Email fraud costs organisations nearly $2 billion every year— the largest category of financial loss in cybersecurity, according to the recent FBI Internet Crime Report for multiple years running. The Bureau also warned the public that business email compromise (BEC) schemes have evolved from hacking or spoofing the email accounts of CEOs, to impersonating and compromising vendor email accounts.
These BEC scams are difficult to detect as:
- Attackers rely on social engineering— there’s no malicious payload to find
- BEC attacks are highly targeted
- Attackers have become more sophisticated— they often leverage both impersonation tactics and compromised accounts jointly in an attack
And among various types of BEC threats, supplier invoicing fraud often accounts for large dollar losses, given the nature of B2B payments. Proofpoint has observed that 98% of organisations have received a threat from a supplier domain with nearly three-quarters of those threats being phishing or impostor threats. Even world class security organisations struggle with stopping these human-activated threats that don’t lend themselves to traditional defence in depth. Additionally, most organisations lack the visibility to scalably understand which of their users are being targeted, which suppliers are being spoofed or compromised, and how to respond once BEC signals are detected.
Advanced BEC Defense
Proofpoint has been stopping email fraud attacks for years, launching an ML-driven classifier as the attack category emerged over five years ago. Despite having stopped millions of fraud attempts, we haven’t rested on our laurels and have now launched an Advanced BEC Defense capability, powered by a completely new detection platform that we call Supernova. Leveraging inbound and outbound gateway telemetry, supply chain risk analytics, and API data from cloud productivity platforms like Office 365 and Google Workspace, it accurately uncovers even the most sophisticated email fraud attacks, and is available to all Protection, TAP, and P bundle customers today at no additional charge.
At its core, the new engine leverages a proven approach that we’ve applied to threat detection of all types over the years – the ensemble. Supernova leverages a combination of machine learning, stateful analytics, behavioural analytics, rulesets, and the work of researchers tracking threat actor tactics to deliver both high efficacy and the lowest false positive rate of any of our detection platforms. The ML components of Supernova are trained by our unmatched data set that comes from global scale and our deployments protecting the #1 threat vector at more of the Fortune 100, Fortune 1000, and Global 2000 than any other security provider.
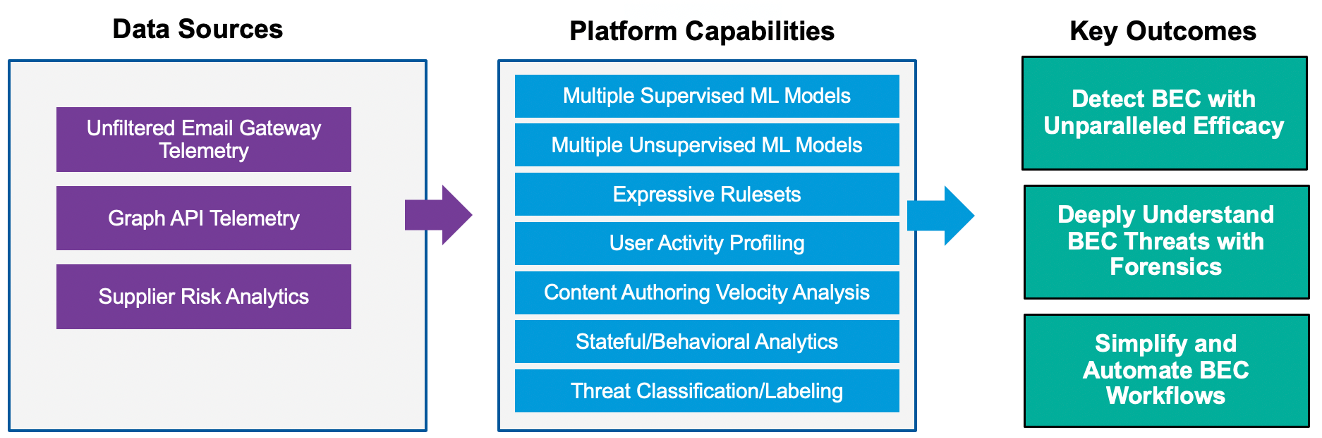
The inputs to both the ML-driven and the other detection components work by analysing multiple message attributes, including message header data, sender’s IP address (x-originating IP, reputation), and sender/recipient relationships, message body for sentiment and language and more to determine whether a message is a BEC threat. It effectively detects and blocks supplier invoicing fraud by analysing messages for numerous tactics associated with supplier fraud, such as reply-to pivots, use of malicious IPs, use of impersonated supplier domains, and words or phrases commonly used in this type of attacks.
