This blog post is part of a monthly series, Cybersecurity Stop of the Month, which explores the ever-evolving tactics of today’s cybercriminals. It focuses on the critical first three steps in the attack chain in the context of email threats. The goal of this series is to help you understand how to fortify your defenses to protect people and defend data against emerging threats in today’s dynamic threat landscape.
The critical first three steps of the attack chain: reconnaissance, initial compromise and persistence.
So far in this series, we have examined these types of attacks:
- Uncovering BEC and supply chain attacks (June 2023)
- Defending against EvilProxy phishing and cloud account takeover (July 2023)
- Detecting and analyzing a SocGholish Attack (August 2023)
- Preventing eSignature phishing (September 2023)
- QR code scams and phishing (October 2023)
- Telephone-oriented attack delivery sequence (November 2023)
- Using behavioral AI to squash payroll diversion (December 2023)
- Multifactor authentication manipulation (January 2024)
- Preventing supply chain compromise (February 2024)
- Detecting multilayered malicious QR code attacks (March 2024)
- Defeating malicious application creation attacks (April 2024)
- Stopping supply chain impersonation attacks (May 2024)
In this post, we continue to explore the topic of impersonation tactics, examining how threat actors use them to get information for financial gain.
Background
Last year, the Federal Trade Commission (FTC) received more than 330,000 reports of business impersonation scams and nearly 160,000 reports of government impersonation scams. This represents about half of all the fraud reported directly to the FTC. The financial losses due to email impersonation scams are staggering. They topped $1.1 billion in 2023, which was more than three times the amount reported in 2020.
Financial fraud is a serious issue—and it’s on the rise. In 2023, consumers reported losing more than $10 billion to fraud. This is the first time that losses reached that benchmark, and it’s a 14% increase from 2022. The most common reports were imposter scams. This category saw significant increases in reports from the business and government sectors.
The scenario
Proofpoint recently detected a threat actor’s message to the financial controller of a Dutch financial institution, which is known for its expertise in commercial risk. In this attack, the threat actor pretended to be the company’s CEO—a tactic that’s known as CEO fraud. In these attacks, the goal is to exploit the recipient’s trust to get them to perform a specific action.
The threat: How did the attack happen?
The attacker emailed the Dutch financial company’s controller, asking that two payments be sent to London. The email demanded that payments be made “today” to create a sense of urgency. To help make the message seem credible, the attacker claimed to have access to the IBAN and SWIFT codes.
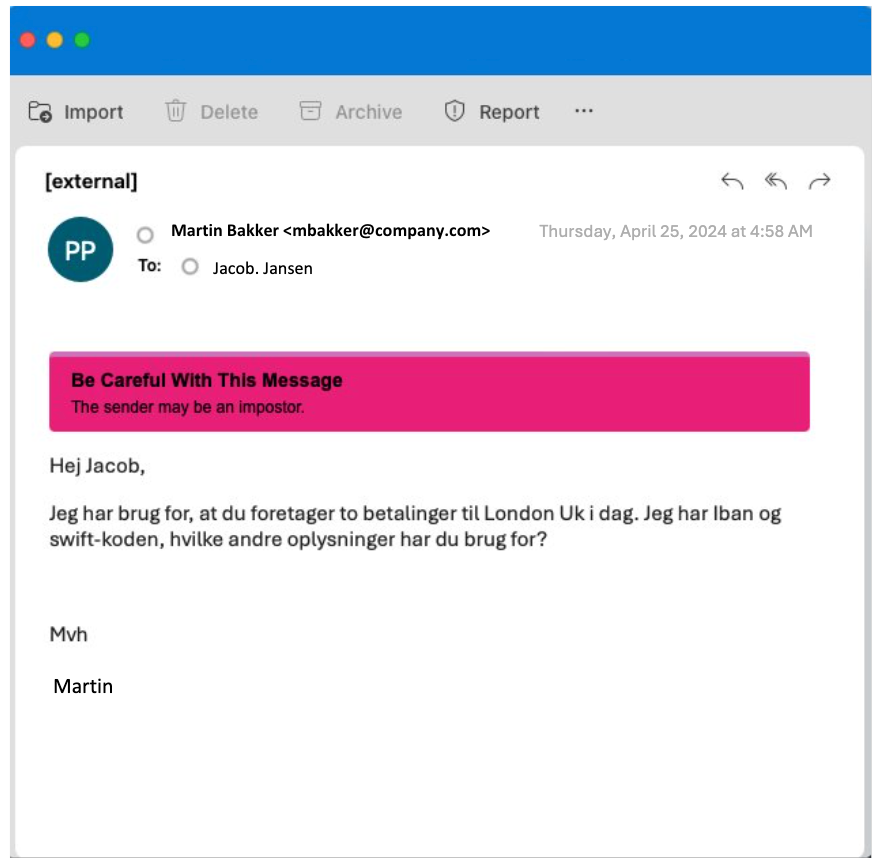
Original email from the threat actor.
