Overview
Real estate transactions frequently involve many electronic signatures, countless exchanges of documents via email, and a variety of interactions with potentially unfamiliar contacts. This environment is ripe for exploitation by threat actors who attempt to steal credentials and other personal information from potential homebuyers and the companies that serve them.
Looking more closely at examples from campaigns we have tracked over the last year, the vast majority use document lures purporting to be from realtors, closing companies, Docusign, or other organizations buyers might expect to be involved in the process. In general, these lures direct recipients to phishing landing pages abusing familiar brands to steal email, Microsoft Office365, and other credentials.
This approach is also consistent with a spike in email fraud or “business email compromise” lures that reference attached or linked documents. While not specific to real estate, this practice increased 14 times between Q1 and Q2 2018, suggesting that threat actors are successfully exploiting the human factor with the promise of important documents.
Docusign
Real estate transactions frequently rely upon electronic signatures, making Docusign a popular and effective lure for potential homebuyers. Threat actors have also recognized the effectiveness of lures that abuse this brand -- click rates globally for Docusign lures are five times the average for the top 20 lures identified in Proofpoint’s most recent Human Factor report.
As noted above, though, these lures are not designed to phish Docusign credentials but rather encourage recipients to log into fake Docusign landing pages with third-party credentials. Figure 1 shows an example of such a landing page that phishes for Microsoft Office 365, AOL, and generic email credentials. These landing pages are linked in phishing emails; the URLs for the links suggest targeting for homebuyers and generally reside on compromised sites, the administrators of which have all been notified:
- hxxp://starsat[.]co[.]zw/Realestate::::FileCD::::DocSign/closin/
- hxxp://the-new-faces[.]com/REALestateFile[.]UNLOCKsecuredCd4Tilleclosing/closin/
- hxxps://cloud[.]greenspringsschool[.]com/realestate/closin/

Figure 1: A basic credential phishing landing page abusing the Docusign brand
Figure 2 shows a more sophisticated phishing landing page that also abuses real estate brands (blurred at the bottom of the image) to increase the sense of legitimacy for potential victims.

Figure 2: A more sophisticated landing page abusing additional real estate-related brands (blurred)
When recipients click Log In or View Document they are taken to the login page shown in Figure 3. The URL for this page demonstrates the ease with which threat actors can set up lookalike domains, in this case, hxxp://business[.]docusign[.]com[.]pinataszass[.]com/account/realestate/letallianac/document/login/email_signin/. Also note that the URL as well as the landing pages themselves continue the real estate targeting.

Figure 3: Credential harvesting page abusing the DocuSign brand
Generic Closing Documents
While the examples above could have been used with document related to real estate transactions, others phishing templates were more specific to the process of closing on a mortgage. Figure 4 is still a credential harvesting page but references “closing disclosure” on the landing and includes “onlineclosing.disclosure” in the URL. It also includes logos for two national realtors (blurred in the figure), again to add legitimacy for victims.
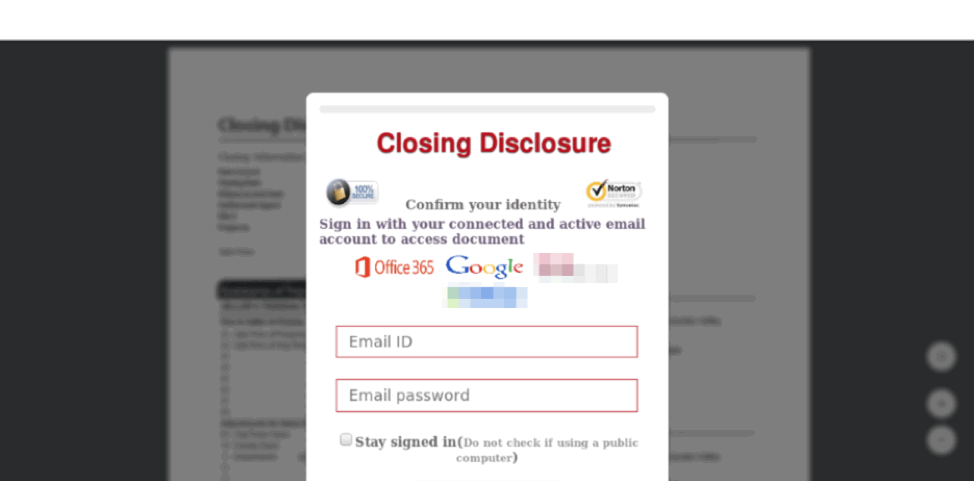
Figure 4: “Closing Disclosure” landing page abusing brands of two national realtors and phishing for email credentials
In several other cases, we also observed generic email credential phishing pages with URLs that referenced closing or closing documents. Thus, threat actors can easily reuse generic templates with more targeted campaigns.
Figure 5 shows another technique in which victims need to download a fake “Important Closing document”, clicking on which takes recipients to another credential phishing page.

