We live in a multi-cloud world. More often than not, companies use several public cloud service providers and may run dozens or even hundreds of Amazon VPCs, Microsoft Azure VNets, or Google VPC Networks.
These cloud platforms typically serve multiple groups including developers, DevOps, sales and customer success, partners, and customers. Naturally, users may be located in different offices, have different access permissions, and connect with a variety of desktop or mobile devices.
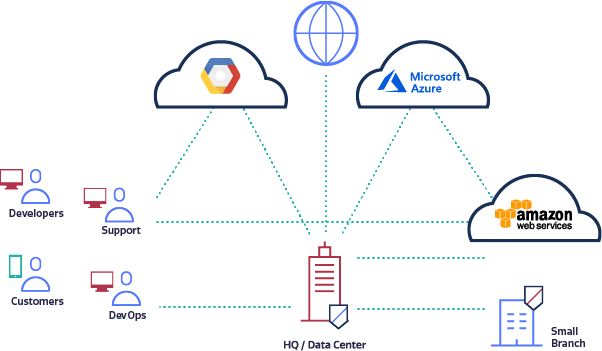
How do you manage 200 Amazon VPCs?
To manage multi cloud connections, you typically have several options. You can:
- Use Access control lists (ACLs) in each VPC to ensure proper access for specific IPs.
- Configure your own VPN gateways for each of the VPCs and provide users with access credentials.
- Use vendor-specific solutions for each cloud platform, like VPC peering in AWS to connect between two VPCs.
- Connect each of the VPCs to a central location, i.e. the company HQ and backhaul user traffic to the HQ
Such methods are perfectly viable when applied to a small number of cloud entities. But they can turn into a nightmare in large scale deployments.
Consider this simple deployment scenario with two cloud providers, Google and AWS. Each is in a different location (Belgium and Germany), and each environment has two VPCs - for production and development.
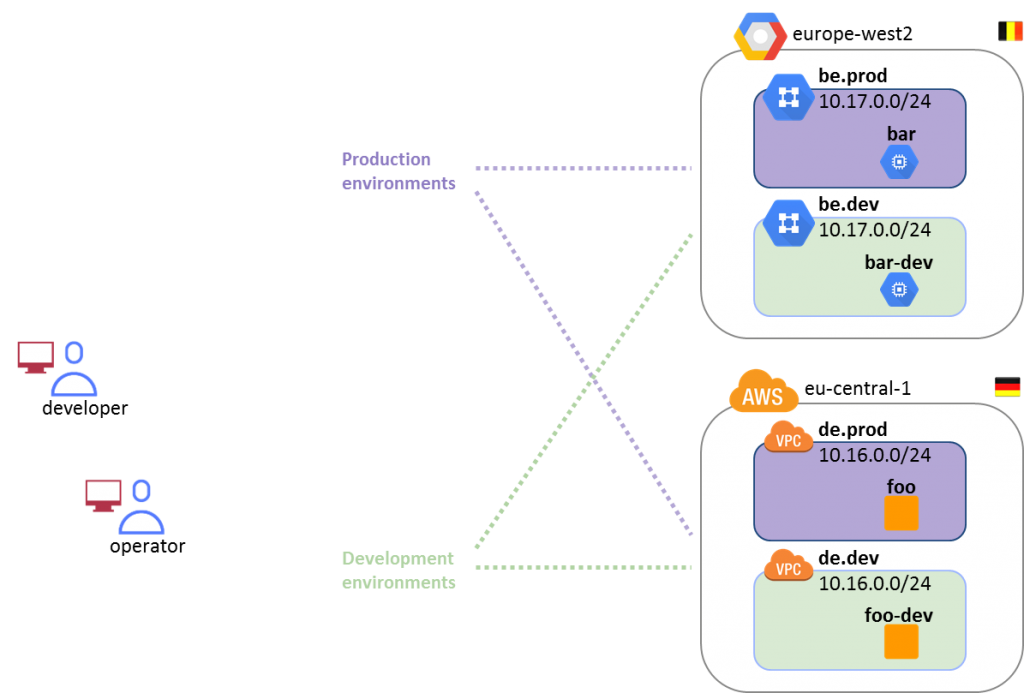
Even at this very small scale, managing access for two different groups - developers and operators - each with its own access rules, is quite cumbersome. Even more so if frequent, granular adjustments are needed, like providing a single developer access to one of the production environments.
Eliminate complexity with a single point of management
Meta NaaS (Network as a Service) provides an alternative approach to large-scale, multi cloud connectivity. It enables you to rapidly provision and manage connections to multiple clouds and data centers.
First, a secure tunnel is created between each of the VPCs, users and the Meta Networks overlay, as you can see below below. Cloud entities are connected using a light, highly available MetaPort gateway. Users can connect with the VPN client, in case they need full network access, and support native applications, or use a browser-based connection that requires no agent at all.

You can define granular, identity-based access policies for applications, services or subnets within each cloud. The Admin console provides a single point of management for all policy definitions, eliminating complexity and minimizing the risk of configuration errors that comes from having to synchronize policies among different products and locations.
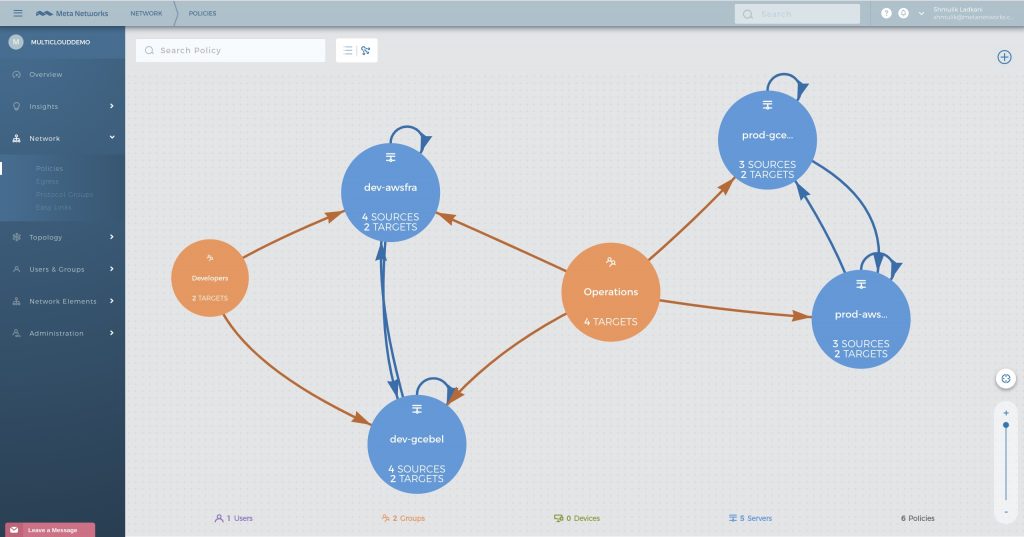
Automate workflows and cross-cloud connectivity via API
Using the Meta API, your DevOps team can orchestrate and automate any cloud-related network workflow - from policy definitions, through dynamic access assignments, routing rules and more. Using our previous example, you could easily connect between the ‘foo’ AWS production server and the ‘bar’ production server in Google in a single API call.
Learn more
Read more about Meta NaasS or contact us for a live demo.
Bio:
View Shmulik Ladkani's profile on LinkedIn

