max Permission Suite |
Velocity |
|
MACT Campaign 1445 |
MACT; Multitenant |
40+ |
“Test App”, “Test”, “Sampler”, “System”, “ewasdf” |
Openid Mail.send Mail.read Mail.readbasic Offline_access Profile |
Low |
|
MACT Campaign 1204 |
MACT; Multitenant |
5+ |
“App” |
Mail.Send User.Read Mail.ReadWrite offline_access |
Low |
|
Unattributed Attacks |
MACT; Multitenant |
1 |
“Sharepoint-API” |
User.Read AllSites.Write AllSites.Read Sites.ReadWrite.All Sites.Read.All offline_access |
Low |
|
MACT + Apphish |
2 |
“NCMSN”, “MNXXN” |
- |
Medium |
Recent cloud malware campaigns involving malicious apps created in compromised tenants.
Takeaways and recommendations
The risks of application creation attacks and malicious OAuth applications stress the importance of continuous vigilance in the cybersecurity landscape. By recognizing the risks and implementing effective prevention and remediation measures, organizations can boost their defenses against this form of attack. Adopting a proactive approach is key to maintaining the integrity and security of valuable organizational assets.
Proofpoint informed its affected customers about the identified threats and their associated risks, upon detection. Using Proofpoint’s ATO Detection Engine, affected parties gained visibility, insights, and access to automated remediation policies, thereby minimizing attackers’ dwell time and limiting their impact, thus mitigating potential damages. Proofpoint continues to support its customers through Incident Response services and ongoing guidance.
Here are some recommendations to help protect your organization and users from cloud malware threats:
- Audit authorized applications within your cloud tenant for excessive privileges. Consider the application’s source or publisher when permitting access to key resources.
- Limit application creation permissions. Microsoft allows admins to prevent non-admin users from creating applications with a policy. This will reduce the risk of attackers compromising non-admin accounts and creating applications in the hijacked environment.
- Watch out for potential user impersonation. Applications with ApplicationImpersonation privileges can easily mimic a user account.
- Reduce the attack surface.
- Identify cloud account takeover incidents in your environment.
- Identify post-access activities, including application authorization, tied to account compromise.
- Automatically revoke applications authorized by a potentially compromised account or within a suspicious session.
- Utilize a comprehensive app catalog, including detailed scoring for 3rd party applications.
- Review applications’ requested permissions.
- Review applications’ source and publisher.
- Regularly revoke unused applications.
- Use Microsoft’s “verified publisher” policy. While some credible tenants host malicious applications, non-credible tenants tend to host cloud malware even more.
Organizations interested in scanning their cloud environments for cloud malware threats can contact Proofpoint for further details and threat-hunting tips from our threat researchers. For more information on how Proofpoint can help protect your organization against these and other cloud threats, please check out our cloud security resources or contact us.
Indicators of compromise
In order to avoid potential exposure of impacted organizations’ and user accounts’ details, malicious application IDs were partially redacted.
|
Indicator |
Type |
Description |
Status |
|
ab91fd4f-d852-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
baf0c4d0-68dd-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
d7f167e6-c4fa-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
e2f1f708-8fde-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
7b22f132-6bd4-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
3c7bed6f-d2cc-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
ba6c467b-79d9-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
8dc6bf96-5645-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
a68cc0e6-ffbe-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
950f9e4e-4a8b-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
8928034b-5ba0-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
88593216-77a8-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
43f2cf24-b3e1-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
fbe36179-2752-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
3b26cb89-7502 -XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
7f8de6ea-90df -XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Active |
|
46e032e2-3d0b-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
aab10050-9676-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
7879f119-1a1c-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
a6252307-b0b4-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
a933558c-2933-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
24c329b1-5b5d-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
bf9f9cb3-2653-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
08865e47-bd93-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
4b910f87-7c56-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
83cf963a-91fb-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
d32b7c3a-c5e1-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
096ac744-b19c-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
cff61a6f-3b96-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
ea8ad615-e7bf-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
304f5079-26c0-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
ee23286d-11ee-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
2f22a4d5-a73b-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
222ce256-14e9-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
2b6f1a8c-7c3c-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
784c6a1f-7a5a-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
dec7dfb2-4cc1-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
0d592cf1-863b-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
184eadb2-dcb3-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
a2e8ef14-e61f-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
0ee8423d-11a2-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1445. |
Disabled |
|
5f09265d-3185-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1204. |
Disabled |
|
1e925616-beb1-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1204. |
Disabled |
|
8029cad1-c764-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1204. |
Disabled |
|
90b43af9-e66a-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1204. |
Disabled |
|
58af928c-d636-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1204. |
Disabled |
|
93f42032-2fbe-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app, attributed to MACT Campaign 1204. |
Disabled |
|
962ecf8d-d185-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app. |
Active |
|
fd997549-3053-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app; Apphish. |
Disabled |
|
3c5d6000-2a7e-XXXX-XXXX-XXXXXXXXXXXX |
Application ID |
Malicious second-party app; Apphish. |
Disabled |
|
https://sharepoint-nigace4800388926[.]codeanyapp[.]com/steptwo |
URL |
Reply URL used by malicious application. |
- |
|
https://teste-shaepoint-files[.]azurewebsites[.]net/steptwo |
URL |
Reply URL used by malicious application. |
- |
