Proofpoint vs. Microsoft
Considering Microsoft? Consider the risk first.
Protect your Microsoft investment with Proofpoint
Proofpoint stops modern email threats more accurately with continuous detection and analysis—pre-delivery to post-delivery to click time—throughout the entire email delivery lifecycle. It’s time to enhance your Microsoft 365 security to better protect your people and business with Proofpoint.
With Proofpoint, your organization can strengthen your Microsoft 365 security today
Microsoft is a great business productivity company, but…
Microsoft’s native email protection helps to protect you from phishing, malware and ransomware. With Proofpoint, you can fortify your Microsoft 365 security now with advanced threat detection of business email compromise (BEC), QR codes and social engineering-based attacks, all with a compelling return on your investment.
Why customers choose Proofpoint and Microsoft
Enhanced detection efficacy

Microsoft helps to stop threats targeting your organization, but bad actors continue to find new and inventive ways, like MFA bypass, to exploit your existing security defenses.

Proofpoint provides continuous detection and analysis pre- and post-delivery through click time, giving you superior end-to-end threat protection. Our high-fidelity detection stack uses advanced AI, machine learning (ML), large language models (LLMs) and industry-leading threat intelligence to detect the most advanced email threats. With Proofpoint, you get 99.99% email detection efficacy, lower false positives and an easy-to-use and operate solution.
AI-driven threat protection
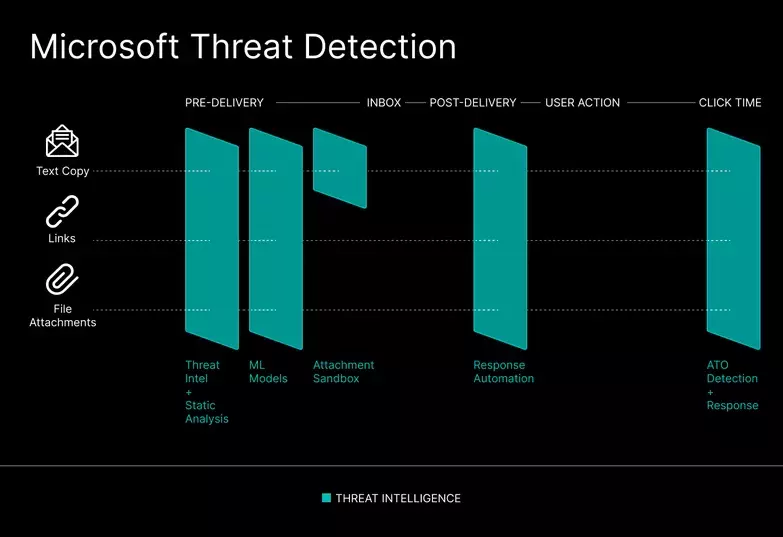
Microsoft can detect modern email threats, such as credential phishing, business email compromise (BEC) and socially engineered attacks. However, Microsoft’s static detection and analysis can lead to limited threat detection that can leave your organization open to compromise.
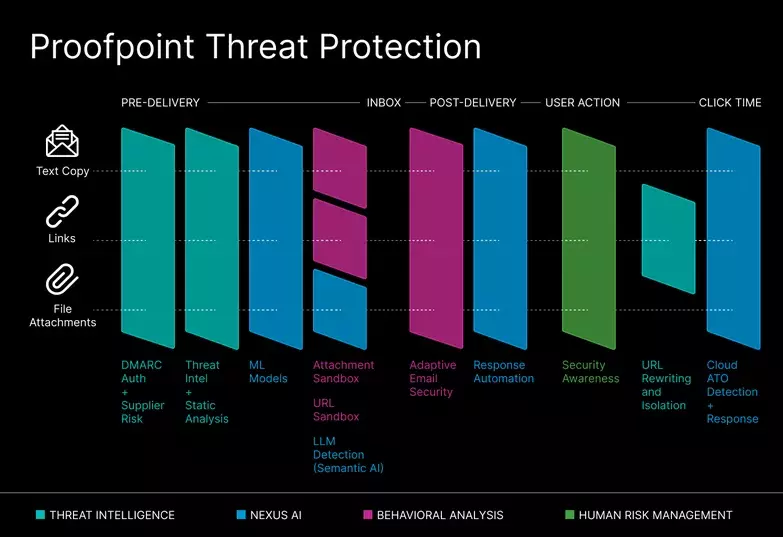
Proofpoint Nexus is an AI-powered, multilayered detection stack that combines threat intelligence, static and dynamic threat analysis, behavioral AI, semantic analysis LLM, and predictive URL analysis and sandboxing to identify and stop modern threats in their tracks. With over two decades of AI/ML experience and more than 250 (and counting) AI patents, we deliver superior threat detection and end-to-end protection against modern email threats.
