After reading the book Nudge: Improving Decisions About Health, Wealth, and Happiness, it is tempting to believe a well-crafted, perfectly timed pop-up message will move people away from engaging in unsafe online behaviors and toward building better cybersecurity habits. But let’s be honest. If it were that simple, then we wouldn’t be seeing the ongoing financial losses that many individuals and organizations are experiencing each year.
Instead, it is more productive to talk about the judicious application of nudging to this incredibly complex problem. We wish to understand how the practice of nudging fits within the broader scope of cybersecurity education and behavioral change. The purpose of this blog is to lay the conceptual groundwork for deciding when nudging is appropriate, as well as maintaining a realistic understanding of the magnitude of the impact.
Toward that end, we will attempt to address three important questions when considering nudging in the context of cybersecurity education and behavioral change:
- What is a nudge? Conversely, what is not a nudge? Where do we draw the line?
- Under which conditions are nudges effective, and what is the expected magnitude of the effect?
- Assuming nudges are cheap and easy to ignore (by definition), what is the alternative?
Question 1: What is a nudge? What is not a nudge?
As stated above, the concept of a nudge was made popular in 2009 with the publication of Nudge: Improving Decisions About Health, Wealth, and Happiness. In the past 15 years, we have collected ample evidence of its efficacy.
One advantage of nudge theory is its broad applicability. It has been shown to facilitate better behaviors in several disparate domains, including auto-enrolling employees into retirement plans, increasing the number of organ donors, and the number of people who pay their taxes on time. These benefits were achieved by architecting sensible defaults and crafting well-designed messages for the target audiences.
The broad applicability might be related to the all-encompassing definition of what counts as a “nudge.” The authors Richard H. Thaler, and Cass R. Sunstein define a nudge as, “Any aspect of the choice architecture that alters people’s behavior in a predictable way without forbidding any options or significantly changing their economic incentives.” One easily overlooked aspect of the nudge definition is, “the intervention must be easy and cheap to avoid” (my emphasis).
In other words, a nudge aims to influence the decision a person makes without taking away any options. A good example of this is putting healthier foods at the beginning of a salad bar. You can still wait and choose to fill your plate with desserts. However, given that many people choose the first food that sounds good, having salad ahead of dessert makes people more likely to pick it.
By this definition, then, a policy should not be considered a nudge because a policy expressly forbids a specific action, behavior or choice. This is problematic because most cybersecurity behaviors fall under “policy violations.”
Consider, for example, an organization that does not allow its employees to use third-party storage solutions like DropBox. If an employee attempts to save their work-related files on an unsupported storage platform, then a data loss prevention (DLP) policy might be triggered, thus preventing them from executing their action (see Figure 1).
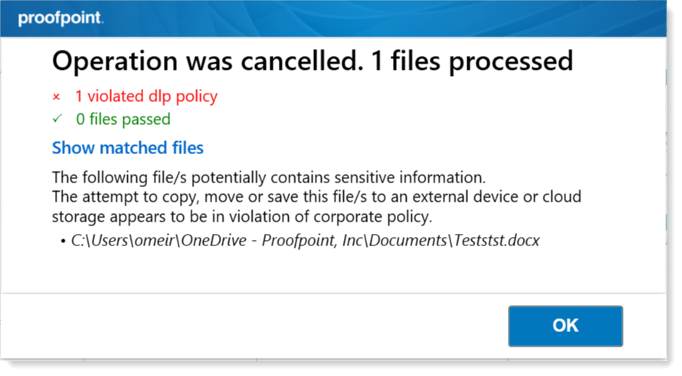
Figure 1. A DLP warning to the end user that their action has been blocked.
If a pop-up message explains what happened, then that would not count as a nudge, under the strict definition, because it prevents the end user from taking their preferred action. Instead, this message might be considered “feedback” or a “just-in-time learning opportunity” that reiterates or reinforces the company’s DLP policy.
It is also important to consider the pragmatics of nudge delivery. Policies are rarely included at the decision point. Even if they were, would we really want employees reading a data-sharing policy each time they want to share a file? Probably not.
Question 2: Under which conditions are nudges effective, and what is the expected magnitude of the effect?
Are nudges effective? On balance, it is safe to say that nudges are indeed effective. In a metanalyses, between 66% and 62% of interventions that used nudges significantly impacted the target behavior.
