At Proofpoint we’re passionate about continuous improvement, and we spend quite a bit of time thinking about product enhancements. We’re excited to share some major updates to the platform that will help you, our customers, better protect your organizations against insider threats.
Not an Proofpoint ITM customer yet? Test drive ITM now.
Key capabilities introduced in ITM 7.4
Streamline Investigations
The ITM platform not only focuses on what users are doing, but also on what data is doing. Whether a sensitive report has been downloaded from your CRM cloud application and moved to Dropbox or a strategic presentation has been downloaded from your SharePoint portal, ITM provides customers with the best tools to drastically decrease mean time to remediate any insider threat-related issue that may arise.
Proofpoint ITM 7.4 introduces a fresh feel and makes the already clear UI even easier to use. You can now see a summary of data activity, such as file downloads or exfiltration to the cloud. This is visible right inside the session summary and ensures security analysts and investigators do not miss potential data exfiltration activities while reviewing the session. Adding the application or website involved with the user activity also provides investigators with better context around what has happened making it easier than ever to spot suspicious activity in sensitive applications.
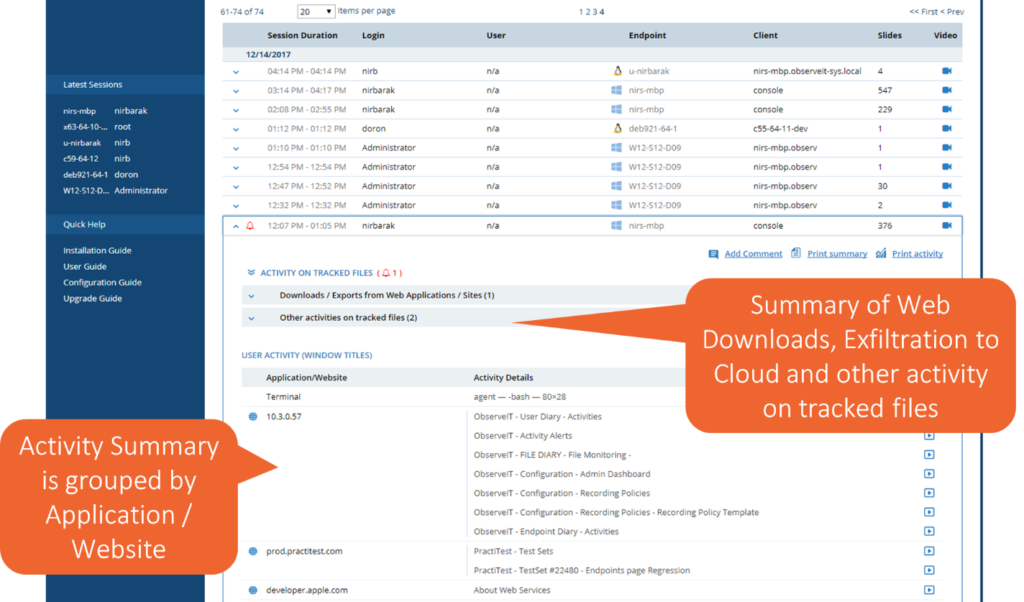
Proofpoint ITM 7.4 makes insider threat investigation easier and more efficient than ever by:
- Processing and providing data faster than ever before (up to 10x faster, in fact), including when customers need to access large amounts of recording data in the User and Endpoint Diaries
- Offering faster and more flexible searching capabilities. Search also works asynchronously, and the user can cancel a search query at any time if they decide it is no longer pertinent
Do More with Less
- ITM is well-known for its lightweight and robust agent. Because of this, our customers have been able to deploy ITM across a wide variety of endpoints without creating headaches for IT or end users. Allowing maximum agent density per environment is a core focus for us because it streamlines and simplifies the user experience.
- For this reason, ITM 7.4 dramatically reduces customers' total cost of ownership (TCO) for deploying our platform. Now, the same number of users can be monitored with less backend infrastructure. This means existing deployments can expand to monitor more users without needing to add application servers or upgrade database servers. In other words, more bang for your buck!
- ITM 7.4 can also handle up to four times more capacity of ingested metadata
Go Full Stealth, if You Choose
Some of our customers need the ability to monitor users in full stealth mode. Others require the ability to monitor only certain employees in stealth (such as departing employees or those on a watch-list). For security reasons, some organizations choose to ensure these users do not know they are being monitored.
