The healthcare industry is under attack. Ransomware is shutting down emergency rooms, fraudulent emails are defrauding patients, and attackers steal confidential medical data regularly.
Any effective cybersecurity defense starts with a better understanding of advanced threats. That’s why Proofpoint analyzed more than 100 million malicious emails sent to hospitals, clinics, and health insurers in the twelve-month period ending on March 31, 2018.
Our full analysis is detailed in Proofpoint’s 2018 Healthcare Threat Report, “An Ounce of Prevention,” which we launched today. Below, we explore the key findings healthcare professionals need to know.
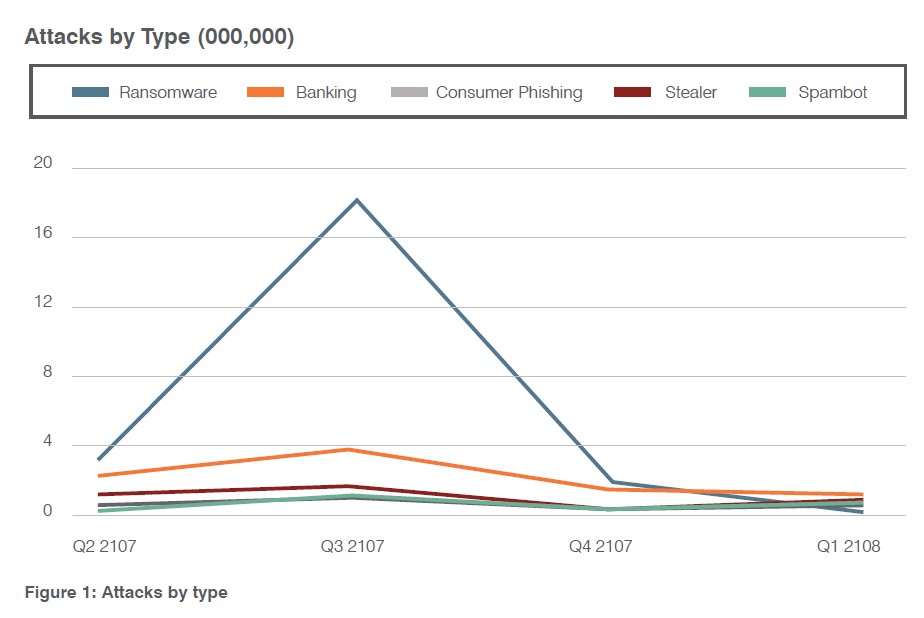
Ransomware Was The Malware Du Jour in 2017. Until It Wasn’t.
Ransomware proved to be the biggest threat targeting healthcare organizations. We detected a combined 40 million attacks using malicious URLs or attachments in Q3 alone. In the fourth quarter, ransomware traffic collapsed as cybercriminals opted for other forms of attack.
But just because attackers switched tactics doesn’t mean they won’t leverage ransomware again in the future. We saw a similar lull in 2016 only to see the technique skyrocket less than a year later.
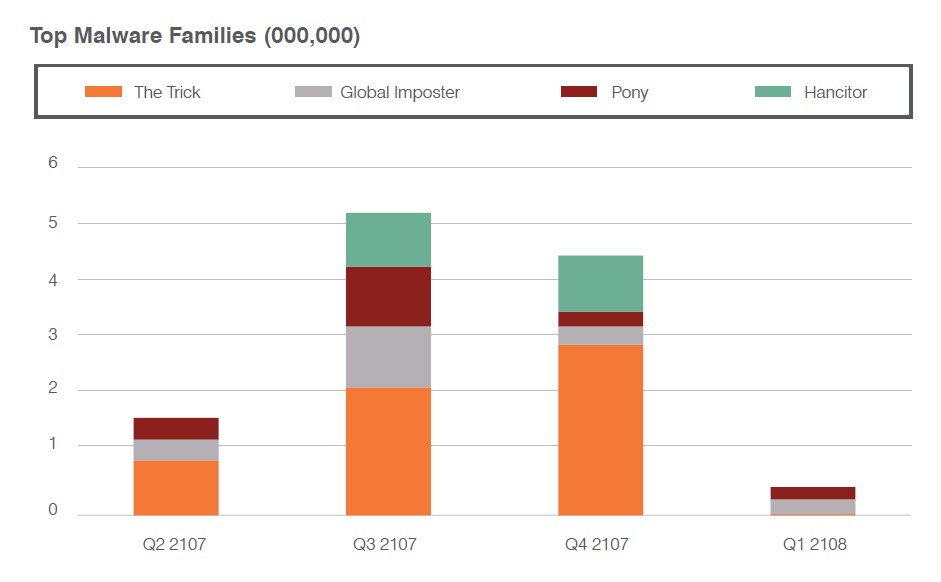
Locky Was Not Lucky For Health Institutions.
Locky, a malware that locks and encrypts a large number of systems and file types, was the top ransomware variant and the most popular strain of malware overall. But it’s not the only threat healthcare defense teams have to worry about. We discovered several other malware families targeting healthcare institutions over the course of our study.
Email fraud leveraged to steal protected health information (PHI)
PHI is valuable to cybercriminals, which is why the healthcare industry a top target. We discovered top phishing techniques include:
- Domain spoofing, in which a cybercriminal uses a trusted domain to send malicious messages.
- Display-name spoofing, when an email’s “From” field is spoofed to fool the recipient.
- Lookalike (or cousin) domain spoofing, when an attacker registers a domain that looks similar to a trusted domain.
While the attack techniques against healthcare organizations vary and evolve, one common thread is that they attack people, not just technology. They exploit healthcare workers’ curiosity, time constraints in acute care settings, and their desire to serve. Combatting these attacks requires a new and people-centered approach to security.
To get our top recommendations for protecting your organization, download our healthcare report here.
