Many medium-sized and large organizations allow their business users to access the company’s Unix/Linux servers only from Windows desktops via SFTP. This approach is more secure than allowing users to connect to those machines using SSH or NFS.
Business users and administrators connect to Unix/Linux servers using SFTP for various purposes such as downloading log files, uploading software patches and backing up or restoring databases. Typically, these tasks are performed using a command-line interface or using Windows utilities with SFTP protocol.
For Unix/Linux servers hosted in the cloud, SFTP is the only method typically provided to get files or data on or off the machine.
With all of these activities performed by a wide range of users, securing data can be a challenge. Companies can mitigate risk by utilizing a zero-gap User Activity Monitoring solution capable of tracking every action that users take via SFTP. Activity on Unix/Linux machines performed via SFTP does not necessarily involve an interactive shell session, there may not be keystrokes to log or screens to record.
Therefore, it is necessary for the User Activity Monitoring solution to monitor the SFTP protocol itself. Otherwise, there would be a significant security gap that can dramatically increase the risk of undetected data breaches or system corruption on Unix/Linux servers.
Monitoring and Recording User Activity in SFTP Sessions with Proofpoint ITM
Proofpoint ITM records every action that users perform on Unix/Linux machines via SFTP, regardless of the client software used. This is unlike some systems that monitor SFTP activity by limiting SFTP monitoring to specific tools or forcing users to work with a proprietary client.
Proofpoint ITM records both the executed commands and the resulting output of each command. The recordings generate easily reviewable and keyword-searchable user activity logs, along with screen simulations showing the commands and output as if they had appeared on screen. Individual logged actions are linked directly to the portion of the simulated video where they occurred.