The Supernova engine is technically our third generation ML platform, but as the earlier models are all still operational, effective, and highly useful in training each other, it’s really just the newest member of the ensemble. That said, its other analytical capabilities make it both more effective and less false positive-prone than any ML-only approach. In recent head to head comparisons against several API-only tools, it has delivered both higher true positive detection rates and substantially lower false positive rates.
How Advanced BEC Defense Stops Supplier Invoicing Fraud
Here’s a real-world example that shows how an attacker leveraged compromised accounts and supplier impersonation jointly in a sophisticated supplier fraud attack.
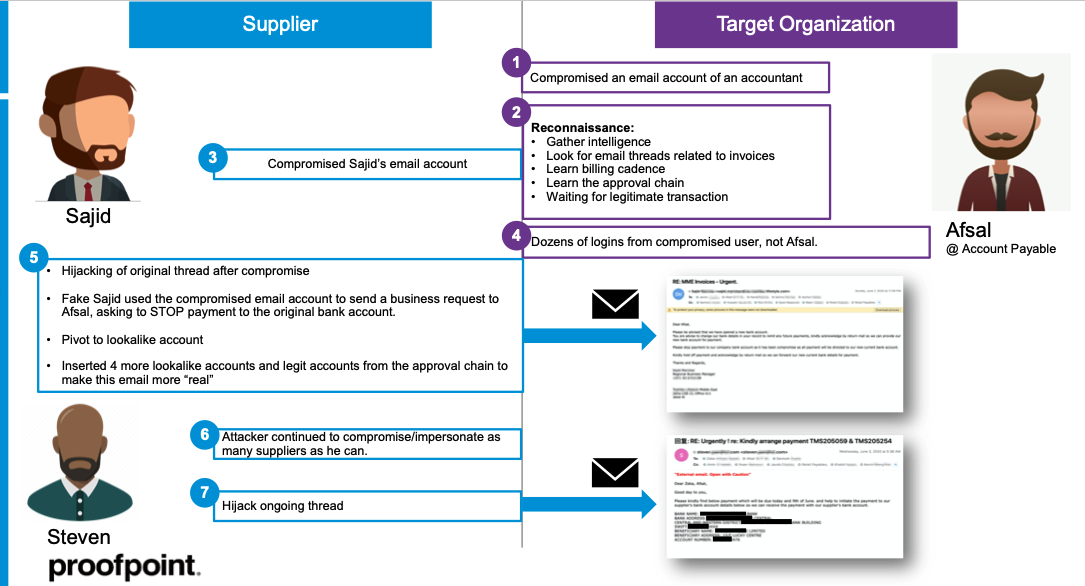
Diagram: Supplier fraud attack overview
In this attack, the attacker compromised the email accounts of both the target organisation and of its suppliers. The attacker first compromised an email account of an accountant who works at the account payable department of the target organisation. From there, he conducted extensive reconnaissance to gather information, such as billing cadence, approval chain, and email threads related to invoices.
