What happened
As the holiday season ramps up globally, threat actors have begun to take advantage of people’s desires for deals, jobs, and end of year bonuses. Proofpoint researchers have observed an increase in timely, themed content delivering malware, fraud, and credential phishing campaigns.
Fly for the holidays
For example, on 18 November, researchers identified a “Winter Holiday Promotion” campaign purporting to be from an airline. The messages were sent in both Spanish and English and contained compressed executables that led to the installation of Remcos RAT.
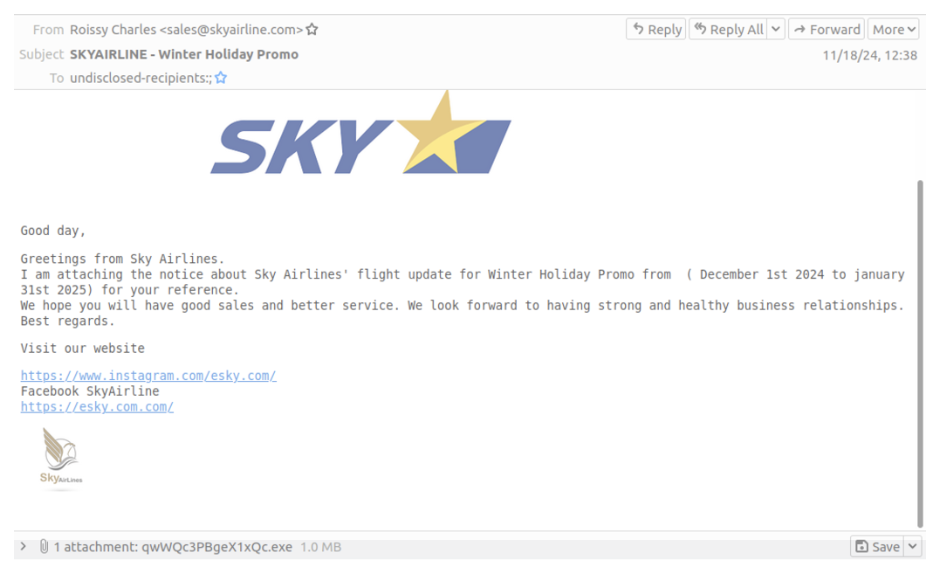
“Holiday promo” themed lure delivering Remcos RAT.
The campaign was low volume and included less than 100 messages.
Merry phishmas
The majority of holiday themed lures Proofpoint has observed are credential phishing campaigns.
In another campaign that began on 9 December, threat actors purported to be human resources or payroll departments sending information about end of year bonuses and “Xmas Employee Payroll.”
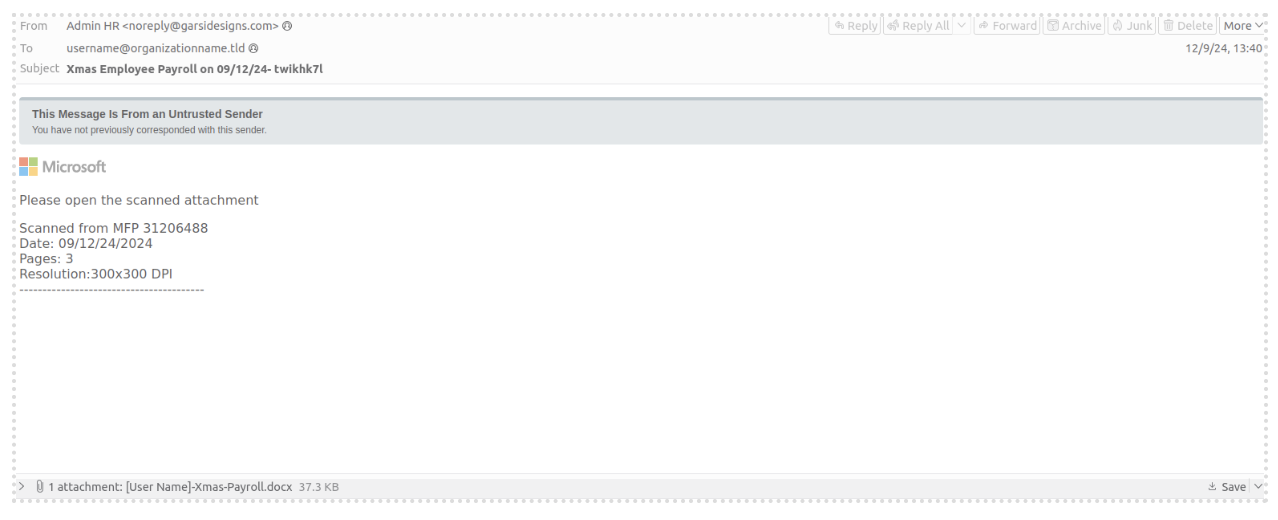
Lure impersonating corporate HR to send “Xmas” themed credential phishing.
