Insider threats can come from anywhere at any time. Although there are well-known insider threat indicators and trigger events, one of the most challenging aspects of containing insider threats is identifying a user who may cause harm to the business—intentionally or not. This uncertainty can be daunting. And it is one of the reasons that insider threats are a leading challenge for CISOs globally.
Insider threat investigations are typically reactive. Cybersecurity administrators focus on risky users like leavers, employees on a performance improvement plan, or contractors once they learn about their potential risk to the company.
This is a valid way to manage known risks. But how can a business manage unknown risks? Proofpoint Insider Threat Management (ITM) has capabilities to help security teams do exactly that with dynamic policies on the endpoint.
Reactive monitoring poses challenges
The riskiest users in a business tend to fall into several categories. They include users who:
- Exhibit risky behavior, like downloading a high volume of sensitive files
- Belong to a predetermined risky user group; some examples include departing employees, privileged users with access to sensitive data and systems, and Very Attacked People™
- Have a high-risk score based on a number of indicators
Security teams typically build manual policies to monitor these users for unusual or risky behavior. When a user’s activity violates corporate policy, their activity is detected by and visible to security teams. Security teams can continue to monitor the user and apply prevention controls when needed.
This is a sound approach. But it relies on identifying the risky user ahead of time, monitoring their behavior and making manual changes to policies. For teams who may not have an approach to identify risky users, they may decide to monitor all users as “risky.” However, collecting data on all users is inefficient. It burdens the security team with too many alerts and false positives.
Another challenge for security teams is protecting users’ privacy to meet compliance requirements. Capturing visuals like screenshots in an insider threat investigation is crucial. It can provide irrefutable evidence that can be used to prove a user’s intentions. However, the collection of such information all the time poses privacy concerns, especially in regions with strict privacy regulations. Balancing security with privacy controls requires that data collection occur on a need-to-know basis.
Identify risky users with dynamic policies
Proofpoint ITM alleviates the challenge of knowing who your riskiest users are at all times. With dynamic policies for the endpoint, security teams do not need to write policies based on specific users or groups. Instead, they can dynamically and flexibly change a user’s monitoring policy in real time if a user triggers an alert. Dynamic policies allow security teams to do the following:
- Change the endpoint agent policy from metadata-only to screenshot mode for a specified time frame before and after an alert
- Capture screenshots only when behavior is risky and an alert is generated, thereby protecting the privacy of the user
- Define when visibility and control policies are scaled up or down on the endpoint
User scenario: a departing employee
Let’s walk through an example of a departing employee. Evan is a researcher at a global life sciences company. She has access to sensitive vaccine data due to the nature of her role.
Evan is being monitored as a low-risk user. That means metadata is being captured when she moves data, such as uploading a PPT file with sensitive data to a partner’s website or uploading a strategy document to the company’s cloud sync folder. However, Evan’s behavior, such as tampering with the Windows registry or any security controls, or downloading an unapproved application, are not captured.
Evan is going on a long trip. She wants to download some documents to read while she’s traveling. She plugs in a USB to copy the documents. Since Evan is trying to copy a document with sensitive patented information, an alert is generated when she plugs in the USB.
The alert triggers the endpoint agent to start capturing screenshots for a specified amount of time before it reverts to the base policy of capturing metadata only. The screenshot captured during the forensics policy can be used to support and accelerate an investigation. It provides irrefutable evidence for the company’s security, human resources, legal and privacy teams.
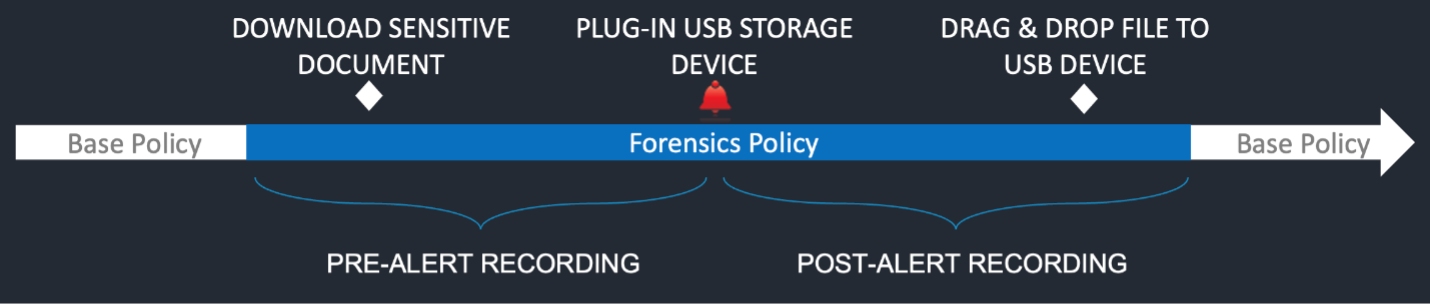
User scenario of a departing employee attempting to move data.
The security analyst will get an alert that Evan plugged in the USB. They can see a timeline of Evan’s activity and screenshots, which help them to understand exactly what she was doing before and after the alert was triggered. This additional context will help in an investigation by demonstrating intent.
The security analyst can toggle through the screenshots and rewind and move forward to get a holistic view of what Evan was doing before, during and after the alert. Rather than digging through numerous alerts, the security analyst has targeted context and alerts that help inform the response to the user’s actions.