The attacker also compromised an account at the target organization’s supplier. Using the compromised account of Sajid, who’s a salesperson from supplier’s company, the attacker hijacked the original email thread and requested Afsal, who also works at the accounts payable department of the target organisation, to STOP payment to the original bank account. He then pivoted to impersonation using a lookalike domain in the reply-to. By adding a bunch of lookalike accounts along with legitimate accounts from the approval chain to the cc field, the attacker made this email more creditable. (see Figure 1)
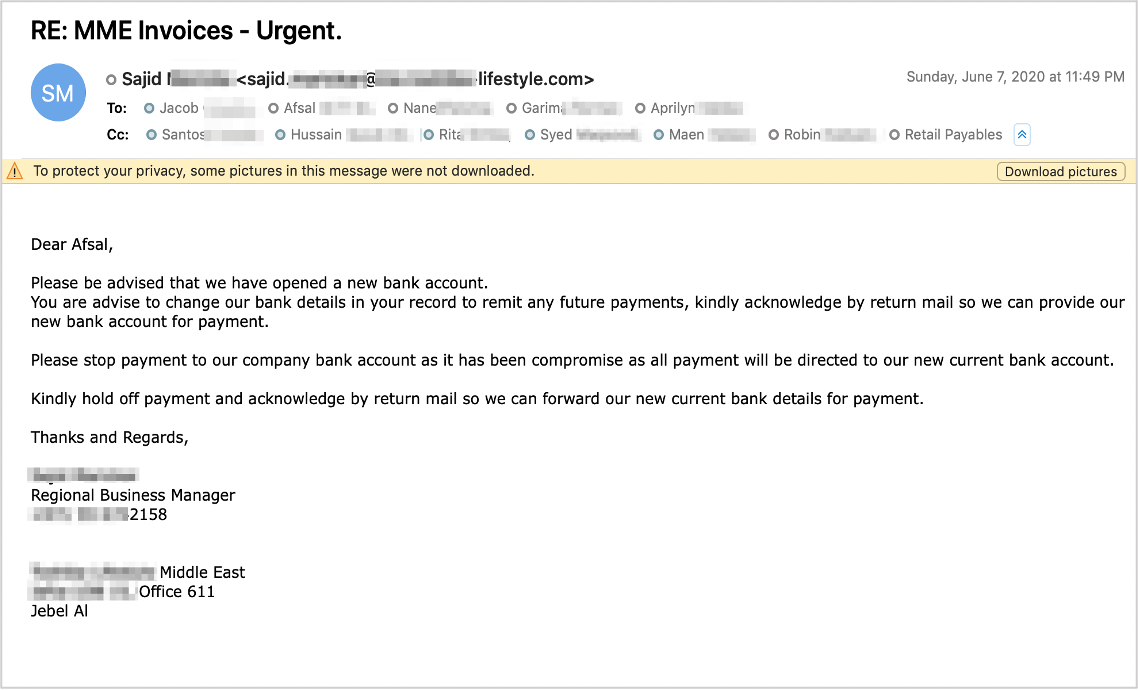
Figure 1: The attacker used the supplier’s compromised account (Sajid) to hijack an email thread, asking the target organisation to stop payment to the original bank account.
Meanwhile, the attacker continued to compromise and impersonate as many suppliers as he could. He compromised Steven’s account, who is another supplier of the target organisation, and used it to hijack another ongoing thread, asking Afsal to initiate payment to the bank account controlled by the attacker. (see Figure 2)
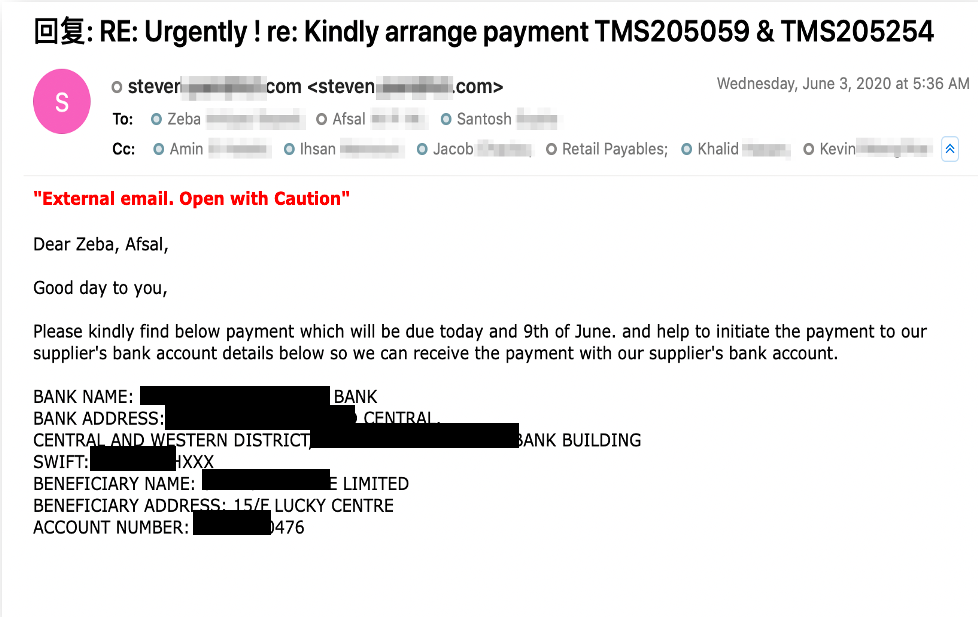
Figure 2: Attacker continued to compromise another supplier’s account (Steven) and use it to hijack other email thread, asking Afsal who works at the account payable department to initiate payment to the bank account controlled by the attacker.
