Businesses that choose Proofpoint tend to stay with us. In fact, while many start by using our email threat detection tools, over time they often consolidate their other cybersecurity tools with us. They end up using Proofpoint for their other attack surfaces, like identity threats and information protection.
But what happens if they’re forced to adopt Abnormal Security by senior management? That’s what happened to the Fortune 500 financial services corporation discussed in this blog post. They wanted to share their story but requested anonymity. As a customer of both Proofpoint and Abnormal, they have some key insights about what makes Proofpoint stand out from the competition.
A defense-in-depth approach
An existing Microsoft 365 E5 customer, the company deployed a defense-in-depth security approach because the native and Microsoft Defender email security capabilities were not good enough to detect and block phishing, malware and ransomware. They also used CrowdStrike and complemented these tools with Proofpoint Threat Protection. Proofpoint ensured that they could detect and block more sophisticated email threats like:
- Socially engineered attacks
- Business email compromise (BEC)
- Advanced credential phishing
By combining Microsoft, Proofpoint and CrowdStrike, the customer had powerful email security. It could detect and block email threats and automate remediation across its offices worldwide. And it had a strong continuous detection model (predelivery, post-delivery and click-time) throughout its entire email delivery flow. End-to-end protection is why 87% of Fortune 100 companies trust Proofpoint to protect their people and business.
Because the customer’s senior executive management team truly believed in the defense-in-depth approach, it decided to add Abnormal Security as an additional layer of defense. Abnormal is an API-based, post-delivery, remediation-only tool that’s positioned as easy to use. Featuring behavioral AI, it’s sold as a “set it and forget it” tool that can detect and remediate email threats faster while improving operational efficiency.
The company soon integrated Abnormal with its existing Microsoft 365 APIs so that Abnormal could receive emails from Microsoft. At the same time, the customer deactivated automated remediation in Proofpoint Threat Response Auto-Pull. The Abnormal tool was now in charge of analyzing emails post-delivery.
“We were told it would be ‘set it and forget it’ with Abnormal but found it couldn’t be further from the truth.”
— IT director, data security, Fortune 500 financial services company
A head-to-head comparison: Proofpoint vs. Abnormal
Once they started using Abnormal, the cybersecurity team watched what it could do and assessed how the company’s new defense-in-depth approach was going. Here’s what they observed.
Predelivery efficacy: Proofpoint wins
Unlike Proofpoint, Abnormal does not provide any predelivery detection or analysis capabilities; it has a 0% predelivery efficacy rate. Compare that to Proofpoint predelivery detection, which stops known and emerging threats before they are delivered to users’ inboxes. This prevents users from engaging with threats and reduces the downstream burden on security teams.
Proofpoint uses a multilayered detection stack to accurately identify and catch the widest array of threats. Our broad set of detection technology means that we can apply the right technique for the right threat. This includes QR code scams, URL-based threats and BEC attacks.
By combining our existing attachment defense with our new predelivery hold and sandboxing of suspicious messages with URLs, Proofpoint ensures that fewer malicious URLs and dangerous payloads are delivered to users’ inboxes. This includes QR codes or any malicious files that are attached to emails. And thanks to our new predelivery large language model (LLM) detection engine, which uses semantic analysis, organizations are also protected from threats like BEC. This engine can understand the intent and context of the language that’s within email messages.
Proofpoint has more than 20 years of experience with AI and ML. Our models are trained with richer datasets, so they provide superior accuracy and efficiency. We analyze over 3 trillion messages per year across 510,000+ organizations globally. Because we have the right data to constantly train our AI and ML models, we deliver an efficacy rate of 99.99%.
Threat intelligence visibility: Proofpoint wins
Unlike Proofpoint, Abnormal does not provide any threat intelligence visibility or telemetry into unknown or emerging threats across the global threat landscape. As a result, Abnormal has a major detection blind spot. In contrast, Proofpoint provides you with rich threat intelligence to help you stay ahead of the ever-changing threat landscape. We are your early warning system.
We have a team of dedicated threat researchers who investigate threats, identify new trends and track threat actor activity including advanced persistent threat (APT) actors. And we don’t keep this data to ourselves. Rather, we proactively provide you with overviews of executive-level, global and vertical threat data so that you’re always informed about what’s going on in the email threat landscape. We also provide detailed insights into which specific threat actors are targeting your business. That insight includes how they are evolving their tactics and techniques.
Proofpoint threat intelligence is also easy to understand. Not only does it explain why a threat was condemned, but it also provides a timeline, a list of affected users and other points observed by our behavioral AI. The customer said that it found our richer and deeper threat visibility incredibly valuable. And when they compared Abnormal intelligence and visibility to Proofpoint, they found Abnormal to be very limited.
Post-delivery remediation: Proofpoint wins
Abnormal relies on a single detection method—anomaly detection. By itself, anomaly detection is extremely “noisy” and generates a lot of false positives. When legitimate messages are flagged as suspicious or malicious, business is disrupted. But that’s not all. Security teams also have a lot more work to do. That’s because it’s their job to manually triage, investigate and remediate every single one.
The customer found that Abnormal needed a lot of attention. Its security team had to constantly verify email messages, put false positives back into users’ inboxes and remove malicious messages that were let through. In fact, the security team had to assign a full-time researcher to review every single alert, every single day for almost a year.
