Overview
KovCoreG, a financially motivated threat actor active since at least 2011, made headlines recently when Proofpoint researchers uncovered a long-running malvertising campaign distributing Kovter ad fraud malware via social engineering. Kovter itself was developed by KovCoreG, first as ransomware and then reincarnated as an ad fraud powerhouse. This blog traces the activities of KovCoreG, also referred to as MaxTDS by FoxIT InTELL, from its early days distributing the Zaccess backdoor to its latest social engineering attacks. The history of KovCoreG in many ways parallels the history of web-based threats over the last several years. Analyzing the evolution of this actor and their techniques enables us to better understand the increasingly sophisticated techniques employed by crimeware threat actors, and, in particular, the general movement from reliance on automated exploits to the integration of social engineering to carry out infections.
Figure 1: Timeline of KovCoreG operations (click to expand)
Figure 1 shows the evolution of KovCoreG operations. Although we can likely trace their activities back to 2010 or even earlier, we began our analysis at end of December 2011 when the connections among malware strains, campaigns, and KovCoreG became most concrete.
Before Kovter: Zaccess/SecurityShield
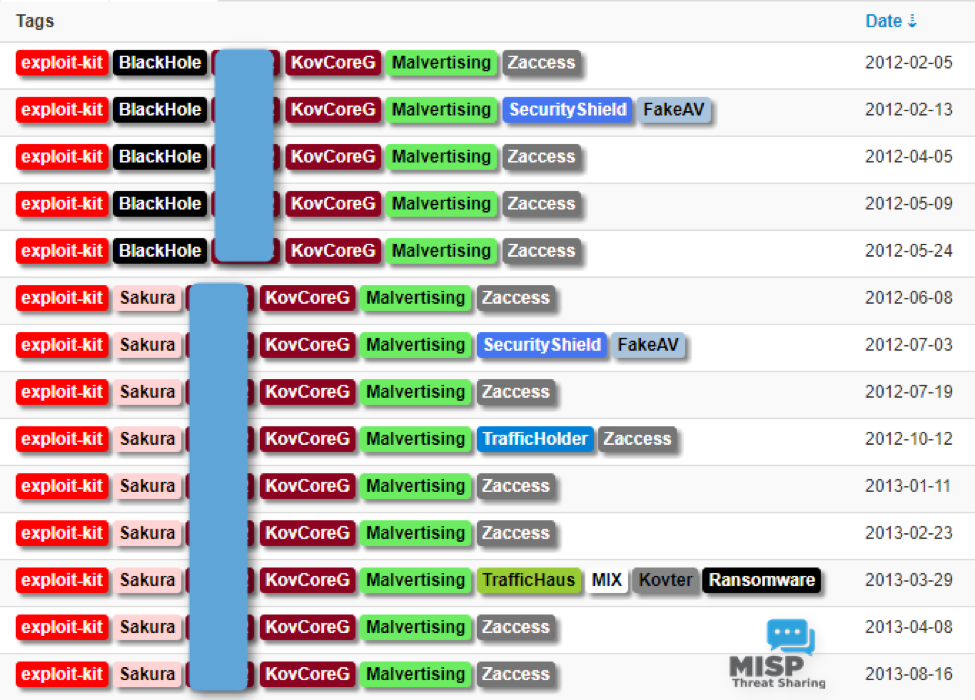
Zaccess, also known as ZeroAccess and Sirefef, is a backdoor Trojan used to load a variety of potential malware on Windows PCs. From at least the end of 2011 through mid-2013, KovCoreG distributed Zaccess via exploit kits (EKs) in large-scale malvertising campaigns. During much of this period, the group was also distributing SecurityShield, a fake antivirus application (“scareware”) that alerted users to nonexistent security threats and prompted them to pay for removal. KovCoreG also leveraged EKs and malvertising to install SecurityShield, setting the stage for distribution of their homegrown Kovter malware via similar vectors in the years to come. Figure 2 details KovCoreG activity related to Zaccess and SecurityShield in 2012 and 2013.
Figure 2: KovCoreG activity before the advent of Kovter malware
KovCoreG distributed SecurityShield as an affiliate, one of many actors involved in widespread scareware infections during this period. Figure 3 is a screenshot showing the application as it appears to end-users with infected PCs.
Figure 3: Screenshot of SecurityShield scareware, July 2012
Between the end of 2011 and the first half of 2012 , KovCoreG’s infections occurred via the Blackhole exploit kit (Figure 4). In April 2012, KovCoreG appeared to test the Redkit EK but quickly returned to Blackhole. In June 2012, however, the group began using the Sakura EK in their malvertising campaigns, continuing through most of 2013.