Messages were customized with the logo of the target organization or a Microsoft logo. These messages contained Open Office XML (OOXML) attachments, which also included the target organization logo, and included a QRCode. If scanned, the QR code URL directed users to a counterfeit Microsoft authentication page.

Example phishing document including QR code.
The credential phishing page presented the user's organization AAD (Azure Active Directory) Branding once email was provided and it was designed to harvest user credentials, 2FA token, and to retrieve an associated session cookie. This is achieved through the Adversary-in-the-Middle (AiTM) technique, utilizing synchronous relay capabilities provided by the Tycoon Phishing-as-a-Service (PhaaS) platform.
The Open Office XML (OOXML) attachments are manipulated "brooxml" files. These "brooxml" files are specially crafted by threat actors prepending data at the start of the file which is not allowed in the OOXML standard, but which Microsoft Office can automatically "fix" by removing. This is a technique Proofpoint has seen abused by threat actors since August 2024 to attempt to bypass sandbox detection.
Proofpoint has observed numerous campaigns using holiday and bonus themes to deliver Tycoon credential phishing URLs.
SakaiPages bonus and holiday lures
On 12 December 2024, researchers identified an AiTM credential phishing campaign using a variety of end of year and holiday themes.
Messages purported to come from the target’s HR team, and included subjects related to payroll and bonuses.
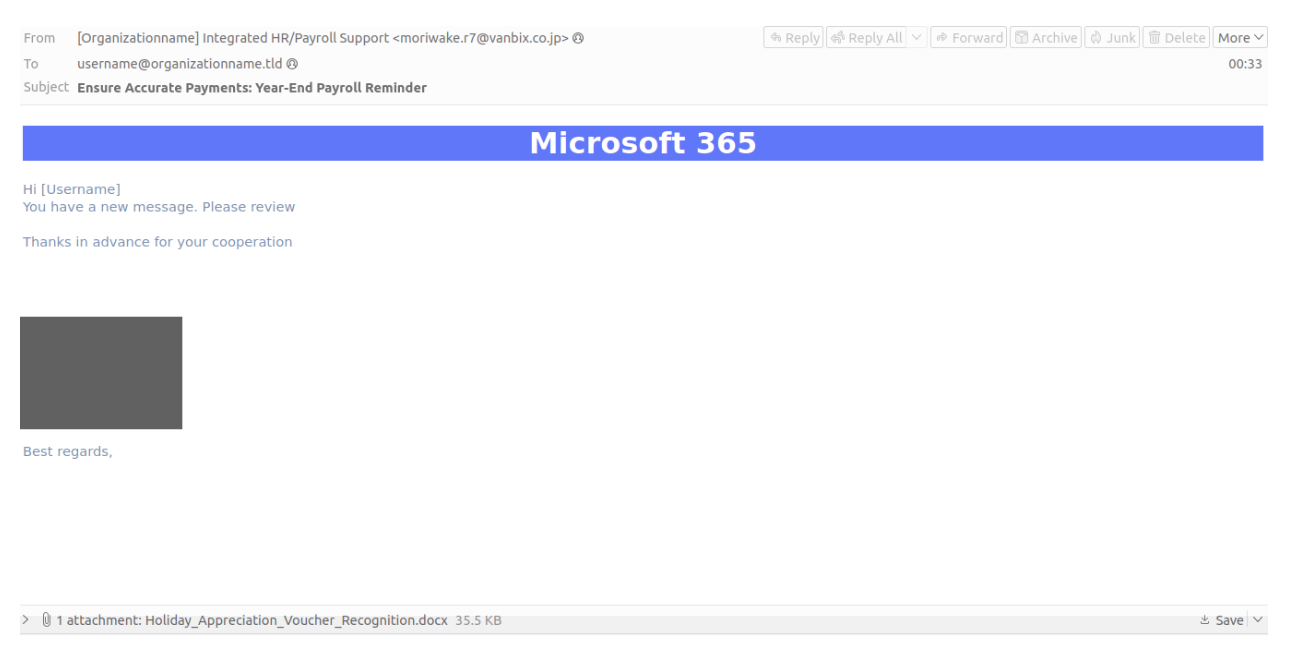
SakaiPages credential phishing lure.
