Microsoft - The Threat Actor’s Playground. A Blog Series.
This post is an ongoing series of blogs on different types of people-centric email attacks Microsoft misses. These attacks cost organizations millions of dollars every year in losses and cause frustration for information security teams and users alike, due to outdated detection technologies and inherent limitations of Microsoft email security. In this series, you can expect to learn more about Microsoft missing several different types of attacks, which we’ll go in-depth about and provide recent examples of:
- Business Email Compromise or Email Fraud
- Ransomware
- Supply Chain Risk
- Account Compromise
- Weaponized File Sharing
Subscribe to our blog at the bottom of this post to stay updated on these misses that may be impacting your organization and better understand your organization’s risk with a threat assessment.
Business Email Compromise Attacks Missed by Microsoft
Business Email Compromise (BEC), a type of email fraud, is one of the most financially damaging threats to businesses of all sizes and across industries, overshadowing most other types of cybercrime in terms of monetary loss.
In 2020 alone, BEC schemes cost companies and individuals nearly $2 billion and comprised 44% of total monetary loss, according to the FBI and Internet Crime Complaint Center’s (IC3) annual cybercrime report. This represents a $100 million increase from 2019. Other research, like The Ponemon 2021 Cost of Phishing Study, shows an average of almost $6 million in direct and indirect losses annually for a large-sized organization, or 40% of the total cost of phishing.

Figure 1: Proofpoint blocks more than 15,000 BEC messages every day
Proofpoint detects, on average, about 450,000 BEC attacks monthly. In the past month, Proofpoint detected about 2,100 BEC threats that have slipped past Microsoft perimeter defenses, just in a limited data set of Threat Assessments.
At one large manufacturer with more than 18,000 employees, almost 300 impostor attacks were delivered. A 1,000 seat higher education university, Microsoft missed nearly 150 impostor messages sent to staff. And at a smaller organization with about 600 employees, Microsoft missed more than 80 impostor messages. In each instance, the POCs ran for about one month.
Below, you’ll see a sample of BEC attack types missed by Microsoft inbound and outbound during recent Proofpoint Threat Assessments.
