Digital transformation can put a modern enterprise at a crossroads. Security practitioners often find they must choose between the organization’s security and the employees’ productivity and privacy.
When companies use data loss prevention (DLP) tools, they are typically forced to make a binary decision when protecting corporate intellectual property; specifically, having to choose either to:
- Enforce strict prevention controls and employ full monitoring (a strict approach)
- Limit the impact on employee productivity and privacy (a flexible approach)
When determining which approach is best, you will carefully need to balance a number of competing priorities, including the following three aspects:
- Information security—protecting the company’s sensitive information
- User productivity—ensuring users have access to the data they need
- Employee privacy—respecting the privacy of employees when using company assets
Let’s review each of these aspects in detail to help you select an approach that may suit your organization’s needs.
Information security—protecting the company’s sensitive information
Securing sensitive information can’t be a one-size-fits-all approach because each organization’s definition of sensitive information can be different. Financial services may care about protecting credit card numbers, while government agencies may want to protect Social Security numbers. And biotech and life sciences companies need to protect scientific research, while manufacturing and high-tech companies likely want to secure engineering designs
Hence, understanding the information that you need to protect is the first step. And a modern information protection solution must provide a way to classify your information easily and represent it in DLP policies in a unified manner.
User productivity—ensuring users have access to the data they need
While protecting sensitive information is at the core of any DLP solution, it can’t come at the cost of user productivity, which keeps the business running smoothly.
Protecting your organization from risky users doesn’t require implementing a restrictive approach for all. Organizations should weigh the impact of productivity when employees arent't able to do their jobs effectively due to the limitations put on information access and sharing.
A modern information protection solution therefore must be flexible enough to implement various security policies, based on the employee dealing with the information (context) as well as the information being handled (content).
Employee privacy—respecting the privacy of employees when using company assets
A company’s privacy policy is typically dictated by two forces:
- Regulatory and compliance rules applicable to where employees are being monitored
- The company’s own culture for respecting employee privacy
Complying with privacy regulations is mandatory and dictates what data is monitored, how it is used, and where, how, and for how long it is stored, for example. Outside of these regulations, the company’s culture and factors such as the employees’ work locations (virtual or on-site) will provide additional challenges to implementing effective data-handling practices.
Regardless of the drivers, and the weight given to different factors, an effective information protection solution must, at the very least, provide the following:
- Flexible policy management to monitor risky users more aggressively than the rest
- Data storage options that are geographically diverse to handle data sovereignty globally
- Granular access to help ensure employee data is only available on a need-to-know basis
- Masking and anonymization to protect unwarranted exposure of personally identifiable information (PII), protected health information (PHI) and user identities
A strict vs. flexible approach
In our information protection deployments, Proofpoint has seen two broad approaches:
Strict:
- Start with the most aggressive prevention controls on all users
- Educate users on why strict controls are in place and when to ask for exceptions
- Grant exceptions through escalations to support business needs
Flexible
- Start with monitoring policies to understand potential risky behavior
- Educate users on best practices when sharing company information
- Establish prevention controls based on observations of risky behavior
In both approaches, respecting employee privacy is a shared concern that is addressed subject to local regulations and compliance needs. As an example, screenshots of employee activities are typically captured when sensitive company data is at risk or if the employee engages in misuse of corporate assets. But such capture is almost always avoided if there is a risk of capturing an employee’s personal information.
Information protection solutions from Proofpoint enable either of these approaches and also provide a hybrid approach for organizations that want to balance all three aspects—security, productivity and privacy—based on their business needs.
Determine the right approach for your organization
As you can imagine, choosing the right approach is more of an art versus science. As you look to balance the three aspects of security, productivity and privacy, consider the following questions:
- What are our business needs and compliance requirements? What is our industry, and what are our desired goals for our DLP program?
- How do the benefits align with our business goals?
If you’re in a regulated industry, and you need to restrict access to sensitive data for compliance, a strict approach may work best. If you want to enable your employees to share information quickly and remove impediments to innovation, you might need to consider the flexible approach.
Across our customer base, Proofpoint has found that financial services and government agencies are more likely to embrace the strict approach whereas high-tech industries tend to be more flexible and want to foster an open culture.
If your business employs a lot of third parties, your risk is higher—hence a strict approach may be necessary. Better yet, a solution that gives you the flexibility to target just risky users will provide you the ability to balance out the strict approach with a flexible one, also known as the hybrid approach:
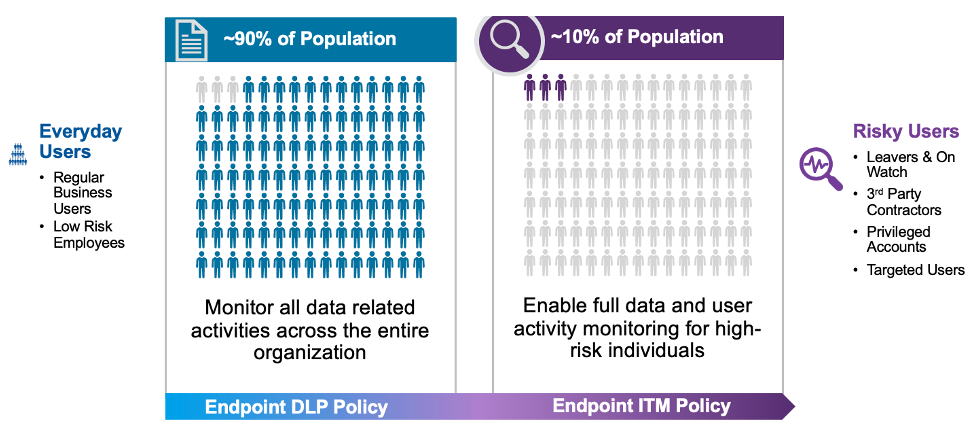
Figure 1. Overview of a hybrid approach for DLP.
Learn more
Check out the Proofpoint webinar on balancing security and productivity this topic to find out more about balancing security, productivity and privacy and see a demonstration of our Insider Threat Management solution.

