With nearly two billion users, Facebook’s reach carries significant potential impacts both for brands and the customers with whom they interact. Comment spam dilutes these interactions at best and, at worst, exposes potential customers to phishing and malware. As with email spam, a high percentage of comment spam on Facebook and other social channels is generated by botnets – networks of compromised machines or accounts that cybercriminals create and control.
Proofpoint researchers observed the API access token for a legitimate, verified Facebook app being used to generate comment spam on Facebook pages. In exchange for more “likes” and comments on their own timelines, users are enticed to provide the app’s access token to a third-party website, the controllers of which leverage the provided access to form a large social spam botnet. In this scheme, attackers exploit an earlier version of the Facebook API and a legitimate but outdated version of a third-party app.
We observed an example of this activity in the social media presence of a Proofpoint customer, a major media outlet, which was the target of large spam attacks posting continuously on its Facebook page. Recent changes by both Facebook and the app developer are now largely preventing this type of attack. We present an analysis of the bot and the third-party and app interactions required to connect profiles to the botnet below.
Analysis
A number of spam comments on the Facebook page in question made reference to various domains that all contained instructions on how to install the Facebook bot on individual accounts using the HTC Sense Facebook app. The incentive for users to install the bot is an increase in likes and comments on the individual’s account, increasing the appearance of popularity.
Figure 1 shows an example of spam comments posted on the media company’s Facebook page.


Figure 1: Example spam comments created by the bot
Searching for “HTC Sense” among Facebook applications yielded several applications by that name. However, further analysis of the app in question showed that the application ID of the app we had installed matched that of the official – and Facebook verified – HTC Sense app. Figure 2 shows the extensive profile permissions requested by the app.
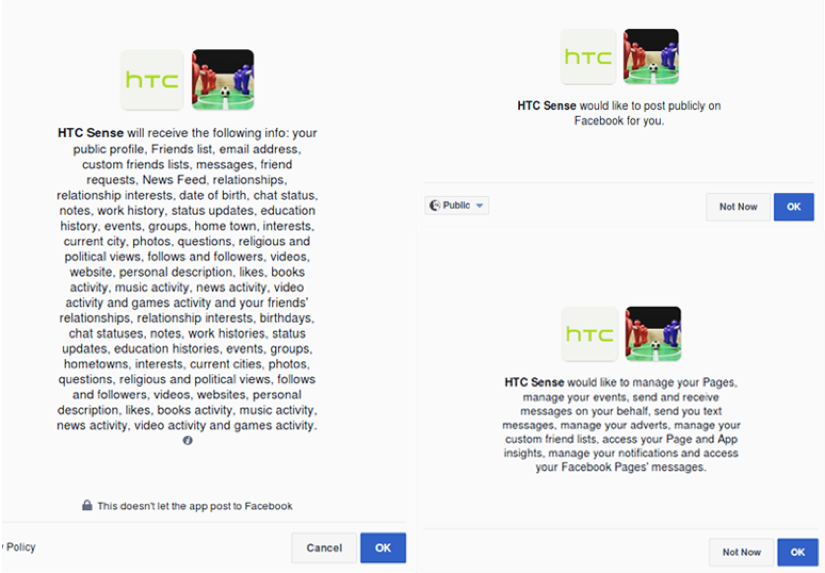
Figure 2: HTC Sense application permissions
It should be noted that while this app was originally developed for mobile devices and maintained for compatibility with earlier HTC phones that had not been or could not be updated, we were able to install it on a test account from a desktop computer.
As shown in Figures 3 and 4, both applications had an ID of: 41158896424, meaning the application was in fact authentic.

Figure 3: Verification of the authenticity of the app

Figure 4: Access Token Debugger output showing the matching app ID of the application
Connecting the HTC Sense application to an individual user’s account and then allowing the spam bot to leverage HTC sense is a multistep process, the details of which are specified on several sites run by the spambot owners (Fig. 5).
Installation and Authentication Process

Figure 5: Schematic of the fraudulent application installation and authentication process
The process is described in further detail below:
- Users visit the bot website from links in comment spam or other path to the website
- They then follow instructions on the bot website to grant the legitimate HTC Sense Facebook application access to an individual Facebook account
- The legitimate app is redirected to Facebook infrastructure for authorization
- Facebook displays the app and the permissions it is requesting, and authenticates the user if they choose to allow the app to access their profile
- User authenticates with Facebook
- Facebook grants the app permissions and gives an access token for the app so it can independently operate on behalf of the user
- User is notified that the app is installed
- The bot website instructs the user to click a link to the Facebook developer page for that specific App ID which prominently displays the access token. The trade for likes socially engineers the user to copy the access token from the website
- The user is instructed to paste the access token into a form on the bot website, thus enabling the bot to operate fully on behalf of the user and masquerade as a legitimate HTC Sense app
While the process is fairly straightforward, the end result potentially has a significant impact both on the users and on the brands targeted by the botnet controllers. This scheme relies on users turning over an app access token that connects their profile to a third-party app with extensive capabilities related to their Facebook profiles. Exploiting the human factor in this way gives the botnet operators powerful capabilities to spam organizations of their choice.
It should be noted that this problem is not isolated to the HTC Sense Facebook app and, in fact, the app itself does not have any specific vulnerabilities. Rather, this attack relies on social engineering and the ease with which users can view and provide access tokens for apps that use an early version of the Facebook Graph API. Since first noticing this activity, we began observing other Facebook applications with generous profile permissions being exploited as well.
Facebook now prevents non-developers from accessing these types of tokens and voluntarily providing them to third parties.
Spam effect
Prior to implementation of mitigation steps by Facebook and HTC, once the HTC Sense application was installed and the user provided its access token to the bot website, Facebook’s activity log made it possible to track when the spam botnet infrastructure posted on behalf of the application and the end user’s account. The botnet would spam other users automatically without requiring any additional input or permission from the user (Figure 6).

Figure 6: Spam posted from a compromised account to other user accounts
The media company’s Facebook page has been hit with tens of thousands of comments from just the botnet masquerading as the HTC Sense Facebook app; well over half of the messages on their page have been spam.


Figure 7: Spam generated by the HTC Sense app on the media company’s page
Facebook revocation of application access
Our analysis found that the botnet began generating spam on behalf of the HTC Sense Facebook application shortly after installation and entry of the access token on the botnet controller’s website. Spam postings were only able to continue for roughly eight hours before Facebook removed the account’s access. The disabling of the offending account was confirmed a short time later by Proofpoint monitoring tools.
Conclusion
As a result of this investigation, we determined that access tokens for verified and official applications are being used as a vehicle by spammers to spread spam on their behalf. The crux of this entire process is that the user has to give up their access token for that app in return for the promise of more friends and followers on their own profile. While this may be tempting, individual users on Facebook should remember that giving excessive permissions to apps and providing their access tokens may result in automatic spamming of other accounts. This can ultimately result in suspension of individual accounts rather than the accumulation of likes and comments.
As noted, we contacted both Facebook and HTC about our findings. Since informing HTC of the issue, the company has removed the problematic version of the app from production and associated access tokens can no longer be exploited by the attackers; Facebook has similarly implemented mitigations described above and this particular type of abuse is now waning. However, end users should still be aware of the potential for scams, malware, and bots that can compromise and abuse their accounts. Facebook recommends that developers review best practices available at fb.me/loginsecurity to avoid these types of problems. It is worth noting that HTC, like many other organizations, was maintaining an earlier version of the app for compatibility with phones that could not be (or had not been) updated by carriers or end users. This speaks to the larger issue of timely updates and obsolescence in both mobile and desktop environments and the potential impact on users and organizations.