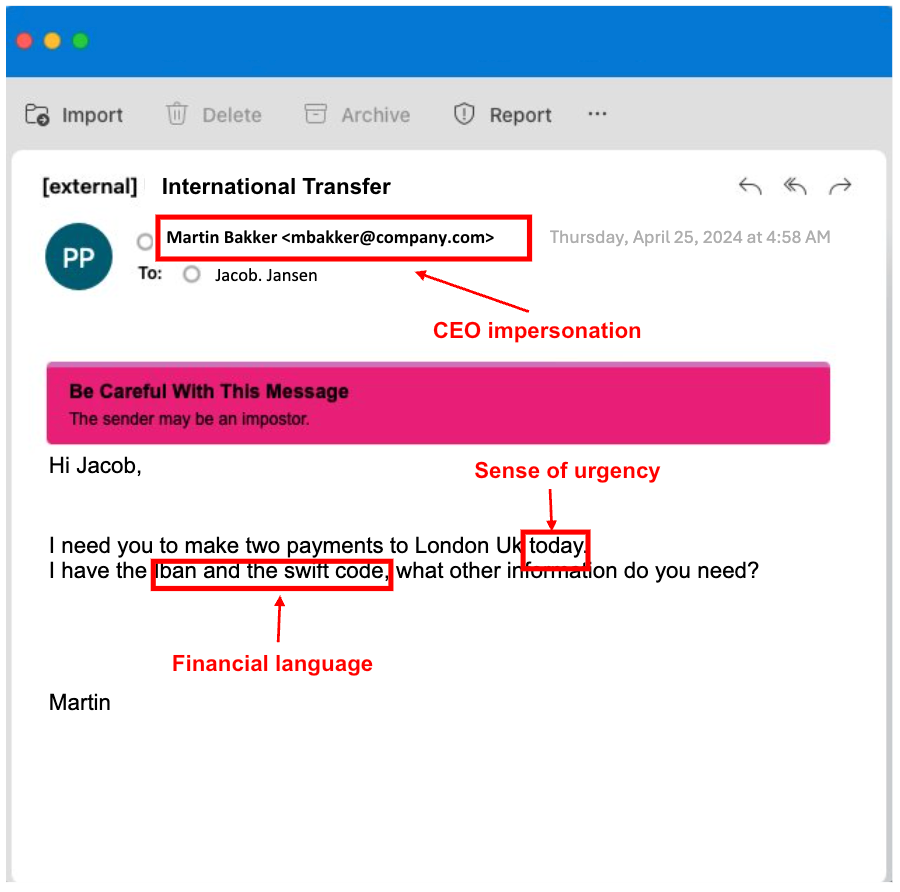
The same email translated into English.
Detection: How did Proofpoint prevent this attack?
Proofpoint has the industry’s first predelivery threat detection engine that uses semantic analysis to understand message intent. Powered by a large language (LLM) model engine, it stops advanced email threats before they’re delivered to users’ inboxes. That’s what stopped this malicious message from reaching the financial controller’s inbox.
Pre-delivery protection is so critical because, based on Proofpoint’s telemetry across more than 230,000 organizations around the world, post-delivery detections are frequently too late. Nearly one in seven malicious URL clicks occur within one minute of the email’s arrival, and more than one-third of BEC replies happen in less than five minutes. These narrow timeframes, during which a user can fall prey to an attack, underscore the importance of blocking malicious attacks before they can reach a user’s inbox.
Here’s more about our LLM engine:
- Intent comprehension. Our LLM engine can understand the intent of incoming messages, which is key to stopping impersonation threats. In this case, the LLM engine identified the sense of urgency and financial language in the attacker’s email.
- Contextual understanding. Semantic analysis can understand the contextual usage of words, phrases and combinations, like urgency and suspicious language. As a result, it can interpret information and grasp the complete meaning of a given message.
- Language agnostic. It doesn’t matter what words are used or what language an impersonation email is written in. Our semantic analysis is language agnostic and supports over 100 languages.
