Today more than ever, companies across the country are facing tighter budgets and resource constraints. Universities and schools are no exception. For many, maintaining suboptimal IT tools to save money isn’t just a matter of prudence—it’s a necessity. So, why would a top university brave the long and complex educational procurement process just to augment their existing Microsoft email security?
This is what one of our newest customers did. Their story echoes those of thousands of Microsoft customers of all sizes, who in the last year have augmented their Microsoft security with Proofpoint to create a defence-in-depth approach. While keeping their identity anonymous, we wanted to share their story and the insights they learned along the way.
Redefining acceptable risks
As part of a larger agreement with Microsoft, the university had spent years using their native email security to protect more than 40,000 mailboxes belonging to students and staff. For much of that time, the university’s security team dealt with multiple obstacles. Microsoft’s lack of integrations, its inflexible email controls and its highly manual incident analysis were just a few.
The security team recognised that as attacks grew more serious, they needed more layers of security to capture missed threats. The university was already grappling with increasing amounts of internally directed business email compromise (BEC) messages. These emails came from accounts that were compromised by malicious phishing emails that had been delivered to users’ inboxes.
On top of that, students and faculty were receiving thousands of additional advanced attacks per week. And the security team had to triage all of them manually. They experienced:
- Advanced social engineering threats
- Multi-layered phishing messages
- Multifactor authentication (MFA) bypass attacks
- Telephone-oriented attack delivery (TOAD) attacks
Without consistent quarantine controls, in-depth threat intelligence and automated remediation, the team couldn’t contain their expanding attack surface. Their threat visibility and productivity were further undermined by subpar reporting and integrations between other tools, such as SIEM and endpoint protection. When these issues were raised with Microsoft, its support team was slow to respond and follow up.
It was clear that Microsoft couldn’t stop these escalating attacks. So, the university turned to Proofpoint.
Why Augment: Comparing Microsoft and Proofpoint
With many years of Microsoft experience, the university had high expectations of Proofpoint to prove its business value. They wanted to be sure that Proofpoint would be a worthwhile addition to their existing security program. What follows are three key areas in which Proofpoint improved their security posture during the evaluation period.
Continuous detection and superior efficacy: Proofpoint wins
Unlike Proofpoint, Microsoft can’t detect many modern email threats like BEC and advanced phishing attacks. Our data shows that more than 63% of the threats missed by Microsoft—but detected by Proofpoint—are credential phishing.
This is largely due to Microsoft’s restricted URL-detection capabilities, which limit the sandboxing for links to post-delivery, payload-only threats. This means a user must click on a link to trigger Microsoft’s dynamic analysis. In our customer’s case, this puts the university and students at significant risk and frequently leads to compromised accounts.
Phishing links are one of the fastest-growing threat tactics. That’s why Proofpoint offers continuous detection for URL threats throughout the email lifecycle. Eighty percent of the URL threats we condemn are stopped before users can interact with them.
Our predictive URL analysis and new, industry-first predelivery URL hold and sandboxing make this possible. Together, they greatly reduce the chances that a user might activate a threat by accident. The remaining 20 percent of URL threats are stopped through click-time protection by:
- Rewriting URLs
- Sandboxing links in real time
- Opening potentially suspicious links in a sterile, isolated browsing session
Proofpoint’s superior efficacy doesn’t end with URLs and phishing. We stop the widest variety of targeted threats with the highest accuracy. That’s because we have a multilayered, artificial intelligence (AI)-driven detection stack.
To improve our already superb BEC protection, we added predelivery semantic analysis to our large language models (LLMs). As a result, our behavioural engines can understand the context and purpose of an email’s content. When a message with malicious intent is found, we automatically remove it before it’s delivered to a user’s inbox.
During the first few days of the university’s evaluation, Proofpoint caught several hundred BEC messages. All of them had been missed by Microsoft. This saved our customer substantial manual remediation efforts and confirmed the need for more layers of security.
Management and remediation efficiencies: Proofpoint wins
Many Microsoft security customers know that supporting their solutions is both time and labour intensive. For example, Microsoft provides very restricted options to automate message remediation post-delivery. And unless you’re willing to pay for add-ons, like Microsoft 365 E5 with Defender, you get even less visibility into the emails that are condemned after the fact.
