Overview
Ransomware has exploded in the last year, becoming the malware of choice for many threat actors because of its easy monetization and ease of distribution, whether via massive email campaigns or through a variety of exploit kits. Proofpoint research suggests that the number of ransomware variants has grown tenfold since December 2015. While most such malware encrypts a victim's files and demands that a ransom be paid in Bitcoins to decrypt them, Proofpoint researchers recently discovered a new variant that scrapes Skype and social media profiles for personal information while it scans files and torrents for potentially sensitive information. Instead of encrypting files, it threatens victims with fake legal proceedings if they fail to pay the ransom.
The Discovery
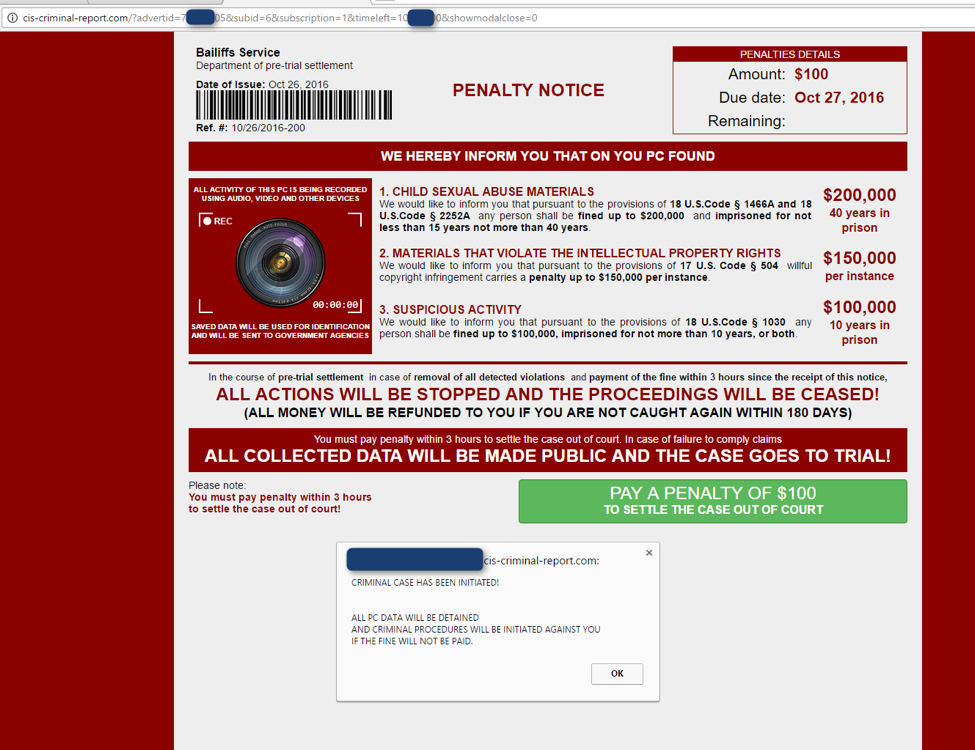
In the last week of October, our colleague at FoxIT InTELL, Frank Ruiz, pointed us to a new browser locker variant. Unlike traditional encrypting ransomware like Locky, browser lockers are full-screen web apps that prevent users from accessing their operating systems or closing the browser window. In this case, the browser locker displays a fake "Penalty Notice" offering to let the victim "settle [their] case out of court," avoiding the threat of legal actions and much larger penalties for objectionable content and suspicious activity purportedly discovered on the victim's computer (Figure 1).
Figure 1: Browser locker “Penalty Notice”
This browser locker was spread in United States via malvertising traffic (primarily fed by the Plugrush and Traffic Shop traffic exchanges on adult websites) aimed at Internet Explorer on Windows and Safari on OS X.
This type of threat was endemic between 2012 and 2014 and was frequently seen spreading concurrently via exploit kit with “Police Locker” malware [1]. Since then, the same kind of traffic has largely focused on exploit kit distribution of crypto ransomware and other malware as well as Tech Support scams in which victims are told to contact a fake tech support service to remove malware from their PCs, usually for a fee to be paid by credit card.
However, in the first week of November, we discovered an unusual malware variant that we believe is tied to the “Penalty Notice” browlock shown in Figure 1 based on visual and thematic similarities and distribution mechanisms. Note, however, that while the browser locker functions cross-platform, the related malware, dubbed Ransoc, is a Windows binary.
Ransoc
In a sandbox environment, we observed this new malware perform an IP check and send all of its traffic through the Tor network. Further examination revealed that the malware scanned local media filenames for strings associated with child pornography.