Figure 4: Example artifact of infection chain using the Blackhole EK in March 2013 (Source: MalwareDomainList)
Figure 5 shows an example infection chain from August 2012 in which KovCoreG used Sakura EK to distribute the Zaccess Trojan on adult websites.
Figure 5: KovCoreG chain to Sakura spreading Zaccess through adult traffic, August 11, 2012
The Advent of Kovter
KovCoreG is best known for development and distribution of Kovter malware. Initially developed as ransomware, the malware was later reengineered as ad fraud malware. Below, we trace the discovery and evolution of KovCoreG’s malware of choice, including the affiliate distribution we believe they control.
On December 9, 2012, researchers detected the first sample of malware (SHA-256 669c4212bb1c65b2957f2ac5e68560ef11457a556d3f156dd0f5a3599d7b6434) showing Kovter characteristics. This sample appeared to be in development and based on the Sisron Trojan. On January 5, 2013, another sample (SHA-256 16e4f9bf1e877020e8880ffc707ab110662885e78a74c2dbc4a39473d81d3d2b) was detected with a Kovter command and control (C&C) on compromised host. In both cases, the infection vector was unknown.
Figure 6 illustrates a selection of KovCoreG activity distributing Zaccess and Kovter ransomware, before exclusively spreading Kovter as an ad fraud malware, via multiple exploit kits and social engineering schemes. The final instances of Zaccess distribution appear to coincide with the group’s transition of Kovter to ad fraud.
Figure 6: Illustration of some of the KovCoreG activity in the Kovter Era
On March 29, 2013, Kovter ransomware was observed in a live infection chain via the Sakura EK.
Figure 7: Live infection chain for Kovter, March 29, 2013 [1]
Figure 8 shows another infection chain in which KovCoreG leverages the Sakura EK:
Figure 8: Another KovCoreG infection chain into the Sakura Exploit Kit, April 1, 2013
In August 2013, KovCoreG distributed a “PRISM-themed” version of Kovter ransomware. The version used social engineering to convince victims that they may face prosecution for “illegal content” on their computers if they did not pay to resolve the bogus charge. The infection chain and a screenshot of the ransom message appear in Figures 9 and 10, respectively.
Figure 9: KovCoreG infection chain into PRISM-themed Kovter, August 25, 2013 [2]
Figure 10: A PRISM-Themed Kovter ransom message, August 25, 2013 [2]
Figure 11 shows a similar German-language “Police Locker” message for Kovter from October 2013.
Figure 11: German Design for a Kovter ransom message , October 2013 [3]
To our knowledge, KovCoreG was the last user of Sakura, extending their use of the EK for several weeks beyond that of any other customers. Figure 12 shows the last recorded Sakura pass.
Figure 12: Last recorded Sakura pass: a KovCoreG chain, November 22, 2013
End of 2013: Infection chain filtering and transition to ad fraud
At the end of 2013, the group began adding significant filtering and implemented a multistep infection chain. This helped them avoid repeated reports to ad agencies and reputation services that forced them to rebuilt accounts, proxies, etc., The approach proved highly effective, allowing KovCoreG to stay globally below the radar and reach high volumes with quality traffic. [4][5][6][7][8]. It also became increasingly difficult to obtain a full infection chain replay.
In March 2014, KovCoreG began using the Styx EK, an infection chain an example of which is shown in Figure 13:
Figure 13: KovCoreG chain into Styx dropping Kovter which, at this point, had been converted to ad fraud malware, March 2014.
By the end of March 2014, Kovter migrated from ransomware to ad fraud malware; Kovter continues today as part of a sophisticated ad fraud scheme.
June 2014 Transition to Sweet Orange
In June 2014, KovCoreG stopped using Styx EK and began using the Sweet Orange exploit kit. Figure 14 shows the use of Sweet Orange to distribute Kovter exploiting CVE-2014-0569, a Flash vulnerability that allowed arbitrary code execution.
Figure 14: KovCoreG using the Sweet Orange EK to distribute Kovter, October 10, 2014 [10]
In October 2014, the group also briefly used RIG EK to distribute Kovter, but quickly turned back to Sweet Orange, which they continued to use until early 2015 when they switched to Nuclear EK.
