It is truly difficult to communicate cyber risk in business terms. Chief information security officers and security and risk management leaders have come a long way in their efforts to create relevant narratives around cyber risk to earn a seat in boardrooms. However, the ability to articulate and quantify cyber risk is a dark art that most security professionals aspire to practice daily—and may spend their lifetimes working to get right.
That is why the growing field of cyber risk quantification (CRQ) has caught the attention of many security and risk management leaders. Gartner® defines CRQ as “A method for expressing risk exposure from interconnected digital environments to the organization in business terms. Risk exposure can be expressed in currency, market share, customer and beneficiary engagement and disruption in products or services over a chosen period.”
Currency is the defining metric of business. But it can be difficult to map a hard-dollar value to black swan cyber events (low probability, high impact) or even soft opportunity costs.
Gartner defines the top five use cases for CRQ by the percentage of security and risk management leaders (SRM) as:
- 78% prioritize cyber-risk mitigation
- 61% communicate to risk owners
- 61% communicate to C-level executives
- 53% communicate to the board
- 53% align cyber risks to other risk practices
To create compelling narratives that break through the noise, it’s helpful to center your storytelling around people. Here, we’ll discuss the ways that people create cyber risk—and show you how to quantify cyber risk, so that you can tell better stories.
Cyber risk in human-centric terms
When you frame cyber risk in the context of people, it can help make the concept real and relevant to business stakeholders. Telling stories about incidents that affect people in the business is often a starting point. This form of scenario analysis is one of the most compelling ways to demonstrate tangible impact.
However, in the language of the FAIR (Factor Analysis of Information Risk) methodology, this approach tells only a fraction of the story. That is because the loss magnitude and loss frequency are limited to the scope of the incident or person.
To tell a more universal human-centric cyber story, the risk model needs to recognize that human risks and vulnerabilities encompass a spectrum of behaviors, events and actions that can expose people, companies or institutions to cyberthreats. Crucial facets to consider in the broader view of human risk include the following.
1. Security awareness and education
Many users lack adequate knowledge about cybersecurity best practices. Ignorance about phishing scams, the significance of secure passwords or the dangers of downloading suspicious attachments can inadvertently open the door to cyberthreats.
2. User negligence and oversight
Even with sufficient knowledge, human error remains a significant risk factor. Careless actions like leaving devices unlocked or unattended, using unsecured public Wi-Fi, or failing to update software regularly can create vulnerabilities that cybercriminals exploit.
3. Social engineering
Most modern cyberattacks exploit human psychology through social engineering tactics. Techniques like phishing—where attackers masquerade as trustworthy entities to obtain sensitive information—rely on human trust to succeed.
4. Insider threats
Employees or other users with access to sensitive data can pose an insider threat. Whether through malicious intent or inadvertent actions, insiders can compromise data security. That makes them a significant concern for businesses.
5. Threat landscape or threat intelligence
Human behaviors are not malicious or risky unless there is context and consideration for the ever-evolving panorama of potential risks, vulnerabilities, and dangers that may threaten a company’s information security.
6. Security posture and controls
Many businesses have made sizable investments in cybersecurity readiness and capabilities to defend against potential threats and mitigate risk. These efforts encapsulate the measures, strategies, policies and practices that are intended to protect information systems, networks and data.
When it comes to the human factor, security and risk managers often default to discussion of security awareness training as the primary—or sometimes only—mitigating control. But risk needs to be seen through the lens of the people who create it and when they create it.
The challenge is how to quantify cyber risk and understand when people create cyber risk. The telemetry lies across the security ecosystem. It does not easily reside in any single product— even those that are designed with integrations.
Any business leader would describe their “analytical nirvana” as having reports with accurate and relevant data that is readily available to them in near-real time for decision-making. This is also the hope in cybersecurity for risk, but it is not easily done.
Proofpoint can help you quantify cyber risk and human risk
To state the obvious, when it comes to quantifying cyber risk, it is highly unlikely that any single vendor can provide the ultimate answer or singular “correct” approach.