We also noticed that it was running several routines interacting with Skype, LinkedIn, and Facebook profiles (Figure 2).
Figure 2: Code examining Skype and social media profiles
The code also examined folders from Torrent software (Figure 3).
Figure 3: Code examining Torrent folder contents
To determine the nature of the malware's interaction with these services, we ran it manually in our sandbox. We logged into fake social network accounts then closed the browser and launched the Skype desktop application. As suspected, after running the malware, we saw it connecting to the fake Facebook and LinkedIn profiles we created (Figure 4).
Figure 4: Ransoc capturing photos from social media account profiles
The malware, which we call Ransoc because of its connections to social media, then displayed a Penalty Notice that was visually and functionally similar to the browser locker shown in Figure 1. The new Penalty Notice is shown in Figure 5. It appears that this penalty notice only appears if the malware finds potential evidence of child pornography or media files downloaded via Torrents and customizes the penalty notice based on what it finds. If we manually changed file names to match specific strings, we were able to trigger the penalty notice.
Figure 5: New penalty notice with social media profile information and a threat stating that “All Collected Data will be made public and the case goes to trial!”
The ransom message displays accurate personal data captured from Skype and social media profiles, including profile photos. It threatens to expose the collected "evidence" to the public, with legitimate social profile information being used as a social engineering lure to convince victims that sensitive information may actually be at risk of exposure. Unlike most ransomware variants, the target here is the victim's reputation rather than their files. Ransoc also includes code that may allow it to access a victim's webcam, although we did not verify this functionality.
The ransom message is actually a full-screen window that functions much like the browser locker application shown in Figure 1. However, Ransoc checks every 100ms for regedit, msconfig, and taskmgr, killing the processes before victims have a chance to remove or disable the malware. Ransoc only uses a registry autorun key to persist, though, so rebooting in Safe Mode should allow users to remove the malware. The sample we examined had an HKCU\Software\Microsoft\Windows\CurrentVersion\Run\JavaErrorHandler registry key with a value of a shortcut pathname ending in 'JavaErrorHandler.lnk', although future versions may use a different key.
The payment system (Figure 6) is also unusual.
Figure 6: Ransoc payment page
Credit card payment is almost unheard of in ransomware schemes. While it removes the hassle and confusion for many victims associated with Bitcoin processing, it also potentially allows law enforcement to trace activity back to the cybercriminal more easily.
This fairly bold approach to ransom payments suggests the threat actors are quite confident that people paying the ransom have enough to hide that they will probably not seek support from law enforcement. In fact, while Ransoc may seem to be motivated by vigilantism against genuine criminals, the motives are likely less-than-altruistic, as the attackers target users who will be unlikely to resist or inform the authorities and thus increase the likelihood of payment. This theory is further bolstered by the fact that most victims encounter this malware via malvertising on adult websites and the penalty notice only appears when Ransoc encounters potential evidence of illegally downloaded media (via BitTorrent) and certain types of pornography. To encourage payment, the ransom note also claims that money will be sent back if the victim is not caught again in the 180 days.
Conclusion
Although exploit kit activity has dropped off precipitously over the past year, malvertising activity remains strong, with threat actors exploring new ways to infect victims and extort money through this vector. By incorporating data from social media accounts and Skype profiles Ransoc creates a coercive, socially engineered ransom note to convince its targets that they are in danger of prosecution for their browsing habits and the contents of their hard drives. With bold approaches to collecting payments, the threat actors appear confident in their targeting, introducing new levels of sophistication to ransomware distribution and monetization.
Indicators of Compromise (IOCs)
|
Date |
Domain |
IP |
Comment |
|
2016-10-27 |
cis-criminal-report[.]com |
5.45.86.171 |
Browlock for IE Windows |
|
2016-10-27 |
criminal-report[.]in |
5.45.86.171 |
Browlock for Safari OSX |
|
2016-11-03 |
violation-report[.]in |
5.45.86.171 |
Browlock for IE and Safari |
|
2016-11-02 |
latexfetishsex[.]com |
78.47.134.204 |
Intermediate Redirector/TDS |
|
2016-11-03 |
italy-girls[.]mobi |
5.9.86.131 |
Intermediate Redirector/TDS |
|
2016-11-10 |
N/A |
5.45.86.148 |
IP found in the Ransoc |
|
sha256 |
Comment |
|
fee53dc4e165b2aa45c3e7bd100b49c367aa8b7f81757617114ff50a584a1566 |
Ransoc PenaltyNotice |
References
[1] http://malware.dontneedcoffee.com/2014/05/police-locker-available-for-your.htm