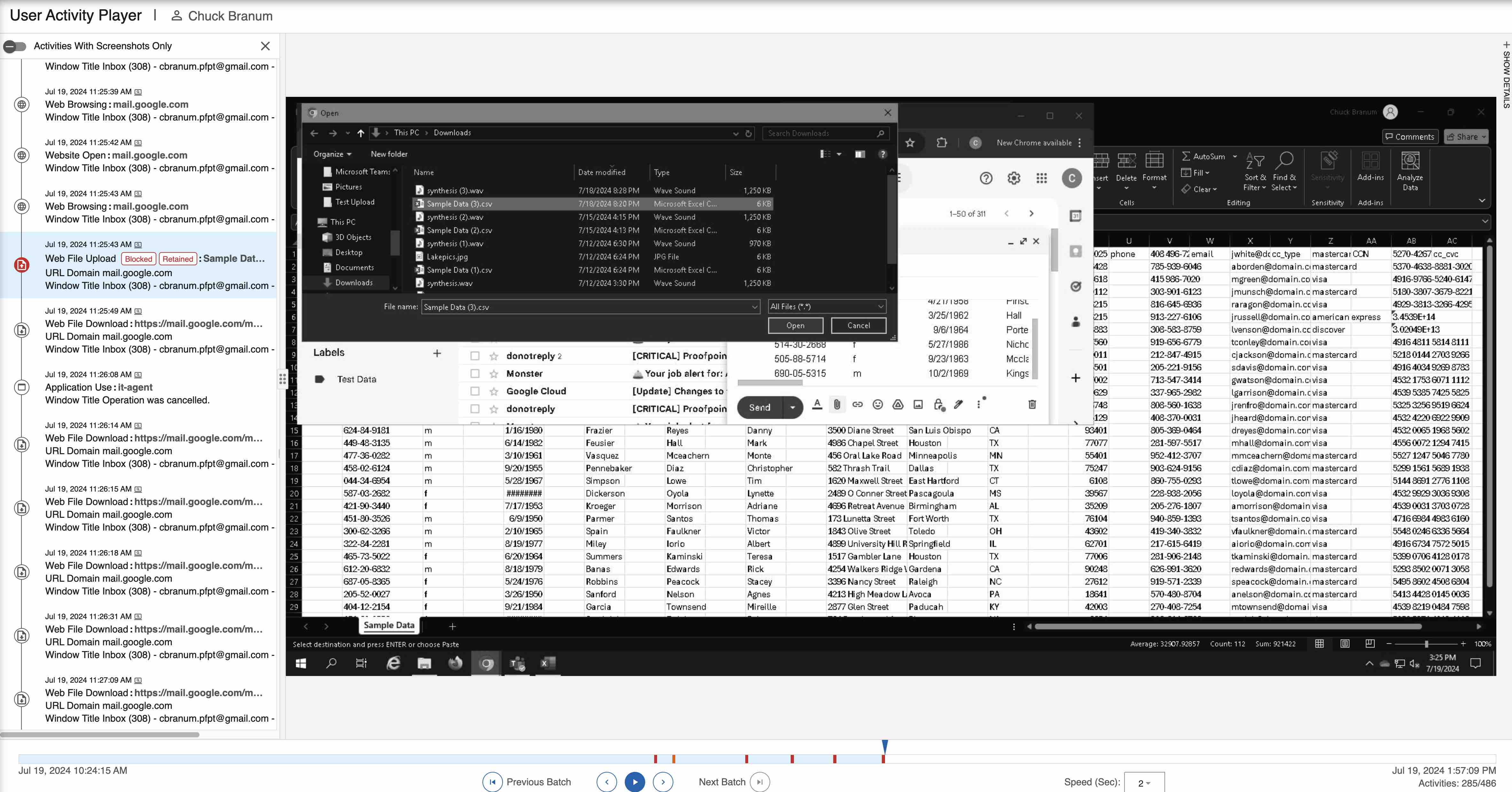
A timeline view of user activities and screenshots in Proofpoint ITM.
Dynamic policies help drive security analyst efficiency
Dynamic endpoint policies in Proofpoint ITM help security analysts to tackle one of their biggest challenges—monitoring risky users before they can cause harm to the business, like brand or financial damage.
With dynamic policies, security analysts do not need to know who their users are ahead of time. They can instead write rules to start monitoring a user when they exhibit risky behavior. Dynamic policies shift the responsibility of the security analyst from building manual policies to dynamically responding to a user’s risky behavior. That, in turn, helps analysts to work more efficiently. Dynamic policies can help them to:
- Make real-time policy changes, which alleviates the burden of writing manual policies based on a specific user
- Ensure objectivity by focusing on risky behavior across the organization instead of targeting specific users
- Ensure user privacy by capturing screenshots of user activity only when an alert is triggered
- Reduce their workload by providing actionable alerts
- Accelerate investigations by providing contextual insights and irrefutable evidence
- Decrease data storage needs by only capturing screenshots and metadata when needed
Learn more
Find out more about Proofpoint ITM and how it can help you contain insider threats. You can also read about the latest trends around data loss and insider threats in our 2024 Data Loss Landscape report.

