The modern workplace has expanded beyond email. Attackers now exploit collaboration tools, supplier relationships and human trust to bypass defenses and compromise accounts. This five-part blog series raises awareness around these shifting attack tactics. And it introduces our holistic approach to protecting users.
In our past installments, we have covered one attacker’s tactics for exploiting new digital channels, why these channels are vulnerable and how business communications are compromised. Now in Part 4, we explore the importance of security awareness.
Humans are the primary target for attacks
As social engineering attacks evolve, attackers are using more than just email. They’re expanding their reach across different channels. With the help of AI and automation, they can personalize their attacks and create more convincing messages. This allows attackers to scale their attacks, making it harder for traditional security measures to detect and stop them.
Employees remain the primary targets of these attacks. And security awareness plays a crucial role in supporting them. However, if it’s going to be effective at helping people spot socially engineered attacks, security awareness training needs to evolve. It’s time to shift away from basic training toward driving behavior change.
This blog post takes a closer look at social engineering and why it’s a top tactic for cybercriminals. It also explores why traditional security defenses are no longer sufficient to protect people against these ever evolving, complex attacks.
Social engineering leads to account compromise
Traditional hacking methods exploit technical vulnerabilities in systems. But many of today’s successful cyberattacks don’t use these tactics. Rather, they begin with a well-crafted social engineering scheme. What makes these attacks so effective is that they prey on human psychology, manipulating peoples’ emotions, instincts and human vulnerabilities.
Social engineering works by exploiting trust, fear, urgency and curiosity to manipulate people into doing what an attacker wants them to do. This might mean sharing sensitive data, transferring money or granting access to a system, application, database or device.
These initial exploits are often only the first step in a multistage attack starting with compromising a user account. They can lead to much more complex attacks where attackers steal data, commit financial fraud and gain unauthorized access to other parts of an environment to cause havoc.
What’s worse is the use of AI and automation enhances the scale and sophistication of social engineering attacks. AI algorithms are used to identify ideal targets within corporate environments, develop convincing personas, and fabricate plausible scenarios to manipulate unsuspecting targets effectively. Attackers can adapt their strategies in real time, amplifying and relentlessly scaling their attacks. Attackers are armed with launching dynamic, AI-driven attacks that outpace conventional defenses, leaving organizations vulnerable.
These are just a few ways an AI cyber attack can help cybercriminals succeed:
- Collect sensitive information automatically. Platforms like Social-Engineer.com can automate the process of collecting sensitive information from unsuspecting victims.
- Create realistic fakes. Tools like DeepFaceLab or Descript's Overdub and vishing (voice phishing) tools enable attackers to create hyper realistic fake videos or audio clips or simulate realistic phone calls from a trusted entity. These can be used in telephone and voice phishing or video impersonation attacks, making the deception even more convincing.
- Automate and scale attacks. With automated tools, attackers can scale their attacks and increase their likelihood of success. Tools like Autopilot and Hootsuite are legitimate marketing and social media management tools that can be used for automating tasks like email campaigns and social media posts. However, attackers repurpose them for malicious purposes to amplify and relentlessly scale their attacks.
Why technical defenses aren’t enough
Threat actors’ goals haven’t changed. But the digital workspace has expanded.
Traditionally, security tools have focused on keeping email safe. And while email remains the primary threat vector, digital transformation has given people new ways to communicate and collaborate. Employees use Microsoft Teams, Slack, social media and file-sharing platforms. Not surprisingly, attackers are now exploiting these platforms, providing more opportunities to manipulate users through social engineering.
Attacks are designed to be deceptive. Bad actors use carefully crafted messages and tactics that mimic legitimate communications. This creates an illusion of authenticity and makes it harder for people to know what’s legitimate and what’s malicious. No technical security solution is 100% effective. With AI-driven phishing and automation, attackers can adapt faster than security controls can keep up. Organizations cannot rely on technical controls alone and need to build human resilience against human-targeted social engineering threats.
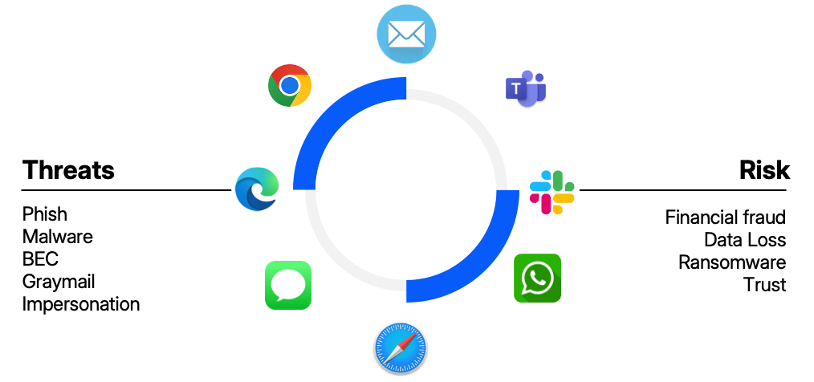
Threats and risks across digital workspaces.