People and threat visibility
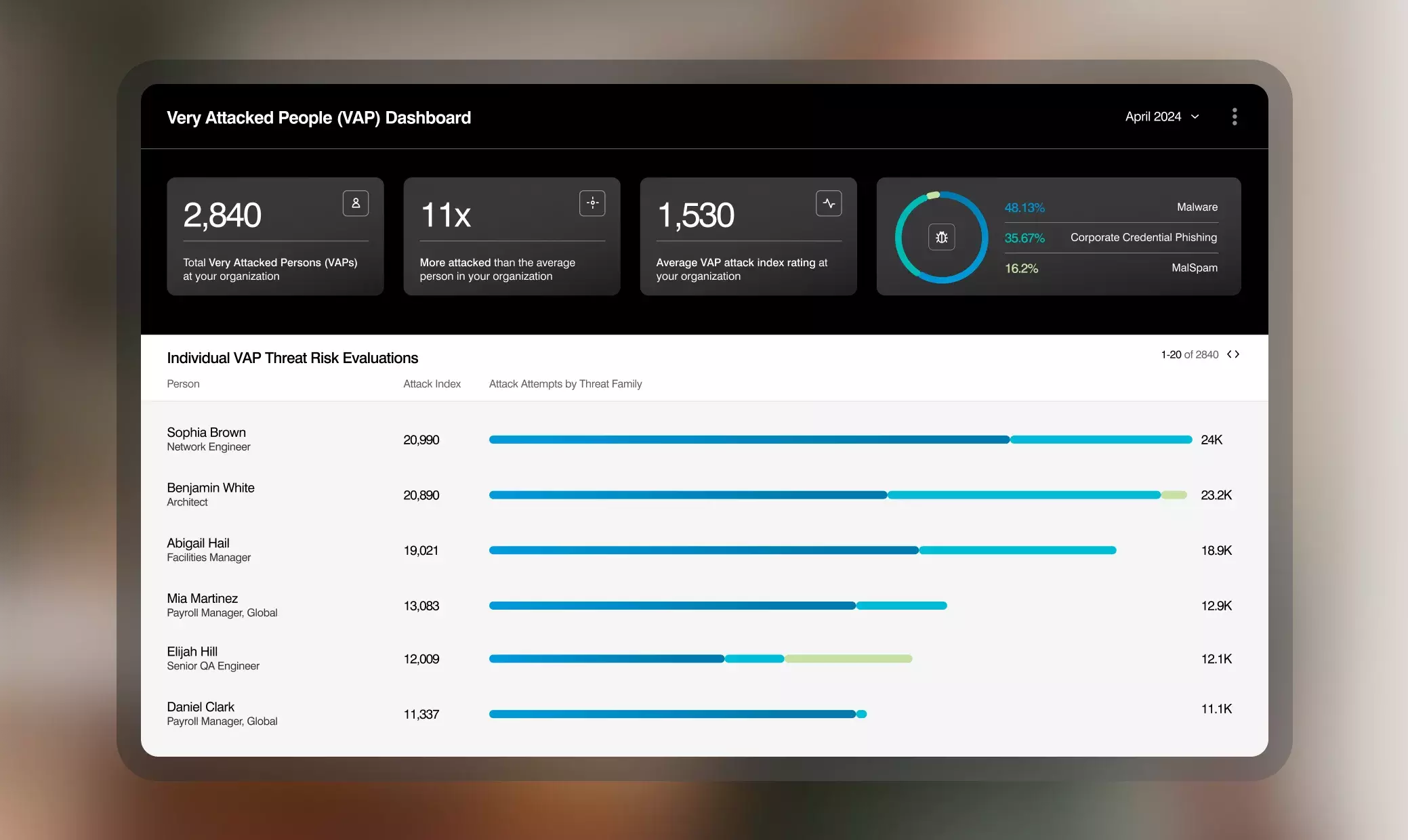
Proofpoint tracks threat trends, correlates campaign insights and automates threat forensics to allow you to better understand the type of threats impacting your organization. Combined with our Very Attacked People™ (VAPs) visibility, we allow you to see which threats are targeting your users and how threat actors are attacking them. This allows you to quickly identify the users most at risk and potentially compromised, so you can take immediate remediation actions.
