The Story So Far
Data exfiltration is a really big problem for cybersecurity teams and executives in a wide variety of industries. In fact, 2 out of 3 insider threat incidents are caused by employee or contractor mistakes, which can lead to data breaches and exfiltration.
The reason for this is that there are so many ways for your employees and third-party contractors (your potential insider threats) to exfiltrate valuable company data. From the hundreds of web applications, from webmail to cloud storage drives, to physical means like USB thumb drives, your insiders could be knowingly or inadvertently transmitting sensitive information outside of your protected space.
How can any security team be expected to protect so many exit points, and know who, did what, and for what purpose?
What's New
Version 7.6 of our Insider Threat Management platform enhances the existing user activity metadata collection capabilities with something that we call: File Activity Monitoring (FAM).
File Activity Monitoring does exactly what it sounds like: helps you monitor file activity. Combined with Proofpoint ITM’s unique user activity data streams, FAM helps provide the added context that you need to be able to detect, investigate, and stop data exfiltration within your organization.
Your Job, Made a Little Easier
The File Activity Monitoring tools that arrive in Proofpoint ITM version 7.6 can proactively alert you (based on customizable indicators) when insiders are distributing files outside of the scope of policy.
For example, if your policy disallows file sharing (i.e. uploads) to a web application like Dropbox, you might receive an alert notifying you that an insider is acting “riskily.”
Be Selective, Or Cast a Wide Net
With Proofpoint ITM 7.6, you can choose exactly which file and user activity is worth watching, broadening or narrowing the scope as needed.
For example, if you would prefer to include only web applications that contain sensitive information such as internal content hubs (e.g. Sharepoint), sales and support portals (e.g. Salesforce), and financial and HR applications (e.g. Workday).
Let’s See it in Action
In the event that you start monitoring file activity (such as a user download from a web application, webmail attachment, social media posting, or upload to cloud storage drive), Proofpoint ITM can keep track of the files and alert you.
-
Proactive Alerts
A Proofpoint ITM alert was triggered when a file was uploaded from an insider’s local system to the web.
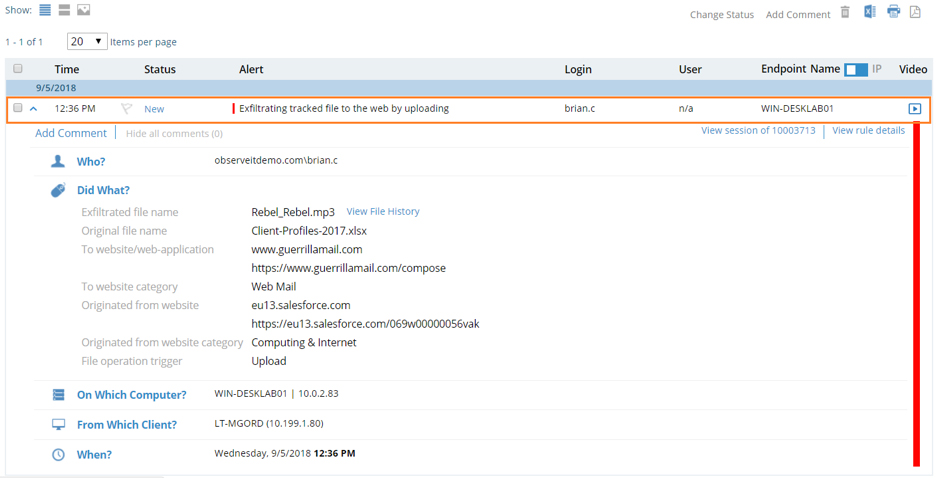
It’s important to note that even if the original download gets moved, copied, or renamed, Proofpoint ITM will continue to track them to the exfiltration point. (In this case, Guerilla Mail.)
-
Timeline View of User Activity
After receiving the initial alert, you may wish to investigate the incident further. Proofpoint ITM delivers a full chronological timeline view of everything that happened from the insider’s perspective, before and after the file activity occurred.
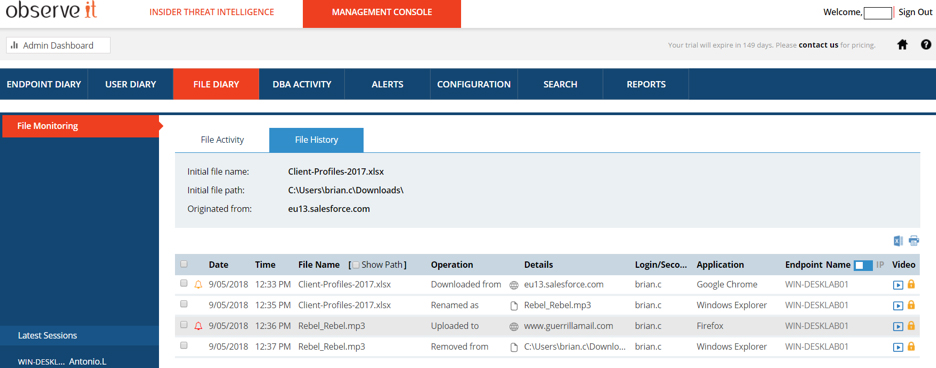
This provides much needed context for assessing the risk posed by the activity.
-
Control Which Files Are Monitored
Proofpoint ITM platform administrators have full visibility into which files are currently being tracked on each endpoint, and what can be excluded from tracking.
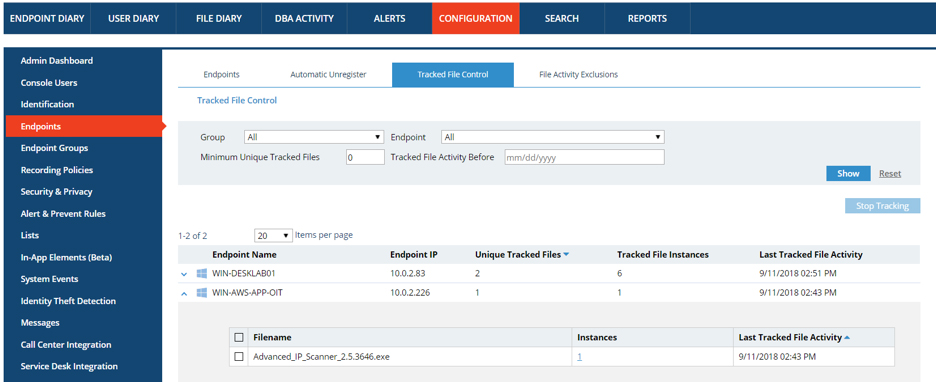
-
User-mode Agent
Proofpoint ITM lightweight user-mode agent technology tracks user Web file uploads and downloads without requiring any additional browser plug-ins, this means your IT teams can be assured that they will not be flooded with support tickets reporting browser and application crashes or even worse blue screens on their workstations.
What's Next
If you’re a current Proofpoint ITM customer, you can learn more about Version 7.6 (and how to upgrade) over on our Product Release page.
Not a current Proofpoint ITM customer? That’s okay! You can start learning more about our Insider Threat Management platform on our homepage.

