Reports of messaging abuse and smishing continue to increase at a rapid pace. Since the beginning of May, reports of U.S.-based abusive messages have grown by 39%, and Proofpoint threat engineers are observing a significant increase in one specific subtype. Reported MMS (multimedia messaging service) abuse has increased by 220% over the same period. These messages use images and/or graphics to trick subscribers into providing confidential information or entice them into falling for other scams.
MMS-based abuse represents a burgeoning attack vector. In the past 18 months, subscriber reports of unwanted MMS messages have grown from far less than 1% of all reports in January 2023 to more than 21% in October of this year. Since January of this year, reports of unwanted MMS messages have grown by a staggering 429%.
What is MMS, and how is it abused?
MMS is built on the same technology as SMS (short messaging service) and allows mobile subscribers to send and receive pictures, audio and video content. Today in the United States, subscribers often use MMS without even realizing it. We often combine SMS and MMS and simply call it “mobile messaging.”
We have written in the past regarding how quickly users read and respond to mobile messages. Typically, mobile messages are read and replied to within three minutes, which is why mobile marketing works so well. Threat actors are now starting to embed images to add a level of perceived authenticity to their scams as they impersonate businesses, public or governmental representatives, or otherwise entice subscribers to fall for scams.
Examples of MMS scams
Imaging impersonation and abuse comes in a variety of types. The following are just a few examples of some recently observed scams.
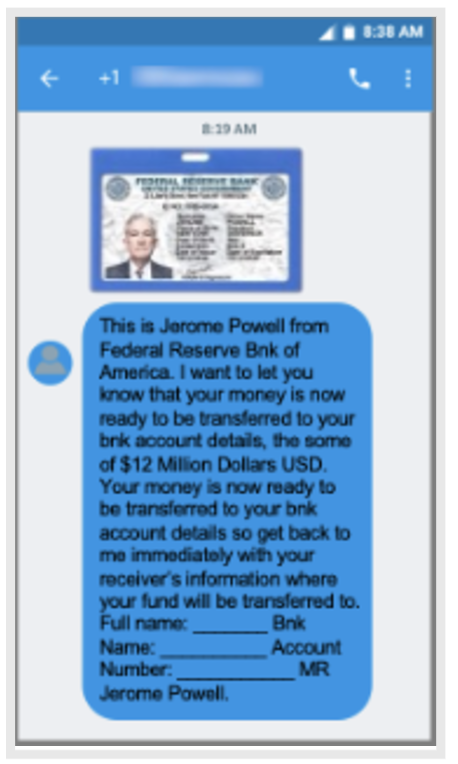
MMS message impersonating Jerome Powell of the Federal Reserve Bank.
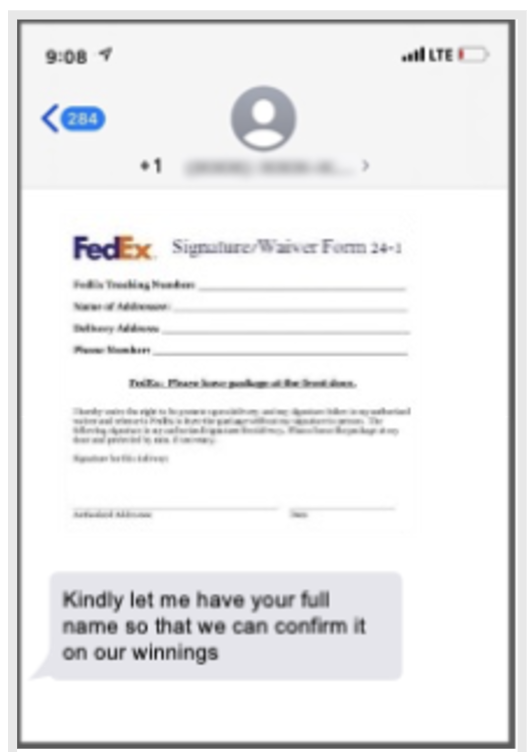
MMS message impersonating FedEx and an official-looking waiver document.