With Proofpoint, you can fortify your Microsoft 365 environment with human-centric security.
Microsoft and Proofpoint at a glance:
| People Protection Feature | Microsoft | Proofpoint |
|---|---|---|
| Connection filter |
Yes
|
Yes
|
| Inbound email authentication |
Yes
|
Yes
|
| Basic email hygiene (AV/AS) |
Yes
|
Yes
|
| Basic fraud protection (domain spoofing, display name and more) |
Yes
|
Yes
|
| Advanced BEC protection |
No
|
Yes
|
| Contextual email warning tags |
No
|
Yes
|
| User-report message automation |
Yes
|
Yes
|
| Email message hold |
Yes
|
Yes
|
| Basic attachment reputation |
Yes
|
Yes
|
| Basic attachment sandboxing |
Yes
|
Yes
|
| Basic URL rewrite |
Yes
|
Yes
|
| Comprehensive URL sandboxing (pre- and post-delivery) |
No
|
Yes
|
| Manual message remediation |
Yes
|
Yes
|
| Basic automatic message remediation (URLs and attachments) |
Yes
|
Yes
|
| Browser isolation (Very Attacked People) |
No
|
Yes
|
| Semantic analysis LLM detection (pre-delivery) |
Yes
|
Yes
|
| Advanced QR code detection and analysis (scan all inbound URLs pre-delivery) |
Yes
|
Yes
|
| Misdirected email and attachments |
No
|
Yes
|
| Comprehensive campaign and threat insights |
No
|
Yes
|
| Agentless threat detection |
No
|
Yes
|
| Deception-based threat detection |
No
|
Yes
|
| Automated reset of malicious user account configuration changes in M365 |
No
|
Yes
|
| Sophisticated account takeover detection |
No
|
Yes
|
| Compromised vendor account identification and alerting |
No
|
Yes
|
| Supplier compromised account risk scoring |
No
|
Yes
|
| Adaptive controls (isolation) for compromised supplier accounts and Very Attacked People |
No
|
Yes
|
| Secure transactional email from internal applications and SaaS providers |
No
|
Yes
|
| DMARC compliance of transactional email via DKIM-signing |
No
|
Yes
|
| Application email regulatory compliance via encryption and data loss prevention |
No
|
Yes
|
| Delivered threat alerting |
Yes
|
Yes
|
| Comprehensive forensics/IOCs (URLs and attachments) |
No
|
Yes
|
| Campaign correlation |
No
|
Yes
|
| Threat actor analytics, reports and trending |
No
|
Yes
|
| SaaS application visibility |
Yes
|
Yes
|
| People risk explorer |
No
|
Yes
|
| Adaptive controls to combat targeting trends |
No
|
Yes
|
| Executive threat summarization |
Yes
|
Yes
|
| Condemnation threat summarization |
No
|
Yes
|
| Comprehensive identity vulnerability discovery and remediation, including cloud services and endpoints |
No
|
Yes
|
| Attack path visibility to prioritize risk remediation |
Yes
|
Yes
|
| Full attack sequence timeline view |
No
|
Yes
|
| Suspected compromised supplier account insights |
No
|
Yes
|
| Spoofed supplier domain visibility |
No
|
Yes
|
| Global supplier high-risk rankings |
No
|
Yes
|
| Comprehensive suspicious domain visibility |
No
|
Yes
|
| Complete email domain visibility (hijacked domains, domain abuse rate, DMARC, SPF, DKIM pass rates and more) |
No
|
Yes
|
| Supplier DMARC record validation visibility (Nexus Supplier Risk Explorer) |
No
|
Yes
|
| Supplier DMRAC message volume and message visibility from lookalike supplier domains (Nexus Supplier Risk Explorer) |
No
|
Yes
|
We’re recognized as an industry leader by leading analyst firms and customers alike
At Proofpoint, our mission is to protect your people and business. We provide a comprehensive email security solution that provides you with end-to-end protection against known and unknown email-borne threats. That is why Microsoft and Proofpoint together makes your organization more secure. It’s no wonder why 83% of the Fortune 100 trust Proofpoint to enhance Microsoft native security.
Proofpoint ranked #1 in G2's Summer 2023 Email Security Report



Better together with Proofpoint
Microsoft is complex to run—and complex to maintain
Microsoft email security is a good start, but it’s challenging to operate and maintain. The allure of Microsoft fades quickly when you consider its risks. It has hidden costs and complexities that burdened organizations in terms of maintenance, operational efficiencies, customer support and total cost of ownership (TCO).
