Mobile malware and SMS phishing, or “smishing,” lures have converged during the pandemic, as cyber criminals piggyback on the surge in online shopping and package delivery. This development has been particularly damaging as people tend to trust mobile messages more than email, making this piece of social engineering one of the year’s stand-out threats.
Mobile attacks on the move
Over the course of 2021, smishing has jumped more than 80% worldwide. In the first half of the year, more than 60% of global enterprises said that their employees were targeted by smishing attempts, with that number rising to more than 80% for U.S. businesses. And yet knowledge of the problem remains low, with only around 30% of people aware of the danger.
Cyber criminals recognize that mobile messages are read more quickly and with less scrutiny than email, and are often received on devices that have access to both personal and business accounts. Mobile phones have become an extremely lucrative target, offering several monetization opportunities through a single compromise, ranging from simple identity theft to invoice fraud.
And smishing isn’t the only way that attackers are looking to take advantage. 2021 has also seen a spike in mobile malware, led in no small part by the appearance of FluBot. This malicious application has lived up to its name, crossing borders and infecting Android devices across several continents. FluBot can already deploy overlays on around 200 different financial apps, and with several even more powerful malware applications already in circulation including TangleBot, the threat will continue to grow in 2022.
One lure to rule them all
What increasingly unites both smishing attacks and mobile malware is the nature of the lures being utilized. In Q3 of this year, almost 50% of smishing messages sent globally were themed as package delivery notifications, alerts or related lures. Likewise, FluBot is commonly spread using messages purporting to be from reputable logistics firms such as FedEx and UPS.
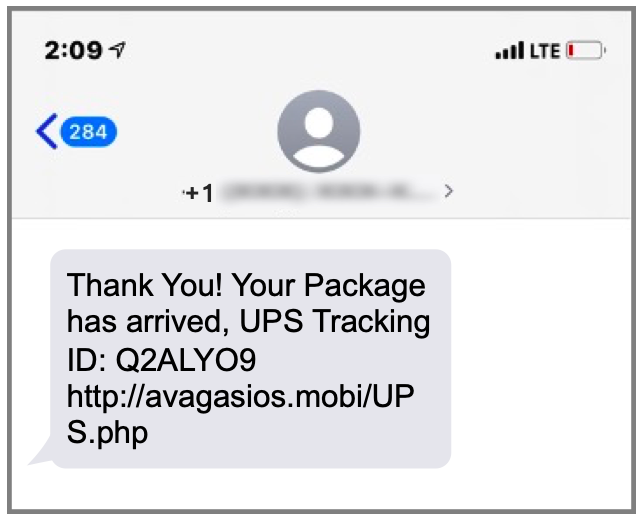
Fig. 1 An example of a delivery lure leading to a smishing page
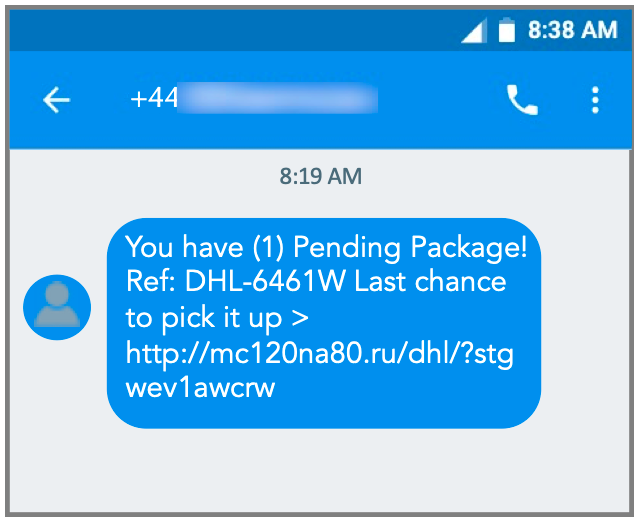
Fig. 2 An example of a delivery lure leading to malware download
Attackers have standardized around package delivery-based lures, and as these two examples show, there is almost no discernible difference between a smishing message and a mobile message containing a URL linking to malware. In both cases, the attacker relies on the fact that people rarely think twice about clicking on these messages, especially as no one likes the thought of missing a delivery because they didn’t respond in time. Also in the attacker’s favor is the fact that we have not yet learned to distrust mobile messaging the way twenty-plus years of spam and malware have taught us to distrust email.