December 2014: KovCoreG begins pyramid/affiliate distribution of Kovter malware
In December 2014, Kovter was detected appearing in other infection chains involving different actors and vectors. It appeared that the malware was being distributed in affiliate mode, with all affiliate IDs (affids) in the 8xx range associated with other actors and 5xx and 6xx affids operated by KovCoreG itself.. Figure 15 shows nearly three years of activity following the move to an affiliate or pyramid model. It appears that KovCoreG controls this model with all other actors distributing Kovter downstream from KovCoreG.
Figure 15: Illustration of Kovter distribution following its move to affiliate mode (click to expand)
Figures 16-21 all show various infection chains and actors distributing Kovter beginning in late December 2014.
Figure 16: Selected websites compromised by “Pseudo-Darkleech” that redirect to Fiesta EK, dropping Kovter instead of Miuref, another ad fraud Trojan previously associated with this chain, December 30, 2014
Figure 17: Kovter and Redyms Spread via Nuclear Pack by another actor, December 30, 2014
In April 2015, Kovter distribution accelerated with additional new actors joining as affiliates.
Figure 18: 2015-04-02 EITest redirecting traffic to Nuclear Pack spreading Kovter (SHA-256 51e5ac323d93505f18ddeaeb44c8b06d3215b346631033b08056d53a1a9b7477), April 2, 2015
Figure 19: Kovter spread via Fiesta by another group than KovCoreG, April 2, 2015
Figure 20: Kovter spread via Nuclear Pack by another group than KovCoreG, April 2, 2015
Figure 21: Kovter spread along with Andromeda (not shown here but later grabbing Cryptowall 303) via Nuclear Pack from a fifth different driveby actor, April 7, 2015.
The threat actor TA548 (aka “Nemucod”) are also integrating it as one of their payloads in spam campaigns [13]. The actor TA530 spread Kovter heavily in October 2016, also via malicious spam campaigns. [15]
KovCoreG Followup
February 2015: Nuclear Pack
KovCoreG relies heavily on malvertising to distribute Kovter. Figure 22 shows a complete malvertising chain abusing the Engage:BDR network and using an instance of the Nuclear Pack EK in February 2015.
Fig 22: Full malvertising chain via EngageBDR into the KovCoreG Nuclear Pack threads dropping Kovter, February 21, 2015
June 2015: Angler EK
In mid-2015, KovCoreG transitioned to Angler EK for their malvertising operations. Figure 23 shows one such malvertising chain, again dropping Kovter.
Figure 23: 2015-07-03 - KovCoreG chain to Angler EK (dropping Kovter)
July 2015: Neutrino test
In July, the group used Neutrino EK for several days. Snapshots of their driveby activity statistics for two of these days provide significant insight into the reach of these campaigns. The statistics for the captured Neutrino threads can be found in Appendix A. These four sets of snapshots, taken 24 hours apart on July 19 and 20, 2015, show not only a strong focus on the US, Canada, and Great Britain, but also the accumulation of more than 20,000 infections over this 24-hour period.Notably, these statistics are only for Kovter distribution operated by KovCoreG; affiliate infections are not counted in these snapshots.
February 2016: Adding a social engineering scheme
In February 2016, KovCoreG added a social engineering scheme that allowed the group to also target Chrome and Firefox users. Microsoft documented this social engineering scheme in May 2016 [9]. One such scheme, utilizing a fake Adobe Flash update, is shown in Figure 24.
Figure 24: KovCoreG Social Engineering Scheme, February 15, 2016
In parallel with this activity, KovCoreG was also still targeting Internet Explorer users with Angler EK:
Figure 25: KovCoreG chain to Angler dropping Kovter for IE users February 17, 2016
Figure 26: Another KovCoreG social engineering template (moved to an HTA drop)
April 2016: Infection chain gains full HTTPS support
Finally, in April 2016, the group’s infection chain gained full HTTPS support, making it more difficult to capture complete chains (Figure 27).
Figure 27: KovCoreG social engineering template template observed in a chain with HTTPS support, May 1, 2016 [11]
KovCoreG has continued extensive malvertising campaigns in 2017, using a variety of stolen branding over the last year, a selection of which is shown in Figure 28:
Figure 28: List of “creative” used by KovCoreG in the last year. [12]
Conclusion
KovCoreG demonstrates how a financially motivated actor can adapt, evolve, and innovate over several years, influencing the threat landscape while remaining effective and viable as they fly under the radar of law enforcement, the sites and ad networks they abuse, and end users. KovCoreG also provides a window into the ways in which affiliate models can grow, increasing the footprint of a particular threat while spreading the risk for a single threat actor. KovCoreG has been at the forefront of malvertising, exploit kit usage, and, as EKs declined, social engineering, while distributing lucrative malware through multiple vectors. Through their relatively long history, the group has adapted to the shifting popularity of scareware, “police locker” ransomware, exploit kits, and, for the last few years, taken advantage of the massive scale and automation of online advertising. We will continue to follow this actor and the affiliates distributing Kovter to see what comes next - and how best to defend against it.
