Dynamic security and compliance controls to manage access and data.
AWS has enabled the modern workforce to be cloud-based and remotely distributed, making them a prime target of today’s cyber attacks. Threat actors have shifted their attention from the old network perimeter to people and the data, systems and resources they access. In this evolving environment, securing access to AWS resources, preventing data loss and staying compliant is critical.
Proofpoint for AWS
Discover AWS resources and accounts
Proofpoint can simplify multi-region AWS security and compliance with centralized management. You get visibility on all your SaaS apps and IaaS resources across AWS
- Visualize resource creation trends and look for anomalies such as excessive resource creation or deletion
- Drill down into discovered resources and ensure accounts are provisioned according to regulations and best practices
- Audit network traffic logs to discover cloud apps and AWS accounts accessing your network

Learn more about CASB
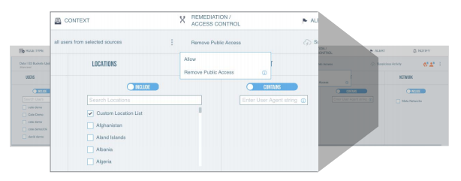
Protect sensitive data
Proofpoint helps you identify and classify sensitive data in your cloud storage repositories such as AWS S3 buckets
- Monitor file activities for DLP violations
- Monitor S3 buckets for excessive sharing
- Build data security policies using 240 built-in DLP classifiers – including built-in smart identifiers, dictionaries, rules and templates that are shared with other Proofpoint DLP products
Learn more about Enterprise DLP
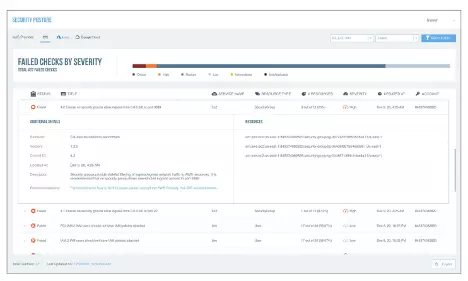
Identify misconfigured services
Proofpoint helps you govern security posture in your AWS environment
- Discover configurations and settings that deviate from published baselines
- Recommend best practices for fixing identified misconfigurations that present a security risk
Learn more about CSPM
Cloud threat prevention
Proofpoint uses threat intelligence about known threat actors to block suspicious logins and prevent account takeover. Contextual data (incl. user location, device, network, login time) is used to further confirm a user’s identity and prevent risky access of AWS resources
- Block access to highly attacked user accounts when CASB detects a suspicious login
- Create a blocklist of countries where your organization does not have a presence

Learn more about Adaptive Access Controls
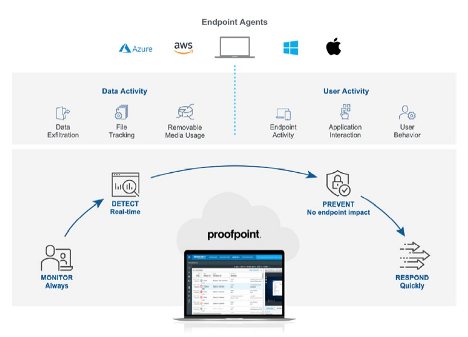
Manage insider threats
Proofpoint delivers visibility on user and data activity across AWS EC2 instances and Amazon WorkSpaces
- Complete view of endpoint-based activity to get full context around user-driven incidents and data-exfiltration
- Visualize threat context around unique user groupings to better manage user risk
Cloud Migration
Proofpoint eliminates complexity of providing secure remote access when moving workloads to Amazon AWS
- Provide users with micro-segmented secure access, enable hybrid-cloud networking between on-premise servers and AWS
- Seamlessly set up cloud-to-cloud connections and apply security policies
Learn more about Cloud Security
Improve email trust
Proofpoint secures your Amazon SES email channel, giving you visibility, tools and services needed to authorize legitimate email
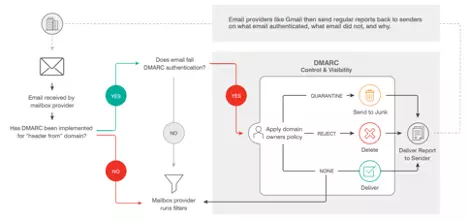
- Address misconfigured email sending systems and email deliverability challenges related to broken email authentication validation checks
- Expose DKIM signing & SPF problems as seen by email receivers
- Identify and report email spoofing
Learn more about Email Fraud Defense
Best practices to ensure email deliverability for Amazon SES customers
Proofpoint Information and Cloud Security Platform
Reviewed by AWS, it brings together Proofpoint Enterprise DLP, Proofpoint Insider Threat Management, CASB, Browser Isolation and Web Security.