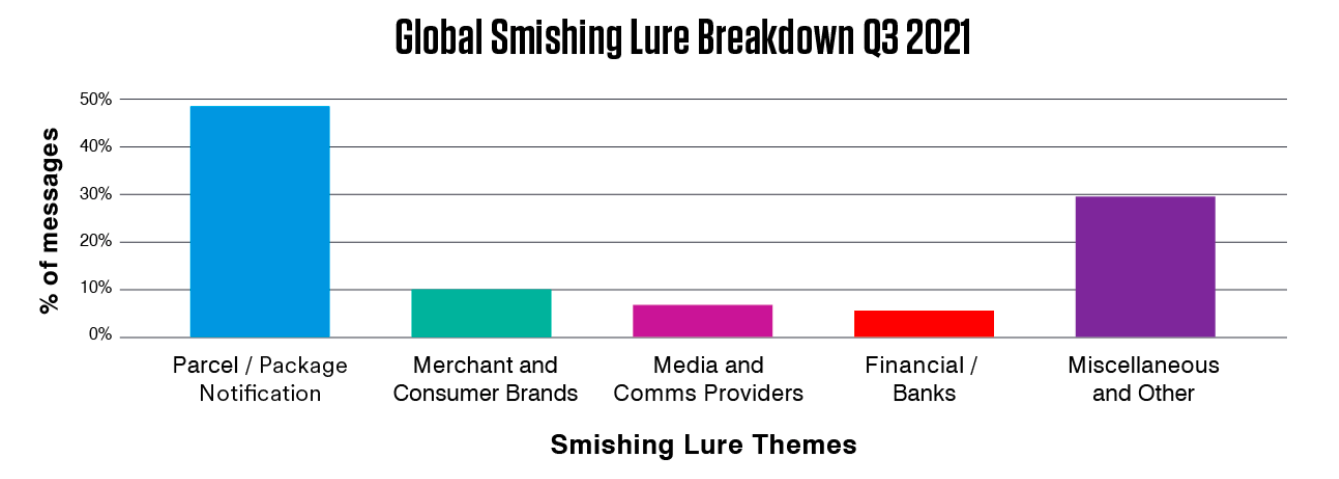
Fig 3. Common themes for smishing lures
A problem for everyone
Mobile’s centrality to both our personal and professional lives means that a single compromise can do damage to several parties.
At the consumer level, people risk having their personal information stolen and financial loss from compromised banking credentials.
At the carrier level, network operators face decreased consumer trust and increased customer support costs; very high-volume attacks can even degrade network performance.
And at the enterprise level, it’s a smorgasbord of risk. Impersonated businesses suffer brand erosion while targeted employees can have corporate credentials stolen, potentially putting networks at risk of data theft and even ransomware infection.
And with advanced malware like TangleBot now including camera and microphone access, we may not have to look too far into the future for mobile compromise to be a source of audiovisual deep fakes, which will enable ever more sophisticated forms of invoice fraud and bigger business losses.
A solution that needs everyone
Smishing and mobile malware present a risk to individuals, mobile networks, and businesses, and so all of these groups have a part to play in mitigating the danger and maintaining a high level of trust in the mobile channel. Here’s what we propose:
Consumers:
- Watch for unknown senders and treat unexpected mobile messages like you would an unexpected email notification.
- When you do receive a mobile message that contains a link, including package delivery notifications, don’t use the web link provided in the text message. Instead, use your device’s browser to access the sender’s website directly, or use the brand’s app if you already have it installed.
- Report smishing, abuse, and other spam using the reporting feature in your messaging client if it has one, or by forwarding spam text messages to 7726, which spells “SPAM” on the phone keypad.
- Install a reputable anti-virus (AV) application on your phone and scan regularly for malware.
- Be careful about downloading and installing new software to your mobile device. Don’t install software from any source other than a certified app store. Read install prompts closely, particularly for information regarding rights and privileges that the app may request.
Businesses:
- Implement security requirements for employees to access corporate accounts on personal devices.
- Train staff to recognize smishing messages alongside traditional email phishing.
- Issue alerts if your brand is being used in smishing or phishing lures.
- Employ URL takedown services to have fraudulent or lookalike domains removed quickly.
Mobile Network operators:
- Enable one-click reporting of suspicious messages.
- Invest in best-in-class network protection.
- Continue collaboration across the mobile ecosystem. Work with consumer brands and government entities to share attack information, enable threat tracking and increase the likelihood of identifying attackers and criminals.
Learn More
To learn more, check out the Proofpoint Threat Hub, your home for the latest research and insights.