Payroll Redirect Attack Overview:
Payroll redirects, also called payroll diversions, are email fraud attacks that typically target finance, tax, payroll and human resources employees. Payroll redirects employ various social engineering tactics that can be hard to detect. Proofpoint detects, on average, about 60,000 payroll redirect attempts monthly.
Payroll redirects are considered a medium risk to businesses and organizations. According to the FBI Internet Crime Complaint Center’s report on BEC from 2019, the average loss of payroll fraud is $7,904 per incident.
Here’s one example of an attack missed by Microsoft:
- Environment: Microsoft 365
- Threat Category: Business Email Compromise
- Attack Type: Payroll Redirect
- Target: Benefits Administrator
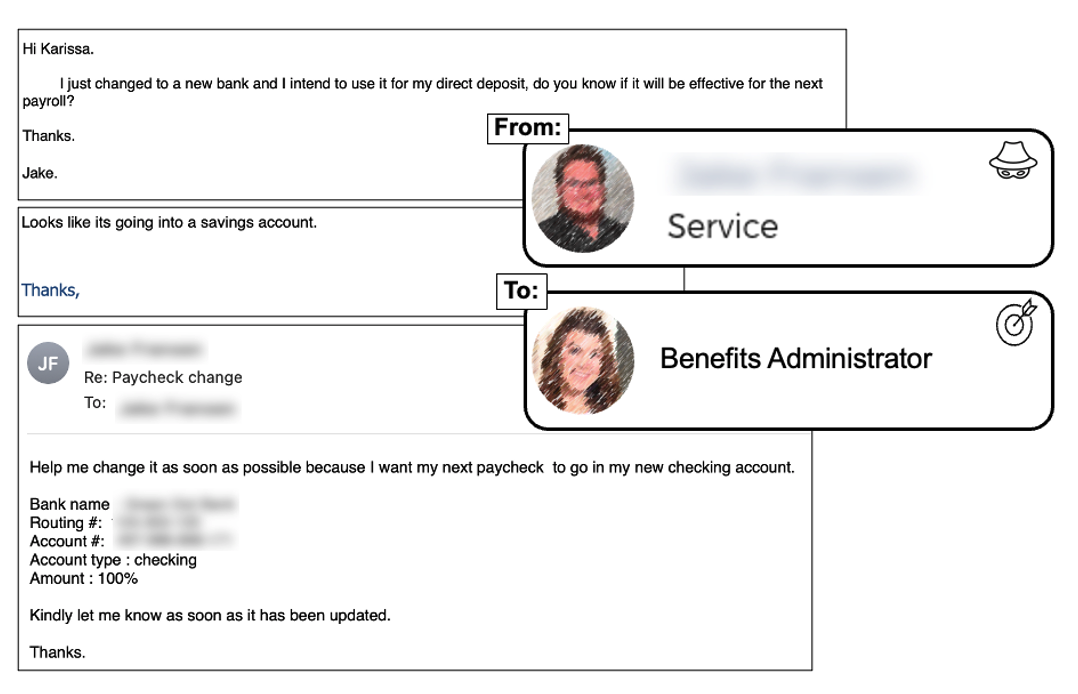
Figure 2. An example of a payroll redirect attack
The Anatomy of the Payroll Redirect Attack:
This payroll redirect attack bypassed native Microsoft email security controls and even allowed communications back and forth from the impostor and victim. The impostor used a Gmail account and purported to be an employee requesting a direct deposit change to a new bank account. Impersonation of employees is problematic, but when high-level executives are impersonated, the financial losses can be more severe.
Executive Impersonation Attack Overview:
Impersonation attacks, especially of executives, also known as CEO fraud, have risen drastically with changing work environments. Since March 2020, Proofpoint has seen email scammers impersonate more than 7,000 CEOs. Over half of Proofpoint customers have had at least one high-level executive impersonated and their email persona used in a scam attempt.
Here’s one example of an attack missed by Microsoft:
- Environment: Microsoft 365
- Threat Category: Business Email Compromise
- Attack Type: Impersonation
- Target: Directors, Strategic and Business Development
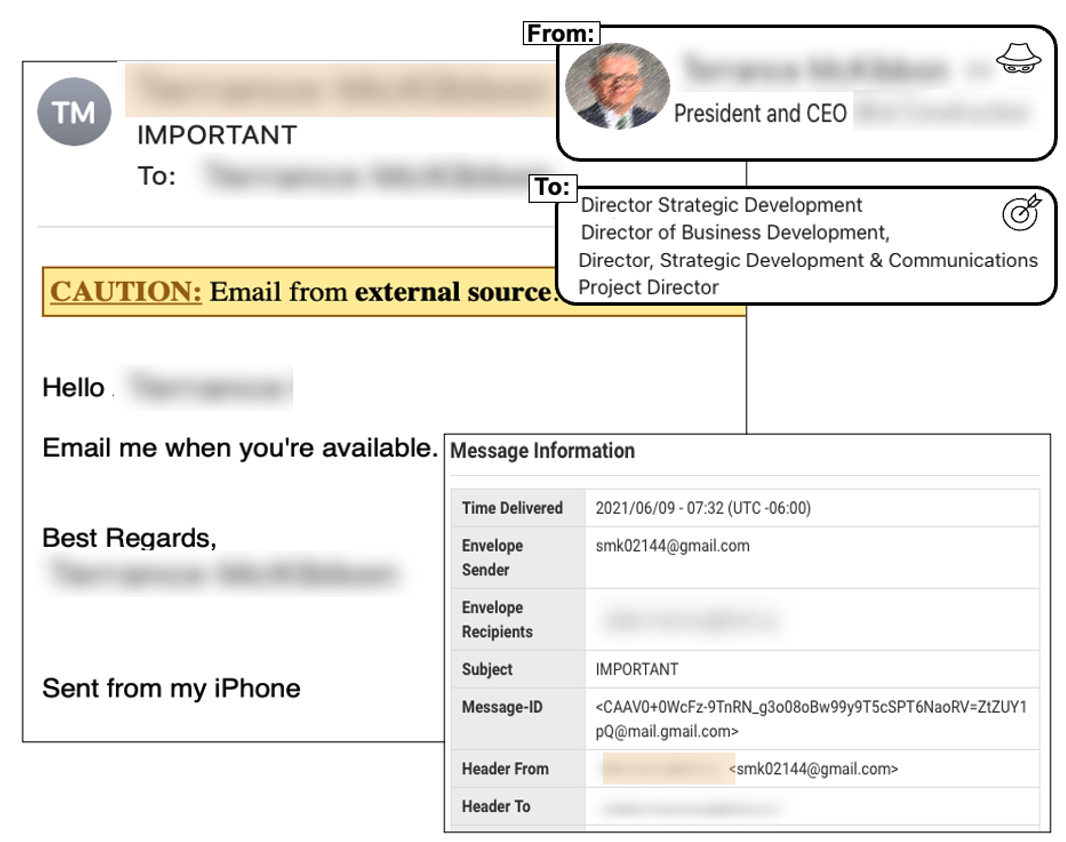
Figure 3. An example of an executive impersonation attack
The Anatomy of the Executive Impersonation Attack:
This impersonation attack bypassed native Microsoft email security controls. The impostor used a Gmail account and purported to be the CEO requesting follow-up action by the employees. If employees had engaged with this email, the attacker could have easily continued to manipulate and extract data or financial rewards.