Acknowledgements
Frank Ruiz from FoxIT InTELL for his invaluable and long-running assistance in the ongoing study of KovCoreG.
@maciekkotowicz - CertPL for Affid association assistance.
@herrcore for multiple inputs into this research including assistance with Affid identification
@malekal_morte for all the work he did also tracking this group from 2011 to 2014
References
[1] http://malware.dontneedcoffee.com/2013/03/ransomware-kovter-looking-at-your.html, March 29, 2013
[2] http://malware.dontneedcoffee.com/2013/08/prism-themed-ransomware.html
[3] http://malware.dontneedcoffee.com/2013/10/kovter-even-more-abominable-also-add.html
[4] http://blog.trendmicro.com/trendlabs-security-intelligence/youtube-ads-lead-to-exploit-kits-hit-us-victims/, August 14, 2014
[5] https://blog.malwarebytes.com/threat-analysis/2015/01/major-malvertising-campaign-hits-sites-with-combined-total-monthly-traffic-of-1-5bn-visitors/, November 26, 2014
[6] https://blog.malwarebytes.com/threat-analysis/2015/08/large-malvertising-campaign-takes-on-yahoo/, August 3, 2015
[7] https://blog.malwarebytes.com/threat-analysis/2015/08/angler-exploit-kit-strikes-on-msn-com-via-malvertising-campaign/, August 27, 2015
[8] https://www.invincea.com/2015/02/fessleak-the-zero-day-driven-advanced-ransomware-malvertising-campaign/, February 2015 (Mixing several actors including Hanjuan
(https://www.invincea.com/wp-content/uploads/2015/02/chalie-huffington.png) and KovCoreG (https://www.invincea.com/wp-content/uploads/2015/02/analysis-1.png) )
[9] https://blogs.technet.microsoft.com/mmpc/2016/05/10/large-kovter-digitally-signed-malvertising-campaign-and-msrt-cleanup-release/, May 10, 2016
[10] http://malware.dontneedcoffee.com/2014/10/cve-2014-0569.html
[11] https://twitter.com/kafeine/status/730172140692082688
[13] https://techhelplist.com/spam-list/781-problems-with-item-delivery-fedex-js-malware, April 11, 2015
[14] https://www.proofpoint.com/us/threat-insight/post/spike-kovter-ad-fraud-malware-clever-macro-trick
[15] https://www.proofpoint.com/us/threat-insight/post/spike-kovter-ad-fraud-malware-clever-macro-trick
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
www.maxtds[.pro|109.236.86[.]55 |
Domain|IP |
2012-03 - KovCoreG aka MaxTDS |
|
217.23.4[.]32 |
IP |
KovCoreG G BlackHole proxy (2012-01) |
|
76.73.1[.]186 |
IP |
KovCoreG BlackHole proxy (2012-02) |
|
109.235.49[.]23 |
IP |
KovCoreG BlackHole proxy (2012-03) |
|
208.94.247[.]50 |
IP |
KovCoreG BlackHole proxy (2012-03) |
|
kilmotor[.co[.cc|83.133.125[.]125 |
Domain|IP |
KovCoreG BlackHole proxy (2012-03) |
|
76.73.39[.]18 |
IP |
KovCoreG BlackHole proxy (2012-03) |
|
95.163.66[.]195 |
IP |
KovCoreG BlackHole proxy (2012-03) |
|
95.163.66[.]198 |
IP |
KovCoreG BlackHole proxy (2012-04) |
|
66.90.104[.]163 |
IP |
KovCoreG BlackHole BackEnd (2011-12 > 2012-08) |
|
78.83.177[.]247 |
IP |
KovCoreG Sakura proxy (2012-08) |
|
78.83.177[.]251 |
IP |
KovCoreG Sakura proxy (2012-08) |
|
50.7.247[.]82 |
IP |
