Business email compromise (BEC) was clearly an effective strategy for fraudsters in 2022. Last year, businesses lost more than $2.7 billion due to these scams, according to the latest Internet Crime Report from the FBI’s Internet Crime Complaint Center (IC3). That’s $300 million more than in 2021.
These losses were also nearly 80 times greater than those due to ransomware. In fact, the FBI’s IC3 reports that BEC scams represented a whopping 27% of all cyber crime-related financial losses last year. Plus, the average cost of each incident increased—up from $120,000 in 2021 to $124,000.
There were fewer complaints to the FBI’s IC3 in 2022 (800,944 vs. 847,376). But total losses rose from $6.9 billion to more than $10.2 billion. This represents a year-over-year increase of 48%.
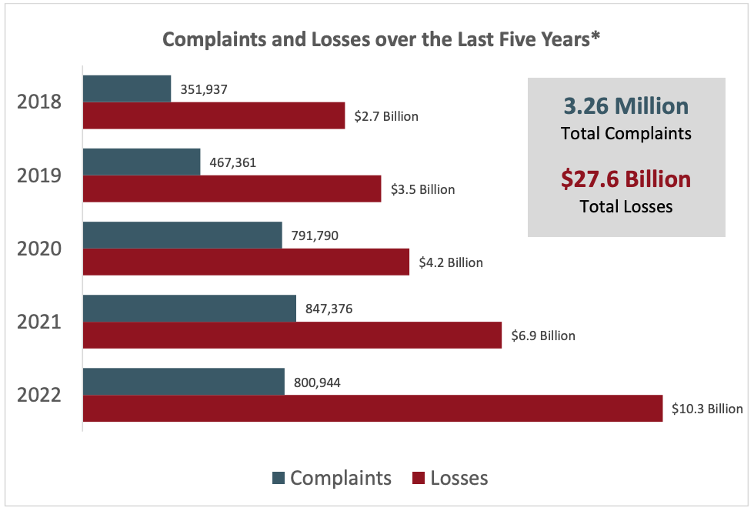
Figure 1. Complaints and losses to cyber crime reported over the last five years. Source: FBI’s IC3 2022 Internet Crime Report.
BEC More Prevalent Than Ever—and Losses Keep Climbing
BEC was one of the top threats highlighted in the report. In 2022, the FBI’s IC3 received 21,832 complaints about BEC scams. Year-over-year growth of BEC complaints tripled, from a 3% increase in 2021 to a 9% increase in 2022. This trend suggests BEC attacks are more prevalent than ever.
The number of victims falling for BEC schemes also increased year over year—by nearly 10%. Research for Proofpoint’s 2023 State of the Phish report underscores this trend. We surveyed 7,500 end users and 1,050 IT security professionals across 15 countries. Seventy-five percent of the respondents said their organization had experienced at least one BEC attack in 2022.
The State of the Phish report also notes that non-English-speaking countries are seeing more BEC attacks in their own languages. However, English remains the primary language used in BEC attacks.
Compared with phishing, BEC has fewer victims. But BEC financial losses can be significantly higher. That’s because BEC scams are highly targeted so they often cause bigger financial losses even if the volume is low.
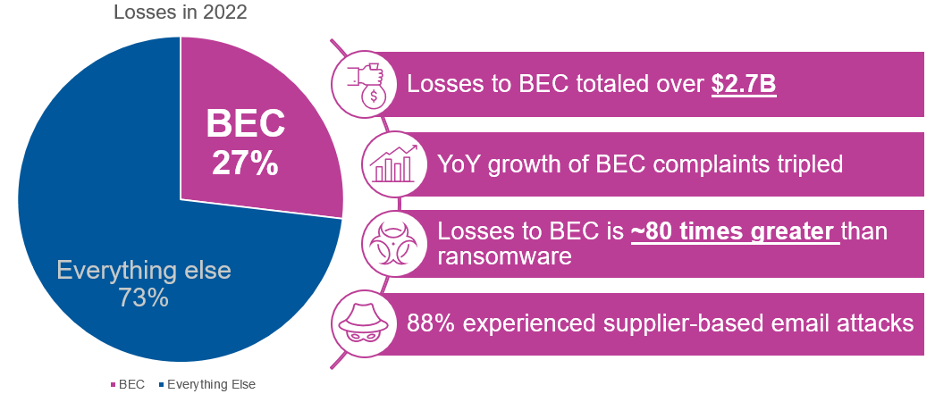
Figure 2. BEC scams accounted for 27% of all cyber crime-related financial losses reported by businesses last year. Source: FBI’s IC3 2022 Internet Crime Report.
Fraudsters using more sophisticated tactics
Commonly used BEC schemes include compromised vendor emails, requests for large amounts on gift cards, payroll redirects, requests for W-2 information and real estate fraud. More recently, the FBI is seeing sophisticated scams where fraudsters:
- Convince victims to send funds directly to cryptocurrency platforms where funds can be quickly transferred without being tracked by banking institutions
- Target victims’ investment accounts instead of bank accounts
- Spoof legitimate business phone numbers to confirm fraudulent banking details with victims
- Use call centers to defraud victims by impersonating tech and customer support agents and government personnel
Proofpoint blocks more than 3 million BEC messages monthly. The largest losses from BEC incidents—based on what we’ve observed—come from supplier invoicing fraud.
We recently analyzed nearly 2,000 organizations. And we found that about 88% experienced a supplier-based email attack over a seven-day period in February 2023. This finding is further evidence that suppliers are now another threat vector. Unfortunately, most organizations don’t have the tools to see which suppliers or business partners might be impersonated or compromised.