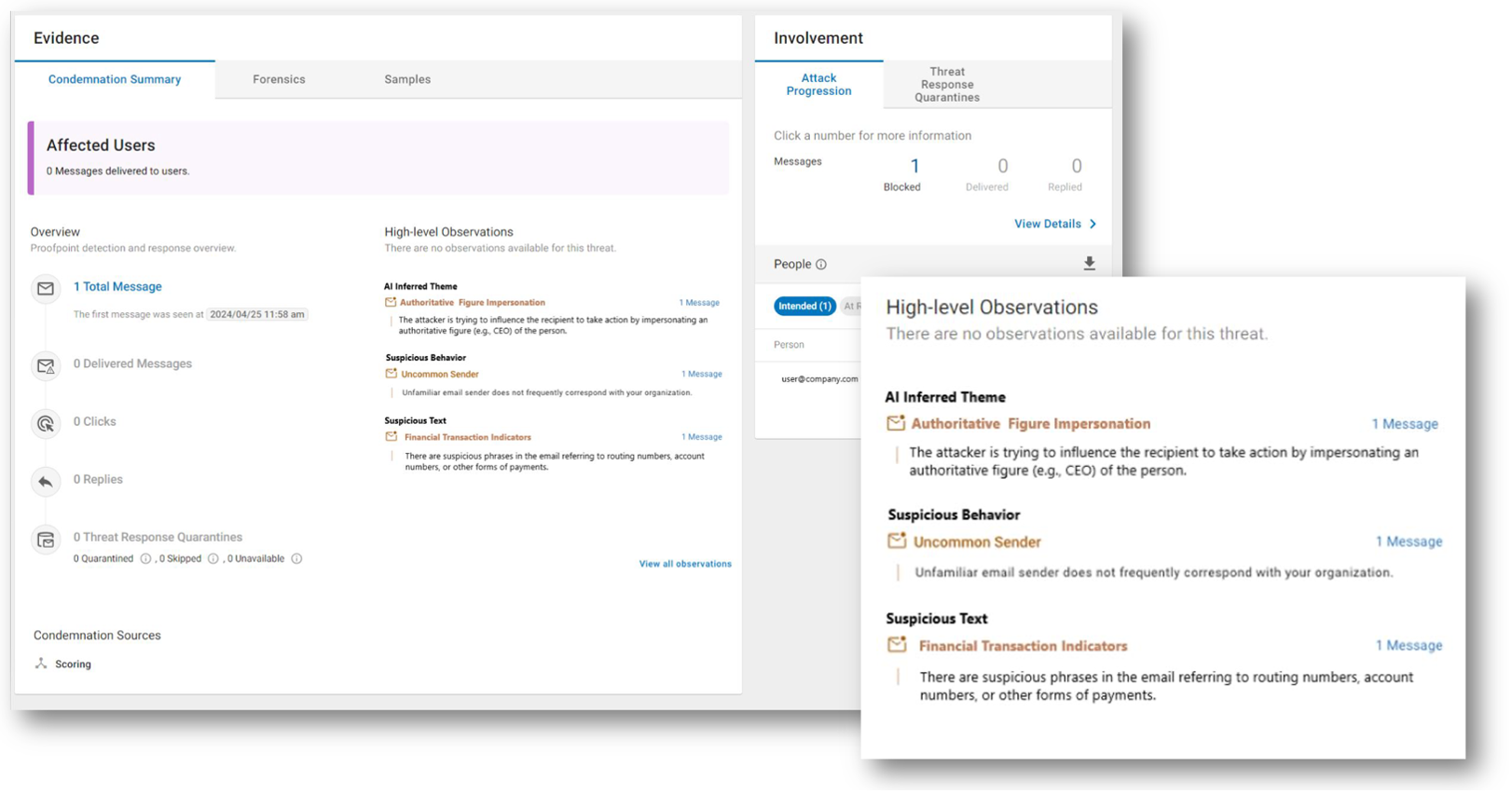
TAP Dashboard with semantic analysis. High-level Observations shows how Proofpoint summarizes the impersonation, including AI Inferred Theme, Suspicious Behavior and Suspicious Text.
Remediation: What are the lessons learned?
Here are a few lessons from this CEO impersonation scenario:
- Stop threats before users see them. Advanced technologies like semantic analysis can help detect and prevent threats before they reach a user’s inbox. This ensures that fewer threats slip through the cracks. It also reduces the risk of false positives and enhances threat detection efficacy.
- Proactively report suspicious messages. Reporting tools can ensure that threats are stopped quickly. So give users tools to proactively report suspicious emails in their inbox.
- Help users change their behavior. Threat actors will employ sophisticated methods to manipulate users into performing actions that compromise security by impersonating figures of authority. Security awareness training can help educate end users and empower them to report suspicious messages.
Proofpoint delivers human-centric protection
Proofpoint offers a human-centric approach to cybersecurity. We provide robust protection for your users and business against these and other types of attacks. We understand that people are the most targeted link in the attack chain, which is why we focus on protecting them.
Our new semantic analysis LLM provides high-fidelity detection and efficacy to stop advanced email threats before they reach users’ inboxes. Our modern approach provides continuous threat detection and analysis throughout the email delivery flow, from predelivery to post-delivery—and at click-time, too. This end-to-end protection allows your business to guard against new and emerging threats.
To learn how to protect people and defend data in the world of generative AI, register for our next webinar series, “In the Trenches with Threat Research: Innovations and Insights to Defend the Human Layer,” which started on June 6, 2024.