KovCoreG Sakura (BackEnd - 2012-08) |
|
50.7.213[.]194 |
IP |
KovCoreG Sakura proxy (2012-08) |
|
50.7.233[.]18 |
IP |
KovCoreG Sakura (BackEnd - 2012-09) |
|
146.185.255[.]49 |
IP |
KovCoreG Sakura proxy (2012-08) |
|
xaemeeze.eebackinfo[.pro|83.133.127[.]142 |
Domain|IP |
KovCoreG Sakura proxy (2012-08) |
|
146.185.255[.]102 |
IP |
KovCoreG Sakura proxy (2012-09) |
|
afhcfhhfd[.co[.cc|63.223.107[.]33 |
IP |
2012-09 KovCoreG Sakura proxy |
|
afhbccacg[.co[.cc|146.185.255[.]115 |
IP |
2012-09 KovCoreG Sakura proxy |
|
afhjjafii[.co[.cc|50.7.240[.]189 |
Domain|IP |
2012-09 KovCoreG Sakura proxy |
|
146.185.255[.]87 146.185.255[.]95 146.185.255[.]123 146.185.255[.]130 146.185.255[.]137 146.185.255[.]149 146.185.255[.]158 |
IPs |
2012-10 KovCoreG Sakura proxy |
|
afichedbb[.co[.cc|50.7.211[.]50 50.7.211[.]51 50.7.211[.]52 50.7.211[.]53 50.7.211[.]54 |
Domain|IP |
2012-10 KovCoreG Sakura proxy |
|
91.220.35[.]182 91.220.35[.]188 |
IPs |
2012-10 KovCoreG Sakura proxy |
|
91.220.35[.]230 91.220.35[.]231 91.220.35[.]234 91.220.35[.]241 91.220.35[.]248 91.220.35[.]249 91.220.35[.]250 91.220.35[.]251 91.220.35[.]252 91.220.35[.]253 91.220.35[.]254 91.220.35[.]166 |
IPs |
2012-10 KovCoreG Sakura proxy |
|
fa99faa78d.carmonsri.waw[.pl:82|50.7.241[.]142 |
Domain:port|IP |
2013-02 KovCoreG Sakura proxy |
|
669c4212bb1c65b2957f2ac5e68560ef11457a556d3f156dd0f5a3599d7b6434 |
sha256 |
2012-12-19 First known sample showing Kovter Sigs |
|
16e4f9bf1e877020e8880ffc707ab110662885e78a74c2dbc4a39473d81d3d2b |
sha256 |
2013-01-05 Kovter on compromised host C&C |
|
occro.ascelibrary.wloclawek[.pl|91.214.202[.]175 |
Domain|IP |
2014-03-31 KovCoreG Styx Proxy |
|
navio.suez-online.ostrowiec[.pl|192.133.137[.]68 |
Domain|IP |
2014-04-09 KovCoreG EK Proxy |
|
wecyc.growstats.ostroleka[.pl|69.65.52[.]179 |
Domain|IP |
2014-06-13 KovCoreG EK Proxy |
|
emark.abagsnet.jaworzno.pl|217.23.3[.]178 |
Domain|IP |
2014-08-11 KovCoreG Sweet Orange Proxy |
|
progr.rixposednewsonline.czeladz[.pl|23.19.44[.]204 |
Domain|IP |
2014-09-03 KovCoreG Sweet Orange Proxy |
|
rtysu.yedion.olkusz[.pl|64.251.19[.]199 |
Domain|IP |
2014-10-26 KovCoreG Sweet Orange Proxy |
|
flash.ikallzu.pila[.pl|64.251.19[.]201 |
Domain|IP |
2014-11-13 KovCoreG Sweet Orange Proxy |
|
adolf.xtoday-news.karpacz[.pl|79.143.82[.]84 |
Domain|IP |
2014-12-12 KovCoreG Sweet Orange Proxy |
|
ompld.nchothuexedulichtphcm.malbork[.pl|195.138.246[.]20 |
Domain|IP |
2014-12-30 KovCoreG Sweet Orange Proxy |
|
quali.tlechorepublicain.legnica[.pl|108.61.147[.]251 |
Domain|IP |
2015-01-11 KovCoreG Sweet Orange Proxy |
|
dress.cunitynews[.com|209.239.124[.]156 |
Domain|IP |
2015-02-15 KovCoreG Nuclear Proxy |
|
searc.dhinezammohandesi[.in|148.251.36[.]121 |
Domain|IP |
2015-04-28 KovCoreG Nuclear Proxy |
|
group.thmphotofunny[.in|144.76.229[.]31 |
Domain|IP |
2015-05-15 KovCoreG Nuclear Proxy |
|
laith.miothpostmanpligg[.net|209.159.145[.]150 |
Domain|IP |
2015-06-15 KovCoreG Nuclear Proxy |
|
