Protecting people and defending data are ongoing priorities for federal agencies whose missions are constantly under attack. These entities struggle to keep pace with an array of potent threats, like insiders who steal secrets about missile technology and threat actors who use living off the land techniques (LOTL).
Proofpoint can provide agencies with a critical edge in their efforts to defend data from risky users and detect real-time identity threats. Products to help with these challenges include:
This blog takes a closer look at these products and how they help our federal customers.
Understand the context behind user behavior with Proofpoint Insider Threat Management
Across all levels of government, data loss is costly—these incidents have cost agencies $26 billion over the past eight years. A critical first step toward preventing data loss and risky behavior is to understand that data does not lose itself. People lose it.
Employees, third parties and contractors have access to more data than ever—on their laptops, in email and the cloud. But you can’t reduce the risk of insider threats without first understanding the context behind user behavior. Context also helps you to choose the best response when an insider-led incident occurs, whether it’s due to a malicious, compromised or careless user.
Proofpoint Insider Threat Management can help you gain that vital context. It also helps you to move swiftly to address insider threats. Here’s how:
- Get a clear picture of threats. You can gain complete context into users and their data activity on endpoints, and web and cloud applications. User attribution is easy thanks to a clear, visual timeline and flexible, real-time screenshots.
- Identify risks proactively. Proofpoint includes preconfigured indicators of risk that can help you catch user activities in real time, like data exfiltration, privilege abuse, unauthorized access and security controls bypass. The out-of-the-box Insider Threat Library was built using feedback from our customers as well as guidelines from NIST, MITRE and the CERT Division of the Software Engineering Institute at Carnegie Mellon.
- Investigate faster. You can investigate incidents with more efficiency when you can see user intent. With Proofpoint Insider Threat Management, you can gather, package and export the evidence (who, what, where, when and user intent) and share it easily with groups outside of security such as HR, legal and privacy. This saves time and reduces the cost of investigations.
- Get better time to value. Proofpoint Insider Threat Management, has a single, lightweight user-mode agent that is easy to install and invisible to your users. With a converged DLP and ITM solution, you can monitor everyday and risky users.
Gain efficiencies and manage risks
Here are more ways that Proofpoint Insider Threat Management helps federal agencies:
- Manage alert rules efficiently. Alert rules are grouped by categories and assigned to user lists, which streamlines management.
- Comply with privacy laws. Agencies can protect privacy by anonymizing users in the dashboard, which helps eliminate bias in investigations.
- Manage risks at a department level. Large agencies can manage employee risks based on their department or group by using Active Directory group-based permissions. Each group has a dedicated security team member or manager.
Meet zero trust and CMMC needs
Agencies can use Insider Threat Management to meet their zero trust and Cybersecurity Maturity Model Certification (CMMC) needs as well. Proofpoint capabilities support several pillars of Zero Trust and more than seven domains of CMMC. For Zero Trust, Proofpoint helps agencies align to these pillars:
- Department of Defense: Data and Visibility and Analytics Pillar
- Cybersecurity and Infrastructure Security Agency: Data and Devices Pillars
Proofpoint Information Protection products help our customers with these CMMC domains:
- Access Controls
- Asset Management
- Audit and Accountability
- Configuration Management
- Incident Response
- Media Protection
- System and Information Integrity
Protect your identities with Proofpoint Identity Threat Defense
Proofpoint Identity Threat Defense protects against attackers who exploit your identities and attempt to move laterally inside your agency. These threat actors include nation states, ransomware actors and insider threats.
Our deception technology can help your agency spot attackers as they are attempting to escalate their privileges and move laterally in your agency. In addition, Proofpoint discovers and automatically remediates identity vulnerabilities that exist in your agency. This includes:
- Identities that are unprotected on endpoints
- Identities that are unprotected due to Active Directory misconfigurations
- Identities that are missing from PAM and other identity repositories
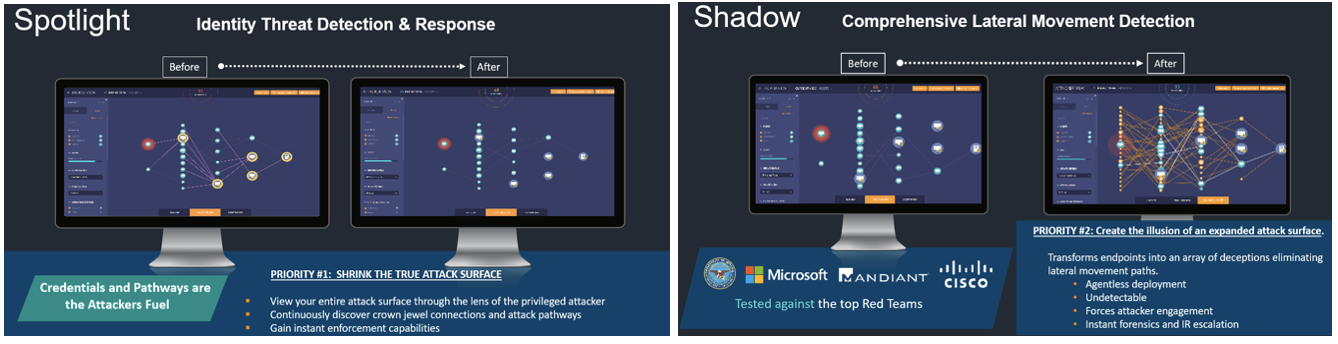
There are two Proofpoint Identity Threat Defense components: Proofpoint Spotlight and Proofpoint Shadow.
Learn more
Federal agencies are under pressure to protect vital data while enabling employees to carry out their missions. To get more details on how Proofpoint helps to protect federal agencies, see our:
You can find information on how Proofpoint Insider Threat Management meets our federal customers’ needs in this white paper. For Insider Threat Management use cases, visit this page.
To learn how Proofpoint Insider Threat Management and other products from Proofpoint meet NIST Cybersecurity Framework requirements, download this white paper.