Why Microsoft is Missing BEC Attacks
These attacks are using sophisticated deception tactics, and Microsoft missed all of them for several reasons:
- These emails pass simple sender reputation checks; due to the use of Gmail, they passed both SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) authentication checks. The use of legitimate services is a common tactic many reputation-based vendors struggle to detect.
- These messages spoof an employee’s display name. Microsoft only detects these once they’ve been identified manually. Moreover, bad actors commonly use nicknames or variants of the employee’s name to bypass Microsoft’s message header analysis.
- Microsoft doesn’t offer metonym (word substitution) detection to decipher the tone and intent of the message phrasing. These threats clearly use phrasing indicative of email fraud.
- Since the email doesn’t contain malicious payload, Microsoft’s built-in sandboxing will provide no detection of these types of threats.
Missing these attacks means organizations need to spend significant time and resources in remediating attacks, often manually. In one case study, an organization was able to save three full-time equivalent hires, or about $345,000 over three years, with the improved email security detection capabilities of Proofpoint.
How Proofpoint Stops Business Email Compromise
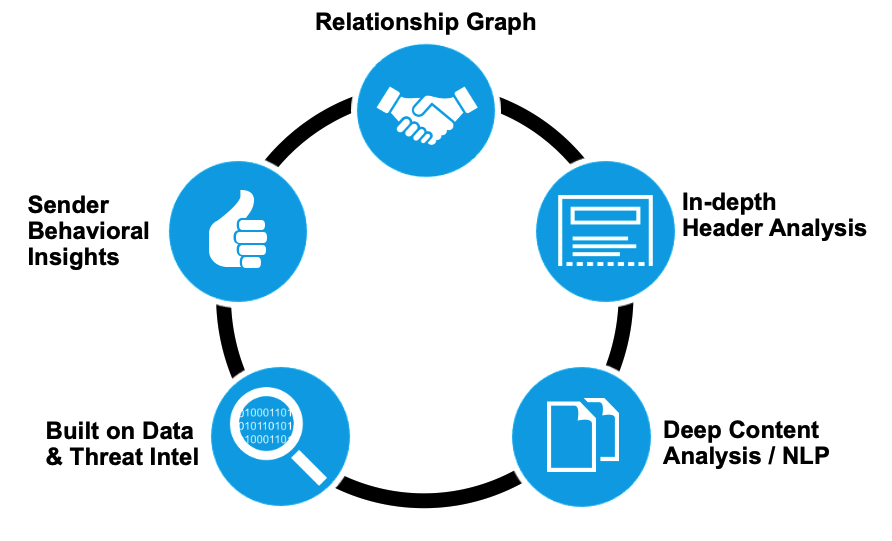
Figure 4. A relationship graph illustrating how Proofpoint helps to stop BEC
Proofpoint is the only vendor that provides an end-to-end, integrated solution to combat BEC. Our machine learning engine, Supernova, uses inbound and outbound gateway telemetry, supply chain risk analytics, and API data from cloud productivity platforms like Office 365 and Google Workspace to provide Advanced BEC Defense.
