In my previous blog, I detailed how Proofpoint has redefined email security, a central pillar of what Gartner has termed Human-Centric Security, one of their three strategic priorities for CISOs in 2024 and 2025. Now I’d like to give you an idea of how we think human-centric security fits with the rest of the modern security stack and how the current trend toward more comprehensive security solution architectures is influencing our strategic direction.
The Third Era
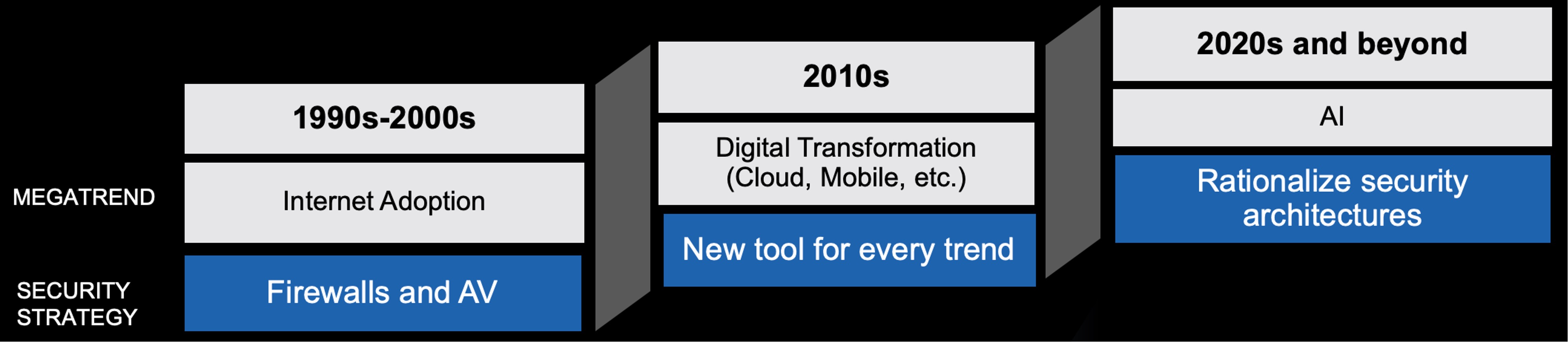
It's worthwhile to start with a bit of history. In our view, we’ve entered the third major evolution of cybersecurity. In the earliest period, the perimeter was established, and basic controls were put in place. The technologies were fewer and less capable, but the consequences of security failures were nowhere near as severe as they are now.
In the second era, the perimeter largely dissolved and the rapid adoption of new technologies during the heyday of digital transformation led to a massive proliferation of point security solutions, cropping up nearly as fast as the tools they were meant to secure. Unfortunately, the cost of the security engineering, operational integration, and alert response required for these tools to be effective often outweighed the risk mitigation they provided.
Now we’ve arrived a phase where the security architectures of the future are finally taking shape. They share several key characteristics: they’re highly integrated, cloud-deployed, and align to what security teams really need to protect: their infrastructure, the apps that run on it, the data that powers those applications, and of course, the humans that simultaneously constitute their organization’s greatest asset and biggest risk.
The Pillars of a Modern Security Architecture
To protect the spectrum between infrastructure and people, five key control planes have emerged. The first of those components is the network, where controls have moved past the classic confines of the firewall, proxy, VPN, and other network devices to the cloud-based consolidated services that make up the modern Secure Access Services Edge (SASE). Secondly, endpoint and server protection evolved into first Endpoint Detection and Response (EDR) and then XDR as servers were increasingly replaced by cloud workloads. That, of course, leaves the human element, to which I’ll return shortly, and the two cross-architecture layers: the operational processes, increasingly automated, that drive the controls and respond to the alerts they generate, and the identity fabric, both human and machine, that ties everything together.