The messages contained customized Microsoft Word attachments containing a QR code that directed users to a fake Microsoft authentication page. Attached document filenames included:
annual_loyalty_compensation_award.docx
december_achievement_compensation_award.docx
december_holiday_appreciation_voucher.docx
When a user provided an email to the credential phishing website, the page masqueraded as the user's organization AAD branded login. The credential phishing page harvested user credentials, 2FA tokens, and retrieved session cookies via the SakaiPages phishing Kit.
Holiday job offers actually scams
On 10 December 2024, Proofpoint identified an employment fraud campaign that impersonated the nonprofit organization Project HOPE attempting to recruit workers as “Community Liaison Agents.” In many emails, the threat actor stressed the idea that it would be "extra income" for the holiday season. Emails were sent from likely compromised senders, but included a contact email address in the body text: [various names]@jobs-projecthope[.]org.
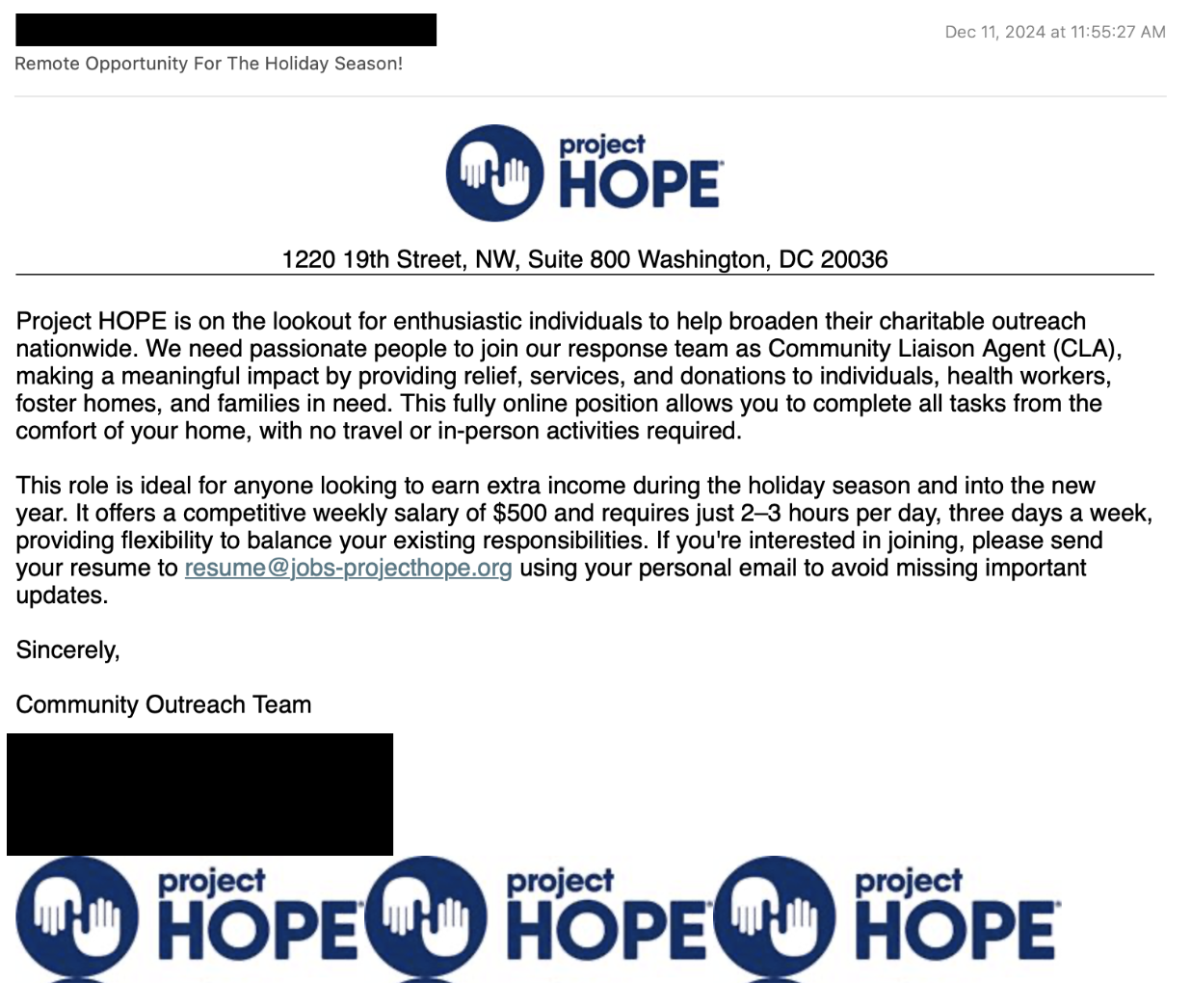
Lure impersonating Project Hope advertising holiday season jobs.
An employment fraud threat occurs when a threat actor attempts to recruit someone under the premise of a legitimate job offer. Threat actors will craft fraudulent job offers hoping to steal money via advance fee fraud (AFF) or cryptocurrency, attempt to obtain personally identifiable information (PII), or to recruit an individual to unknowingly comply with illegal activities such as money laundering. Threat actors will typically pose as recruiters or employers and try to entice victims with a variety of opportunities.
