The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals and how Proofpoint helps organisations better fortify their email defences to protect people against today’s emerging threats.
Cybercriminals continue to refine their phishing campaigns with evolving technologies and psychological tactics. Campaigns often mimic trusted organisations, using phony emails and websites that appear nearly identical to their legitimate counterparts.
According to Proofpoint Threat Research, phishing attacks grew 147% when comparing Q4 2023 with Q4 2024. There was also a 33% increase in phishing delivered by major cloud-based productivity platforms. These alarming statistics underscore how phishing threats are rapidly evolving. And generative AI tools like ChatGPT, deepfakes and voice cloning services are a part of this trend.
A phishing campaign that used the Capital One brand is a good example of the growing sophistication of these attacks, which frequently target financial institutions. In this blog post, we’ll explore how this campaign worked and how Proofpoint stopped the threat.
The scenario
Cybercriminals sent out emails that looked like they were coming from Capital One. They used two main types of lures:
- Transaction verification. Emails asked users whether they recognised a recent purchase. This tactic is especially effective during the holiday season.
- Payment notification. Emails informed users that they had received a new payment and prompted them to take action to accept it. The high payment amounts created a sense of urgency.
From 7 December 2024 to 12 January 2025, this campaign targeted more than 5,000 customers with about 130,000 phishing messages.
Capital One has implemented strong security measures, including email authentication and takedowns of lookalike domains. However, threat actors continue to find ways to abuse its brand in phishing campaigns. Attackers exploit users’ trust in financial institutions, using deceptive tactics to bypass security controls and trick unsuspecting users into revealing sensitive information.
The threat: How did the attack happen?
Here’s how the attack unfolded:
1. Setting the lure. The attackers crafted emails that closely mirrored official Capital One communications. The company’s logo, branding and tone were all copied. Messages created a sense of urgency, which is a tactic often used by threat actors to cause recipients to make hasty decisions.

Phishing lure used by threat actors.
Subject lines were compelling and aimed to quickly capture attention. Financial concerns, like unauthorised purchases or payment alerts, were a common theme to entice users into opening the email and clicking the links.
Examples:
- “Action Required: You’ve Received a New Payment”
- “[Username], Do You Recognise This Purchase?”

Another lure used by threat actors.
2. Abusing URL services. To bypass user scepticism, attackers exploited their inherent trust in Google URLs. Embedded Google URLs were used as redirection mechanisms, linking recipients to phishing websites. These websites were designed to look identical to Capital One’s legitimate login page.

Spoofed Capital One login website.
3. Harvesting credentials. When a user clicked the links, they were taken to spoofed login pages. There they were prompted to enter their Capital One login credentials and SMS verification codes. These credentials were immediately captured by the attackers, which gave them unauthorised access to the user’s Capital One accounts. They could also bypass multifactor (MFA) authentication protections.
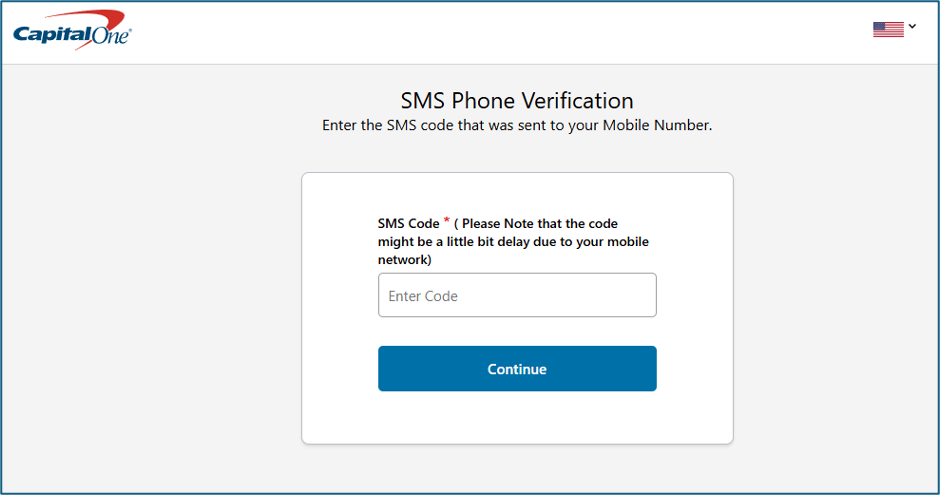
Spoofed verification page on proxy website.
The detection: How did Proofpoint identify this attack?
Proofpoint uses a variety of threat detection techniques. AI is a cornerstone of our Nexus platform. Our multi-model approach combines semantic and behavioural AI, machine learning (ML) and curated threat intelligence from researchers. All of these technologies work together to create a multilayered defence that can detect and mitigate malicious messages and content in highly sophisticated and evolving threats.
Phishing campaign attributes in the Proofpoint Targeted Attack Protection (TAP) dashboard.
Proofpoint Nexus flagged this campaign as malicious based on these observations:
- Abused URL services. Attackers used Google’s URL services, which are commonly abused by threat actors, to mask the redirection to phishing websites. This technique exploited the inherent trust in Google domains to bypass suspicion and increase the likelihood of user engagement with the malicious link.
- Uncommon URL domains. The domains used in the campaign were either newly registered or rarely seen across our monitored traffic. The lack of established history with these domains—coupled with their use in a phishing context—strongly indicated malicious activity.
- Uncommon sender behaviour. The sender was unfamiliar. And they had not emailed the targeted recipients before. While new senders are not inherently suspicious, the combination of urgency in the email content and other red flags raised suspicion.
- Lookalike domain tactics. The campaign used domains that were designed to closely resemble legitimate Capital One URLs. These domains incorporated small, hard-to-spot variations, like altered characters or added symbols.
- Low-volume domain traffic. The sender’s domain had very low email volumes across our entire customer base. Low traffic domains, particularly those that suddenly appear in targeted campaigns, are often linked to threat actors setting up infrastructure specifically for malicious purposes.
- AI-inferred intent. Proofpoint Nexus Language Model (LM) used semantic analysis to understand the content of the messages and identify recurring themes, like urgency and financial concern. Emails were flagged as highly suspicious based on their thematic patterns.
- Suspicious requests. Emails included prompts that urged recipients to verify transactions or claim payments through provided links. These requests were designed to exploit users’ trust and provoke immediate action, a hallmark of phishing campaigns.
Proofpoint not only detected this threat within our own customer data, but we also identified it behind the defences of three other leading Gartner Magic Quadrant Email Security players. This shows that the attack was highly sophisticated. And it proves that Proofpoint advanced threat detection capabilities are highly effective.
Zero messages in this campaign were delivered to our users. Proofpoint detected and blocked all of them.