The academic literature evaluating behavioral interventions that implement a nudge suggests there is much to celebrate. In a meta-review of the literature, it is estimated that the average effect size is around 8.7 percentage points uptake of the nudge intervention over the control group.
However, the magnitude of the effect drops precipitously when we move out of the lab and into the real world. The U.K. and U.S. governments have both implemented what is referred to as “nudge units,” which are focused on public policy issues that includes a behavioral component. For example, suppose the United Kingdom takes up an initiative to reduce the number of drivers who do not pay their parking tickets, which results in lost revenue for the government. Based on the academic literature, we might expect to see an 8.7% increase in payments.
In a review of the real-world nudge units, there is less to celebrate. The efficacy rate drops to about 1.4 percentage points (see Figure 2).
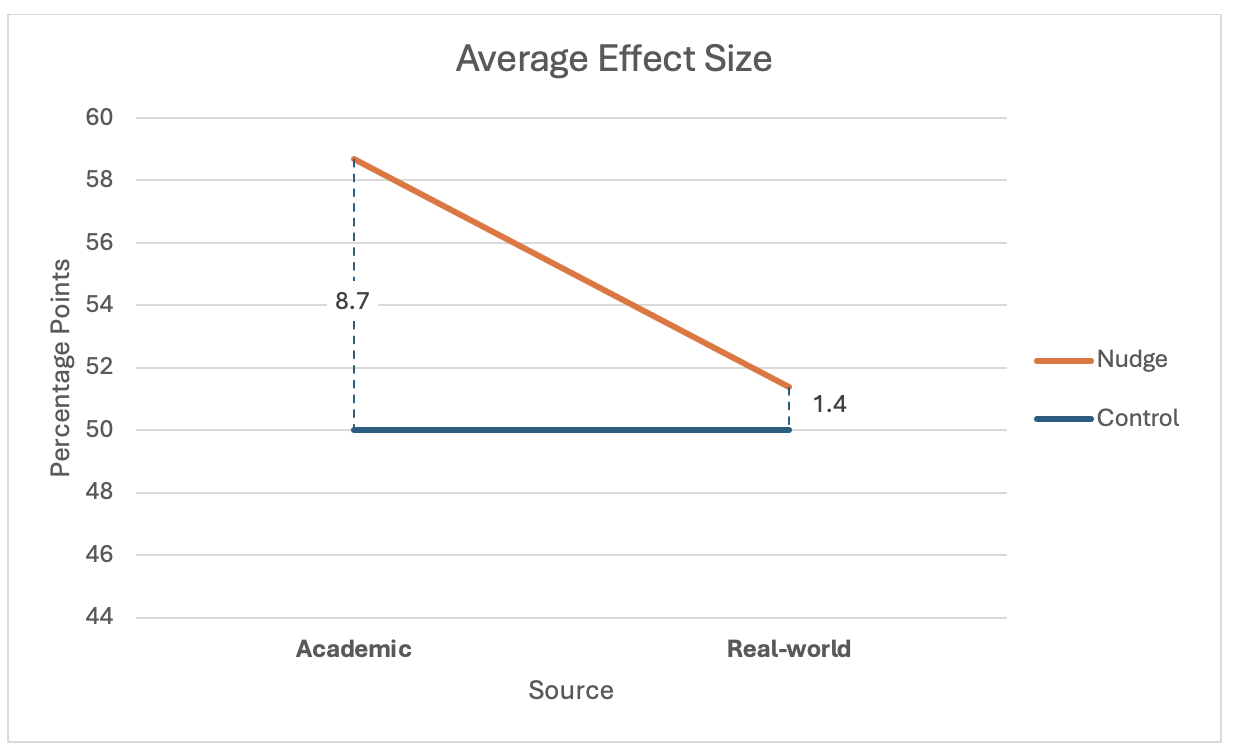
Figure 2. The average uptake (stated as percentage points) for nudge interventions published in the academic literature compared to real-world nudge interventions sponsored by governmental “nudge units.”
While 8.7% may sound small, having 8.7% of your employees reporting phishing threats or not clicking on them represents a huge reduction in risk.
Question 3: Assuming nudges are cheap and easy to ignore (by definition), what is the alternative?
Nudges may not change behavior for two reasons. First, nudges may not work as intended because the focus is on the individual, whereas the change needs to happen at the system level. This is related to the “defense-in-depth” strategy. If a user clicks on a link in their email, then that means the email made it through the secure email gateway. If malware is installed because of the link, then that means the antivirus software did not detect the malicious payload, and the system’s permissions are set to allow for their computer to run arbitrary code.
Second, since nudges aim to influence the choice a user is about to make, they are generally presented either to prompt an action or when the user is about to make a choice, such as when they are trying to attach a file to an email. Suppose your organization prefers users to share files via a central site rather than email. Asking the user to take a course on data sharing every time they try to share a file is not going to be an effective use of their time.
If, despite the nudge, the user still makes an insecure decision, then follow-up training may help address either knowledge or belief gaps that could be causing them to make an insecure decision.
What can be done instead? Another way to look at nudging is that it is one tool in the behavioral change toolbox. Relying on nudges to the exclusion of all other interventions is bound to fail. Instead, it should be used judiciously as part of a broader cybersecurity educational program because then the messages contained within the nudges can cross-reference and reinforce the training materials (see Figure 3).
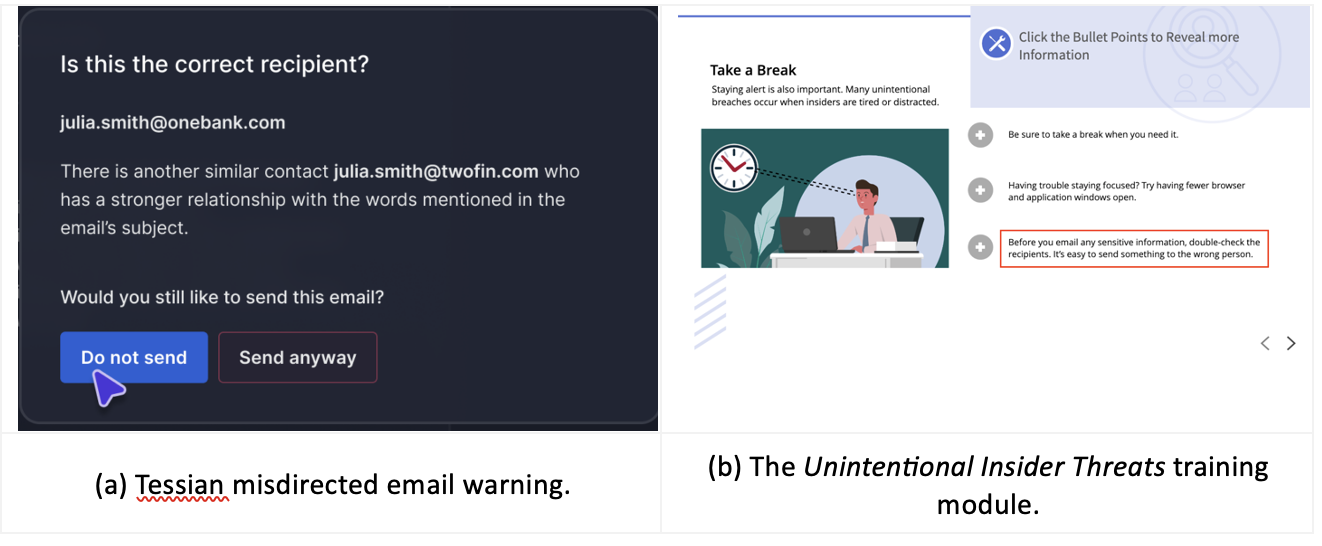
Figure 3. An opportunity to connect (a) a pop-up warning message to (b) the contents of a training module.
It is useful to think of cybersecurity as a marketing campaign. To change behavior, you need to reach your end users through as many channels as possible. Nudges can be one of those channels. But the secret is to build off the learning content, so that it is reinforced through “spaced practice” and contextualized. As we all know, it is much easier to learn something new when you see the immediate applicability of the lesson.
Final thoughts: success is achieved through measurement and iteration
The last point that needs to be made is the importance of measurement and iteration. After the publication of Nudge, Cass Sunstein explicitly stated in a paper titled Nudges That Fail that a nudge is a hypothesis, which means we must measure the impact of the nudge and adjust accordingly. There are many nuances to human behavior, and we might not always get it right on the first attempt. Therefore, it is critical that we measure and adjust our strategies and messaging.
Nudging alone will not solve the problems that we face in cybersecurity. However, they can be a strategic component of an overall behavioral and educational solution.
Learn more about the high-quality, threat-driven security awareness training content available in the Proofpoint Security Awareness platform.

