The Insider Incident of the Month blog series sheds light on the growing problem of email exfiltration of sensitive data to unauthorized accounts. It also examines how Proofpoint helps protect against these serious data loss events. Stories in this series have all been anonymized.
In today’s digital landscape, email is one of the most common tools that organizations use to communicate. However, with this widespread use comes a significant risk—namely, the careless or malicious sending of sensitive data to unauthorized accounts. Whether it’s a simple mistake or caused by a disgruntled or malicious employee, just one of these data loss events can have devastating consequences. This includes reputational damage, regulatory fines and financial losses.
Proofpoint regularly catches these insider data loss events during our complimentary email data loss assessments. During these assessments, Proofpoint helps organizations identify if their sensitive data is being exfiltrated to unauthorized accounts, like personal freemail accounts, private domain email accounts or even a family member’s email account.
Today, we’ll explore a breach at a midsize financial firm, which was caused by a malicious employee.
Background
Email data exfiltration occurs when someone inside an organization—like an employee, exiting employee, contractor or business partner—emails data to their own personal account or to an unauthorized third party. Malicious insiders are people who intend to cause harm. These insiders might exfiltrate data to take to a competitor, to sell to bad actors or to sabotage the organization.
Various factors can motivate them. Here are a few examples:
- Leaving to work at a competitor
- Business changes like mergers and acquisitions, and divestitures
- Resentment due to job changes or conflict with a supervisor
- Fear of job loss
- Poor job performance
The scenario
Recently, Proofpoint detected email data exfiltration during a customer’s assessment. In this case, the customer was a West Coast-based midsize financial firm, which specializes in asset management. An employee left the firm. But before they left, they exfiltrated a large amount of sensitive data to their private email account. A quick search on LinkedIn confirmed suspicions that they were now working at a competing financial firm.
The threat: How did the data loss happen?
The departing employee emailed data to a personal email address over a nine-day period which was detected during the assessment. The chart below shows the anomalous activity in red.
This reflects a typical pattern. When an employee leaves a company, there’s often an increase in the volume and frequency of sensitive data being sent within a short span of time.
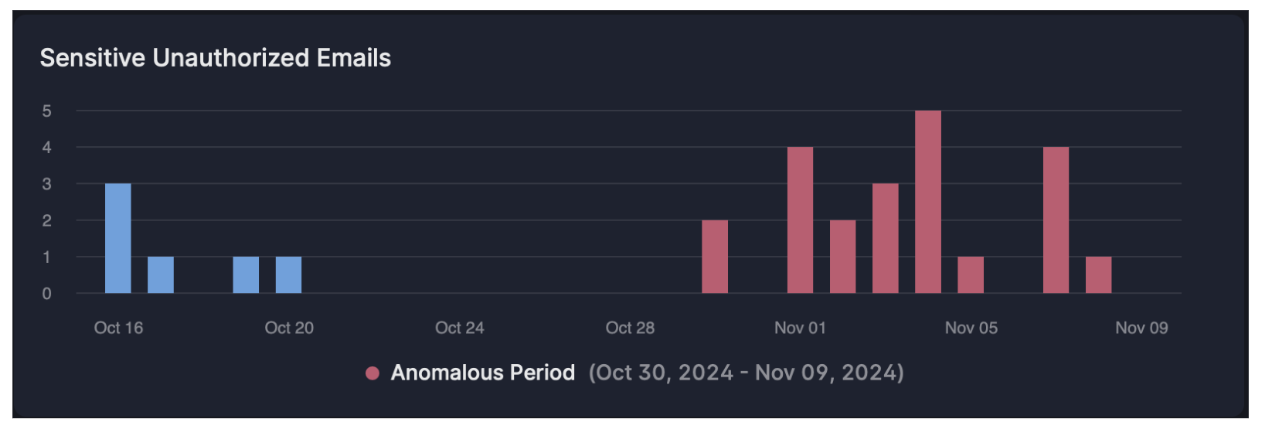
Proofpoint chart that shows anomalous email pattern.
The assessment: How Proofpoint identified this data loss
We deployed Adaptive Email DLP to learn from and detect anomalies based on six months of historical email data.
Adaptive Email DLP uses Proofpoint Nexus behavioral AI and the industry’s broadest email data sets. This enables it to analyze working relationships and to understand when sensitive data is being sent to unauthorized accounts rather than during regular business communication.