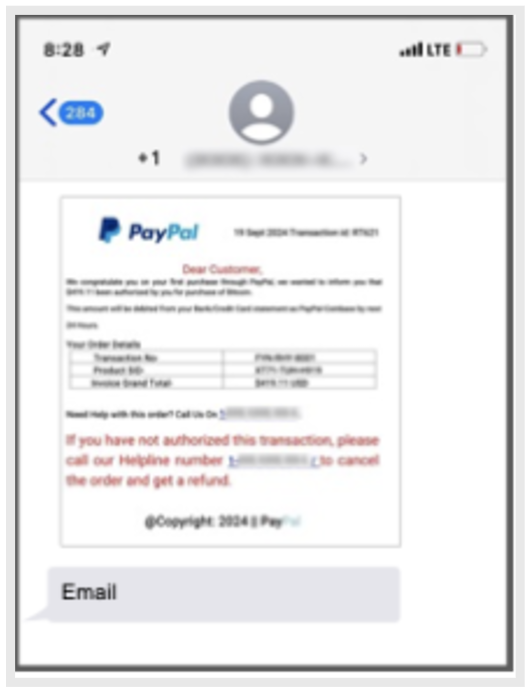
MMS message impersonating PayPal and an official-looking purchase verification.
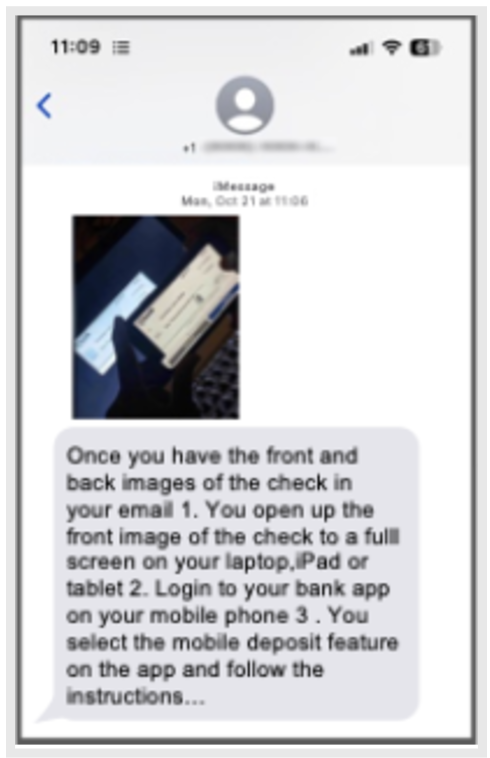
MMS message with pictures of a check with scam instructions.
Smart devices are ubiquitous in the U.S., with more than 90% of Americans using an intelligent device capable of both sending and receiving images. Proofpoint threat analysts have witnessed similar image impersonation and scams in over-the-top (OTT) messaging platforms as well, such as WhatsApp and Line. Proofpoint is continuously enhancing threat detection and protection solutions to protect against evolving threats including those emerging in MMS.
Tips for avoiding MMS scams
We often remind users to be suspicious of mobile messages and to follow the “do’s and don’ts” below. It’s also very important to remain suspicious of messages that have authentic looking images. Just because the message includes an image or picture, that doesn’t mean it’s legitimate or that it was sent by a legitimate source.
Do’s
- Be on the lookout for suspicious mobile messages. Criminals increasingly employ mobile messaging and smishing as an attack vector.
- Carefully consider before you provide your mobile phone number to an unknown entity.
- Whenever you receive a mobile message that contains a URL (web link), including a political message, do not click on the URL. Instead, use your device’s browser to access the known sender’s website directly. Or use the brand’s app, if it’s installed on your device.
- Report unwanted messaging (spam) and smishing to your mobile network operator (service provider) and the Mobile Abuse Visibility Solution run by Proofpoint. To do this, make use of the built-in iOS and Android reporting features by clicking “Report Junk” on iOS or “Report Spam” on Android devices. If this simplified reporting capability is not available, you can forward the unwanted/spam text messages to 7726 which spells “SPAM” on the phone keypad. These reports help the mobile network operator and Proofpoint protect other subscribers from abusive content.
- Be careful when downloading and installing software to your mobile device. Make sure to read install prompts closely. And pay close attention to information about the rights and privileges that the app may request.
Don’ts
- Don’t respond to any unsolicited political, enterprise or commercial messages from any vendor or organization that you don’t recognize. Doing so often confirms that you’re a real person.
- Don’t install software on your mobile device from any source other than a certified app store from the vendor or mobile network operator.
Learn more
Explore the latest threat insights from Proofpoint.
To learn more about Proofpoint mobile messaging solutions, visit the Cloudmark website.