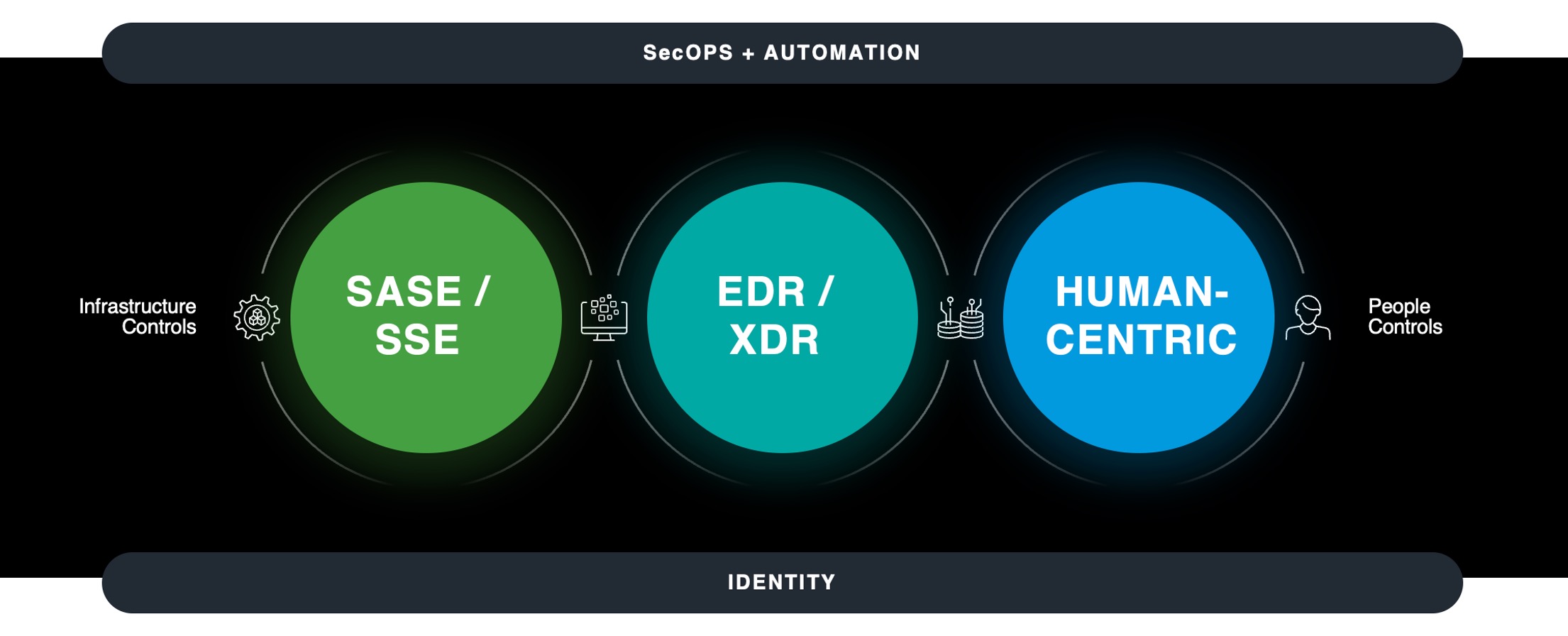
These architectures are powerful on their own, and their effectiveness compounds when they’re well integrated. Attackers have often exploited the gaps between poorly implemented and monitored security controls to pass from a compromise of a person’s credentials through the network to the administrative privileges that make ransomware so disruptive. Frustrating adversaries becomes much more achievable when well-integrated security controls reinforce each other, providing not just defense in depth but also defense in breadth. For example, an attacker’s job is much harder when the malicious attachment they use to try and target a person is blocked and analyzed, with the resulting intelligence shared across SASE and XDR.
Human-Centric Security and the Ecosystem
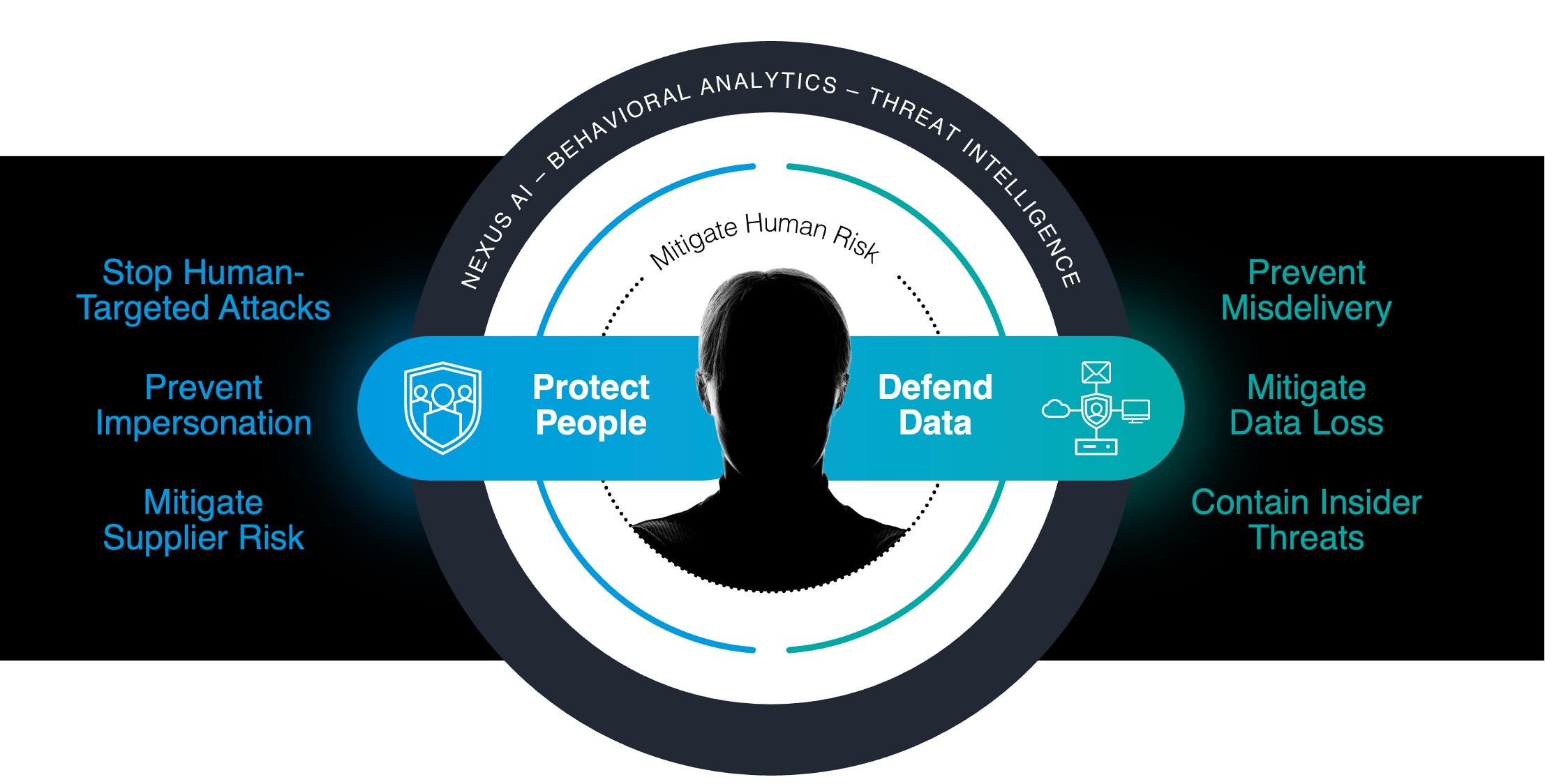
With the rise of these modern security architectures, our controls for protecting networks, endpoints, and infrastructure have evolved, becoming more comprehensive, adaptive, and effective. With over 90% of breaches involving the human element, Proofpoint’s human-centric security platform uniquely does the same for people and integrates with the key leaders across the other five components of the modern security stack.
In pioneering human-centric security, we’ve brought together previously disconnected functionality to accomplish two critical goals. The first is helping organizations protect their people from targeted attacks, impersonation, and supplier risk, along with making their people more resilient and cyber aware. The second is to help them defend their data from users that put it at risk, whether by mistake or intentionally.