By analyzing and learning normal email sending behaviors, trusted relationships and how users handle sensitive data, Adaptive Email DLP understands when anomalous email behavior is occurring.
During the assessment, Adaptive Email DLP identified unauthorized email accounts and anomalous activity related to the sensitive data that was sent to those accounts. Then, we met with the customer to review specific events where we detected sensitive data loss.
As part of the review, we provided a list of all unauthorized accounts that were detected. We also provided all the emails that were sent to those accounts. Details about those emails included:
- Sender
- Recipient
- Subject
- Body
- Attachments
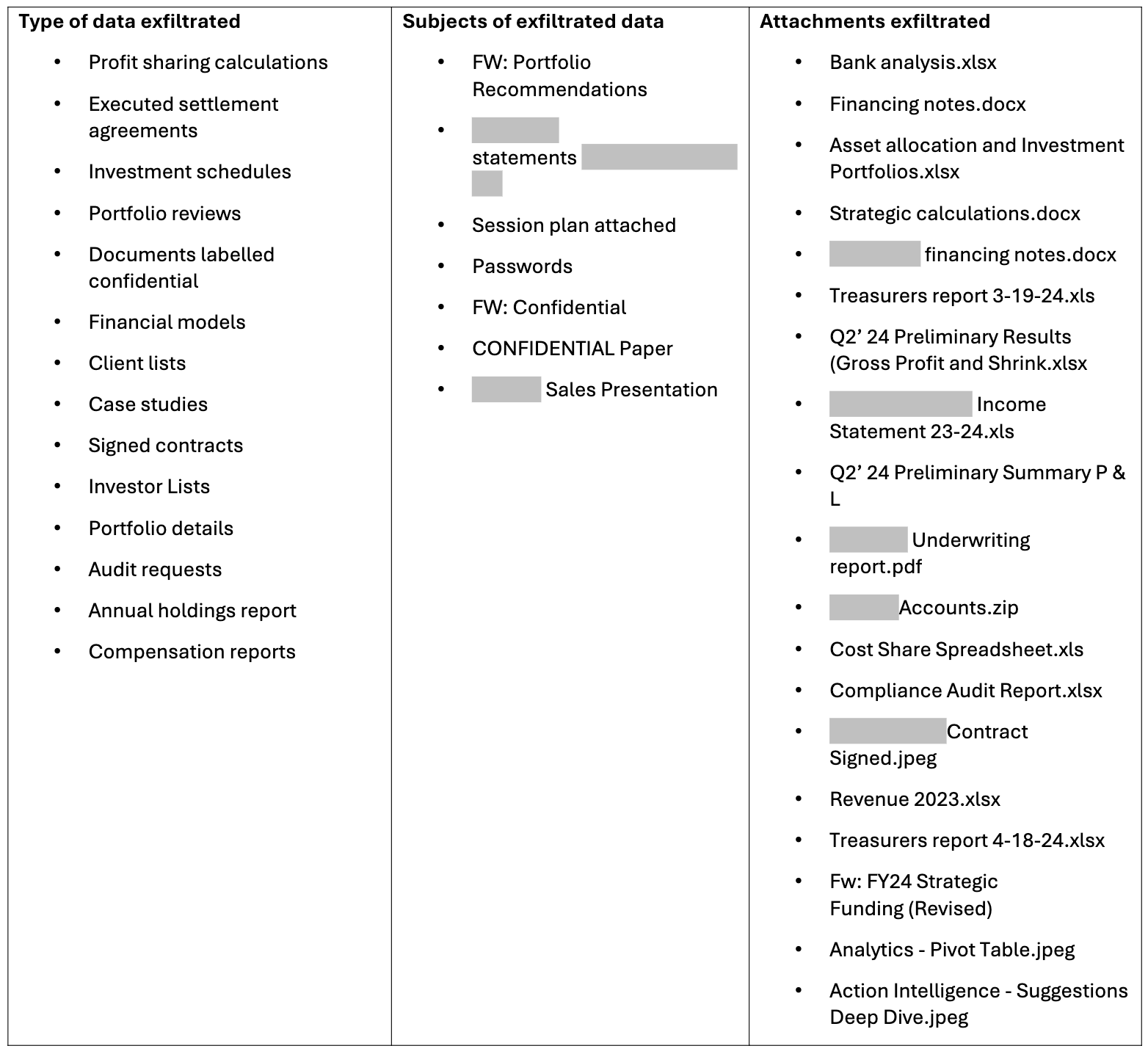
Anonymized examples of the data that was exfiltrated.