Supernova also uses a combination of machine learning, stateful analytics, behavioral analytics, rulesets and the work of researchers tracking threat actor tactics to deliver both high efficacy and the lowest false-positive rate of any of our detection platforms. The machine-learning components of Supernova are trained by our unmatched dataset that comes from email threat protection used by the majority of the Fortune 100, Fortune 1000 and Global 2000.
In the above examples, it’s important to note that Proofpoint detected these messages and would have prevented them from ever reaching a user’s inbox.
Recommendations to Stop Business Email Compromise Attacks
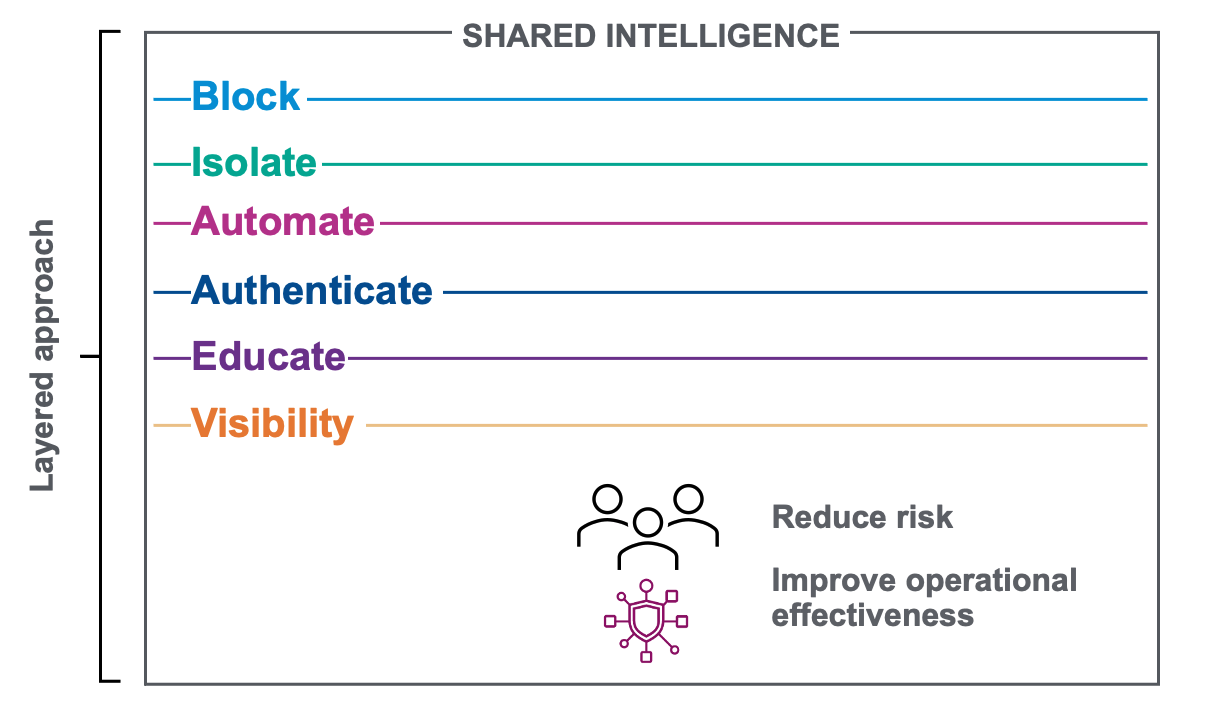
Figure 5. An overview of the layered approach Proofpoint applies to help stop BEC attacks
Proofpoint takes a layered approach to stopping BEC attacks with our Threat Protection Platform. Some of these layers include our leading detection, isolation, authentication, education and automated remediation capabilities. There’s no silver bullet to the ever-increasing phishing threat, which is why a layered, integrated threat protection solution is necessary. Proofpoint also uses machine learning and advanced sandboxing technology to stop ransomware, phishing and account takeover, in addition to BEC attacks.
To learn more about how we can stop these threats and more in your environment with the Proofpoint Threat Protection Platform, see this page. Also, consider scheduling a free Email Threat Discover Assessment.