Condemnation summary of signals Proofpoint used to detect the threat.
The remediation: What are the lessons learned?
Here’s what we recommend to help protect against these threats:
- Invest in pre-delivery URL analysis. Phishing campaigns often use trusted URL services to hide malicious links. Tools that scan URLs pre-delivery can help detect and block these links before they reach users’ inboxes. These tools analyse the underlying URL structure and compare it to known malicious patterns. This ensures that even disguised links are identified and neutralised.
- Strengthen employee education programmes. Regular training sessions can change employees’ behaviour over time, making them more vigilant and proactive. Sessions should teach users how to recognise phishing attempts and to be sceptical of unsolicited messages. They should also emphasise the importance of inspecting email details, such as sender addresses and embedded links. And they should teach users to independently verify transaction alerts by logging directly into their financial accounts.
- Adopt click-time URL protection. Even with robust email filtering, some malicious emails may slip through or be weaponised after delivery. Click-time URL protection adds another layer of security. It reanalyses links when users click on them and blocks access to phishing websites in real time. This dynamic protection helps in scenarios where URLs change post-delivery to evade initial detection.
- Deploy phish-resistant MFA. Traditional MFA methods, such as SMS-based codes, are increasingly targeted by attackers. So, it’s a good idea to use phish-resistant MFA solutions instead. FIDO2-based tools can prevent credential theft and eliminate opportunities for threat actors to get past security measures. They rely on cryptographic keys and ensure authentication remains secure—even if a user’s credentials are compromised.
- Implement email authentication protocols. SPF, DKIM and DMARC protocols can prevent email spoofing and ensure that messages are legitimate. These technologies work together to ensure that senders are who they say they are, which helps reduce the risk of impersonation-based attacks.
Capital One has taken proactive steps to prevent impersonation. This includes authenticating their email domains and working to dismantle fraudulent sites. However, as this campaign illustrates, cybercriminals can still misuse trusted brands in other ways. This shows why it’s so important to have a comprehensive security strategy that includes user education, real-time threat detection and multilayered defences.
Proofpoint delivers human-centric protection
Threat actors continuously adapt to compromise existing defences. Credential phishing campaigns like this one highlight the critical need for a multilayered security solution.
There are two options for implementing Proofpoint threat protection:
- Core Email Protection SEG. It ensures that organisations achieve end-to-end protection against modern email threats. With highly customisable configurations, organisations can tailor protection levels and policies to their specific needs. For security-mature organisations, Proofpoint also delivers detailed insights into people-risk and threat intelligence telemetry.
- Core Email Protection API is designed for lean security and IT teams. It seamlessly enhances Microsoft 365 with advanced threat detection and automated remediation. Organisations can ‘set it and forget it’ because it automates threat detection and response. As a result, it reduces the burden on security teams.
To learn more, download our Proofpoint Threat Protection solution brief.