What’s more, Microsoft’s remediation can’t digest alerts from other security tools, and it can’t cross-correlate their data. Companies are left in the dark and are ultimately less secure with the finite remaining use-cases where Microsoft security features are actually effective.
But it doesn’t have to be this way. Combining Proofpoint remediation with Microsoft lightens the load on your overburdened security team.
Proofpoint automates the analysis and removal of threats from users’ inboxes across your business. This includes messages that are forwarded to other recipients and distribution lists, as well as those reported by users. Our responsive email warning banners make it easy for users to report directly from inside a message. To reinforce good security habits, they receive real-time feedback (malicious or not malicious) on their report, which closes the user experience loop.
Before they started working with Proofpoint, the university needed several full-time employees dedicated to manually remediating missed threats and overseeing email management. This was a critical role because these tasks needed to be done 24/7. With Proofpoint, these employees are now free to work on more impactful and valuable projects. In fact, our data shows that when businesses add Proofpoint email security, the time it takes to remediate malicious emails is reduced by an average of 90% or more.
Human-centric insights: Proofpoint wins
Microsoft can’t catch what it can’t see. And unfortunately, the lack of visibility within Microsoft is systemic. It extends through user reporting and into integrations with third-party vendors. That means it offers a very narrow scope of threat telemetry as well as a fraction of the behavioral and human-centric insights that Proofpoint provides.
This leaves Microsoft customers blind to their greatest vulnerabilities—how and where their people are being attacked. When the university gained this level of understanding through Proofpoint, they found it indispensable in helping to prevent human-targeted incidents that might otherwise have quickly snowballed into larger disruptions.
The visibility into the global threat landscape that we share with our customers is unmatched. Proofpoint analyses more than three billion messages daily across our more than 510,000 customers worldwide. We offer this data to our customers in a wealth of easy-to-understand reports. Reports are designed for every type of user, ranging from executive-level overviews to individual- and campaign-specific forensics.
For example, our Very Attacked People™ report shows much more than how your users are targeted. It reveals who is most vulnerable, why they are attacked and what the impact of a successful threat might be to your business. The information in this report allows administrators to increase protection to who and where it is needed the most—and make better use of limited security resources.
We want this data to be as useful as possible. That’s why we make sure that it’s easily accessible through integrations with other top cybersecurity providers. Proofpoint enables seamless, bidirectional data-sharing with vendors like Microsoft, CrowdStrike, Palo Alto Networks and others. And because we do this, our customers get:
- Security alerts that are more accurate
- Valuable human-centric security observations
- Important context for incident investigations
Because the university didn’t have comprehensive reporting and vendor integrations, they were left waiting to respond to attacks after the damage was done. By combining Proofpoint with Microsoft, they received the additional insights needed to manage threats proactively and understand their entire threat landscape.
Creating a layered defence with Proofpoint
After a few days of evaluating Proofpoint, the university’s security team was convinced. In fact, they had already started to rely on our platform to manage incidents. They saw an immediate shift in their ability to be proactive in their identification of malicious messages and to remove them before users clicked.
The data from the university’s evaluation underscores the difference Proofpoint makes. Within one week, we captured more than 14,000 threats that Microsoft had missed, including malware, phishing and BEC attacks. That is equivalent to over 650,000 messages per year.

Anonymized threat data from the customer’s evaluation.
The university’s experience, though educational, isn’t unique. Proofpoint offers a superior Threat Protection solution that consistently captures 30%+ more malicious messages, on average, than Microsoft alone. This is why 87 of the Fortune 100 companies—83 of which use Microsoft 365—trust Proofpoint to augment and fill the gaps in their native security.