Additionally, security administrators and auditors can define alerts to be triggered whenever specific user actions occur. Focusing on scenarios of greatest interest, these alert rules can combine various parameters without creating a plethora of unwanted or irrelevant alerts.
The parameters that can be combined are:
- SFTP command
- SFTP command parameters (e.g., directories, file names, command switches)
- The server machine/group on which the command was executed
- The user/group executing the command
- The client machine/group from which the command was executed
- Day of week, time of day, particular dates, etc.
How it Appears
In the following screen shot, exhibited is an activity log of an SFTP session performed on a Linux server. Note that the commands are grouped and expandable/collapsible for easy review. Every command has a video play icon on the right that launches a simulated screen video, showing that particular command along with its output, within the chronological order of the session’s SFTP commands.
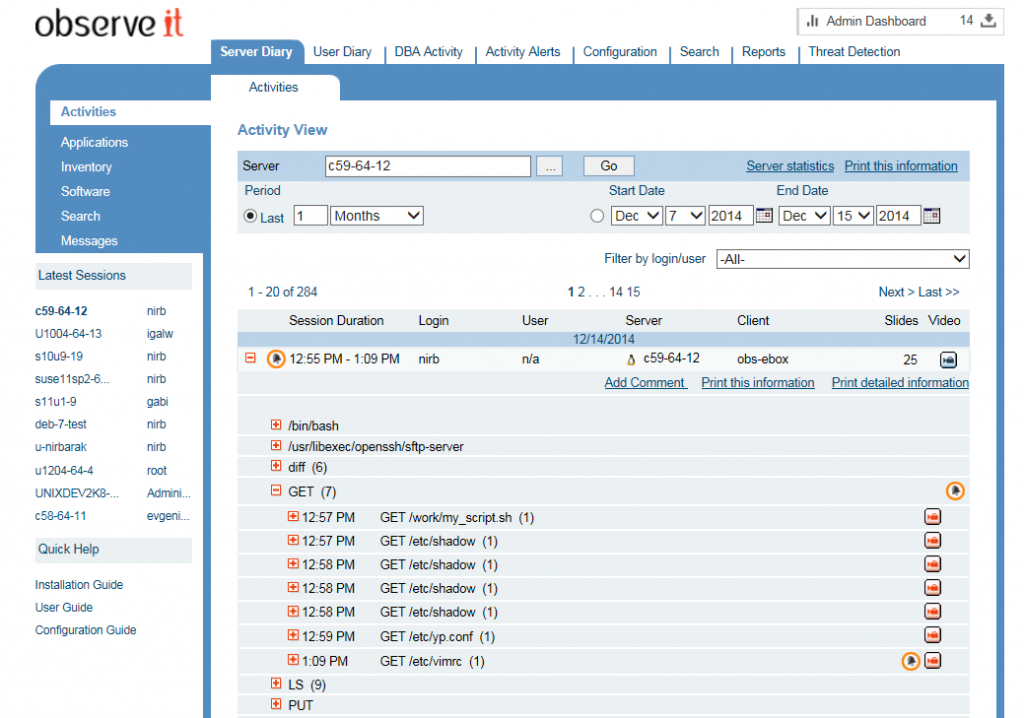
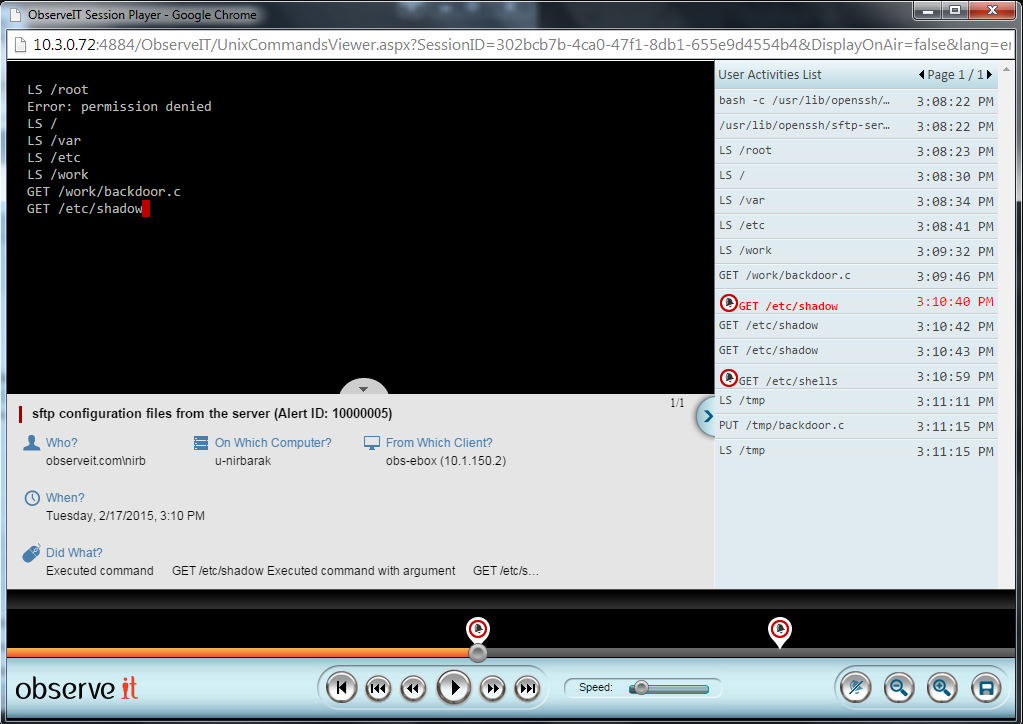
Below is an image of the session player, showing a visual representation of an SFTP session along with a chronological command log. In this screen shot:
- the simulated session screen, showing both commands and command output
- the activity log panel on the right
- the alert icons in the activity log panel highlighting commands that generated alerts
- the alert details panel at the bottom showing the specifics of the generated alert at the current video play location
Try it Yourself!
Download a free 15-day trial of the full-featured Proofpoint ITM Enterprise, and see how easy it is to monitor everything that occurs in SFTP sessions in your own environment. Of course, you’ll also have the opportunity to experience the value of comprehensive User Activity Monitoring across all your Windows, Unix/Linux, Citrix and VMWare systems. After your trial, purchase the solution or keep Proofpoint ITM Lite, free forever. Try it now!
Click here to take a look at last week’s Tech Tuesday blog post “Leverage Active Directory to Quickly Implement a Focused User Activity Monitoring Solution.”

