Overview
The third quarter of 2018 saw the ransomware that emerged in Q2 largely disappear, while banking Trojans, downloaders, and information stealers again filled the void. At the same time, email fraud actors returned to proven methods, social media support fraud continued its steady growth, and social engineering schemes remained pervasive web-based threats.
Among the key takeways from Proofpoint’s Q3 Threat Report:
Email remains by far the most common vector for malware attacks and phishing, while the frequency of email fraud continues to rise rapidly. As in the previous two quarters of 2018, however, the email space was marked by considerably more diversity than in years past, when single families of malware like ransomware or banking Trojans made up the majority of malicious payloads. As shown in Figure 1, bankers, downloaders, and information stealers comprised 94% of all malware payloads, but even remote access Trojans (RATs) appeared in 4% of all campaigns.
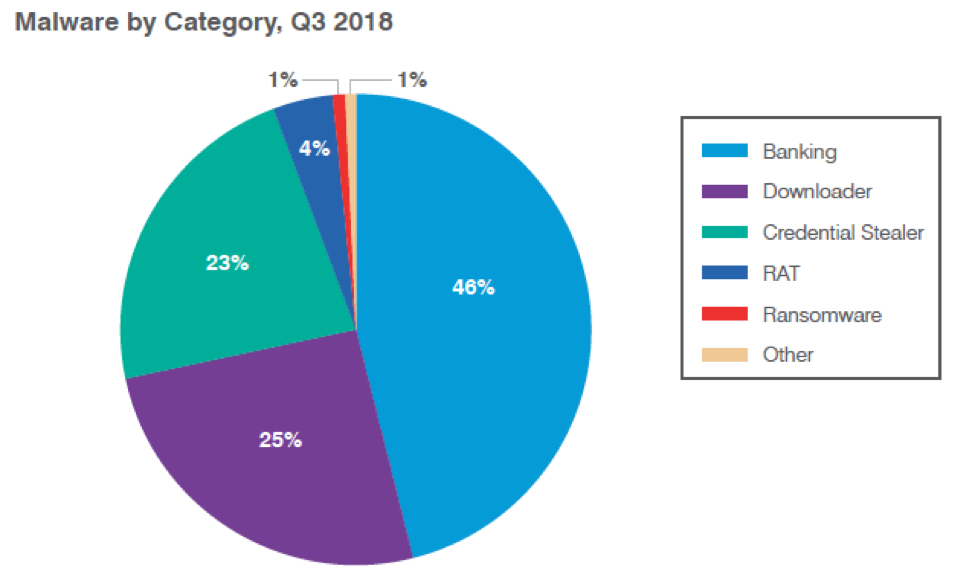
Figure 1: Relative distribution of malicious payloads, Q3 2018
Figure 2 shows the steady, frequent campaigns associated with downloaders and information stealers. Downloaders in particular saw both growth in associated message volumes and increasing diversity as several previously undocumented loaders appeared on the market.
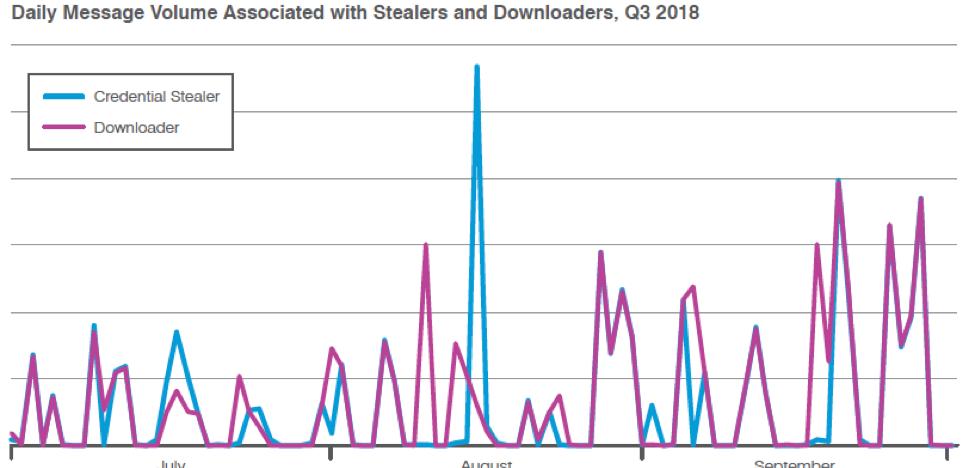
Figure 2: Indexed relative volume of malicious messages bearing downloaders or information stealers as their primary payloads, Q3 2018
Email fraud also continued to grow as a business problem, with targeted organizations receiving an average of over 36 such attacks in Q3. This represents a 77% increase over Q3 2017. While a few industries like pharmaceuticals and construction saw substantial increases in apparent targeting, no industries were immune and organizational size continued to have no impact on targeting.
Exploit kits and web-based attacks
Exploit kit (EK) traffic remained steady at levels far below their 2016 peak, with most web-based attacks now involving social engineering schemes. Social engineering detections continued to increase in Q3, growing an additional 233% quarter over quarter
Cryptojacking also remained a common threat -- Coinhive-related activity exploded at the end of Q2 2018, with the sheer volume and speed of adoption, suggesting that much of this activity was not initiated by legitimate website operators.
Social media
Social media channels remain key vectors for fraud and theft. While the platforms themselves continue to develop automated protections, social media support fraud remains a key challenge for consumers and the brands with which they interact. Social media support fraud increased by 486% vs. Q3 2017.
Proofpoint Recommendations
The Q3 Threat Report provides insight into the shifting threat landscape that can inform your cybersecurity strategy. Here are our top recommendations for how you can protect your company and brand in the coming months:
Assume users will click. Social engineering is increasingly the most popular way to launch email attacks, and criminals continue to find new ways to exploit the human factor. Leverage a solution that identifies and quarantines both inbound email threats targeting employees and outbound threats targeting customers before they reach the inbox.
Build a robust email fraud defense. Highly targeted, low-volume email fraud attacks often have no payload at all and are thus difficult to detect. Preventing email fraud requires a multilayered solution that includes email authentication and domain discovery, as well as dynamic classification that can analyze the content and context of emails, stopping display-name and lookalike-domain spoofing at the email gateway.
Protect your brand reputation and customers. Fight attacks targeting your customers over social media, email, and mobile—especially fraudulent accounts that piggyback on your brand. Look for a comprehensive social media security solution that scans all social networks and reports fraudulent activity.
For more information, download the complete Q3 2018 Threat Report.