At Proofpoint, our goal is to help our customers understand their cyber risk. We believe that the best place to start is to understand people and the human factor.
Proofpoint Nexus People Risk Explorer has the benefits of CRQ in mind. We have accounted for several factors as we consider our customers’ needs and technology strategy.
1. Human-centric approach that uses integrated systems and data
Proofpoint presents a human-centric view of cyber risk. We report on incidents, threats, behaviors and other telemetry across a company’s security infrastructure. And we assess risk by looking at the following elements.
- Vulnerability—the likelihood that users will become victims based on how they behave or interact with threats
- Attacks—the probability that users will be targeted by cyberattackers or will receive severe threats
- Privilege—the impact of the damage to the business that a successful attack would cause (if the user is an administrator of critical infrastructure or systems)
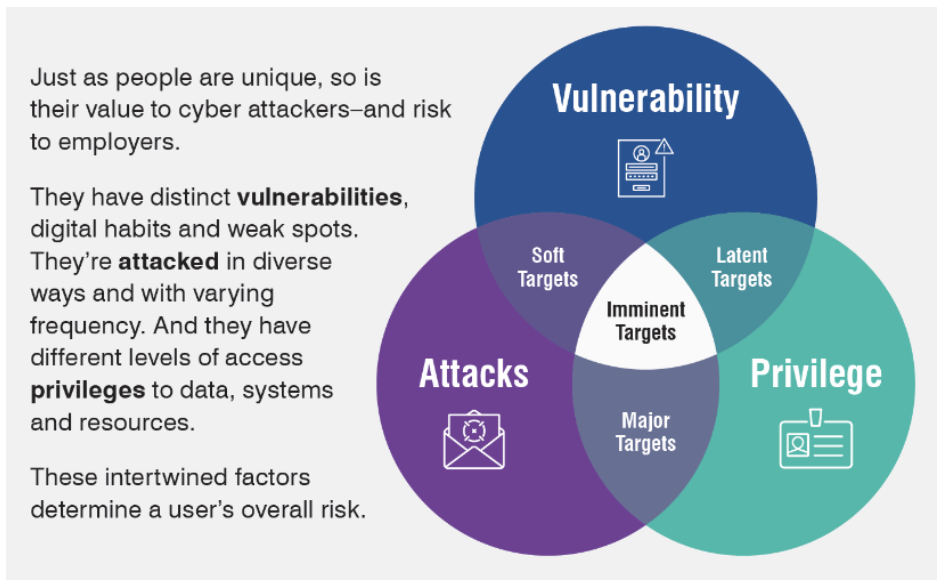
A Venn diagram that illustrates how Proofpoint assesses risk.
2. Relative industry and organizational benchmarks
Nexus People Risk Explorer provides a range of risk scores. It uses statistical modeling techniques to generate risk exposure probabilities. And its machine learning techniques use big data to determine on-demand or daily calculations of risk.
The dataset that Proofpoint uses is one of the most comprehensive in the security industry. It includes:
- 2.8 trillion emails
- 1.7 trillion URLs
- 1.3 trillion SMS/MMS scanned per year
- 46 million end users protected and monitored for data loss prevention activity
You can compare risk scores by user, department, industry or even custom groups.
3. Adjust or customize the risk model according to organizational risk tolerance and security culture
Security controls may exist, but that does not mean there is proper risk mitigation or use of those controls. Knowing when to apply the right control in the right circumstance is the fundamental tension of every cyber program.
Proofpoint provides custom controls that include adjustable risk thresholds to help highlight and prioritize the areas that matter most to the business. Likewise, we integrate security awareness and click-rate metrics that reflect the company’s security culture.
As technology advances, the interplay between humans and digital systems will continue to evolve. Advancements in artificial intelligence and behavioral analytics will evolve in response to trending cyberthreats and aid in fortifying defenses. But the human factor will remain a constant factor for consideration—including and beyond security awareness.
No system can be entirely foolproof. That is why management of the human element in cyber risk is crucial to create a more resilient workforce that can break the attack chain.
Find out more about Proofpoint Nexus People Risk Explorer and watch our video demo.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.

