(Updated on 02/18/2021)
Organizations using UNIX and Linux no longer have to remain in the dark, fully trusting every action that privileged users, including third-party contractors, make once they gain access to the network. The Proofpoint ITM UNIX Auditor monitors and records all privileged activity from the moment the user logs in until the end of the session.
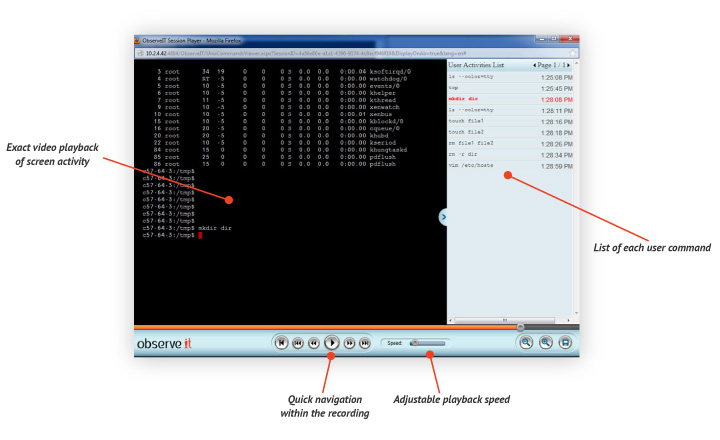
The session recordings capture video of all on-screen activity, while also transcribing every action as users work in UNIX and Linux servers and desktops. Using the most advanced technology, Proofpoint ITM also captures critical hidden information about each user command, including the resources affected and system calls made. This content analysis data is immediately available for free-text keyword searching so that you never need to sit through hours of video to find what you’re looking for.
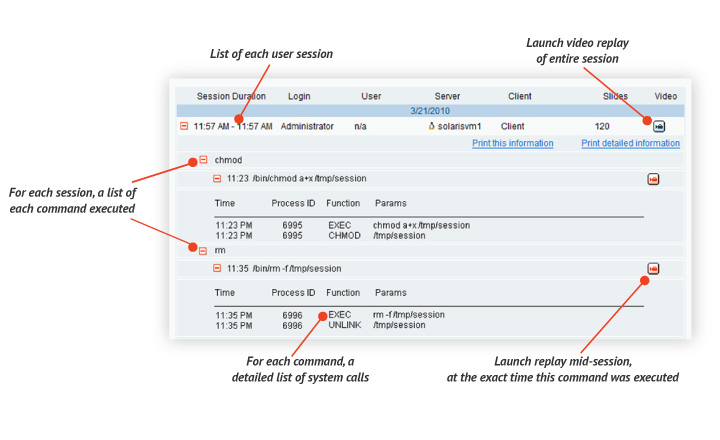
Advanced Keylogger with Deep Search
Detailed session data is immediately available for free-text keyword searching. Matches will be found in:
• user-executed commands
• script-executed commands
• underlying system calls
• names of files/resources affected
• keyboard keystrokes
• terminal screen output
This means that every file create, delete, open and permission change, process creation and link creation is captured and searchable.
The platforms that are supported in UNIX and Linux are:
| UNIX | Linux |
| Solaris (i386/spark) 10u4 – 10u11 | Rhel/CentOS/Oracle Linux (32/64 bit) – 5.0 – 5.10, 6.0 – 6.4 |
| AIX 5.3 TL10 and up, 6.1 | Ubuntu (32/64 bit) – 10.04, 12.04 |
| HPUX (IA) 11.23/11.31 | SuSe (32/64 bit) – 10 SP2 – 10 SP4, 11 – 11 SP2 |
Captures Commands Hidden Within Scripts
If the user runs an alias script that includes system calls to delete files and change user permissions, this info will all be captured. Likewise, Proofpoint ITM captures every file and resource affected by each user command (e.g., if the user typed rm *.txt, Proofpoint ITM will capture the actual name of each deleted file).