What’s worse, Abnormal would also wake up the security team at night. Why? When Proofpoint determined that a message was malicious, it would send a post-delivery alert to Abnormal. At this point, it was up to Abnormal to remove the message from the user’s inbox. If Abnormal determined that the message was benign, then the email would not be removed and it would stay in the user’s inbox. In other words, team members had to go into the system to remove every single message that Proofpoint flagged as malicious. (This situation became particularly frustrating when the security team had to remove messages at 1 a.m. on a weekend manually.)
The customer brought this matter to the attention of the team at Abnormal. However, they were told the situation would “confuse their algorithms.” They could not add exceptions for malicious alerts from Proofpoint.
The choice is clear
After using Abnormal for almost a year, the customer was not impressed with the experience. It was overwhelmed with the growing number of false positives. And it didn’t appreciate the lack of visibility into threat intelligence and the ineffectiveness of its post-delivery remediation. As a result, the customer asked to accelerate their Proofpoint Threat Response Auto-Pull annual renewal. And it removed Abnormal from its environment as soon as possible.
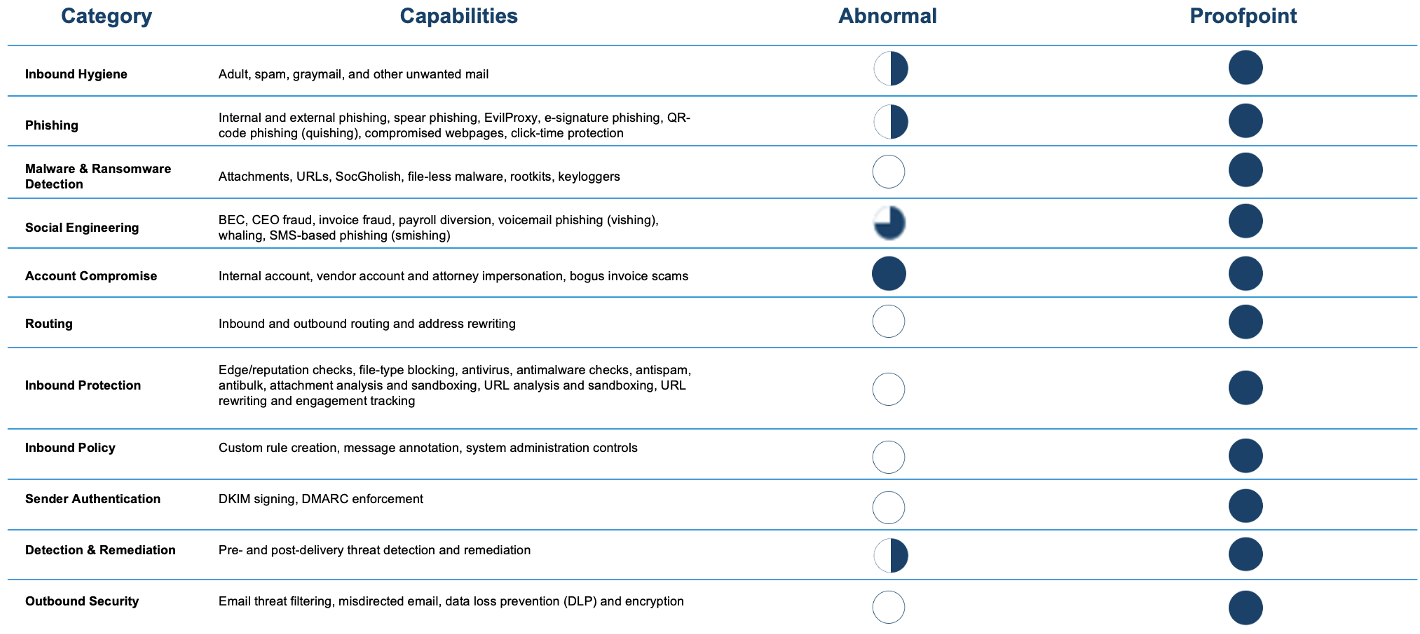
A comparison of Abnormal Security and Proofpoint.
This company’s experience and conclusions are not unusual. Proofpoint research shows that companies that switch to Proofpoint see their detection and prevention of malicious messages improve by more than 30%.
The allure of Abnormal fades quickly when you consider its risks. Abnormal has hidden costs and complexities that burdened this company in terms of maintenance, operations, support and total cost of ownership. And keep in mind that Abnormal cannot exist without Microsoft. That means your company’s security solely depends on Microsoft email security capabilities.
Proofpoint delivers human-centric security
The choice you make on cybersecurity is critical to your people and business. When you compare Proofpoint and Abnormal, Proofpoint wins every time.
To keep your business safe from today’s advanced threats, it’s critical to have a defense-in-depth strategy that complements your native Microsoft email security capabilities. You can achieve end-to-end protection when you take a modern approach to email security by focusing on continuous threat detection and analysis (predelivery to post-delivery to click-time) throughout the email delivery flow.
In this fragmented landscape, Proofpoint provides a cohesive solution that encompasses AI/ML-driven threat protection, behavioral analysis and automated remediation. Our human-centric security is indispensable in your efforts to thwart a wide array of sophisticated email threats.
To learn more about human-centric security and how Proofpoint can help protect your people and your business, download our solution brief, Microsoft and Proofpoint: More Secure Together.