Figure 5: Fake download page for “Important Closing document” leading to Microsoft credential phishing
Additional abused real estate brands
While most of the phishing schemes we observed used lures and templates related to documents for real estate transactions, some abused well-known real estate brands. Real estate search sites and nationally recognized real estate franchises all made their way into phishing templates. Threat actors, as they often do, co-opted these brands and their graphics and then used social engineering techniques to convince potential homebuyers to enter email credentials to access additional content like “secured auction pages.”
Attacks on real estate businesses
While less common than widespread real estate phishing, we also observed a variety of direct attacks on real estate businesses. These include email attacks on realtors, homeowners insurance agencies, and more, in which the primary payloads included remote access Trojans (RATs). Because of the nature of the transactions in which these business engage, RATs and information stealers offer additional opportunities for threat actors to steal a range of personal and banking information. Figure 6, for example, shows an emailed attack delivering a malicious document to an apartment rental business bearing a malicious document that, when opened with macros enabled, would install the Netwire RAT.
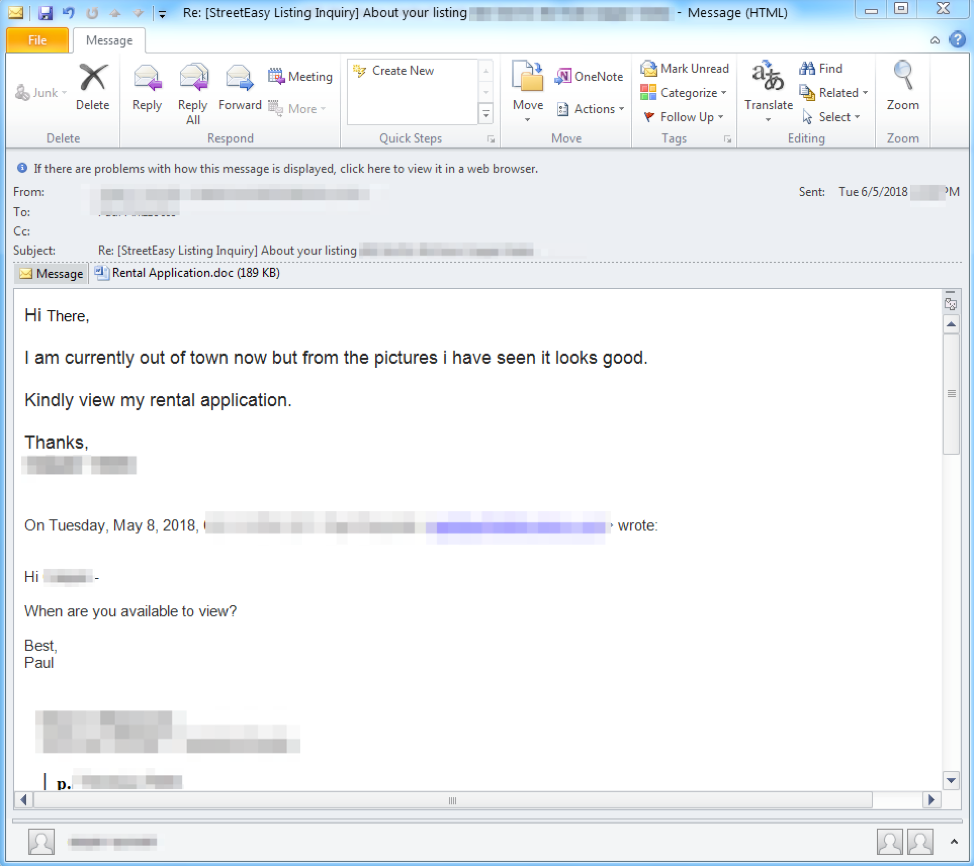
Figure 6: Lure delivering a malicious document that can download and install the Netwire RAT
We also noted BEC attacks on mortgage companies using typosquatted domains and social engineering attempting to initiate fraudulent transfers of funds, rounding out the range of threats revolving around real estate.
Conclusion
Real estate frequently involves high-stakes, rapid transactions for all involved parties. The number of emails exchanged during these transactions can be overwhelming with numerous documents changing hands, digital signatures passing to different entities, and more. Consumers should be exceedingly vigilant in their interactions with parties claiming to be involved in ongoing real estate transactions while realtors, mortgage brokers, and other industry organizations should educate customers about security and take steps to avoid abuse of their brands. Moreover, real estate professionals should implement layers of protection against increasingly frequent attacks on the industry.