Proofpoint provides you with an easy-to-use and an easy-to-operate solution while delivering superior operational efficiencies, and lower risks and total cost of ownership.

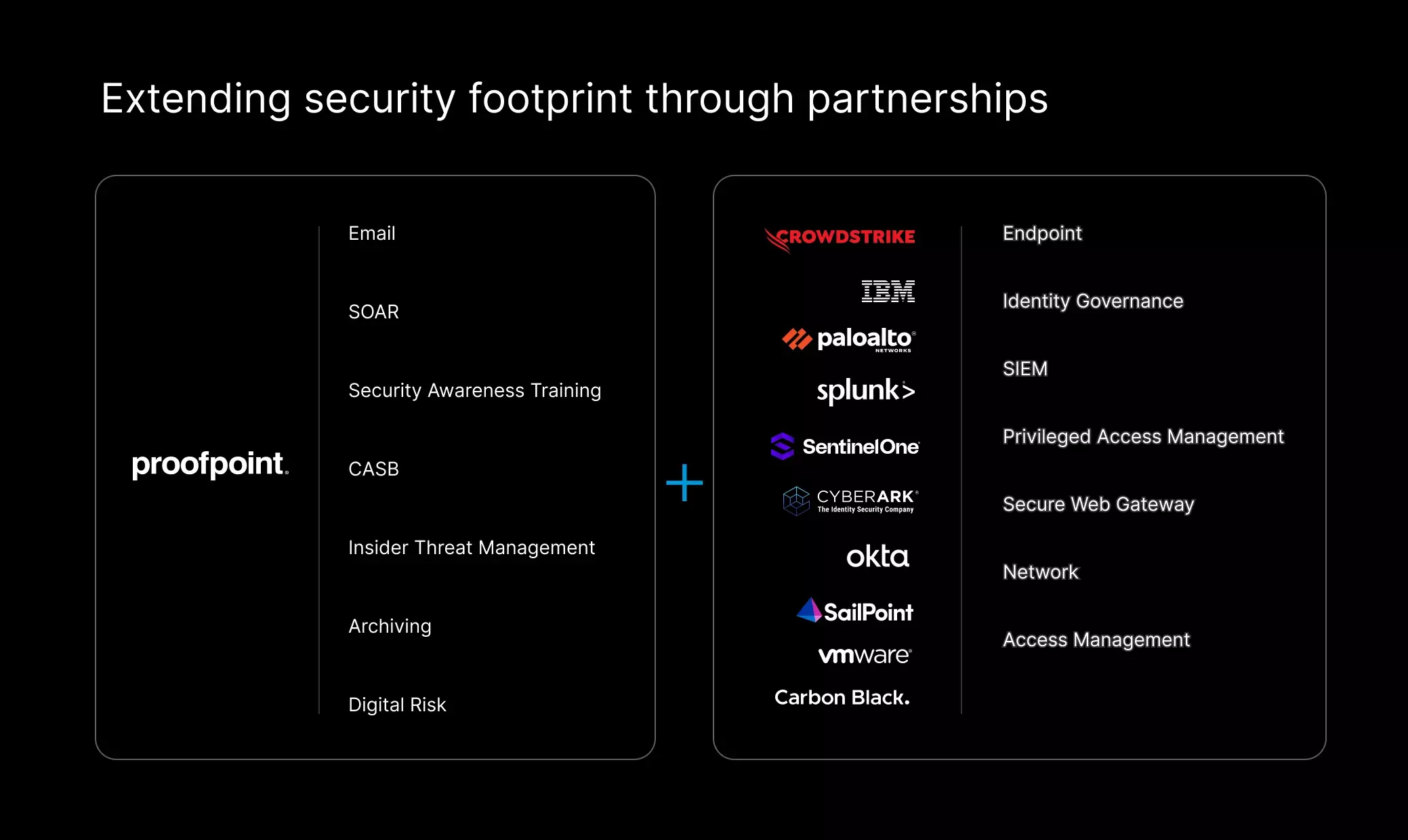
Better together with Proofpoint
Proofpoint augmenting Microsoft email security is just the start. We also integrate and support a rich ecosystem of leading cybersecurity vendors, such as CrowdStrike, Palo Alto Networks, CyberArk, Okta, SailPoint, and even Microsoft Defender and Sentinel. Our API-based integrations combine endpoint, network and identity insights with Proofpoint threat intelligence, behavioral AI and machine learning. This provides you with enhanced security coverage, advanced threat detection and remediation, and lower operational costs.