This is how sophisticated a supplier fraud attack is. With Proofpoint Advanced BEC Defense, we caught this attack in time and stopped a potential loss of millions of dollars.
Advanced BEC Defense analysed the header data and uncovered that the attacker was operating from a Nigerian IP space and that he utilised a compromised GoDaddy mail infrastructure to hijack the original thread posing as Sajid. Our enhanced BEC detection engine also identified the inconsistent reply-to pivot, as well as multiple lookalike accounts inserted in the CC field— both are emerging BEC tactics. Furthermore, in the message body, it detected words and phrases that implied urgency and that required financial transactions. Piecing every detail together, we detected and blocked this complex supplier invoicing fraud attack.
How Advanced BEC Defense Differs from Others
Tackling payload-less threats like BEC requires more than ML algorithms. It requires a broad and deep set of data and human threat expertise to train those ML models to accurately detect and stop bad messages without misidentifying and blocking good messages. ML models trained with bad or incomplete data and no threat context generate high false positives, creating more work for security and messaging teams while delivering a poor user experience.
Proofpoint is uniquely positioned to address this hard-to-detect threat by combining our heritage in machine learning/AI with extensive threat data and threat analyst expertise. We see and analyse 2B+ messages daily and monitor hundreds of millions of domains and 16M+ cloud accounts. We correlate and aggregate everything we see, training our ML with rich threat data gathered across multiple threat vectors and a broad customer footprint. That coupled with our human expertise truly differentiates our BEC protection— providing the best detection effectiveness with minimum false positives. Vendors who tout their ML/AI models often lack the extensive data across multiple threat vectors and expert threat intelligence required to accurately and effectively stop email threats. Finally, ML-only models suffer from high false positive rates that prevent any automation from being reliably built around their detections, introducing cost and complexity for security teams to manually chase down potential BEC risks rather than simply automating common workflows.
And unlike other email security solutions that rely on static rule matching and manual tuning to find BEC scams, Proofpoint’s integrated platform utilises Advanced BEC Defense that learns in real-time. This learning enables dynamic classification of “good” and “bad” emails. It reacts to changes in attack tactics, stopping BEC variants that are often missed by legacy email security providers. Moreover, Advanced BEC Defense provides granular visibility into BEC threat details, revealing BEC themes such as gift carding, payroll redirect, invoicing, and more. It provides observations about why the message was suspicious as well as message samples. This insight allows the security team to better understand, communicate, and mitigate BEC risks.