Every resulting search hit is linked directly to the portion of the video where that action occurred! This makes it incredibly easy to find the exact moment that an action was performed from among thousands of hours of video.
No other product on the market offers these must-have user auditing features!
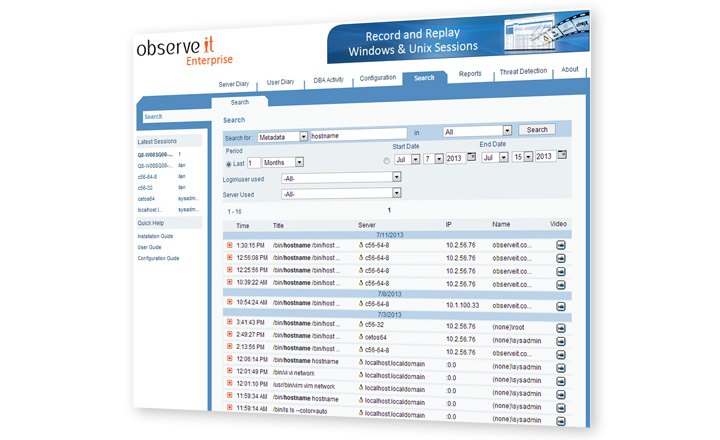
Zero-Gap Recording
Proofpoint ITM records and analyzes user activity over any connection protocol (SSH, Telnet, ICA, direct console login, etc.). Beyond Unix/Linux environments, Proofpoint ITM also records every application and system area in Windows servers and desktops, as well as Citrix published applications, Citrix virtual desktops and VMware environments.
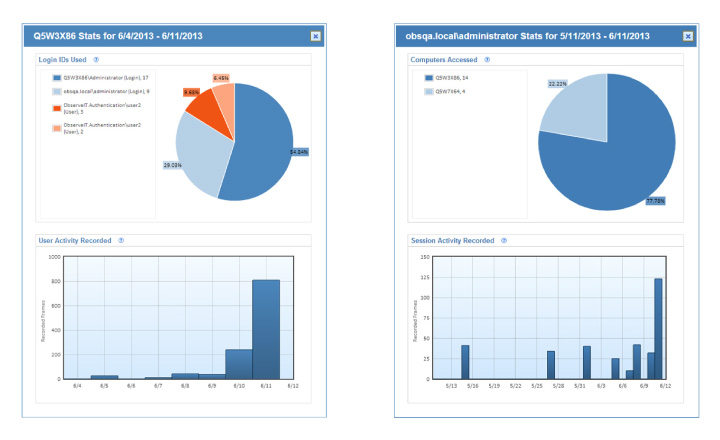
Valuable Usage Reporting
In addition to Proofpoint ITM’s granular per-session auditing features, the system also includes graphical displays and a Threat Detection Console to help administrators and security staff keep an eye on what’s going on across the company’s servers.
Secure and Reliable
Unlike simple UNIX/Linux utilities that log user actions, there is no way for users (even root users) to shut down the Proofpoint ITM recording agent. The agent embeds itself into any shell derived from a login process. Because this mechanism is connected to both the shell and the auditing process, it is impossible to disable or tamper with the agent without closing the shell.
All session data sent by the agent to the Proofpoint ITM server is encrypted before transmission using industry-standard SSL. In the event that agent-server communication is temporarily lost, data is cached locally until the network connection is restored.
Key Benefits of Proofpoint ITM Session Recording
- Better IT security and early data breach detection:
Custom real-time alerts and integration with SIEM/NMS systems provide early warning of both human error and malicious actions. - Easier compliance accountability:
Monitor and audit local users, remote users and third-party vendors to satisfy PCI, HIPAA, SOX and ISO 27001 security requirements. - Total remote vendor monitoring:
Review and search remote vendor sessions to ensure that vendors are meeting their obligations and posing no risks to the organization. - Better end user experience/help desk:
Immediately access video recordings, even live activity streams, of every user session to assist with help desk tasks.