The path forward for Proofpoint will be to focus on giving our customers the best solution to solve this problem leveraging modern AI technologies, behavior analysis and threat intelligence. Plus, we’ll be delivering deeper, more comprehensive technology integrations with our peers across these architectural domains, from SASE/SSE and XDR on the infrastructure side to identity and security operations. We will build upon our existing partnerships —including Palo Alto Networks, CrowdStrike, Microsoft, CyberArk, Okta and many more—to enhance outcomes for our joint customers.
Our integrations enable defense in depth while enabling security operations at scale, what all enterprises need. A Proofpoint customer can, for example, connect to CrowdStrike Falcon, Microsoft Defender, or Palo Alto Wildfire to ensure that intelligence and detection opportunities are automatically linked across protection layers that may see different aspects of a given threat. Additionally, we’ve delivered adaptive controls based on our unique visibility into human-centric risk, leveraging Okta’s Identity Cloud to deliver stepped up authentication for Very Attacked People and CyberArk to ensure that a potentially compromised privileged user can’t have their account abused by a ransomware actor.
The Future is Almost Here
We’ll continue to build upon these integrations, and we’ll have much more to share in the next few quarters, around taking these integrations to the next level. At our reimagined Protect event series, we’ll be joined by other leaders in cybersecurity to lay out our shared vision of a better future in which our respective platforms become more than the sum of their parts. Want to hear about it first? Register here for the event nearest you.