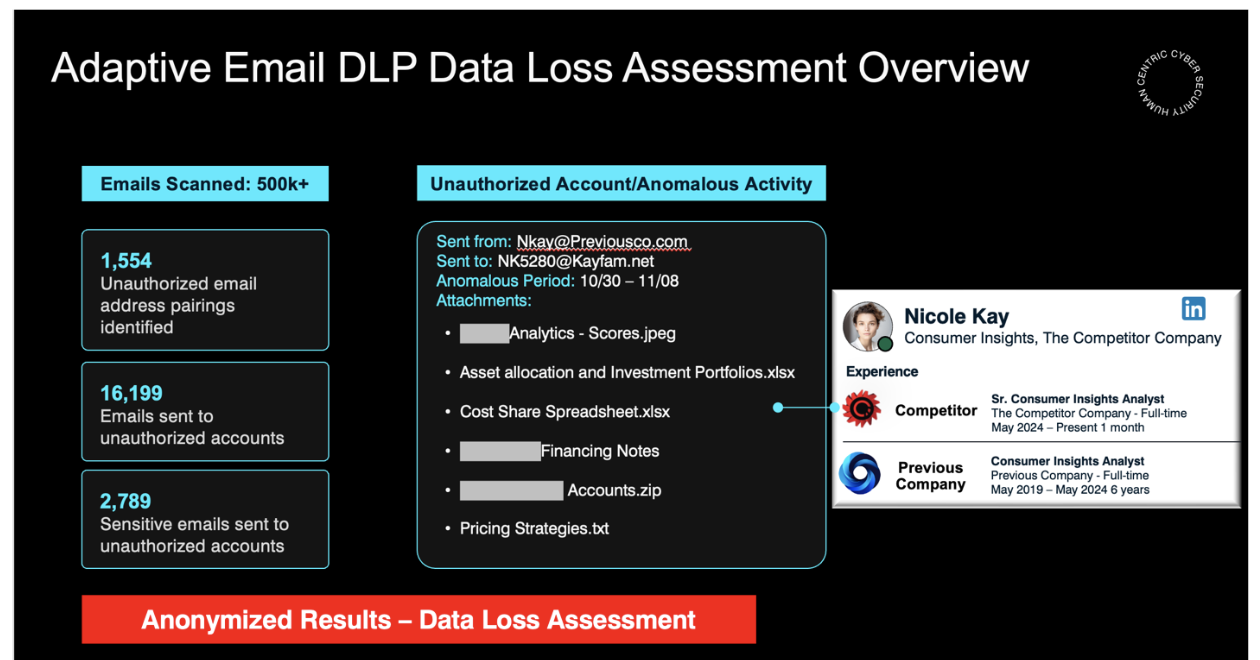
Sample Proofpoint email DLP assessment report.
Prevention: What are the lessons learned?
Here are some tips to stop your data from being sent to unauthorized accounts:
- Adopt a multilayered approach. Rules-based data loss prevention (DLP) is critical in preventing sensitive data loss. However, it focuses on predefined risks and specific RegEx patterns. An adaptive, behavioral approach is necessary to detect unknown risks that you can’t define in a rule. Look for a tool that uses behavioral AI and machine learning. These technologies can analyze context, the relationships between a sender and a recipient, as well as other important details to detect whether data is being sent to an unauthorized account.
- Use in-the-moment warnings. With an adaptive approach, you can implement in-the-moment nudges that warn users when their behavior is risky. This helps them make informed decisions. Plus, it reinforces your security policies. And it prevents emails with sensitive data from leaving your organization.
Proofpoint delivers human-centric protection
Sensitive data being sent to unauthorized accounts is a significant risk that organizations cannot afford to overlook.
Proofpoint Adaptive Email DLP offers a powerful, easy to deploy solution to mitigate this risk. By combining advanced Proofpoint Nexus behavioral AI and machine learning with ease of use, organizations can help keep their sensitive information safe while empowering employees to communicate more effectively and securely.
Proofpoint is a leader in human centric security. We secure more than half of the Fortune 100.Sign up for a confidential complimentary data loss assessment.
To learn how to stop sensitive data from being sent to unauthorized accounts, download our Adaptive Email DLP solution brief today.