Phishing continues to dominate the threat list
Only one person needs to fall for a phish for cyber criminals to get the information they need to breach an organization, compromise accounts, collect money or all of the above. Not surprisingly, phishing remains a go-to attack strategy for many bad actors:
- In 2022, 38% of complaints to the FBI’s IC3 were related to phishing
- 84% of organizations surveyed for Proofpoint’s 2023 State of the Phish report said they’ve experienced at least one successful phishing attack
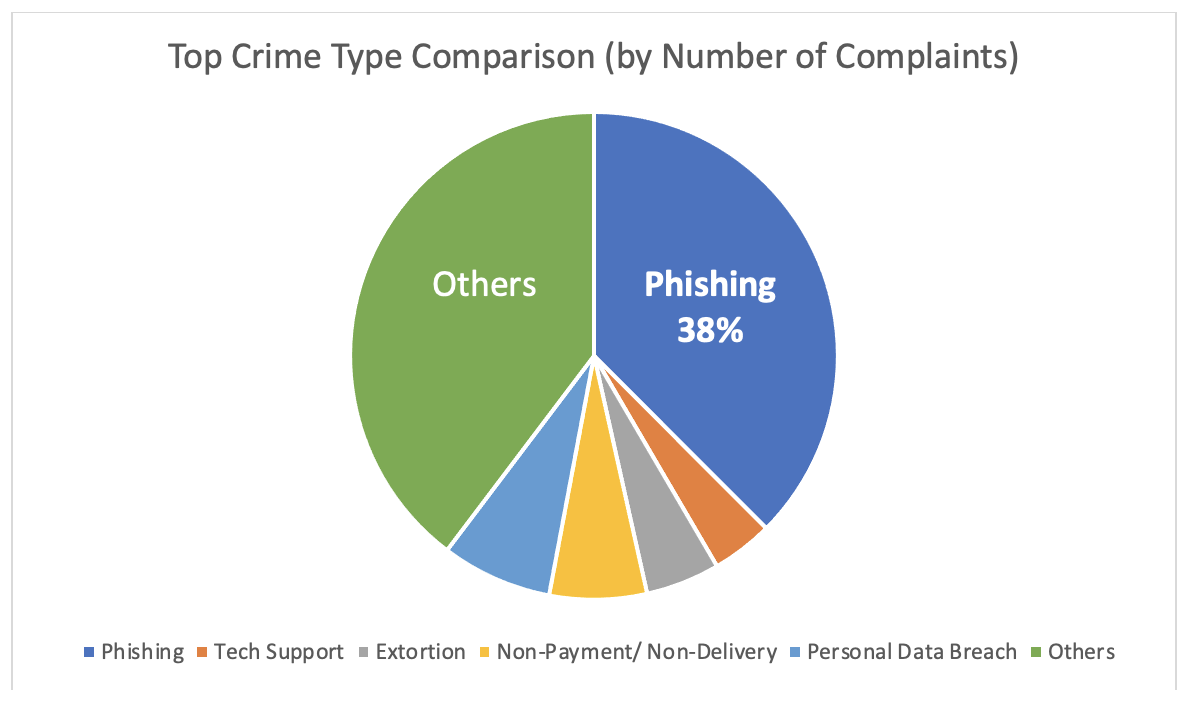
Figure 3. Comparison of the top crime types, based on the number of complaints to the FBI’s IC3 Report. Source: FBI IC3’s 2022 Internet Crime Report.
Attackers are targeting people. But most people don’t have the knowledge and tools they need to defend against phishing attacks, which rely heavily on social engineering.
Organization need to understand the people risk and invest in securing the number one threat vector, which is email. And they should provide security education to all their employees. They should also use threat intelligence to uplevel their security awareness programs. Empowering users with a phishing button to report malicious email also helps to protect them and the organization.
Many ransomware victims likely unwilling to come forward
The number of ransomware incidents dropped 36% in 2022, with 2,385 complaints reported, according to the FBI IC3 Report. Adjusted losses from these incidents totaled $34.3 million—a drop from $49 million in 2021.
These figures may signal good news. But they’re more likely due to ransomware victims’ reluctance to report incidents to law enforcement. The report notes that this reluctance makes it a challenge to know the true number of ransomware victims.
Consider these findings as well: Nearly two-thirds (64%) of organizations surveyed for our 2023 State of the Phish report said they were infected by ransomware in 2022. Alarmingly, more than two-thirds of this group reported multiple incidents of infection. So, we’re almost certain that the true number incidents and associated losses last year are much higher than what’s being reported.
Cyber criminals use various techniques to infect victims with ransomware. According to the report, the top infection vectors for ransomware last year were phishing emails and exploiting Remote Desktop Protocol (RDP) and software vulnerabilities.
Many ransomware attacks start with email. To address ransomware attacks more effectively, organizations should “shift left” and invest in email security that stops threats at an early stage in the attack chain. It’s also important to protect the entire attack chain from pre-compromise to post-compromise.
Protect against email threats with a multi-layered platform approach
What’s clear is that attackers continue to target people and exploit human vulnerability with social engineering. And they’re constantly innovating. They’re always on the lookout for new tools and schemes while using multiple threat vectors to target their victims.
Email is still the number one threat vector. The best defense is a multi-layered platform that features a variety of security controls. These controls go beyond a robust email gateway to include email authentication, security education, mSOAR and shared threat intelligence.
Our threat protection platform can reduce your people risk. Proofpoint Aegis gives you visibility into risky users and suppliers, and the threats targeting your organization.
Learn more about how to combat email threats.

