The Proofpoint Aegis threat protection platform uses data, detection and research to provide actionable insights that help form a complete picture of the threats your business faces—and the best ways to defend against them.
In earlier blog posts, we’ve focused on actionable insights and what you can do to enhance your security posture. We’ve covered people risk, origin risk and business email compromise (BEC) risk. And we’ve explored why ensuring proper context is critical for your insights.
In this post, we look at a newer yet already prevalent threat type—telephone-oriented attack delivery (TOAD) phishing attacks. We also explain how Proofpoint detects these threats and discuss the value of reporting on TOAD attacks through actionable insights in the Proofpoint Targeted Attack Protection (TAP) Dashboard.
What is a TOAD attack?
A TOAD attack is a relatively new form of phishing attack that combines voice and email phishing techniques. Attackers aim to trick users into disclosing sensitive information over the phone, such as login credentials or financial data, by impersonating a trusted authority figure. They will get on a call with the victim, claiming to be a representative from a reputable company or organization. Then, they will follow up with an email that contains a phishing link or attachment.
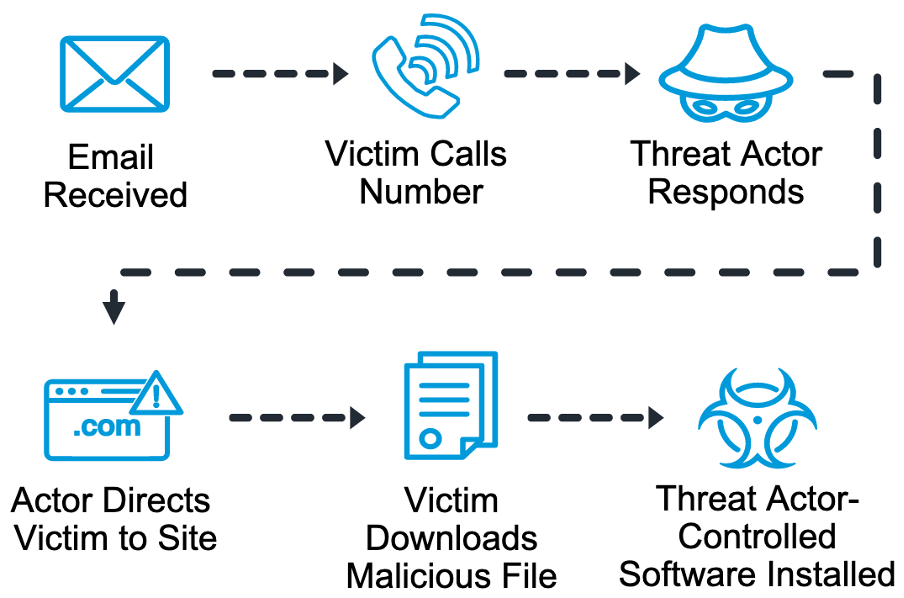
TOAD attack technique.
What makes TOAD attacks particularly dangerous—and effective—is attackers’ use of social engineering tactics to build trust and credibility with their victims. By pretending to be a representative from a trusted entity, an attacker attempts to bypass many of the usual defenses that a company has in place to protect against phishing attacks.
How does Proofpoint detect TOAD attacks?
At Proofpoint, we understand the importance of protecting our customers from the rising threat of TOAD attacks. That is why we developed advanced threat intelligence and machine learning that can detect TOAD phishing attacks and prevent them from succeeding.
Proofpoint Aegis analyzes data from various sources, including email, network and cloud data, to identify general indicators of compromise. And our Supernova Behavioral AI engine uses machine learning algorithms to analyze email content and identify suspicious patterns of behavior that may indicate a TOAD attack is in progress. These two solutions work together to block malicious emails and URLs that are associated with TOAD attacks as soon as they are received.
Insights
By reporting on TOAD attacks through actionable insights in the Proofpoint TAP Dashboard, our customers can gain valuable insights into the threat landscape—and stay one step ahead of attackers. The dashboard provides real-time visibility into the number and type of TOAD attacks that have been detected. It also offers detailed information about the tactics, techniques and procedures that the threat actors are using.
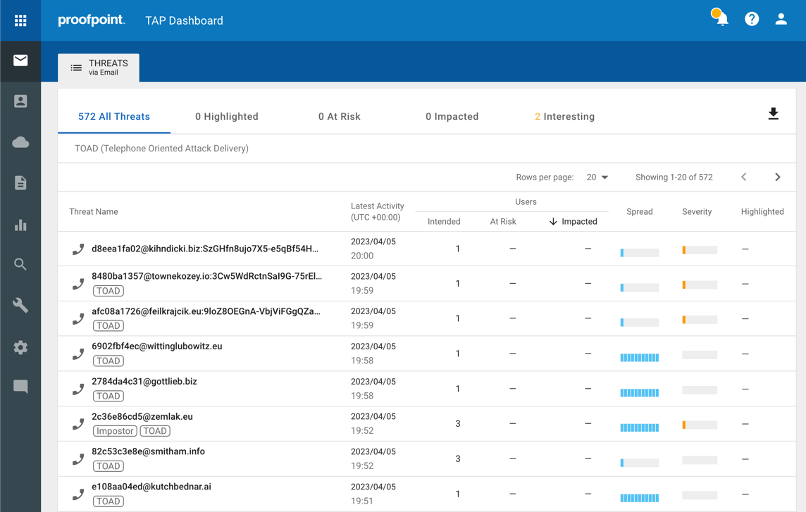
TOAD threat reporting shown in the Proofpoint TAP Threat Insights Dashboard.