skyhi.doofoibotoolboxnews[.net|45.34.75[.]99 |
Domain|IP |
2015-07-15 KovCoreG Angler Proxy |
|
stamf.pahfuupforitnetworks[.com|50.2.191[.]101 |
Domain|IP |
2015-08-15 KovCoreG Angler Proxy |
|
wam.oozoodefiscaliser[.com|198.204.226[.]244 |
Domain|IP |
2015-09-15 KovCoreG Angler Proxy |
|
ax0r7wkbn.eeyohlaprensademonagas[.com|176.9.79[.]83 |
Domain|IP |
2015-10-15 KovCoreG Angler Proxy |
|
kwn6jl3ssuh.iekobsmartbacklink[.net|188.138.82[.]185 |
Domain|IP |
2015-11-15 KovCoreG Angler Proxy |
|
f4be9ffi.ahxaoeslfast[.com|104.243.43[.]221 |
Domain|IP |
2015-12-15 KovCoreG Angler Proxy |
|
nm5a03m4k531.chahmuserinstinct[.net|45.58.118[.]219 |
Domain|IP |
2016-01-12 KovCoreG Angler Proxy |
|
lzb048m.achuyrheinforum[.com|216.244.78[.]186 |
Domain|IP |
2016-02-15 KovCoreG Angler Proxy |
|
b08l0lgy.ahceetechydevil[.biz|216.244.78[.]186 |
Domain|IP |
2016-03-11 KovCoreG SocEng/Angler Proxy |
|
apj5kyc6a4il.aigoldivane[.org|216.244.78[.]186 |
Domain|IP |
2016-03-20 KovCoreG SocEng/Angler Proxy |
|
*.eezoodailycal[.org|162.219.26[.]85 2016-12-20 SocEng |
Domain|IP |
2016-12-20 KovCoreG SocEng |
|
alivestreammarketing[.com|178.63.58[.]117 |
Domain|IP |
2015-02 KovCoreG Malvertising Server |
|
cloudradns[.com|78.46.87[.]52 |
Domain|IP |
2015-07-09 KovCoreG Malvertising Server |
|
flavers[.net|178.63.58[.]72 |
Domain|IP |
2015-07-03 KovCoreG Malvertising Server |
|
abcmenorca[.net|88.198.188[.]158 |
Domain|IP |
2015-07-17 KovCoreG Malvertising Server |
|
ivorylabelmedia[.com|78.46.99[.]154 |
Domain|IP |
2015-06 KovCoreG Malvertising Server |
|
toxicads[.com|176.9.251[.]253 |
Domain|IP |
2015-03 KovCoreG Malvertising Server |
|
miradasystems[.com|46.4.33[.]168 |
Domain|IP |
2015-02-06 KovCoreG Malvertising Server
|
|
formationtraffic[.com|78.46.111[.]132 |
Domain|IP |
2015-05 KovCoreG Malvertising Server |
|
powermediacreative[.com|78.46.99[.]154 |
Domain|IP |
2015-03 KovCoreG Malvertising Server |
|
trafficonlinemarketing[.com|178.63.58[.]115
|
Domain|IP |
2015-03 KovCoreG Malvertising Server |
|
streammarketingsolutions[.com|46.4.33[.]167
|
Domain|IP |
2014-11 KovCoreG Malvertising Server |
|
ads.discreetad.com|162.210.192[.]78 |
Domain|IP |
2014-03 KovCoreG Malvertising Server |
|
cdntrafficstats[.net|176.9.251[.]253 |
Domain|IP |
2014-03 KovCoreG Malvertising Server |
Appendix A - Neutrino wave statistics for KovCoreG Kovter distribution in July 2015
The loads in the following screen captures refer to the number of infections; the group’s filtering ensures that the infections are unique.
Figure A1: KovCoreG Neutrino Thread 1: July 19, 2015
Figure A2: KovCoreG Neutrino Thread 1: July 20, 2015 (+5200)
Figure A3: KovCoreG Neutrino Thread 2 : July 19, 2015
Figure A4: KovCoreG Neutrino Thread 2 : July 20, 2015 (+3600)
Figure A5: KovCoreG Neutrino Thread 3 : July 19, 2015
Figure A6: KovCoreG Neutrino Thread 3 : July 20, 2015 (+4000)
Figure A7: KovCoreG Neutrino Thread 4 : July 19, 2015
Figure A8: KovCoreG Neutrino Thread 4 : July 20, 2015 (+7200)