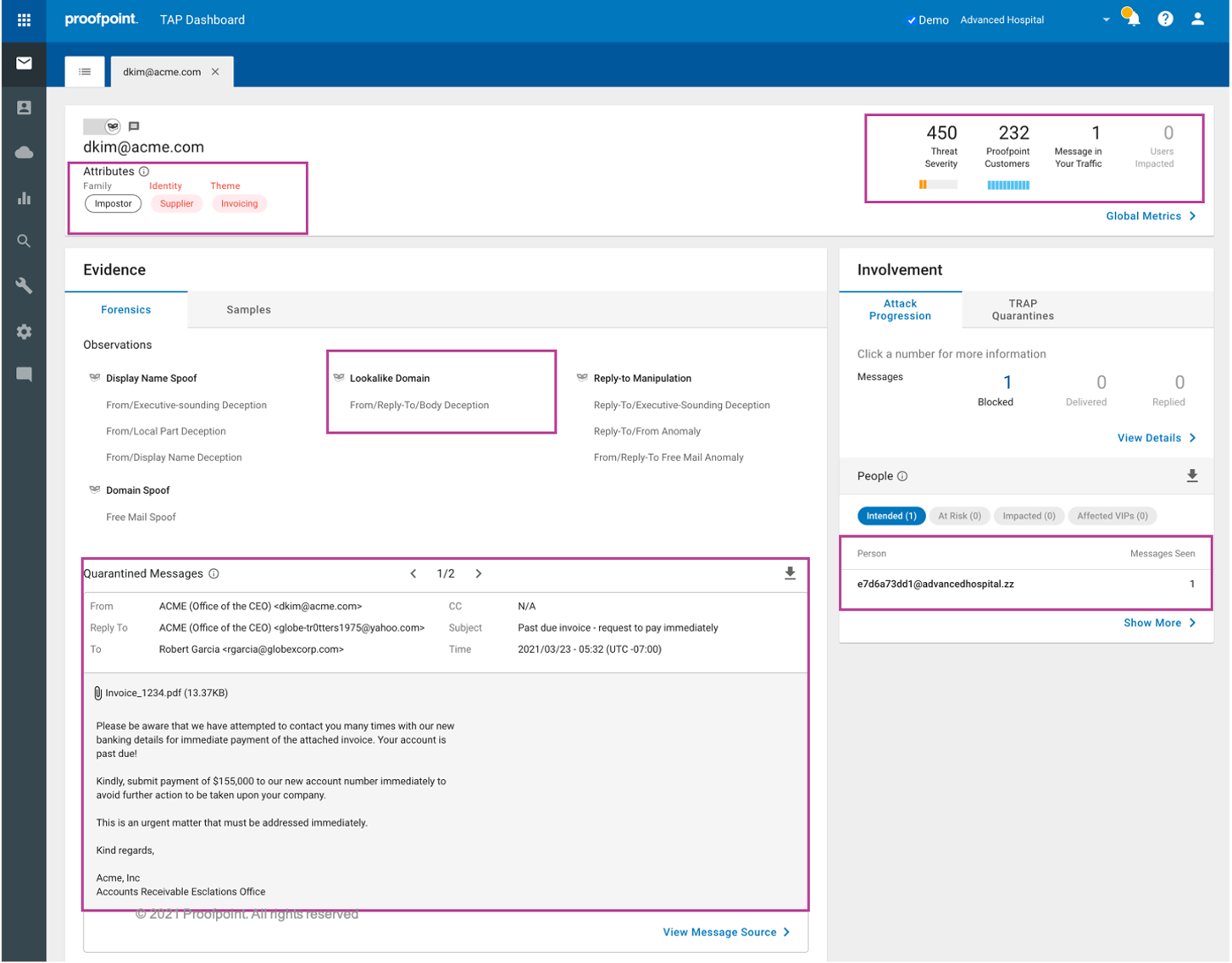
Figure 3: Proofpoint identifies which users are mostly attacked by imposter threats and provides granular visibility into BEC threat details.
Detect and Stop BEC Threats before They Enter
Advanced BEC Defense is an integral part of the Proofpoint Threat Protection Platform. All our existing gateway customers will benefit from the new and improved detection with no additional cost. And only Proofpoint provides an integrated platform that accurately detects BEC threats without blocking good messages, provides visibility into who is being targeted with BEC and granular BEC threat details, automates remediation of BEC threats, educates end-users to identify and report potential BEC threats, and delivers insights into suppliers that may be compromised or impersonated.
To learn more about how Proofpoint addresses BEC attacks, check out our BEC solution page. To find out how prepared your organisation is to fight email fraud, take our BEC readiness assessment here.