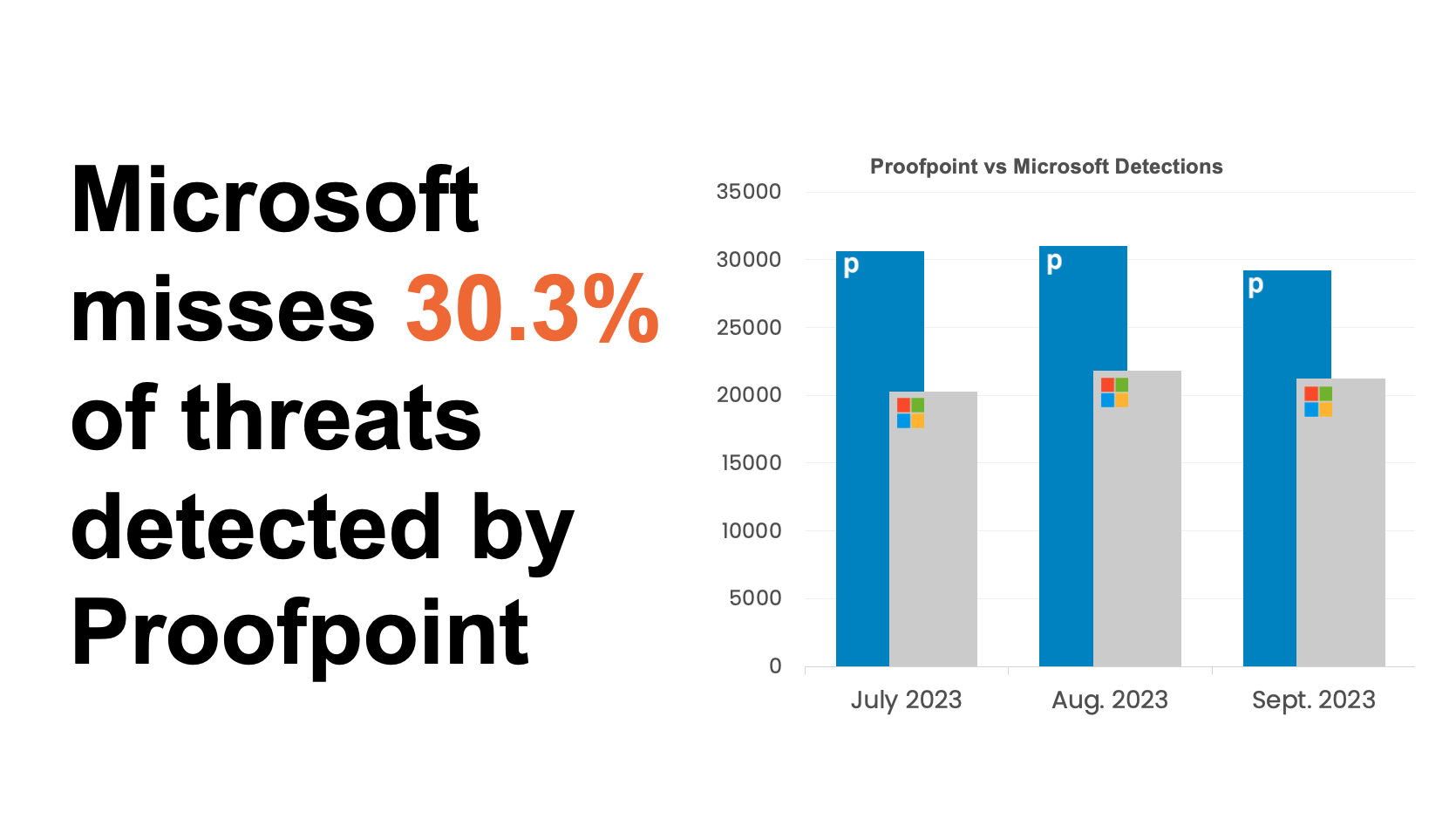
Averaged results from Proofpoint evaluations with Microsoft.
The real cost of native security
There’s a real, unspoken cost to ‘good enough’ security. And it becomes clear when you consider the extra time and resource overheads, increased management and poor technical support that comes from relying on Microsoft’s native security capabilities alone. With advanced threats like BEC that target Microsoft and generate staggering financial losses, your business can’t afford not to have the added protection.