Advanced technical users, such as IT administrators or developers, are sophisticated enough to search the endpoint to determine whether the ITM agent is installed and running. Unfortunately, these same users can pose a significant insider threat risk.
ITM 7.4 better hides the Windows agent by renaming processes, files, and other resources that might enable advanced users to uncover the agent.
Integrate with Your Existing Security Stack
ITM now offers an even tighter integration with many other types of software and systems. This includes:
- HR systems that manage the list of offboarding and watch-list employees
- Sensitive source code files within control systems
- Critical servers and relevant IP addresses
- Security systems
- …and more
ITM 7.4 automates and simplifies integration with both IT and security systems by providing APIs to populate lists with data from other systems. This enables users to easily configure the alerts being triggered and have more control than ever over what types of data are monitored and when they are notified of an insider threat risk.
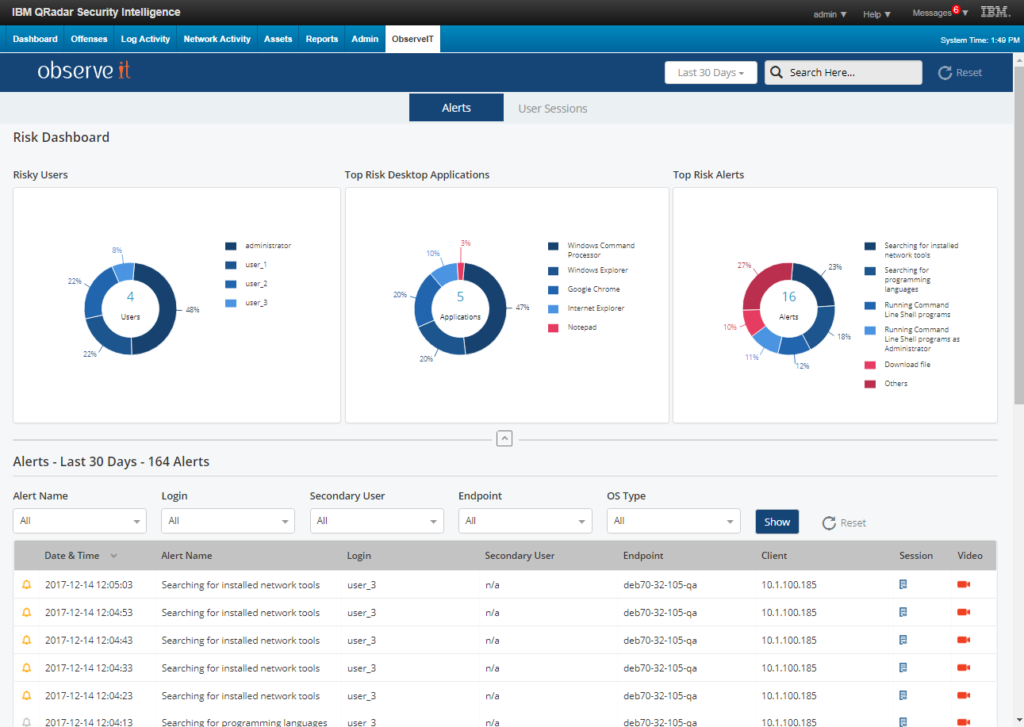
We have also improved SIEM integrations, especially for IBM Qradar, by introducing the new ITM app in the IBM Security App Exchange. The new app provides two dashboards, covering alerts and user sessions. This allows customers to investigate users directly from their SIEMs and to enhance detection and analytics by correlating ITM metadata with other data sources.
Uncover Your Blind Spot
Our Mac agent now provides enhanced visibility for a major blind spot that affects many organizations: ITM 7.4 incorporates the ability to view files and folders being copied on Mac computers, adding Mac-specific scenarios to better detect insider threats, and supporting mass agent deployment for the growing number of Mac users.
Let Us Know What You Think
We’re excited for you to check out our updates! Our goal is to continuously evolve in ways that make it easier and more seamless for our customers to detect and prevent insider threats.
Not an Proofpoint customer yet? Test drive Proofpoint ITM now.