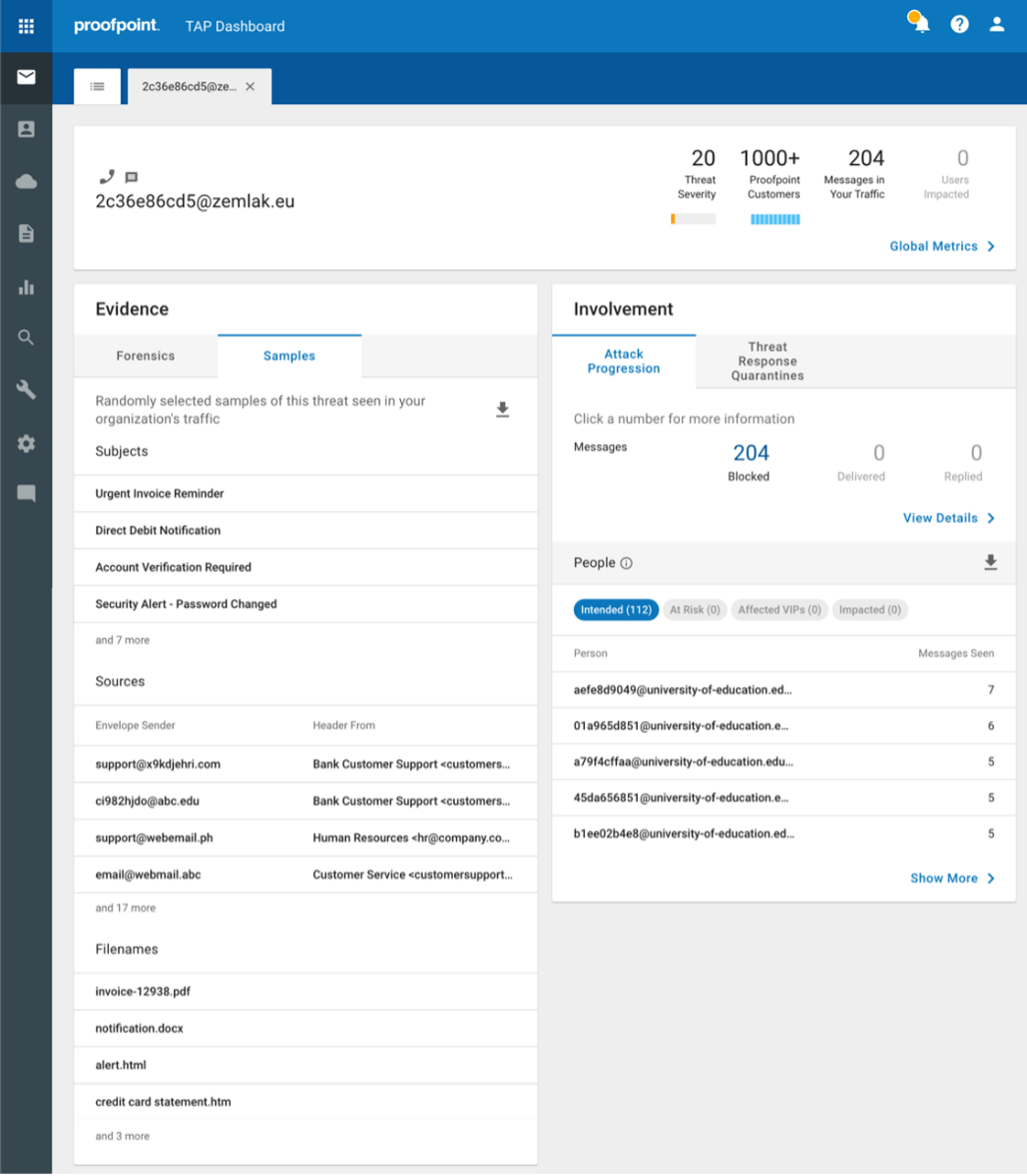
TOAD threat details displayed in the TAP Dashboard.
Targeted controls
Proofpoint Aegis provides targeted controls to help companies focus on particular actions and evaluate the impact of those actions on performance. This capability provides an advantage when you are attempting to optimize your cybersecurity measures or pinpoint areas requiring more attention.
Here are examples of actions that you can take with targeted controls:
- Call blocking. Block calls from known malicious numbers or send warning messages to employees who receive suspicious calls.
- Email filtering. Use Effectiveness Reports to evaluate how well your email filtering stops TOAD threats. If you notice many TOAD threats are getting through, you can adjust your email filtering settings or add more layers of protection.
- User education. Our Very Attacked People™ reports can help you understand how well your user education initiatives are working. The reports also help you to identify individuals that may require additional security awareness training.
Value
TOAD phishing attacks are a serious and growing threat. So it’s essential to have the right tools in place to detect and prevent them. By using the TAP Dashboard to track and report on TOAD attacks, your business can better understand the risks associated with them. That, in turn, can help you to develop more effective strategies to reduce the risk of users falling victim to this type of attack.
You can use the TAP Dashboard to monitor the effectiveness of existing security controls and make informed decisions about where to boost protection. Using the dashboard can also help your business to meet compliance requirements and provide evidence of due diligence in the event of a security incident.
Get more insight into your company’s specific digital risks
If you want to know the biggest digital threats to your business, reach out for a free Rapid Email Risk Assessment. One of our security experts can help you to identify some of the most significant digital threats your business faces, like domain risk—and they can show you how to mitigate them.
Learn more about the Threat Insights Dashboard and actionable insights in Proofpoint TAP.