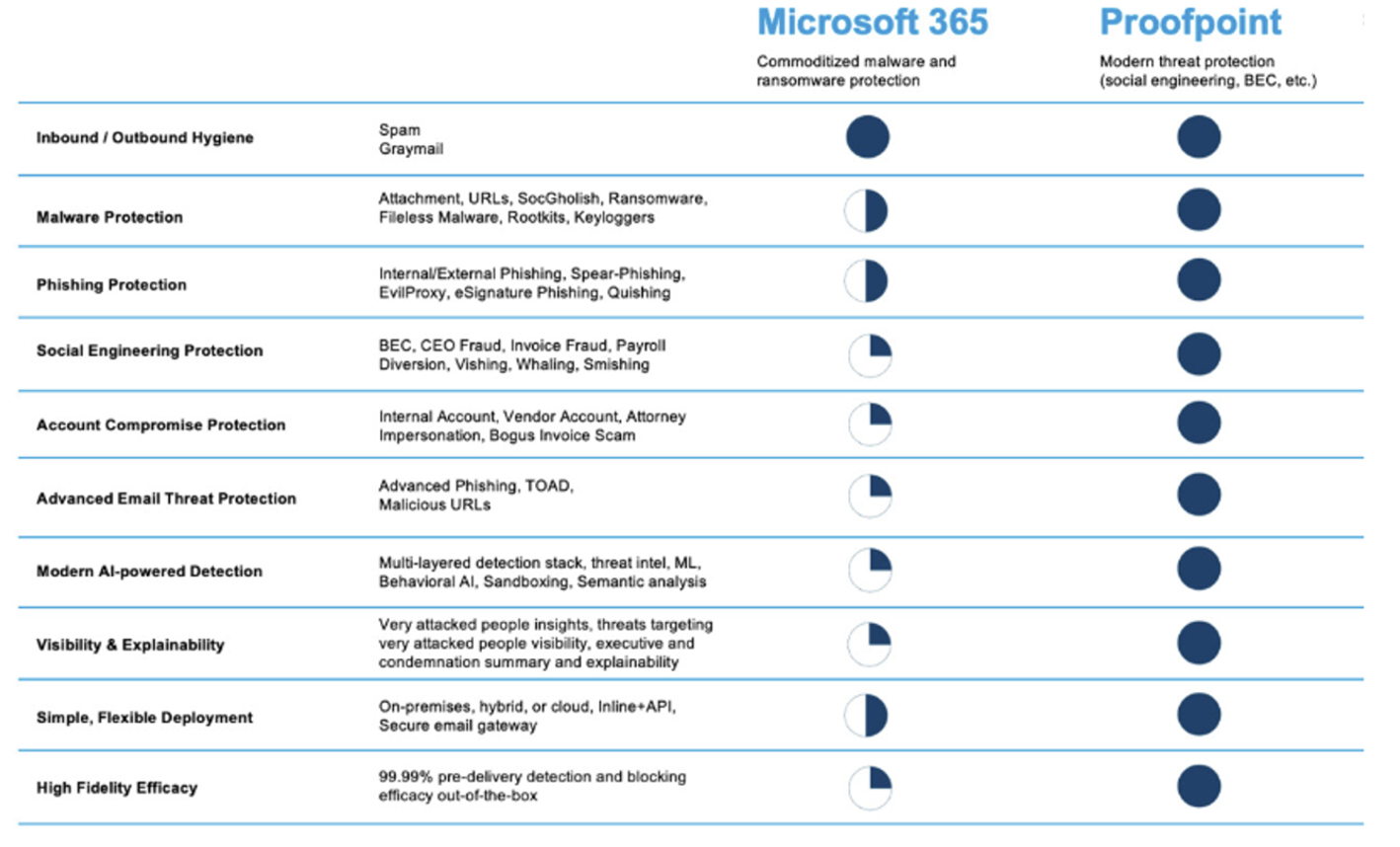
A comparison of Microsoft 365 and Proofpoint protection.
Proofpoint is the best human-centric security platform to enhance Microsoft. We give you the tools you need to create a layered defence against the latest, evolving threat tactics. Our continuous, end-to-end detection stops more human-targeted attacks before, during and after delivery. By fortifying your Microsoft investment with Proofpoint, you can reduce your risk, optimise your limited resources and increase the efficiency of your security teams.
Want to learn more about how Proofpoint can enhance your native Microsoft 365 security against costly cyberattacks? Read our solution brief, Microsoft and Proofpoint: More Secure Together.