Can you spot a phishing threat?
It’s harder to spot threats than you might think. Three messages are below. Can you spot which ones are phish?
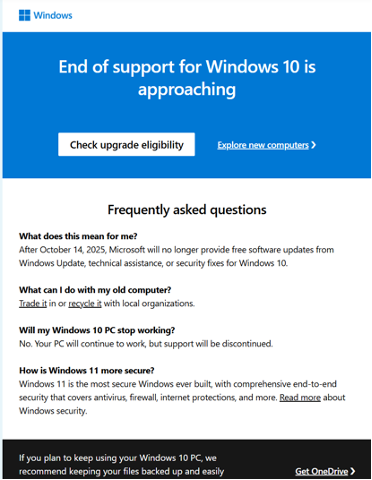
1. Microsoft Windows email message
2. A digital ad from a familiar brand used during a big seasonal sporting event

3. An internal message from IT support delivered in Microsoft Teams
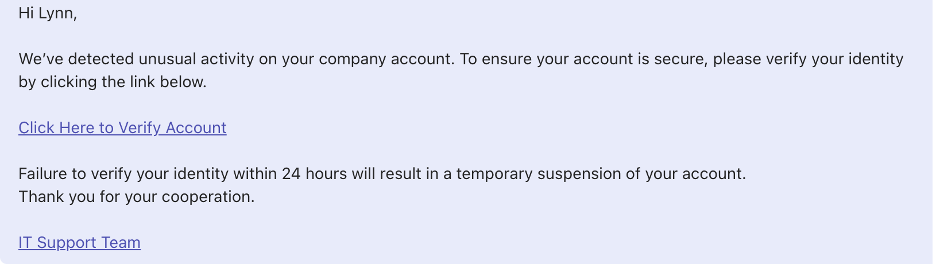
The correct answer: All three examples are based on real-world phishing attempts.
Key social engineering indicators
It can be difficult to spot a phish. Here are some tips for what to look for:
- Urgency. The message creates a sense of urgency and pressures the user to take action before a date or deadline, or a promotional period
- Suspicious links. Links and buttons such as “Check upgrade eligibility,” "Get OneDrive," “Verify Account” and “promotional code” are designed to look authentic, but instead they are directed to phishing websites
- Generic language. The message is vague and does not provide specific information about the issue
- Impersonation of a trusted entity. The message appears to be from a trusted brand or an internal IT-related team, using reputation to gain credibility
- Request for action. A message prompts the user to click links to check eligibility, take advantage of a promo or explore other offers
Why implement an effective behavior change program
With many sophisticated social engineering tactics out there, users really need to be prepared. One of the most effective ways to help them is with a security awareness program that helps them to recognize the signs of a social engineering attack. They should be able to spot attacks that are coming from unexpected channels as well as those that use advanced techniques.
However, security awareness isn’t enough to empower employees to be active defenders. Consider 96% of users who took risky actions did so knowingly, highlighting a critical gap in compliance-based training. Successful security assignments and passed phishing tests are no guarantee that your employees will be resilient against social engineering attacks. Security awareness programs must evolve and focus on delivering personalized, risk-based guidance and adaptive learning to empower real-world behavior change.
Security awareness and behavior change programs are essential. They form a critical foundation by preparing and empowering employees to make safe choices in today’s digitally transformed world. But if you want employees to be resilient in the face of multichannel and multistage attacks, they need extra support. And you need an extra layer of protection. That’s where Proofpoint can help. Organizations require a human risk management strategy that combines technology and education into comprehensive protection.
Protect your people with human-centric security
As digital workspaces expand, attackers continue to target people. While email remains the primary threat vector, cybercriminals are exploiting new channels like messaging collaboration platforms, cloud apps and file-sharing services. This has created a fragmented security landscape with disconnected point products, resulting in higher operational costs and increasing security gaps. This is where Proofpoint can help.
Proofpoint Prime Threat Protection provides a single, comprehensive solution to defend against all human-centric threats, both current and emerging. It combines a wide range of security protections to help you maximize threat prevention. It features:
- Accurate threat detection—Helps prevent the widest variety of threats
- AI-powered account protection—Defends against account takeovers and compromised supplier accounts
- Risk-based targeted training—Guides users to make safer choices when faced with threats
- Phishing protection across platforms—Blocks malicious links from multiple platforms
- Impersonation protection—Protects your brand reputation from being abused
- Human risk management—Identifies high-risk users and automates adaptive security controls
With Proofpoint Prime, you can better protect your people and business by reducing alert fatigue with highly accurate threat detection, improved efficiency through detailed risk insights and automated security workflows. Combined with pre-built integrations and shared threat intelligence, your security and IT teams can accelerate deployments while reducing costs by eliminating fragmented point solutions across your organization.
Learn more about Proofpoint Prime. Or download our Prime Threat Protection solution brief.
Stay tuned to learn more
In our next blog, we’ll explore why MFA isn’t enough to defend against evolving attacks.
Read our Expanding Attack Surface series
Learn more about the threat landscape and get insights about how to stop evolving attacks:

