Key takeaways
- According to Proofpoint findings, 78% of Microsoft 365 tenants were targeted at least once by an account takeover attempt utilizing a distinct HTTP client.
- Most HTTP-based cloud attacks utilize brute force methods, resulting in low success rates.
- Proofpoint researchers found that a recent campaign using the unique HTTP client Axios had an especially high success rate, compromising 43% of targeted user accounts.
- Proofpoint researchers identified a brute force campaign, distinguished by its high velocity and distributed access attempts, utilizing the Node Fetch client.
Overview
HTTP client tools are software applications or libraries used to send HTTP requests and receive HTTP responses from web servers. These tools allow users to craft requests with various HTTP methods (e.g., GET, POST, PUT, DELETE), customize headers, include payloads, and inspect server responses.
Proofpoint has observed a rising trend of attackers repurposing legitimate HTTP client tools, such as those emulating XMLHttpRequest and Node.js HTTP requests, to compromise Microsoft 365 environments. Originally sourced from public repositories like GitHub, these tools are increasingly used in attacks like Adversary-in-the-Middle (AitM) and brute force techniques, leading to numerous account takeover (ATO) incidents.
This blog explores the historical and current use of HTTP clients in ATO attack chains, shedding light on the evolving tactics of threat actors.
Historical trends
In February 2018, Proofpoint researchers identified a widespread malicious campaign targeting thousands of organizations worldwide, leveraging an uncommon OkHttp client version (‘okhttp/3.2.0’) to target Microsoft 365 environments. Using dedicated hosting services in Canada and the U.S., the attacker consistently launched unauthorized access attempts for nearly four years, focusing on high-value targets such as C-level executives and privileged users.
According to Proofpoint research, much of the targeted users’ data seems to have come from breaches like the 2016 LinkedIn credentials leak, enabling attackers to launch sizeable attacks against thousands of organizations. In addition, further analysis revealed that these OkHttp-based activities were just the initial stage of a sophisticated attack chain.
It turned out that threat actors employed user enumeration methods to identify valid email addresses before executing other threat vectors, such as spear phishing and password spraying. This technique generated high volumes of login attempts, mostly aimed at nonexistent accounts. By 2021, the campaign peaked with tens of thousands of attacks monthly but significantly declined by late 2021, signaling a shift in attackers’ tactics.
Current trends
Since 2018, HTTP clients remain widely used in ATO attacks. According to Proofpoint threat researchers, early 2024 saw OkHttp variants dominate, but by March 2024, a broader range of HTTP clients gained traction. Moreover, in terms of scale, the second half of 2024 saw 78% of organizations experience at least one ATO attempt involving an HTTP client, a 7% increase from the prior six months.
During this time, newly observed HTTP clients, like 'python-request,' were being integrated into brute force attack chains, significantly increasing threat volume and diversity. In May 2024, these attacks peaked, leveraging millions of hijacked residential IPs to target cloud accounts.
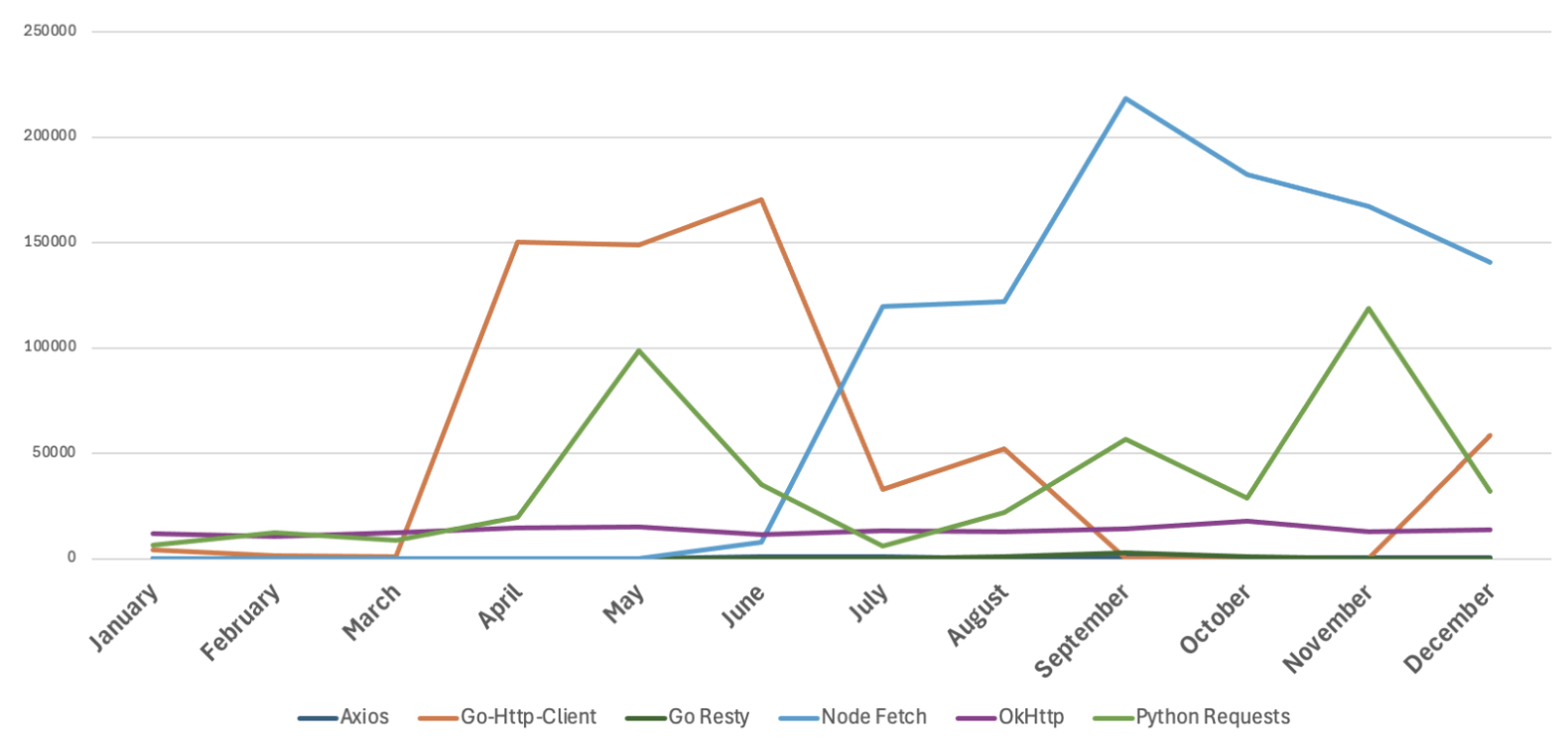
ATO attacks leveraging HTTP clients by volume of affected user-accounts (JAN – DEC 2024).
In fact, most HTTP-based ATO attacks are brute force attempts with low success rates. However, Proofpoint investigated more effective threats, such as a recent campaign using the Axios HTTP client, which combines precision targeting with Adversary-in-the-Middle (AitM) techniques. This approach achieved a monthly average success rate of 38% when trying to compromise user accounts, by effectively overcoming modern security measures like multifactor authentication (MFA).
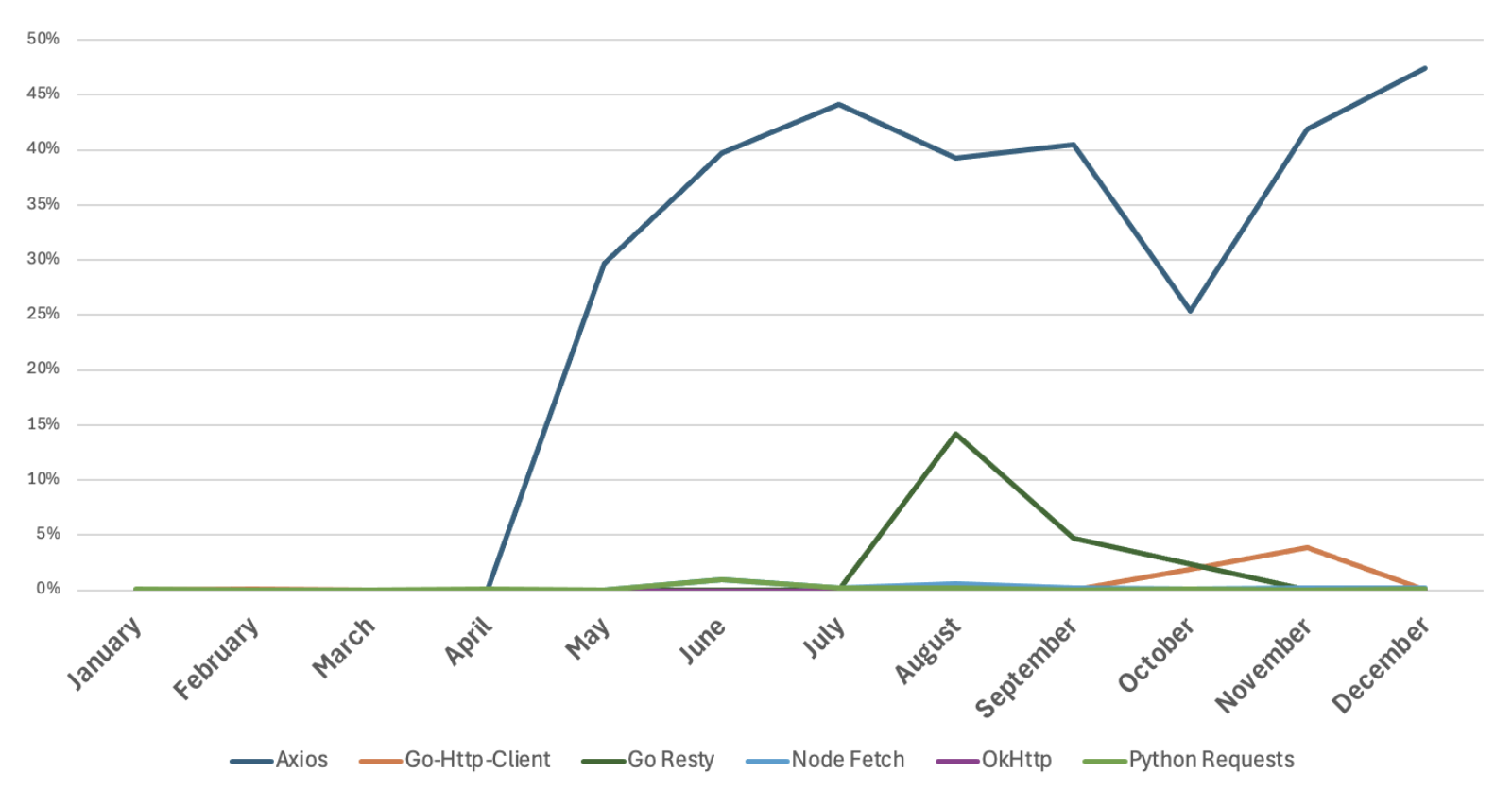
Efficacy of ATO attacks leveraging HTTP clients by volume of impacted user-accounts (JAN-DEC 2024).
Hybrid campaign using Axios clients
Why Axios?
Axios, a promise-based HTTP client for Node.js and browsers, supports traffic interception, transformation, and cancellation. When paired with AiTM platforms like Evilginx, it enables credential, MFA token, and session token theft for unauthorized account access.
Attack chain – key steps
- Credential theft. Email-borne phishing threats facilitate Microsoft 365 credentials theft, leveraging reverse proxy toolkits capable of stealing MFA tokens.
- Account takeover. Stolen credentials, including intercepted MFA tokens, are used to compromise accounts using the Axios HTTP client tool, targeting specific Microsoft Office sign-in apps.
- Post-compromise.
- Mailbox rules. Newly created mailbox rules help the threat actor obfuscates unauthorized activities, delete evidence, exfiltrate data, and facilitate fraud.
- Data exfiltration. The threat actor steals sensitive data, modifies access permissions and creates secure sharing links for future unauthorized access.
- OAuth application creation. In some cases, the attacker registers new OAuth applications with excessive permission scopes (including full mail access and offline access), establishing persistent access sensitive resources within the hijacked environment.
Malicious apps created as part of this attack chain have shown potential connections and similarities to cloud malware assets used by other campaigns, such as VodkaNimbus.
Attack pattern and infrastructure
Our analysis of the activity over time reveals a clear operational model, by which the threat actor primarily operates on weekdays, aligning with typical business hours. Daily attack volumes average 20 targeted users, peaking at 175 on 04 June 2024, before gradually declining.
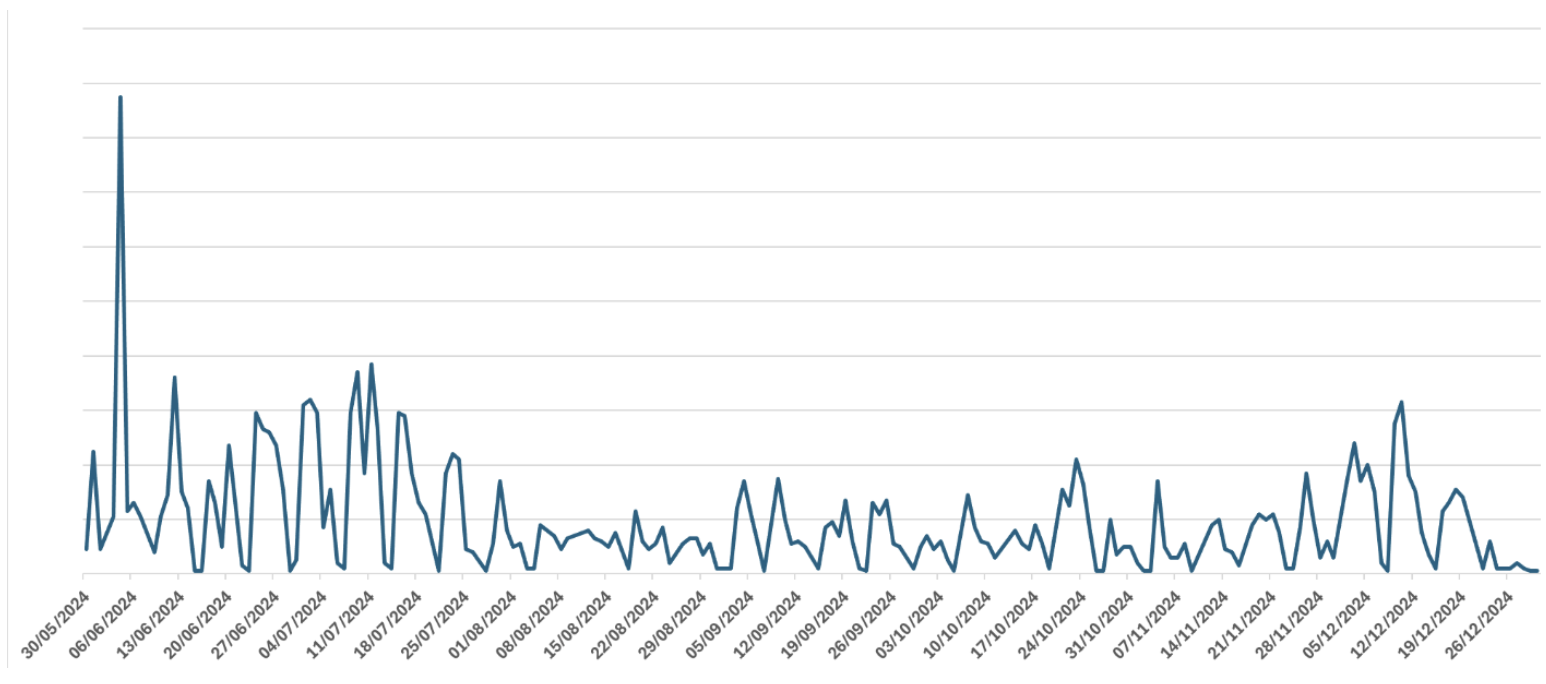
Volume of cloud attacks targeting user accounts using Axios clients (JUN – DEC 2024).
In terms of operational infrastructure, the campaign was first observed using several US-based proxy services. However, in recent months, Proofpoint researchers have observed a shift toward using only Russia-based proxies (see Observables).
Targeted roles and overall impact
So far, this campaign has mainly targeted executives, financial officers, account managers, and operational staff across various industries like transportation, construction, finance, IT, and healthcare. High-value targets with access to sensitive data or financial resources were clearly prioritized. In total, from June until the end of November, it has successfully impacted over 51% of targeted organizations, compromising 43% of targeted user accounts.
Password spraying campaign using node fetch clients
Why node fetch?
Node-fetch simplifies transitioning from native HTTP to the Fetch API in Node.js, avoiding the need for XMLHttpRequests. While it lacks Axios’s interception capabilities, its simplicity allows for easy automation on a large scale.
Attack chain and operational patterns
Node-fetch is primarily used for brute force attacks, particularly password spraying, with threat actors leveraging extensive operational infrastructure and frequently rotating IP addresses to evade detection.
According to Proofpoint findings, since 09 June 2024, this ongoing attack has logged over 13 million login attempts, averaging over 66,000 malicious attempts every single day.
Attack volumes rose from June to December, fluctuating by day, with Fridays and Sundays seeing increased activity and Wednesdays the lowest. On average, each targeted account faced roughly 1.8 unauthorized login attempts, indicating a rapid shift between targets.
However, despite its massive scale, this ATO campaign has a low success rate, impacting only 2% of targeted organizations.
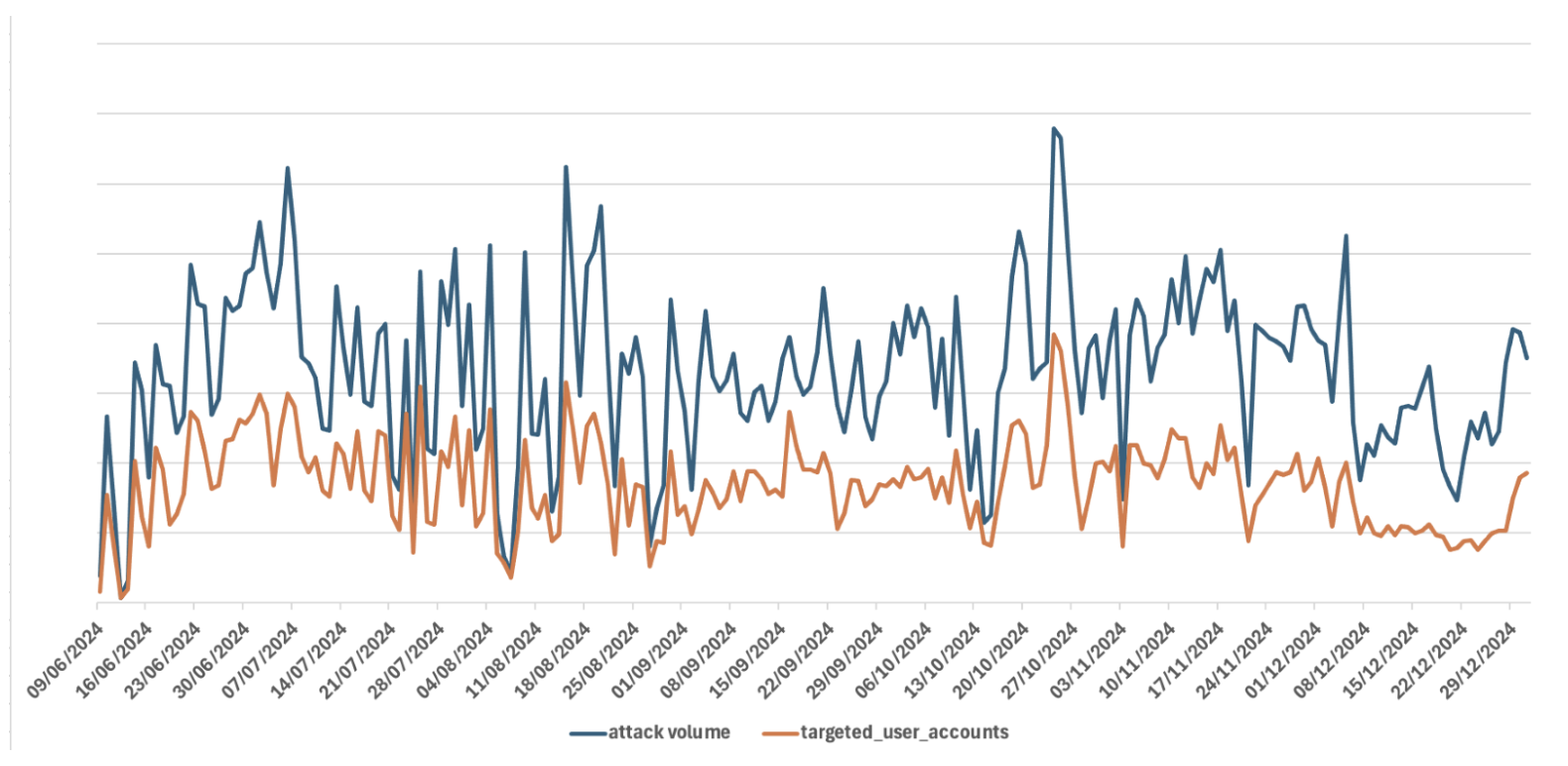
Attack volume and targeted user accounts using Node Fetch (JUN-DEC 2024).
Velocity and overall impact
To date, Proofpoint has identified over 178,000 targeted user accounts across 3,000+ organizations, mainly in the Education sector. Attackers have been observed going after student user-accounts, which are often less protected and can be leveraged for large-scale spam campaigns or sold in bulk to other cybercriminals.
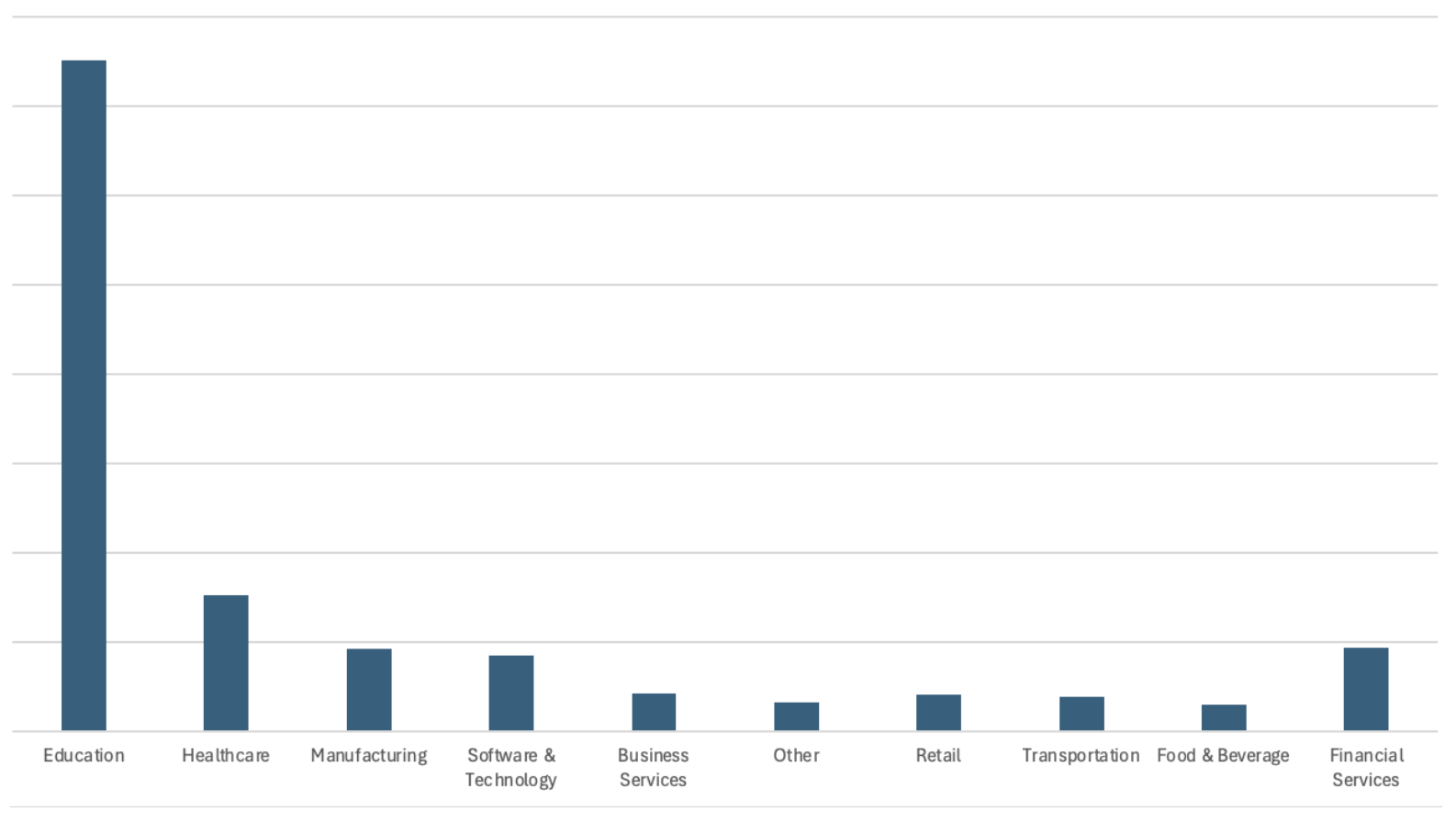
Volume of Node Fetch based account takeover attacks, by targeted vertical (JUN-DEC 2024).
From Node.js to go: evolution of attack tools
In August 2024, Proofpoint threat researchers observed a change in the landscape, with the appearance of a new wave of brute force attacks, this time using Go Resty, a Go HTTP/REST client. This shift was quickly linked to the ongoing campaign using Node Fetch, as both activity clusters utilized the same operational infrastructure and targeted the same organizations simultaneously. Those smaller scale Go Resty based attacks fluctuated in volume, typically peaking on weekdays.
Potential explanations for the adoption of this relatively new client include a slightly higher success rate, minor technical advantages, or an evasion strategy based on variation. However, since October, Go Resty based attacks have ceased, while Node Fetch based attacks persist.
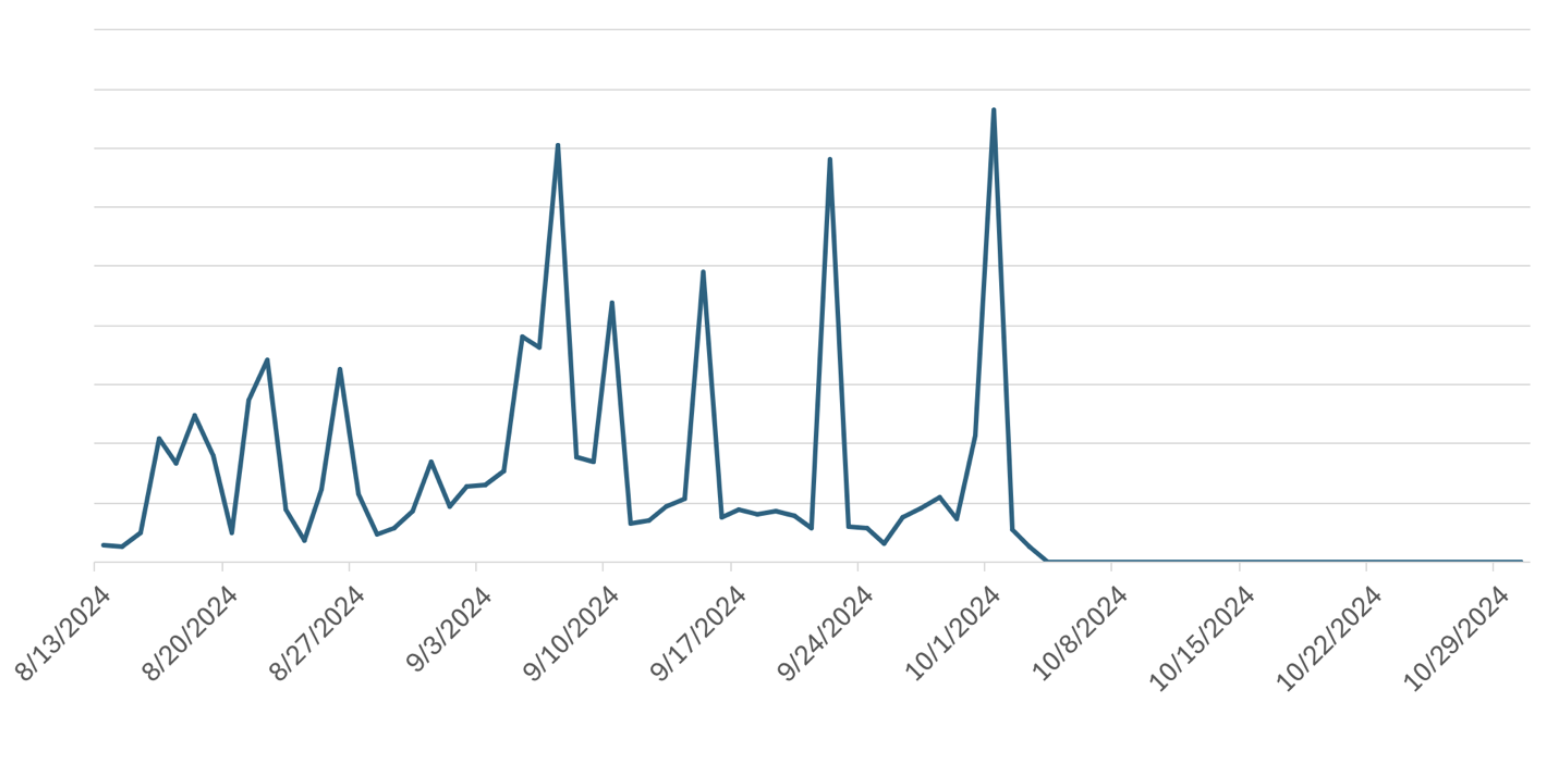
Volume of account takeover attacks using Go Resty (AUG-OCT 2024).
What can we expect next?
Threat actors' tools for ATO attacks have greatly evolved, with various HTTP client tools used for exploiting APIs and making HTTP requests. These tools offer distinct advantages, making attacks more efficient.
Given this trend, attackers are likely to continue switching between HTTP client tools, adapting strategies to leverage new technologies and evade detection, reflecting a broader pattern of constant evolution to enhance their effectiveness and minimize exposure.
Observables
HTTP clients
Proofpoint recommends combining the following observed user-agents with additional confidence boosters, indicators and threat intel to inform accurate detections.
|
Indicator |
Type |
Description |
|
okhttp/3.2.0 |
User agent |
HTTP client version used for user enumeration attacks |
|
okhttp/3.14.7 |
User agent |
HTTP client version used for user enumeration attacks |
|
okhttp/3.14.9 |
User agent |
HTTP client version used for user enumeration attacks |
|
okhttp/4.11.0 |
User agent |
HTTP client version used for user enumeration attacks |
|
okhttp/4.12.0 |
User agent |
HTTP client version used for user enumeration attacks |
|
okhttp/4.9.3 |
User agent |
HTTP client version used for user enumeration attacks |
|
Go-http-client/1.1 |
User agent |
HTTP client used for variants of brute force attacks |
|
Go-http-client/2.0 |
User agent |
HTTP client used for variants of brute force attacks |
|
python-requests/2.20.0 |
User agent |
HTTP client used for variants of brute force attacks |
|
python-requests/2.22.0 |
User agent |
HTTP client used for variants of brute force attacks |
|
python-requests/2.25.1 |
User agent |
HTTP client used for variants of brute force attacks |
|
python-requests/2.26.0 |
User agent |
HTTP client used for variants of brute force attacks |
|
python-requests/2.27.1 |
User agent |
HTTP client used for variants of brute force attacks |
|
python-requests/2.28.0 |
User agent |
HTTP client used for variants of brute force attacks |
|
python-requests/2.28.1 |
User agent |
HTTP client used for variants of brute force attacks |
|
python-requests/2.30.0 |
User agent |
HTTP client used for variants of brute force attacks |
|
python-requests/2.31.0 |
User agent |
HTTP client used for variants of brute force attacks |
|
python-requests/2.32.2 |
User agent |
HTTP client used for variants of brute force attacks |
|
python-requests/2.32.3 |
User agent |
HTTP client used for variants of brute force attacks |
|
axios/0.21.1 |
User agent |
HTTP client version used for AiTM attacks |
|
axios/0.21.4 |
User agent |
HTTP client version used for AiTM attacks |
|
axios/1.4.0 |
User agent |
HTTP client version used for AiTM attacks |
|
axios/1.6.5 |
User agent |
HTTP client version used for AiTM attacks |
|
axios/1.6.8 |
User agent |
HTTP client version used for AiTM attacks |
|
axios/1.7.2 |
User agent |
HTTP client version used for AiTM attacks |
|
axios/1.7.3 |
User agent |
HTTP client version used for AiTM attacks |
|
axios/1.7.4 |
User agent |
HTTP client version used for AiTM attacks |
|
axios/1.7.5 |
User agent |
HTTP client version used for AiTM attacks |
|
node-fetch |
User agent |
HTTP client used for password spraying attacks |
|
node-fetch/1.0 (+https://github.com/bitinn/node-fetch) |
User agent |
HTTP client used for password spraying attacks |
|
go-resty/2.14.0 (https://github.com/go-resty/resty) |
User agent |
HTTP client used for password spraying attacks |
Additional indicators of compromise
For effective detection of unauthorized activities, it is recommended to combine the following observables with specific user agents from the HTTP Clients list. This approach enhances the ability to surface potential threats with high fidelity.
|
Indicator |
Type |
Description |
|
Namecheap Inc. |
Data Center Hosting Service |
Source infrastructure used in Axios-based attacks |
|
LLC Internet Tehnologii |
Data Center Hosting Service |
Source infrastructure used in Axios-based attacks |
|
LLC Baxet |
Data Center Hosting Service |
Source infrastructure used in Axios-based attacks |
|
Global Internet Solutions LLC |
Data Center Hosting Service |
Source infrastructure used in Axios-based attacks |
|
MT6 LLC |
Data Center Hosting Service |
Source infrastructure used in Axios-based attacks |
|
Hurricane Electric LLC |
Data Center Hosting Service |
Source infrastructure used in Node Fetch-based attacks |
|
Black Mesa Corporation |
Data Center Hosting Service |
Source infrastructure used in Node Fetch-based attacks |
|
M247 Europe SRL |
Data Center Hosting Service |
Source infrastructure used in Node Fetch-based attacks |
|
https://nc.667af91ca5068[.]digital/auth |
URL |
Reply URL linked to malicious applications registered post account compromise |
|
https://c.65a9b4549d87a[.]digital/auth |
URL |
Reply URL linked to malicious applications registered post account compromise |
|
https://www.https-65a916cbc80e5[.]org/auth |
URL |
Reply URL linked to malicious applications registered post account compromise |