In this case, the actor is using common employment fraud tactics and paired them with a timely lure for the holiday season. The threat actor tries to entice the recipient to contact them for additional information about a job, with the ultimate objective of the campaign to likely to conduct AFF. This campaign largely targeted universities, which tend to be frequent targets of employment scams.
Why it matters
This activity is consistent with previous holiday seasons where threat actors begin to leverage festive and end of year themed threats.
In the holiday season, threat actors are meeting people where they are: digitally browsing for gifts or deals on many different websites across the internet. Many people are also expecting holiday bonuses or work-related announcements for their financial benefit, which is a theme threat actors will take advantage of. The holiday season is also a good time to exploit people via social engineering. They’re often in a rush, hoping to snag a deal before it expires, accept their bonuses, work a seasonal job, or already willing to spend money or share their information to get the perfect gift or enticing benefit. Threat actors take advantage of this and tailor lures to seem like can’t miss opportunities to try and convince people to make risky choices online.
Example indicators of compromise
|
Indicators |
Description |
First Seen |
|
713d2cca841c2d3df5ba1a4f8926970966ff931d01616ac48d5170a69c1e0765 |
promocion.rar.zip SHA256 |
18 November 2024 |
|
cybelejack9[.]mywire[.]org |
Remcos C2 |
18 November 2024 |
|
quantumdhub[.]ru |
Tycoon Credential Receiver Domain |
9 December 2024 |
|
9a8ed03d.f2cb57a2c2a430507599d2aa[.]workers[.]dev |
SakaiPages Cloudflare Worker |
12 December 2024 |
|
orients-pk[.]com |
SakaiPages Landing Page |
12 December 2024 |
|
185.161.251[.]208 |
Sign-In SystemFacing IP, SakaiPages |
13 December 2024 |
|
jobs-projecthope[.]org |
Job Fraud Domain |
10 December 2024 |

